This document discusses malware samples that abuse PowerShell on Windows systems. It provides examples of malware behaviors like generating batch files to execute PowerShell scripts, downloading data from command and control servers, dumping browser cookies, checking for sandbox detection, and downloading/executing files. The document concludes that PowerShell is commonly used by malware in a similar way that AutoIt is abused, and that the focus should be on malicious behaviors rather than the scripting language itself.



![Fourteenforty Research Institute, Inc.
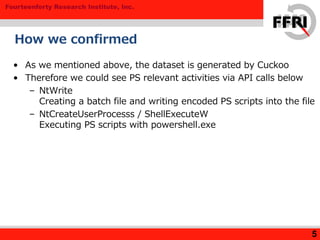
Dumping cookies
8
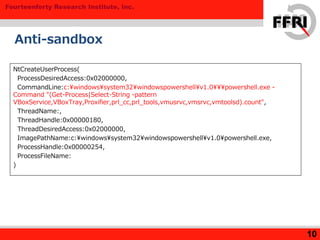
NtCreateUserProcess(ProcessDesiredAccess:0x02000000,
CommandLine:c:¥windows¥system32¥windowspowershell¥v1.0¥¥¥powershell.exe -
Command "dir ([system.environment]::GetFolderPath('Cookies')+'¥*.txt')|Get-Content >>
'C:¥Users¥admin¥AppData¥Local¥Temp¥lbdatdp.txt'",
ThreadName:, ThreadHandle:0x0000019c, ThreadDesiredAccess:0x02000000,
ImagePathName:c:¥windows¥system32¥windowspowershell¥v1.0¥powershell.exe,
ProcessHandle:0x000001a4, ProcessFileName:)
NtCreateUserProcess(ProcessDesiredAccess:0x02000000,
CommandLine:c:¥windows¥system32¥windowspowershell¥v1.0¥¥¥powershell.exe -
Command "dir ([system.environment]::GetFolderPath('Cookies')+'¥Low¥*.txt')|Get-Content
>> 'C:¥Users¥admin¥AppData¥Local¥Temp¥lbdatdp.txt'",
ThreadName:, ThreadHandle:0x00000224, ThreadDesiredAccess:0x02000000,
ImagePathName:c:¥windows¥system32¥windowspowershell¥v1.0¥powershell.exe,
ProcessHandle:0x00000270, ProcessFileName:)](https://image.slidesharecdn.com/malwaremarmedwithpowershell-150604051058-lva1-app6892/85/Malwarem-armed-with-PowerShell-8-320.jpg)