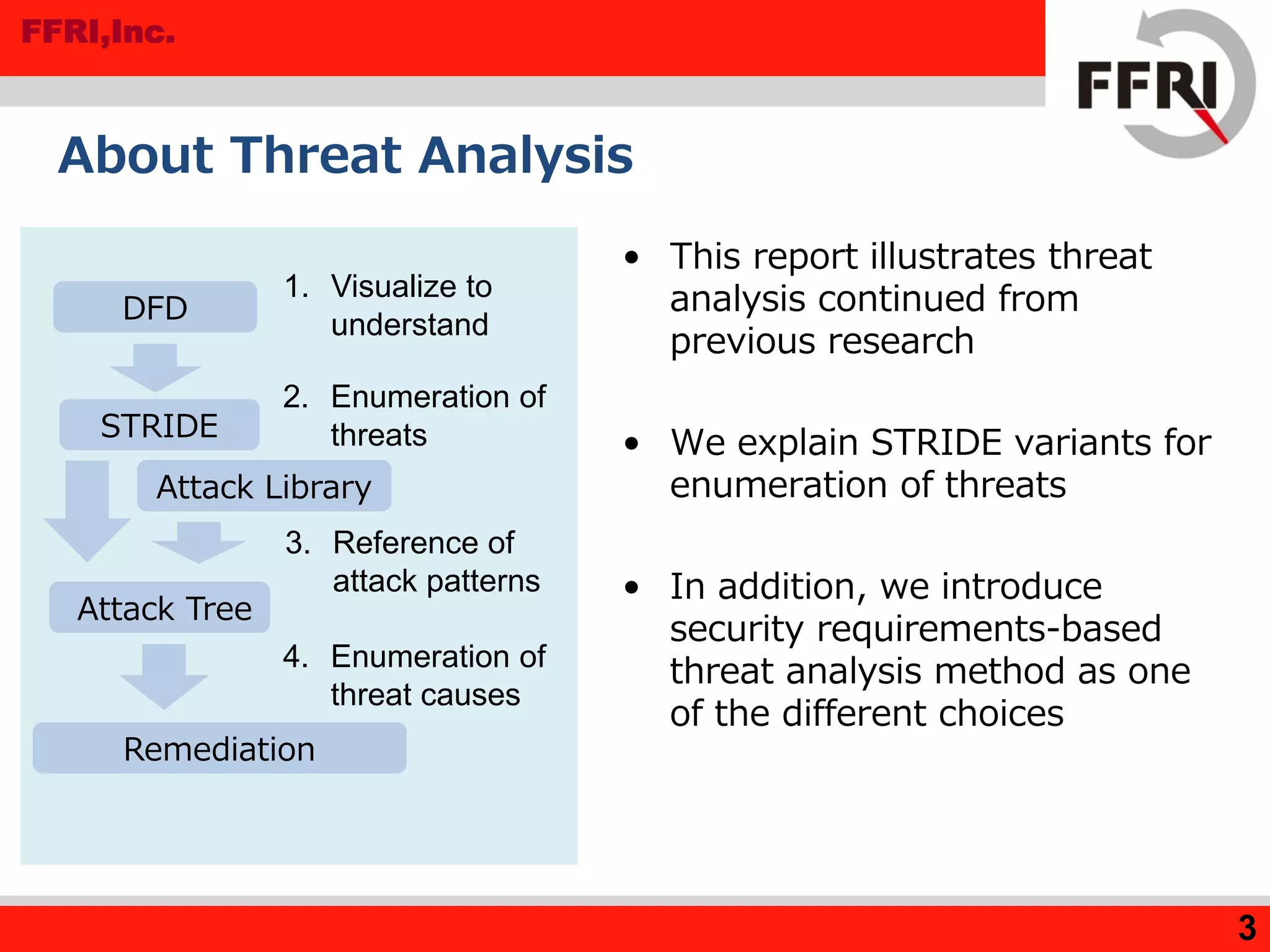
The document discusses various threat analysis methods, focusing on STRIDE variants (stride-per-element and stride-per-interaction) and a security requirements-based threat analysis approach. It highlights the advantages and disadvantages of each method, including time efficiency, accuracy, and ease of use. The analysis methods are intended for different phases of system design and varying levels of analyst expertise.
![FFRI,Inc.
1
STRIDE Variants and
Security Requirements-based Threat Analysis
FFRI, Inc.
http://www.ffri.jp/en/E-Mail: research-feedback[at]ffri.jp
Twitter: @FFRI_Research
Monthly Research 2016.10](https://image.slidesharecdn.com/mr201610stridevariantsandsecurityrequirements-basedthreatanalysiseng-161115103259/75/STRIDE-Variants-and-Security-Requirements-based-Threat-Analysis-FFRI-Monthly-Research-Oct-2016-1-2048.jpg)
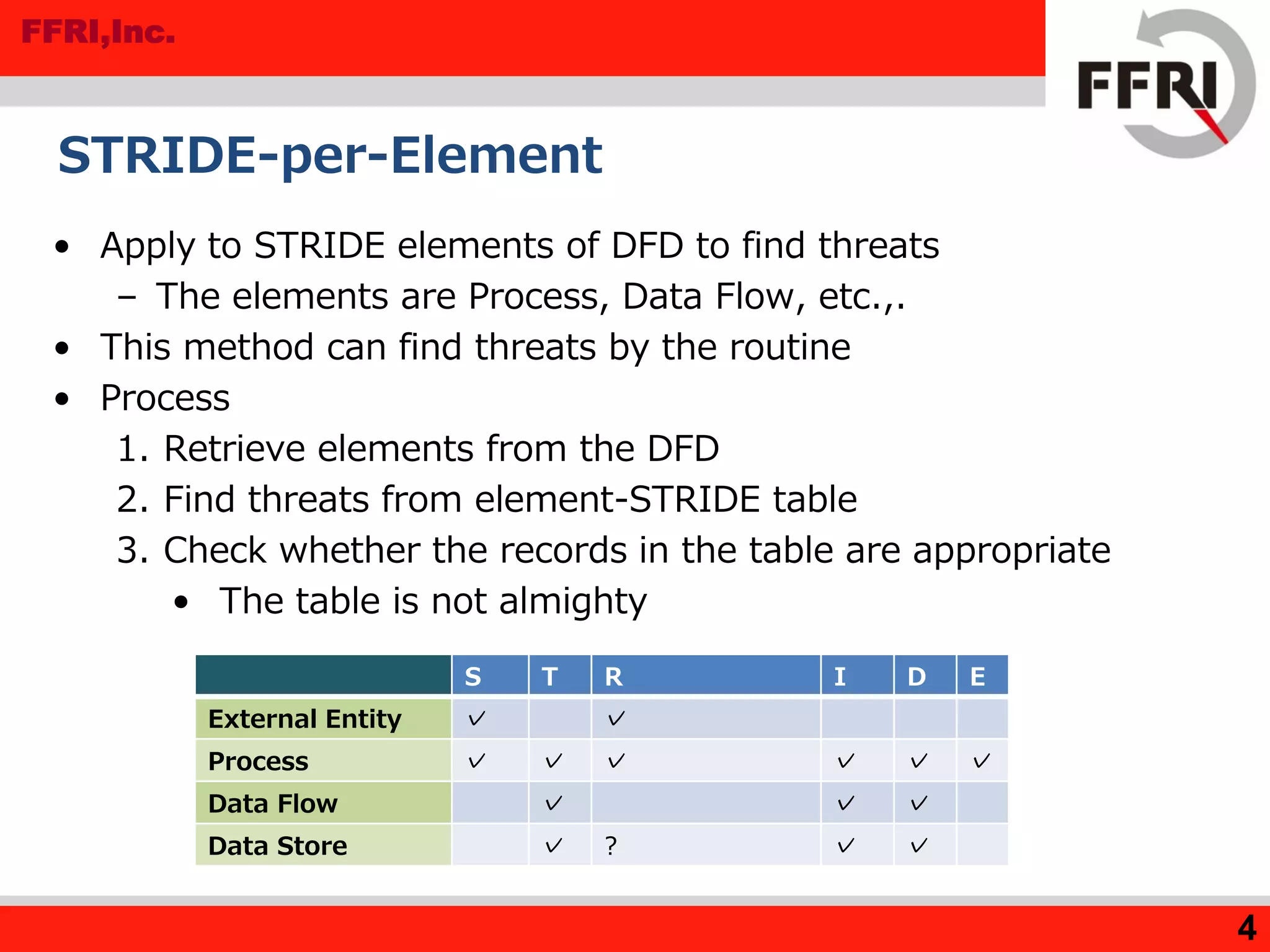
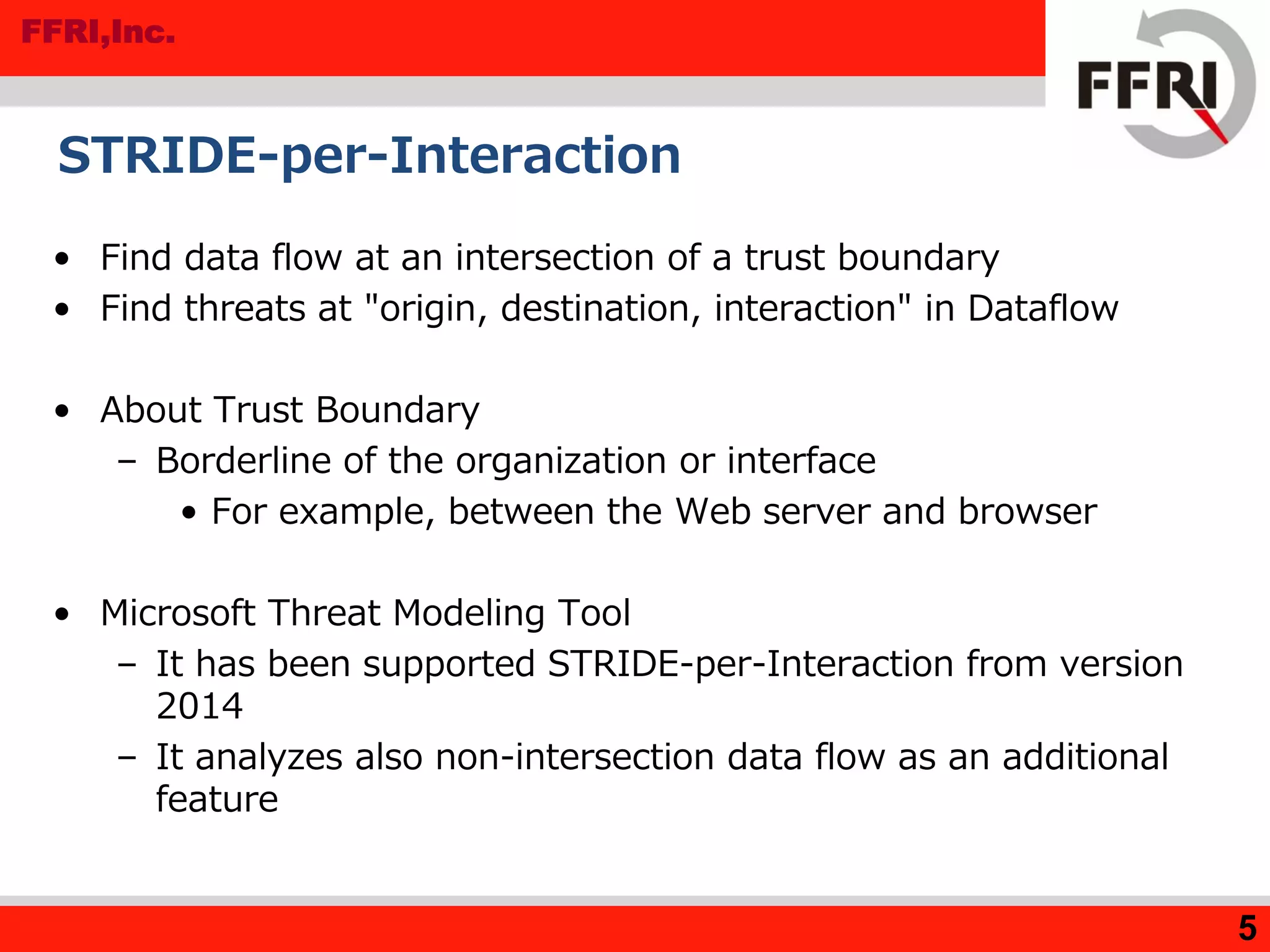
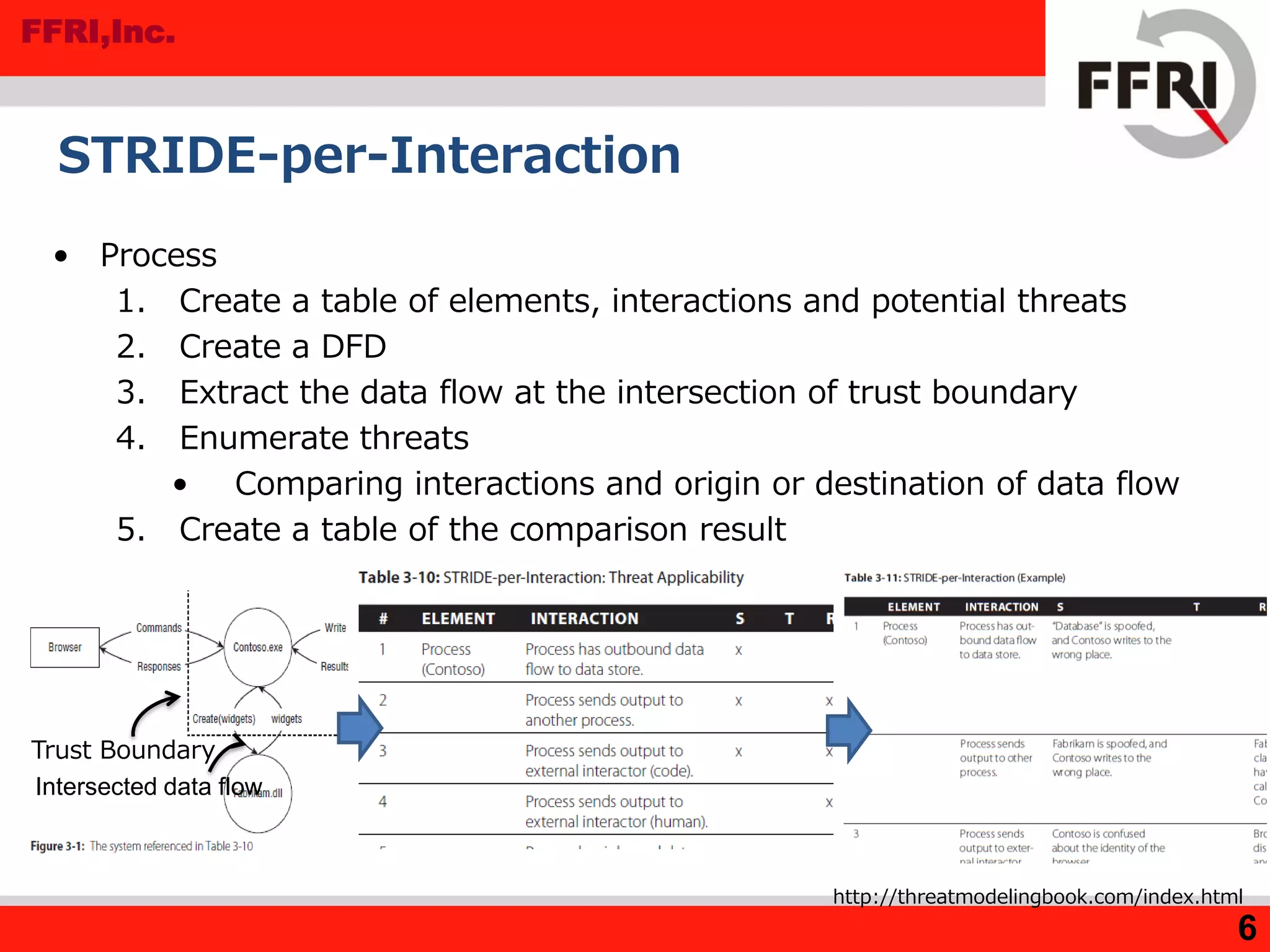
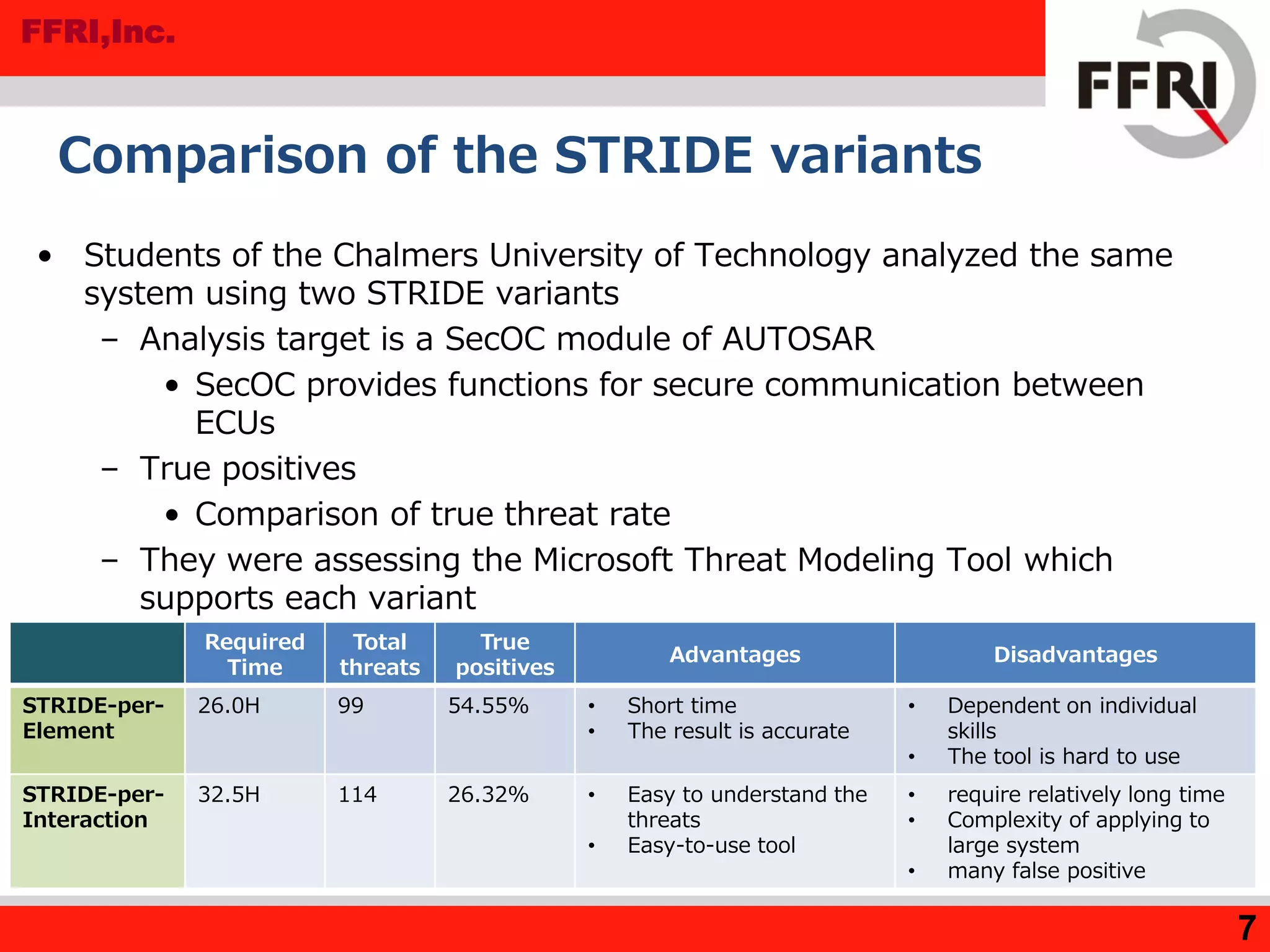
![FFRI,Inc.
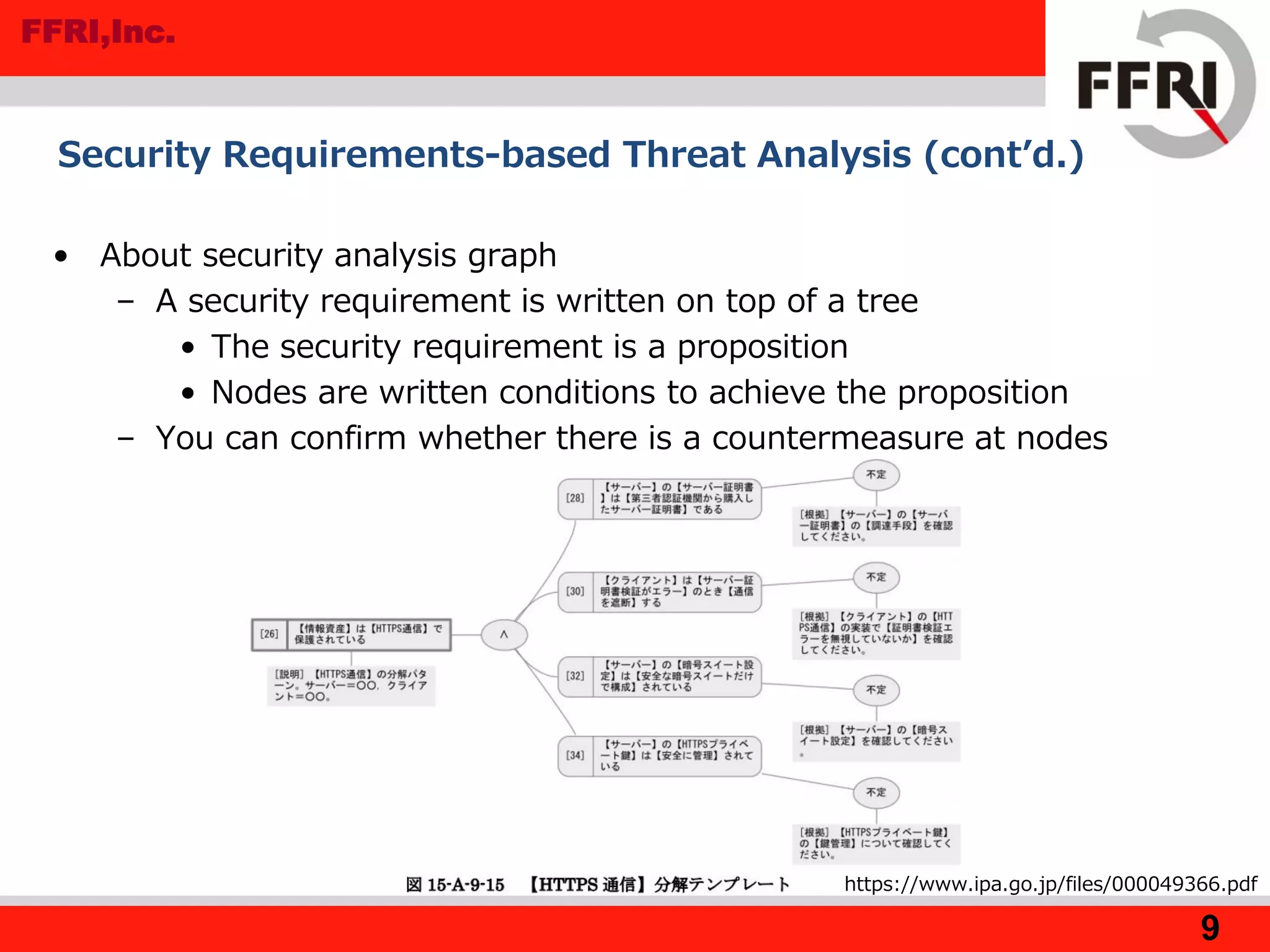
Security Requirements-based Threat Analysis
• This method has been proposed by Masaru Matsunami of Sony DNA
• It extracts security requirements from design and specification
• It was used for threat analysis of "harmo" system by the Sony
• Process
– Find "actor" and "assets" from specification documents
– Extract threat event based on template ["actor" "can / can't"
"read/write/execute" to "assets"]
• Threat event: Malicious third party can read personal data
• If necessary find also "Location"
– Security requirement is found on the basis of threat events
• Security requirement is found on the basis of threat events
– Draw a security analysis graph on the basis of security requirements
8](https://image.slidesharecdn.com/mr201610stridevariantsandsecurityrequirements-basedthreatanalysiseng-161115103259/75/STRIDE-Variants-and-Security-Requirements-based-Threat-Analysis-FFRI-Monthly-Research-Oct-2016-8-2048.jpg)