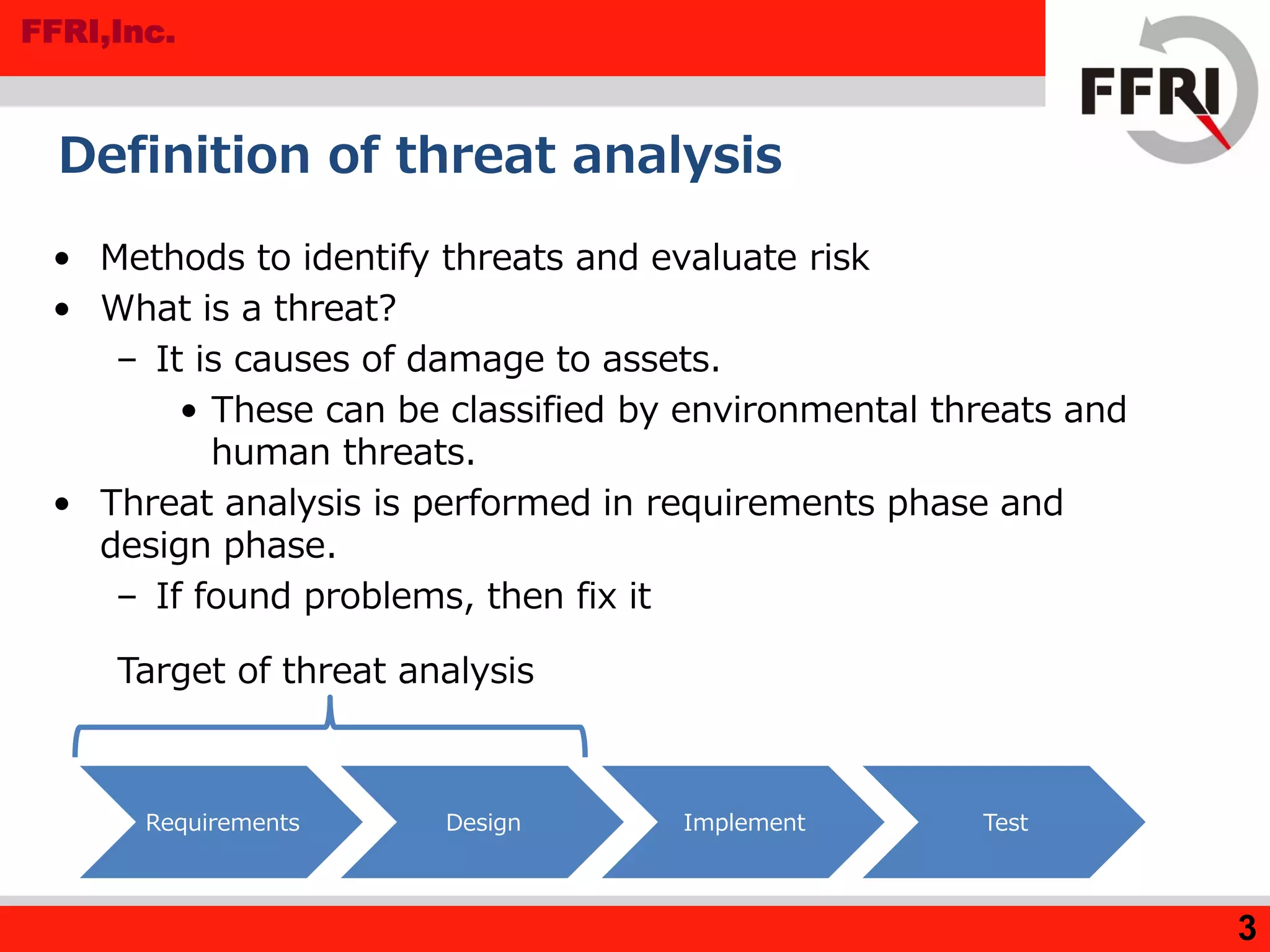
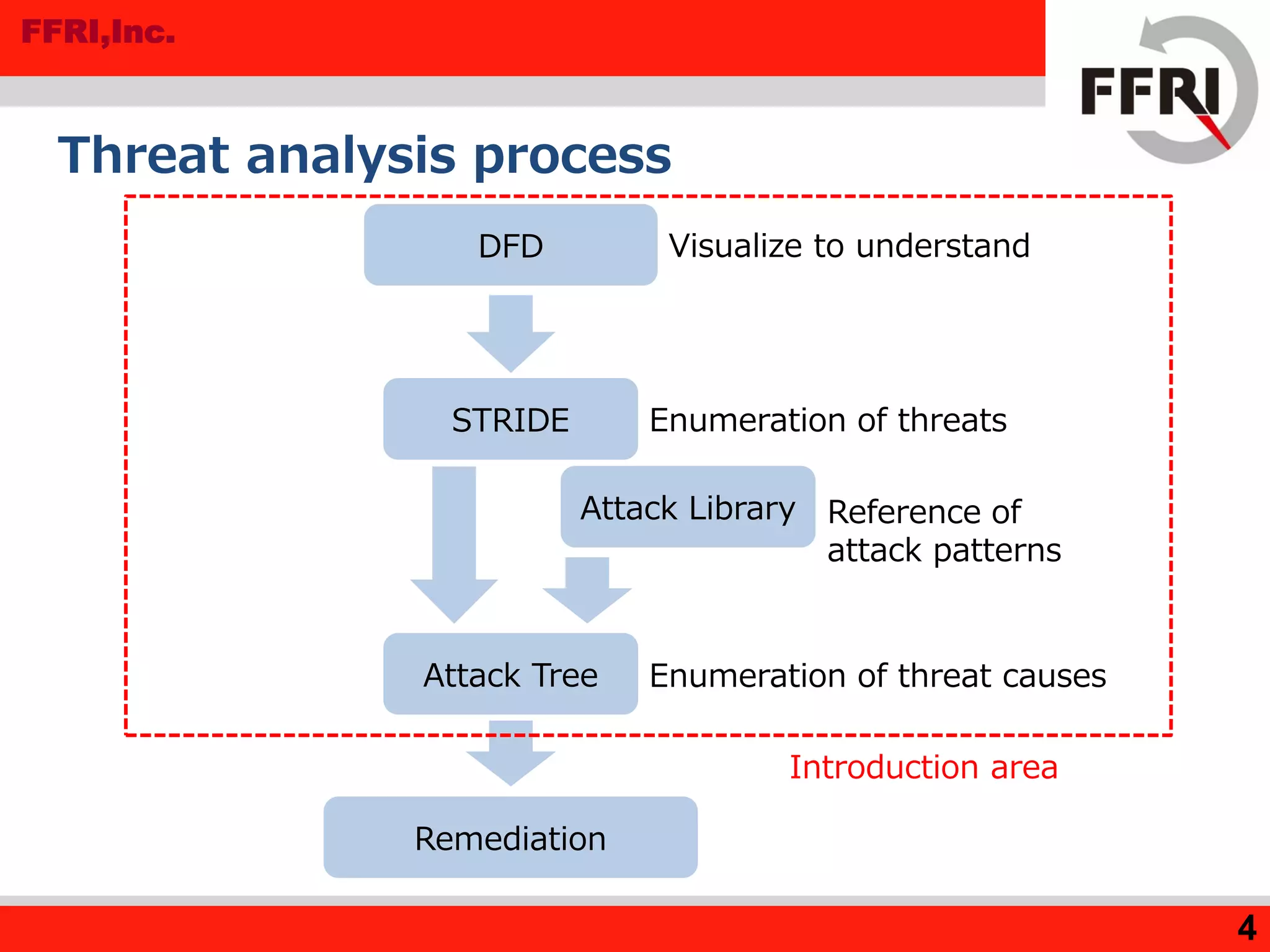
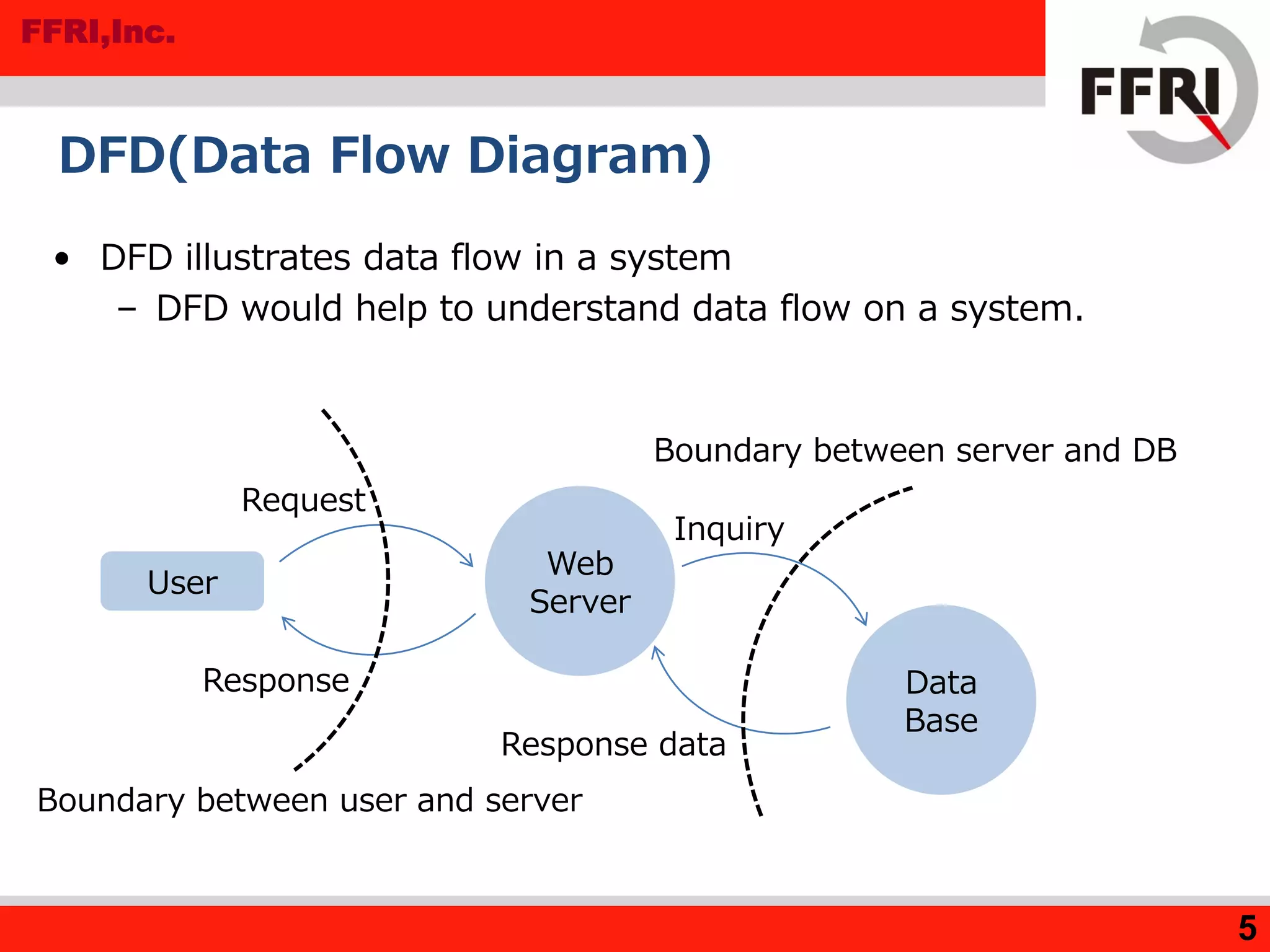
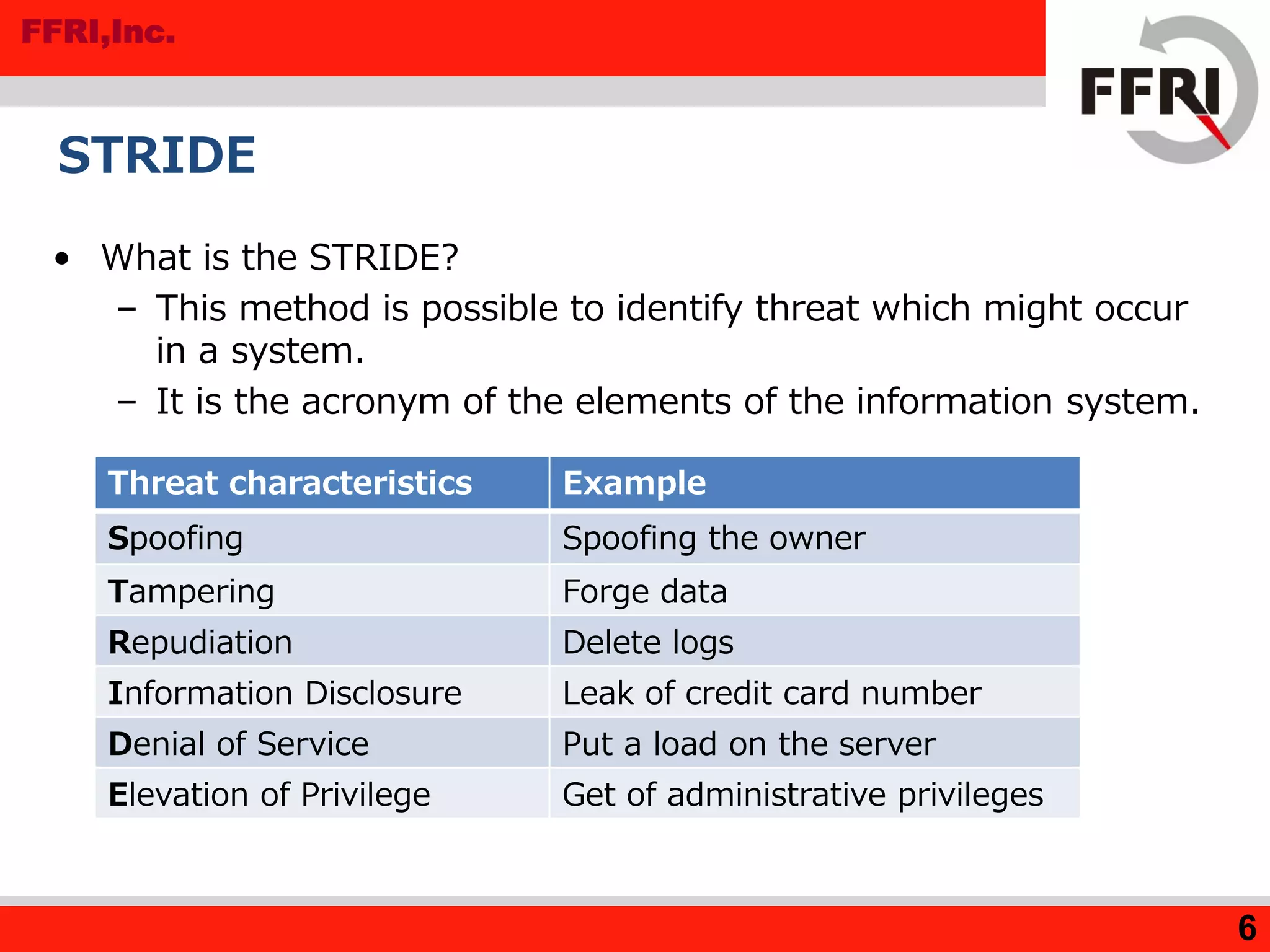
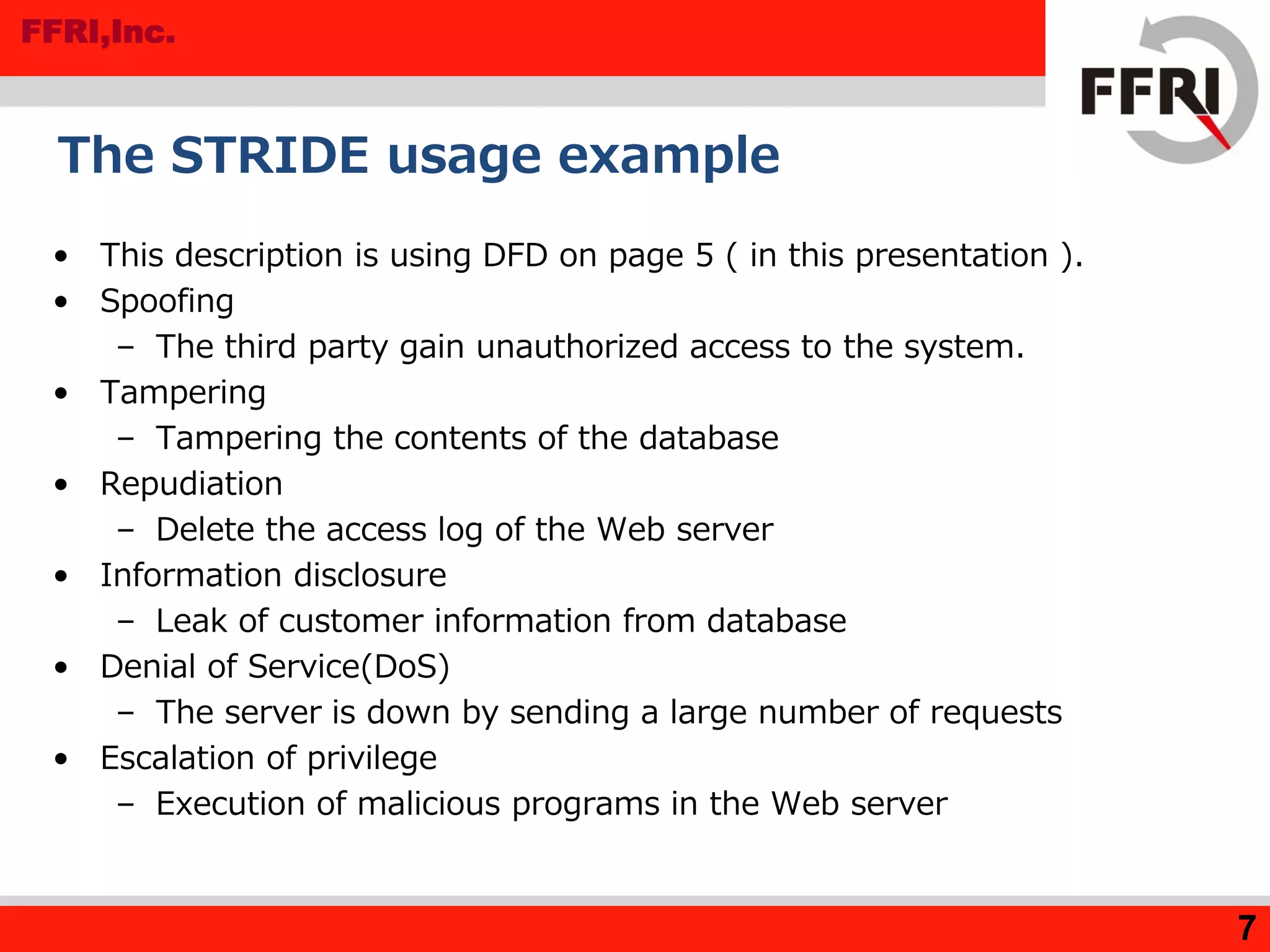
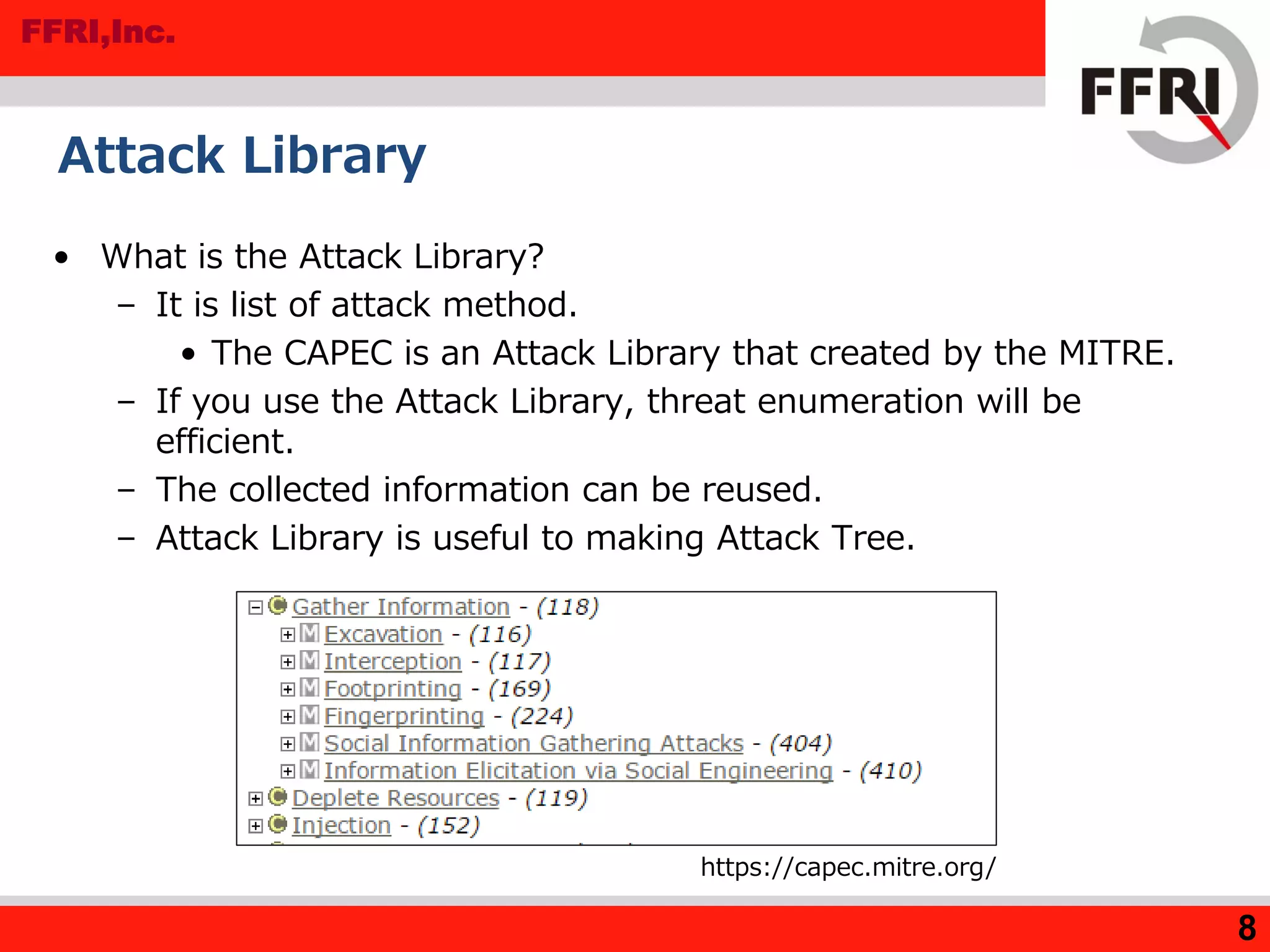
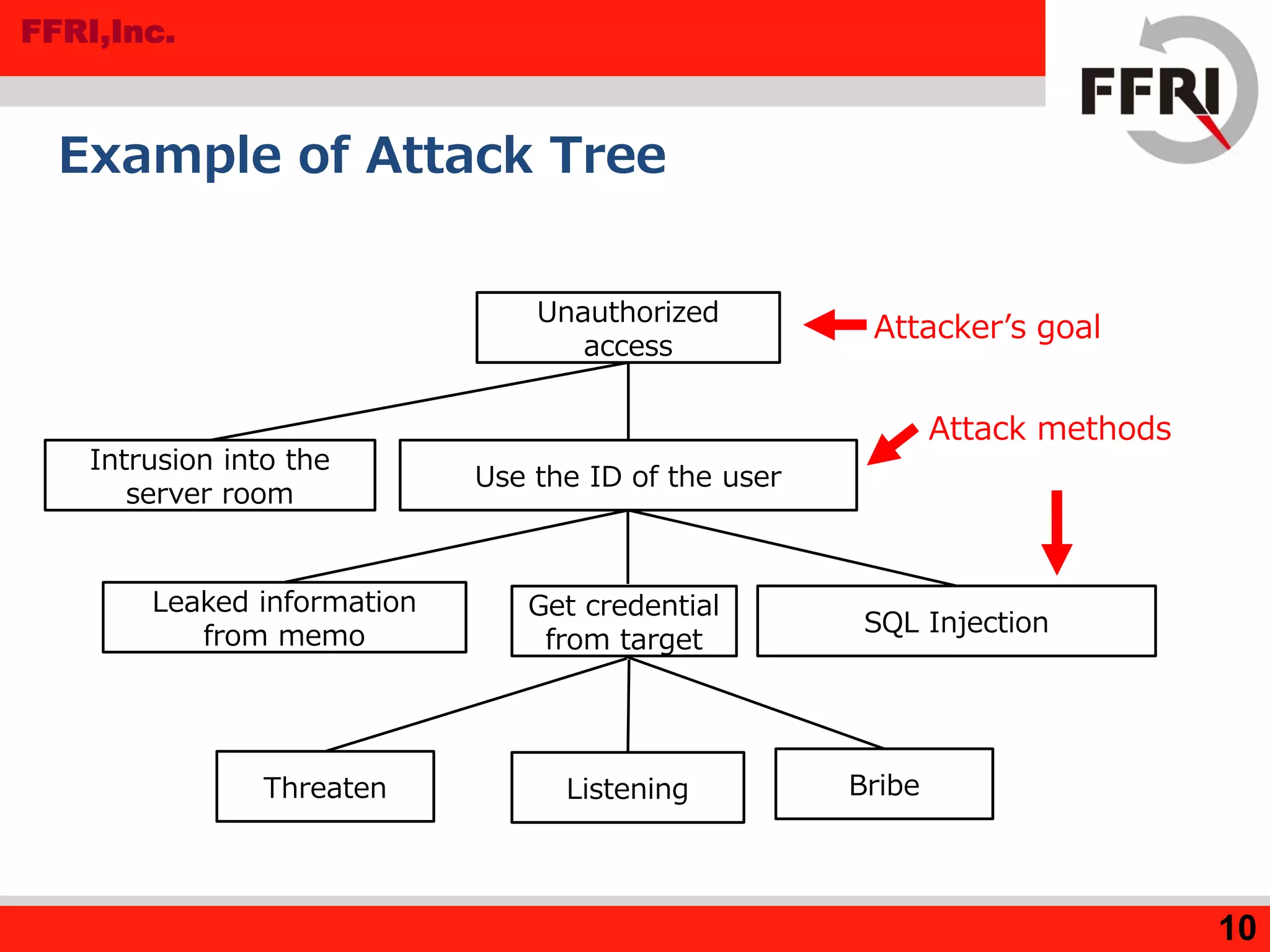
The document outlines various methods for threat analysis, including Data Flow Diagrams (DFD), STRIDE, attack libraries, and attack trees. It defines threats, enumerates various threat characteristics, and explains the processes involved in conducting a thorough threat analysis. The document concludes that these methods, especially when combined, can help efficiently identify and visualize threats to enhance security planning.
![FFRI,Inc.
1
Introduction of Threat Analysis Methods
FFRI, Inc.
http://www.ffri.jpE-Mail: research-feedback[at]ffri.jp
Twitter: @FFRI_Research
Monthly Research 2016.9](https://image.slidesharecdn.com/mr201609introductionofthreatanalysismethods-161017084917/75/Introduction-of-Threat-Analysis-Methods-FFRI-Monthly-Research-2016-9-1-2048.jpg)