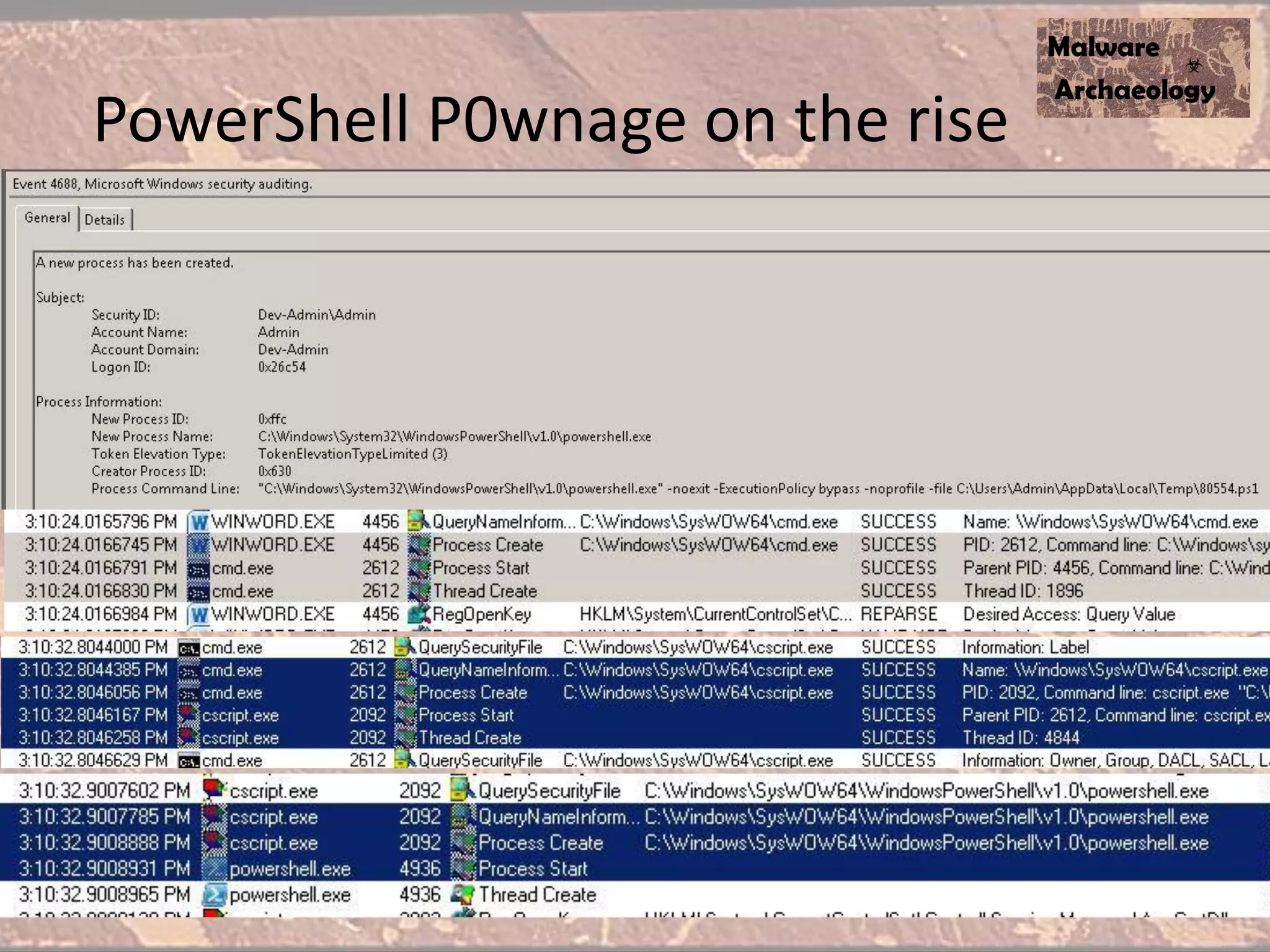
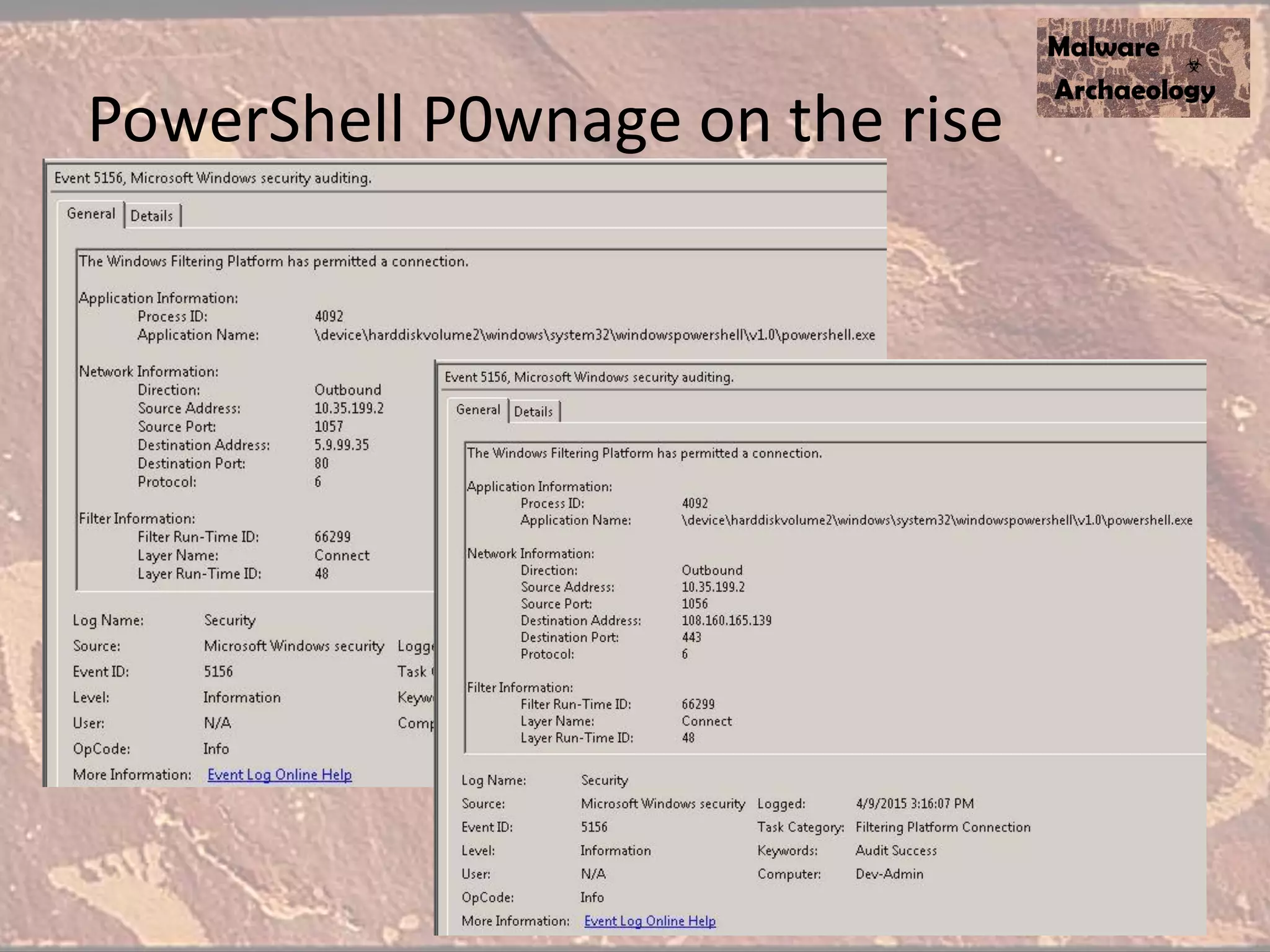
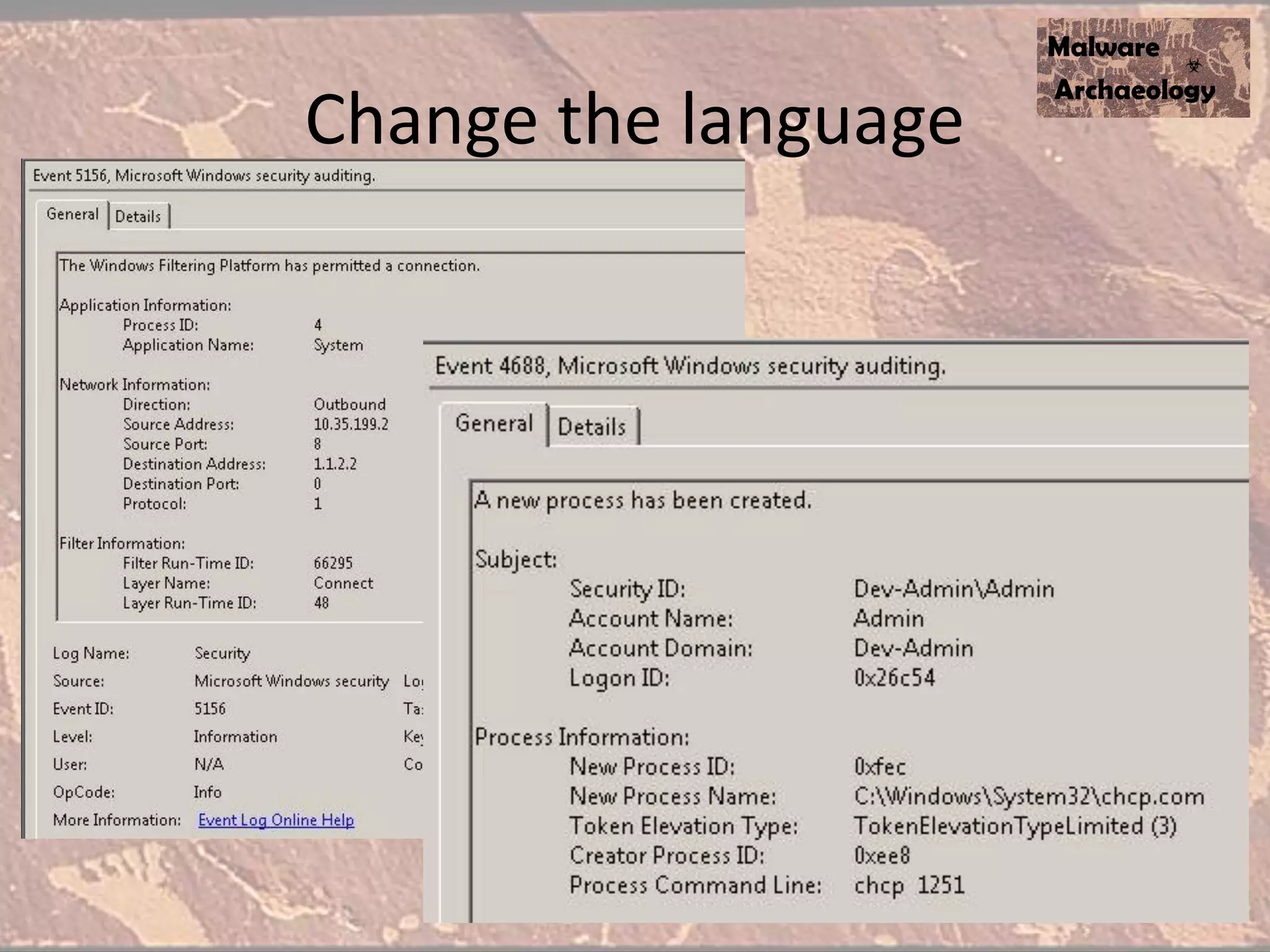
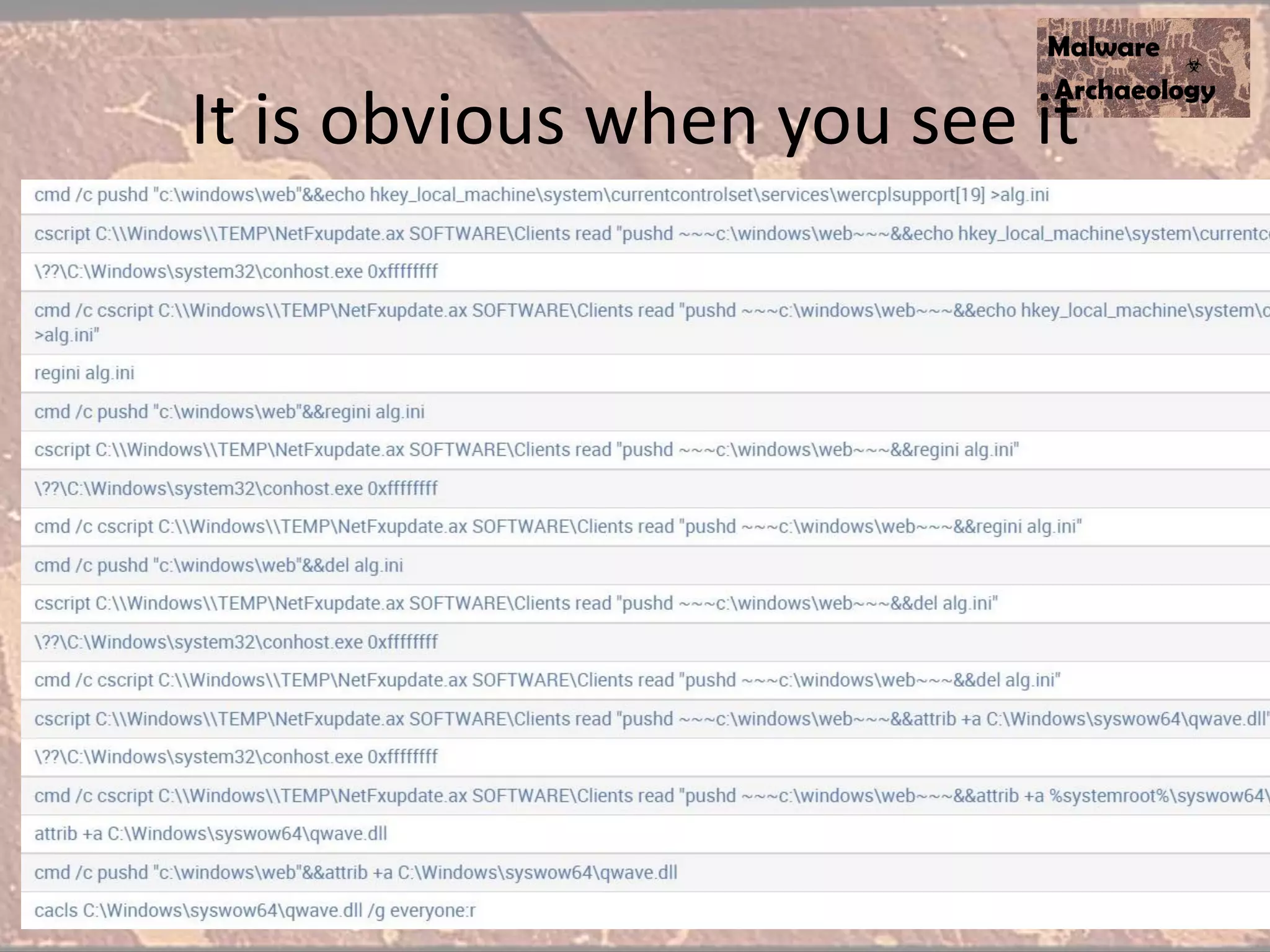
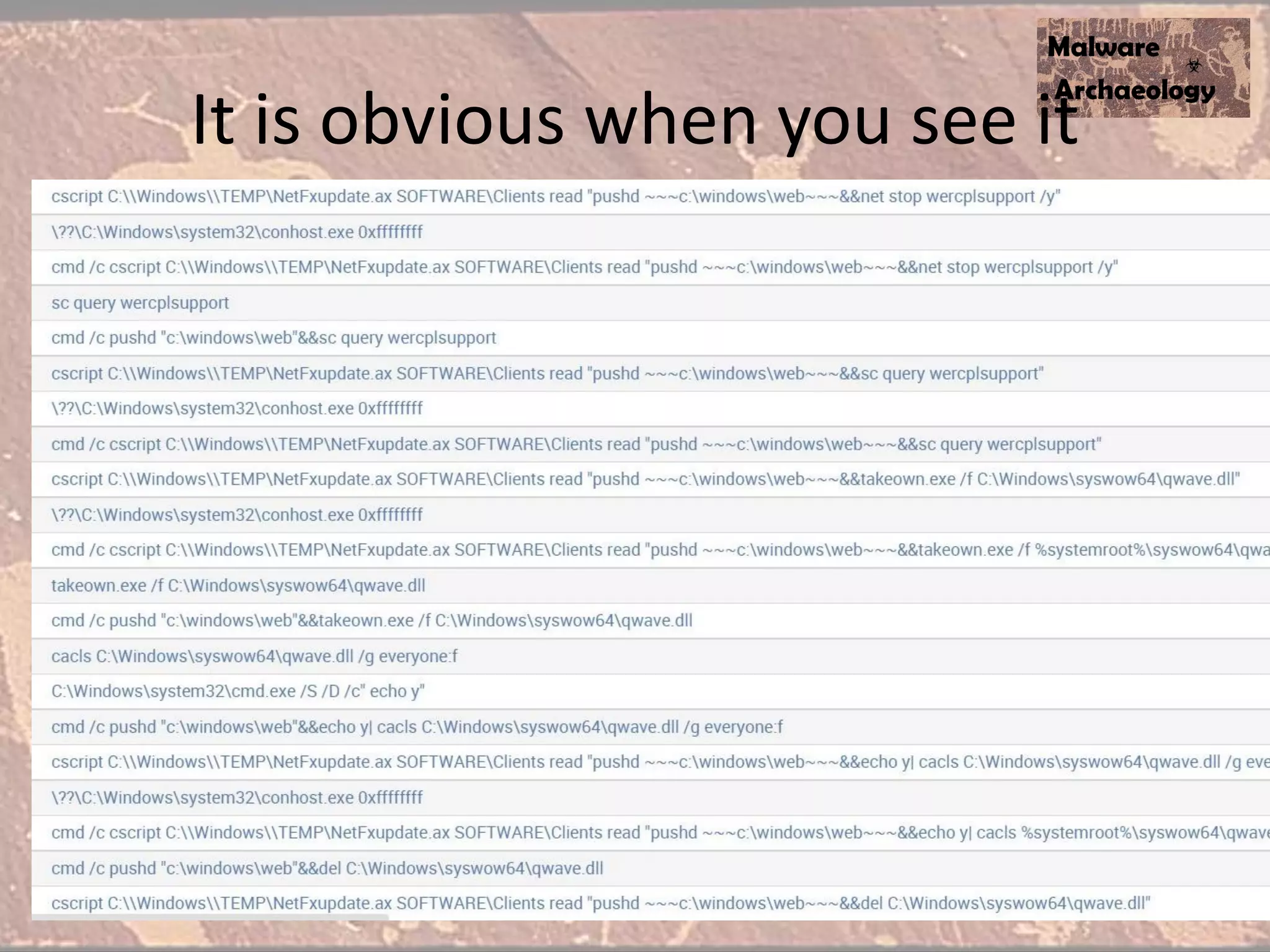
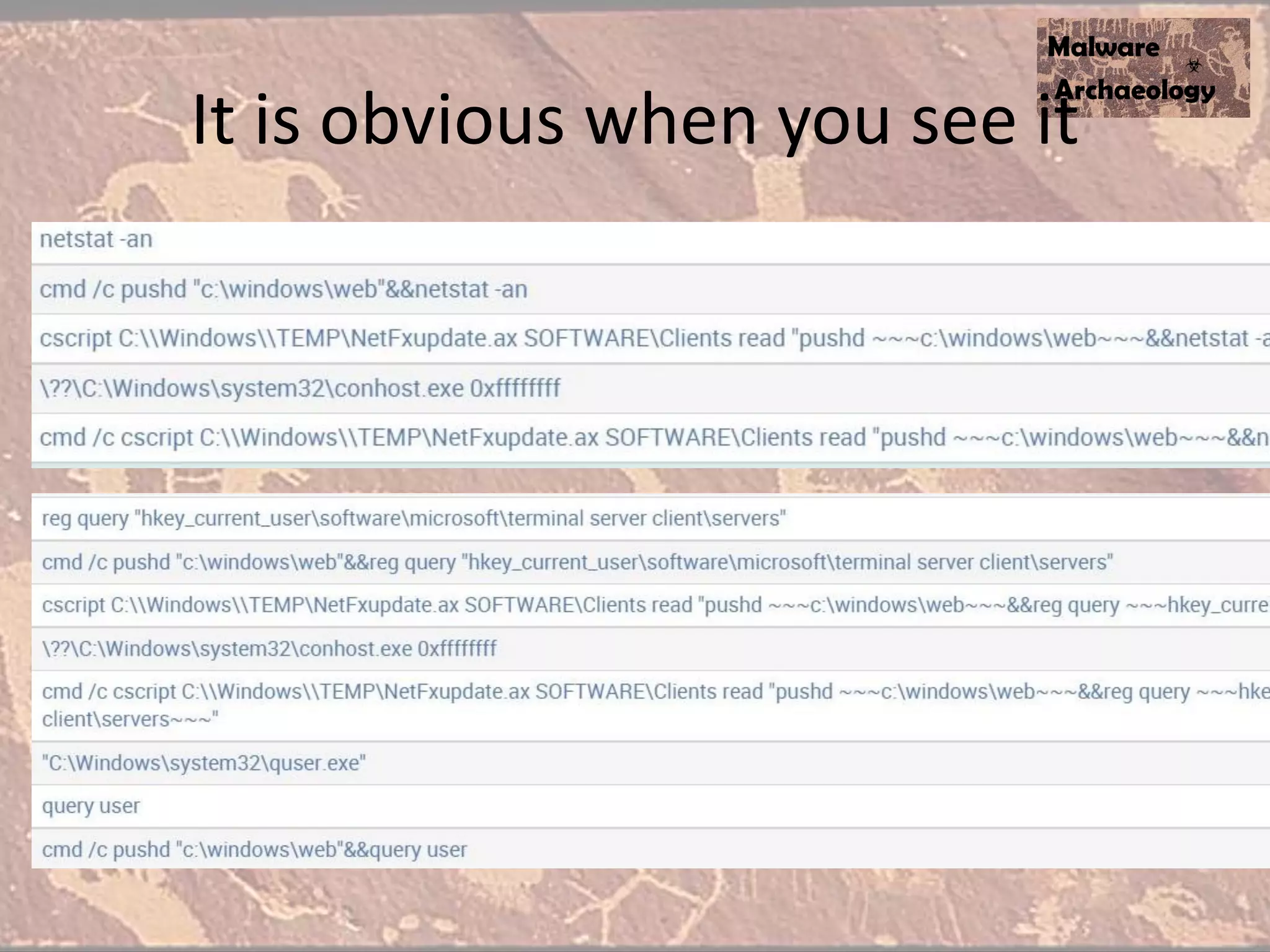
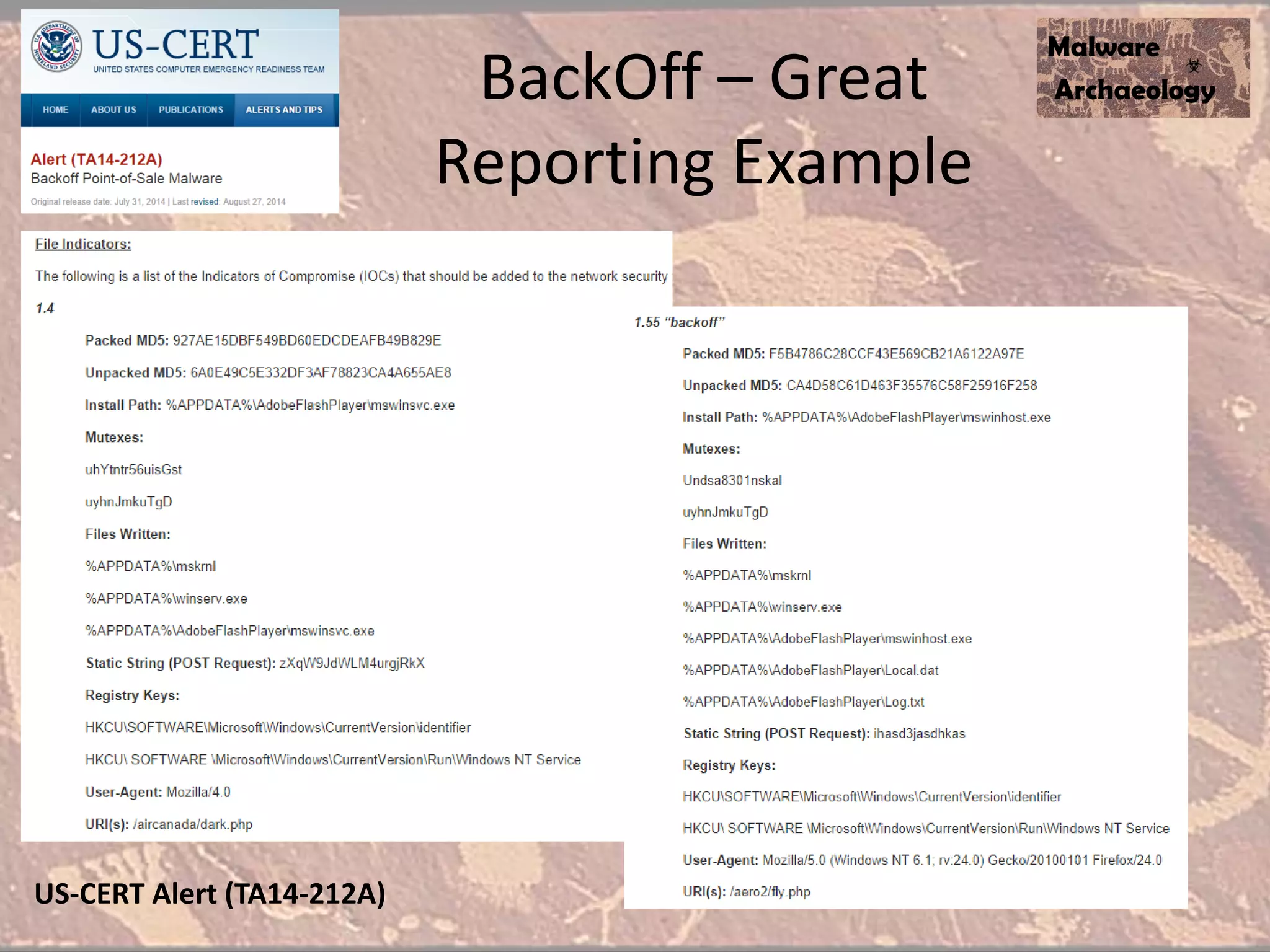
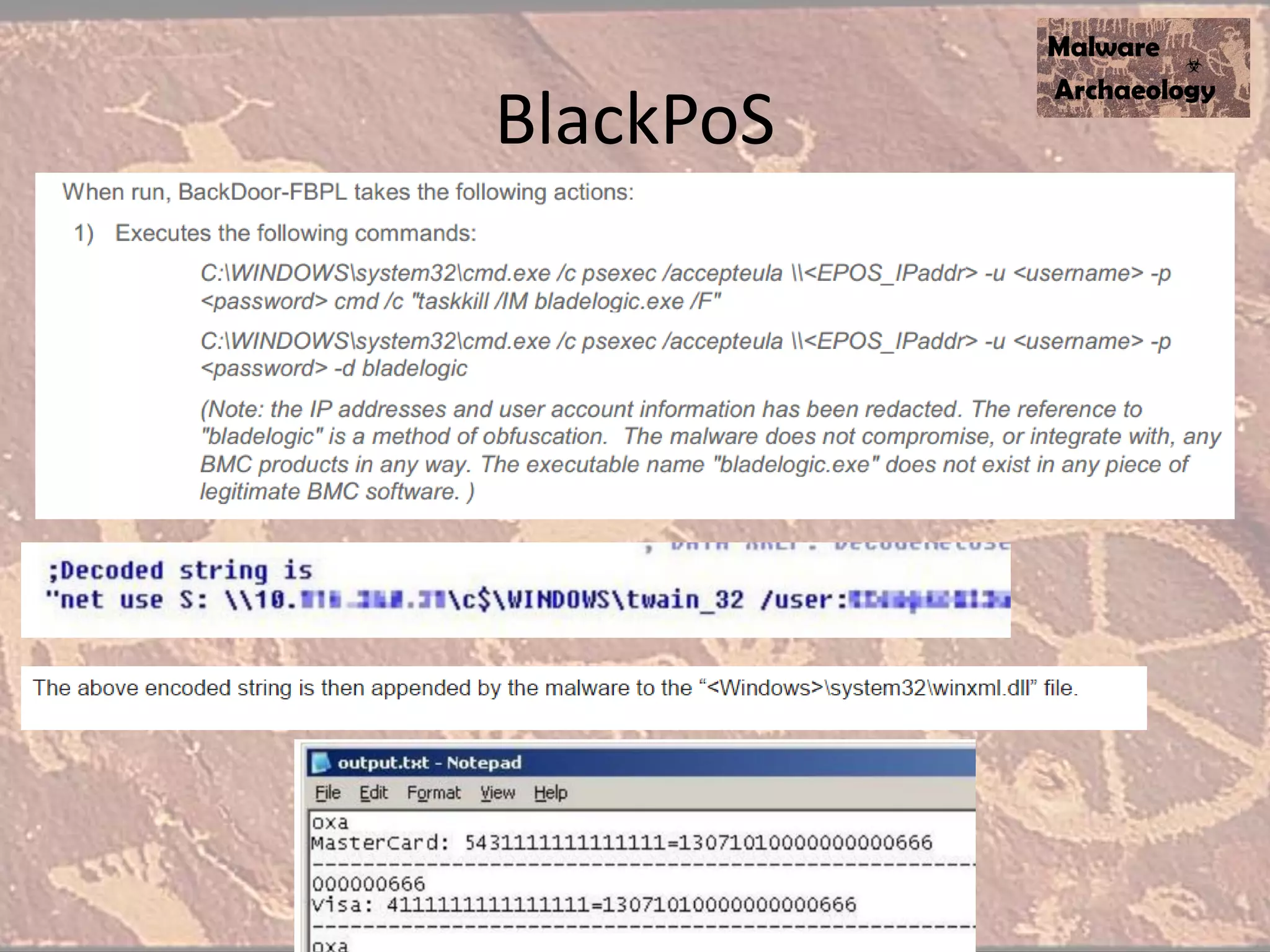
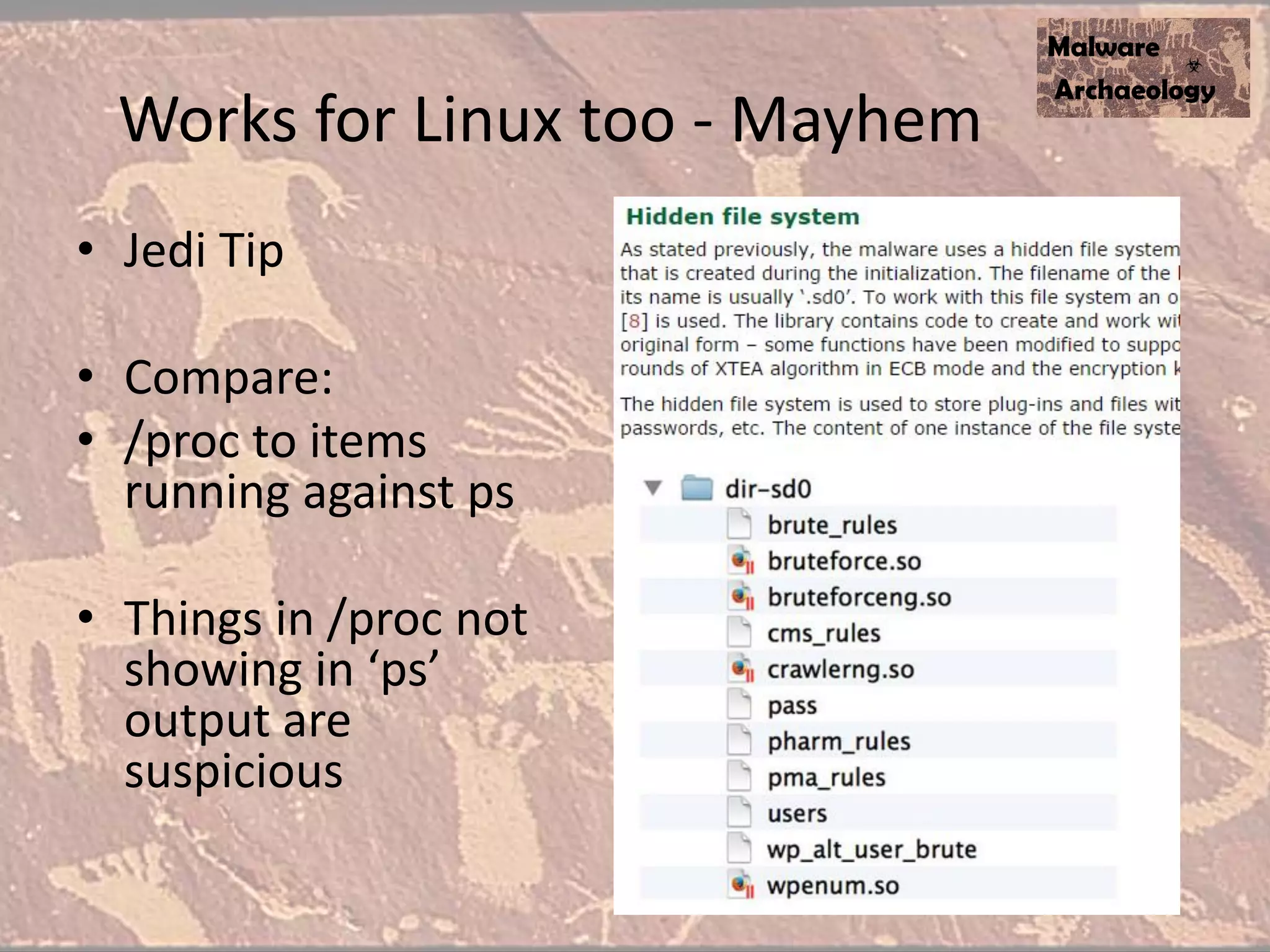
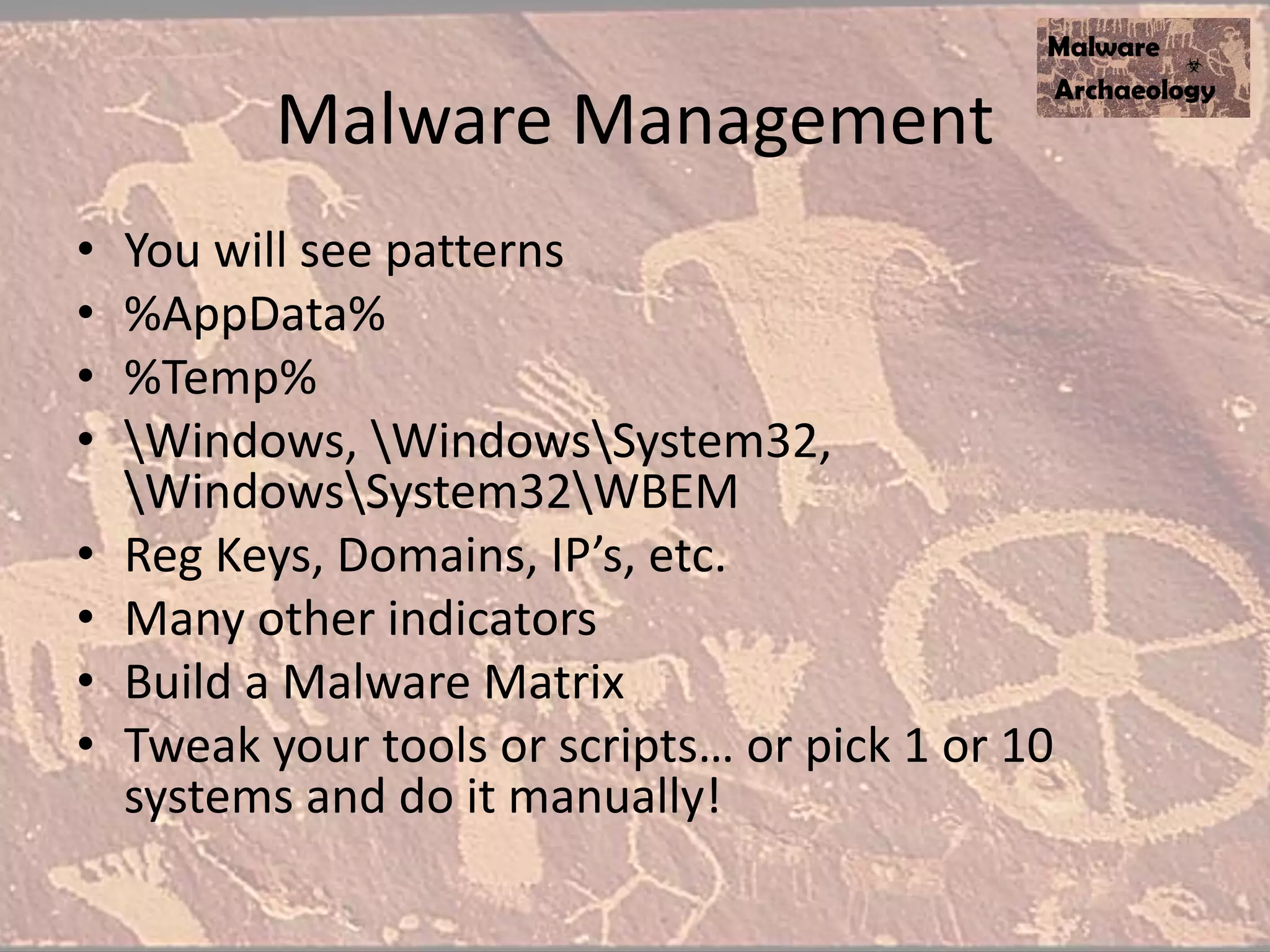
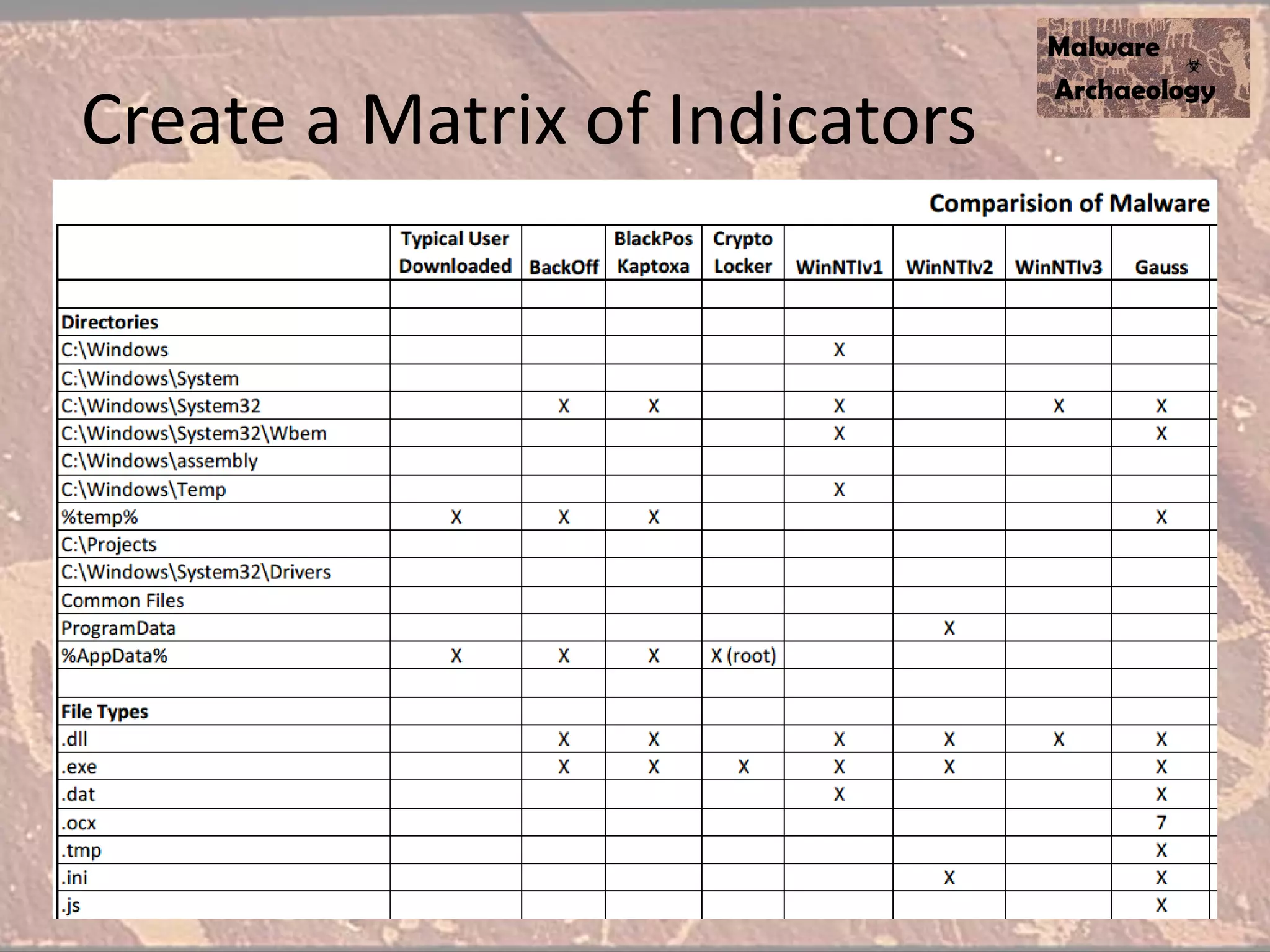
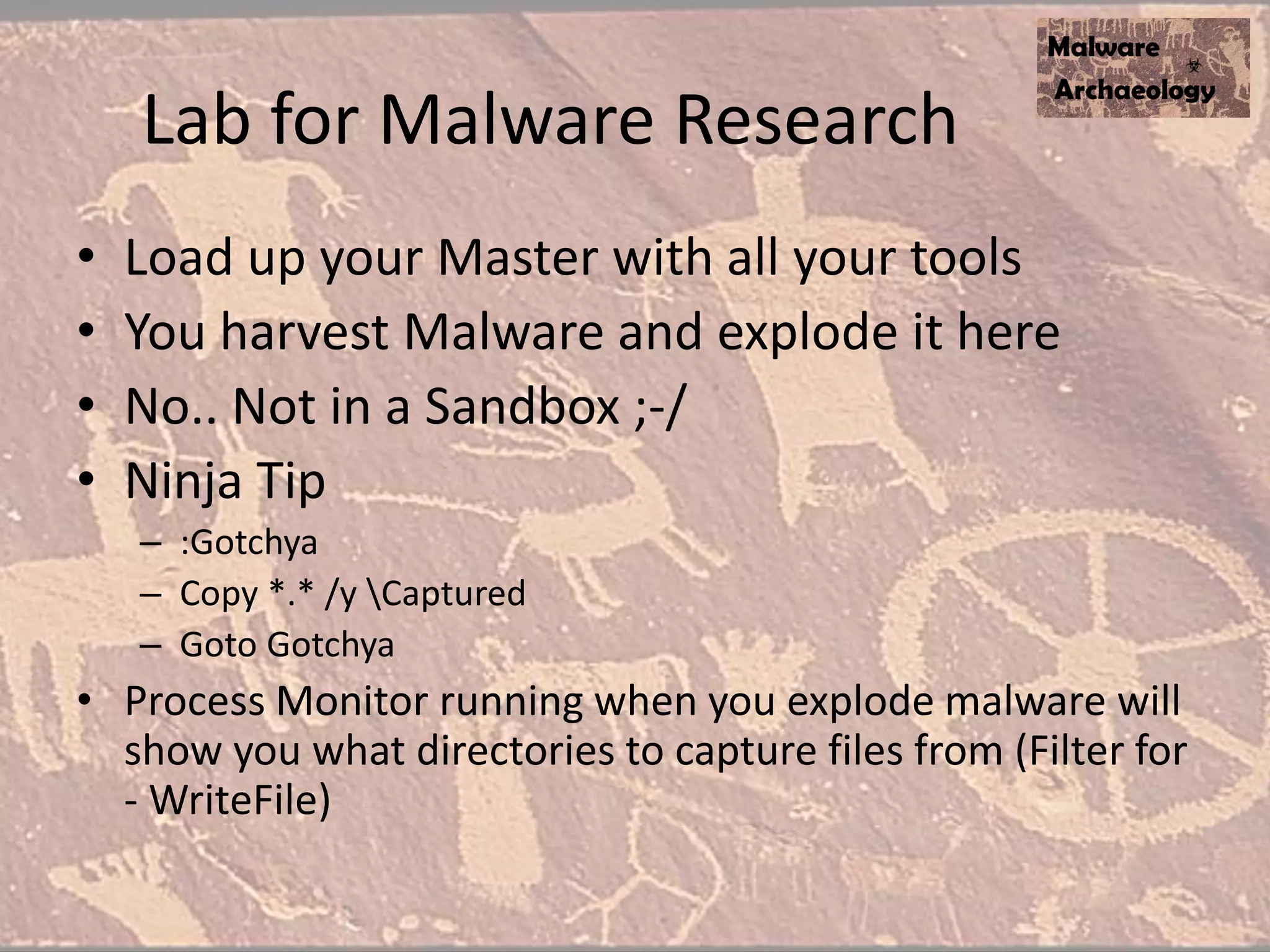
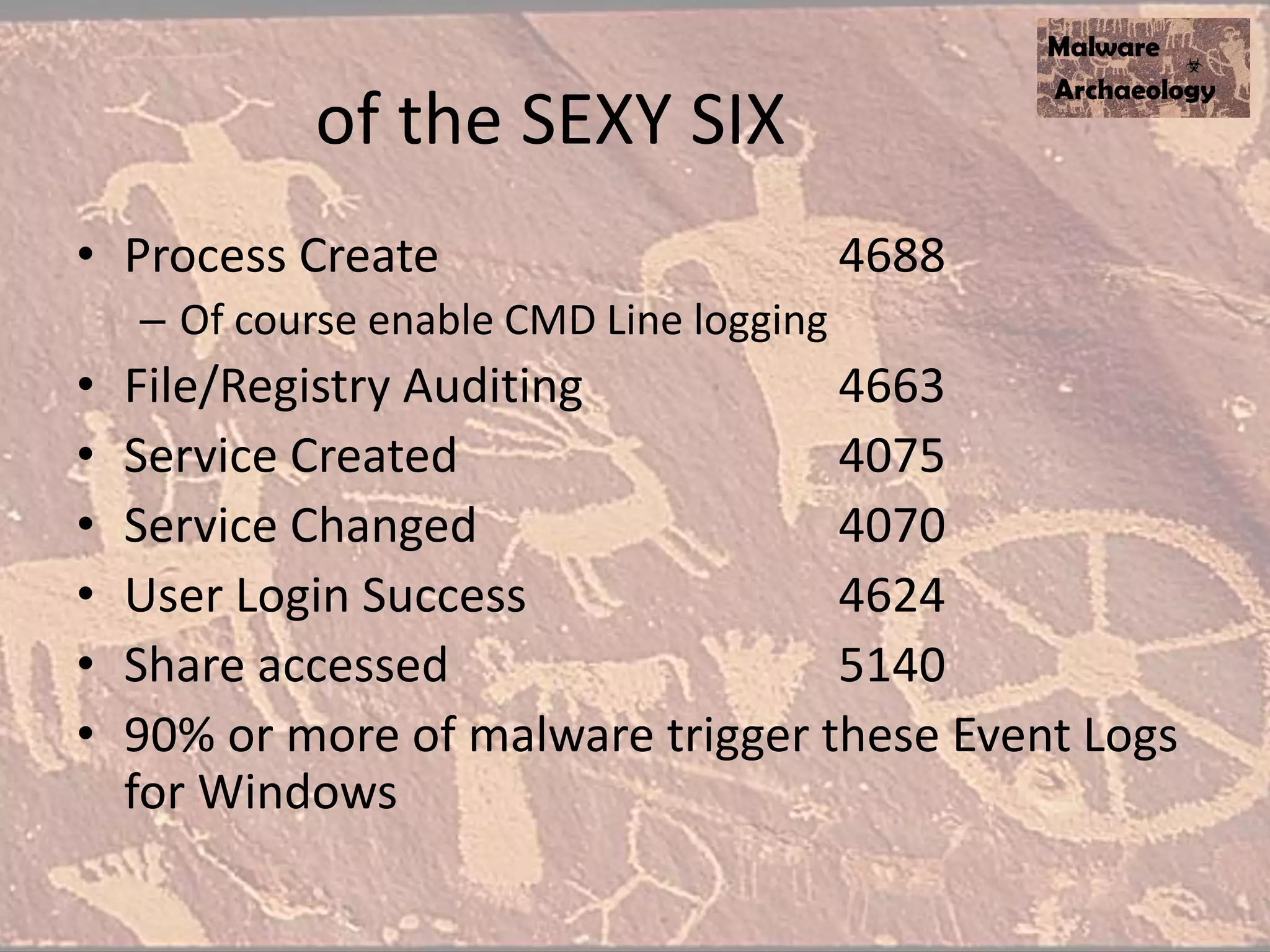
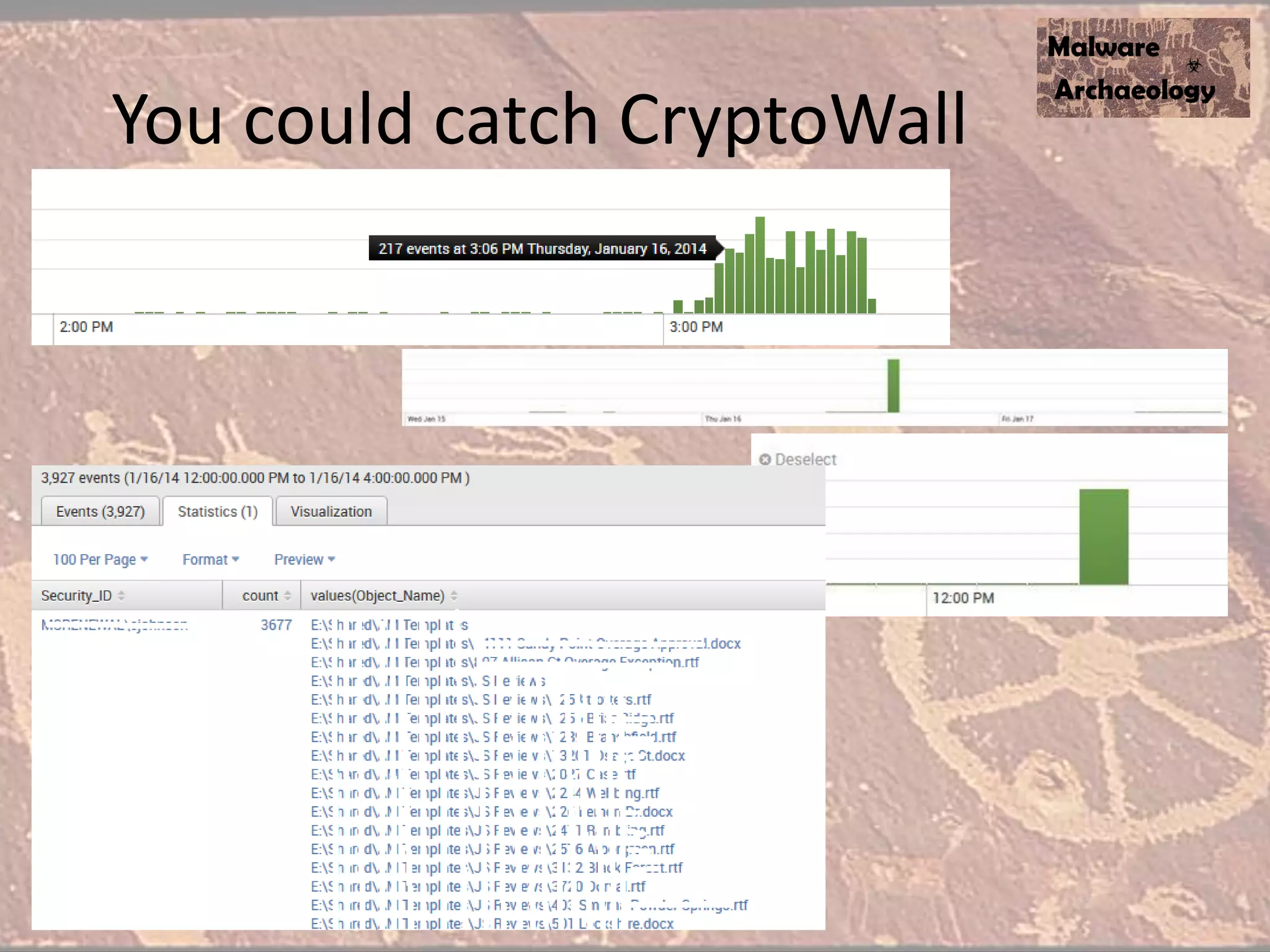
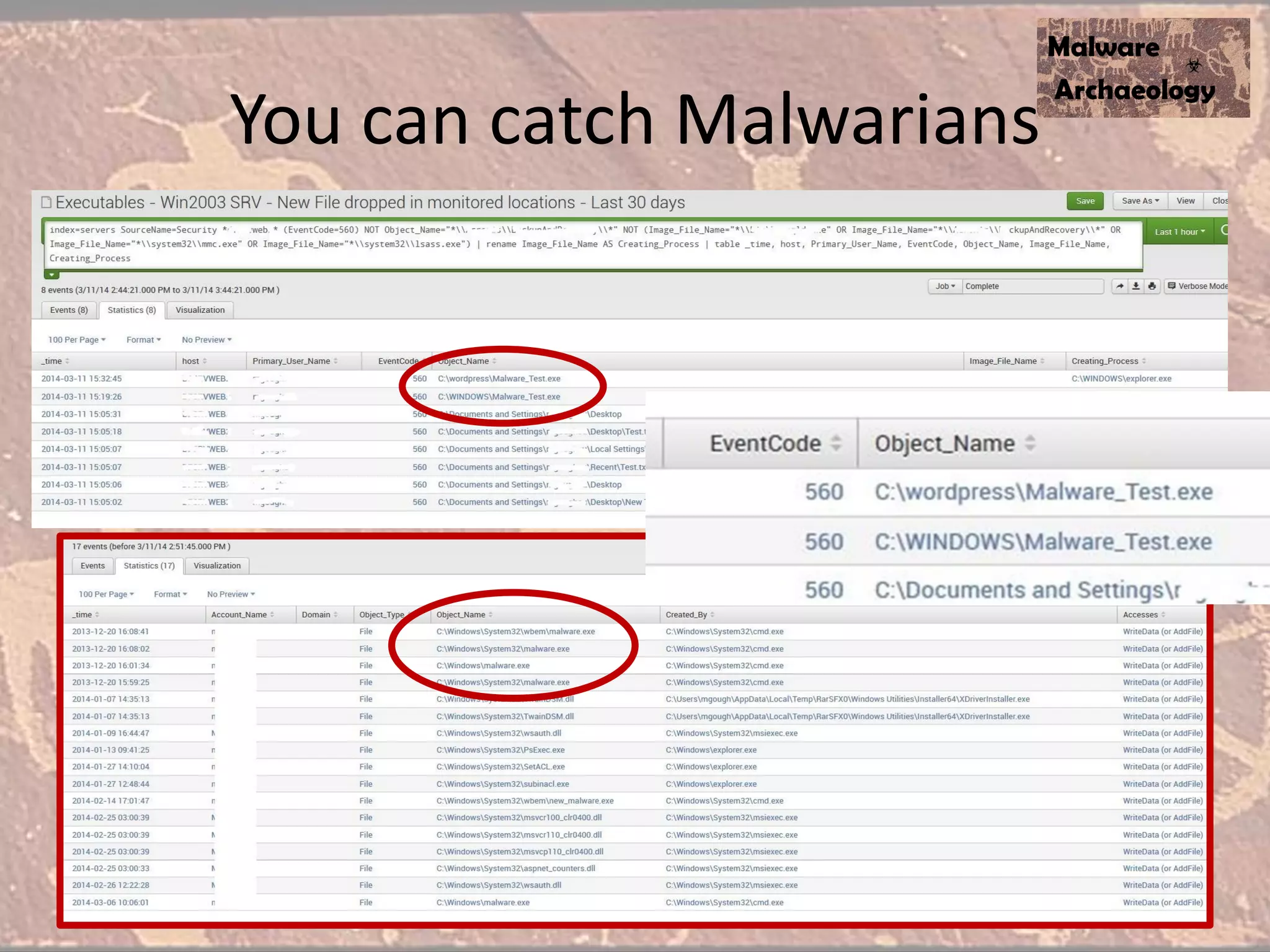
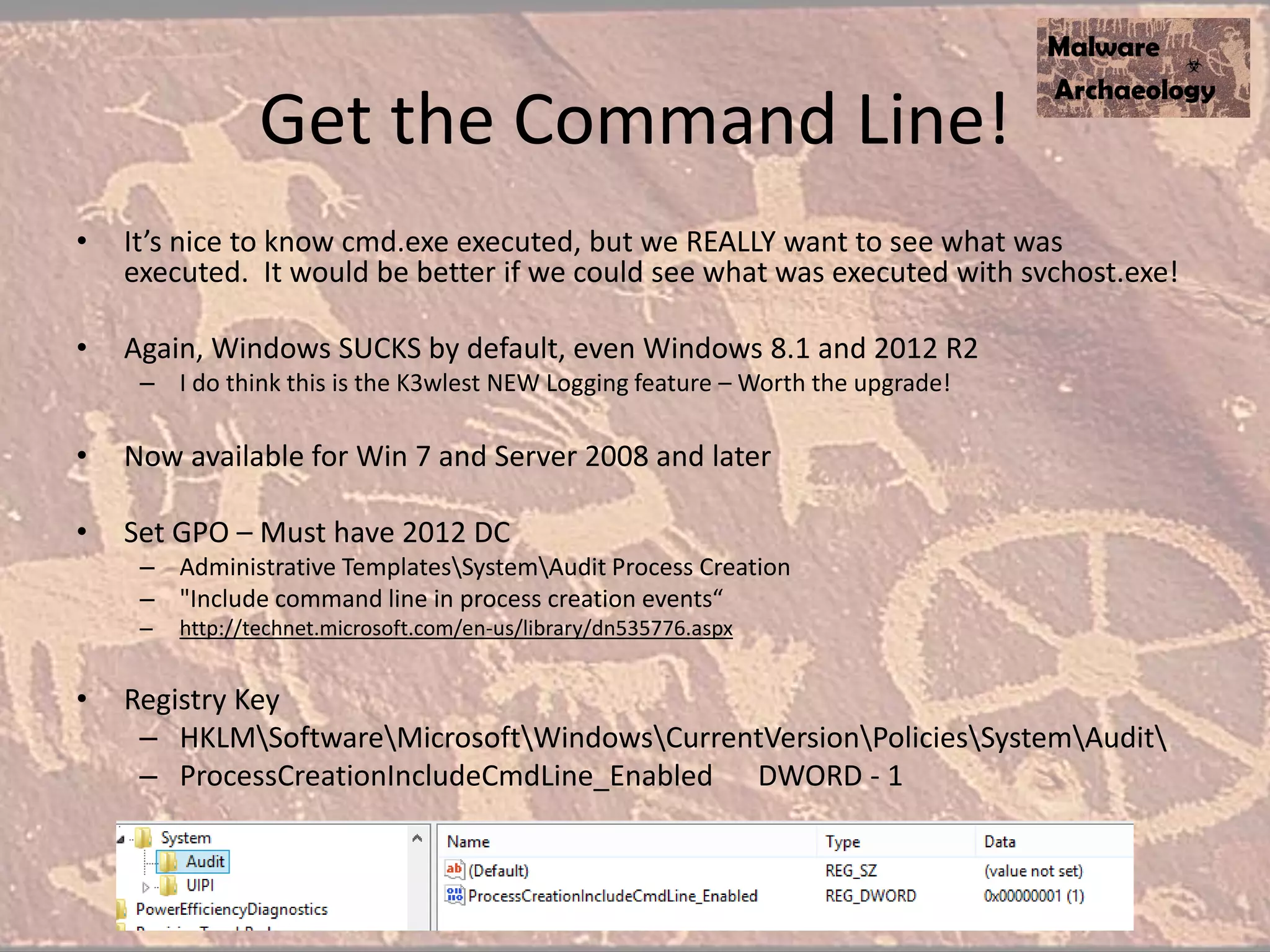
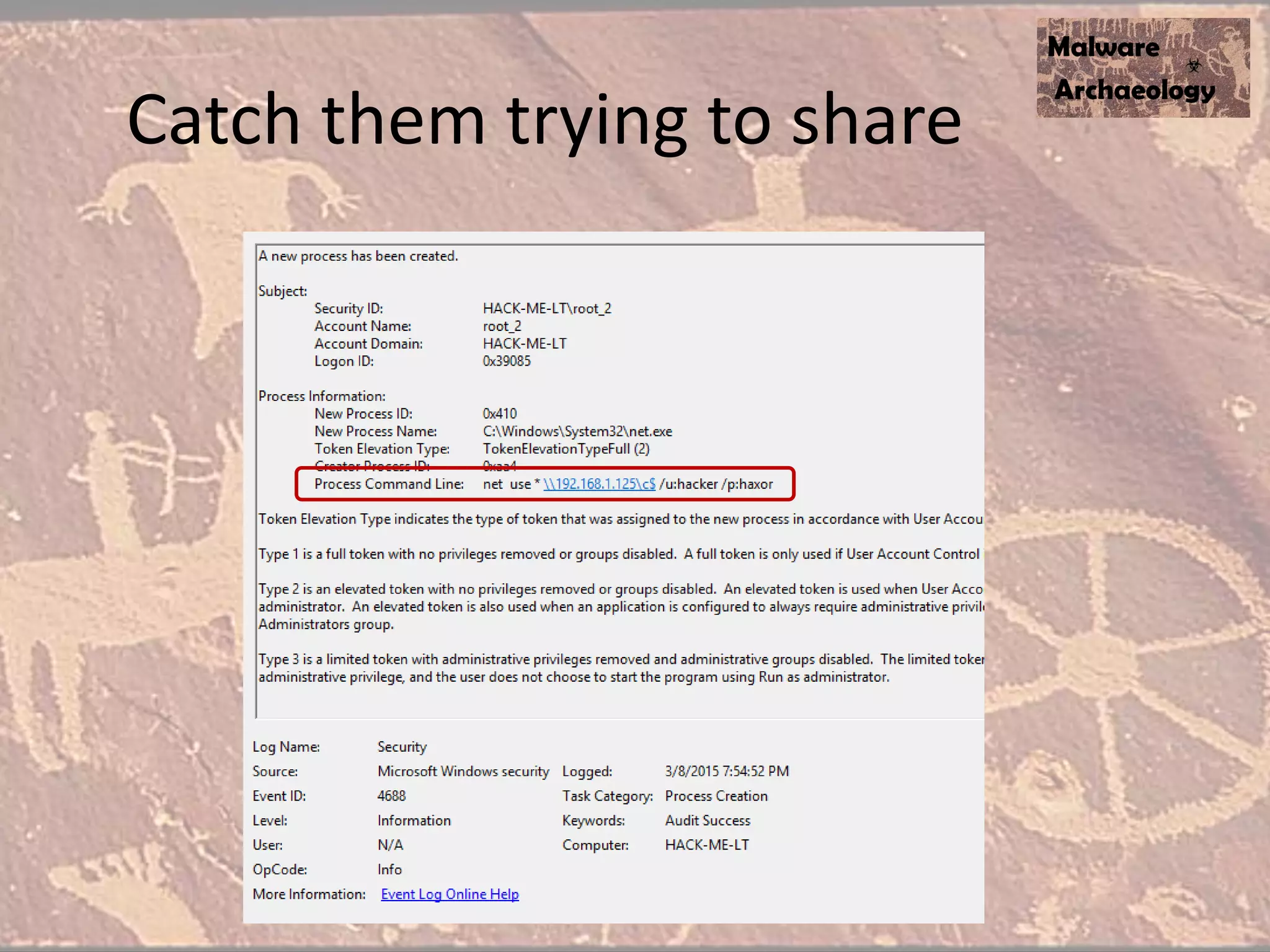
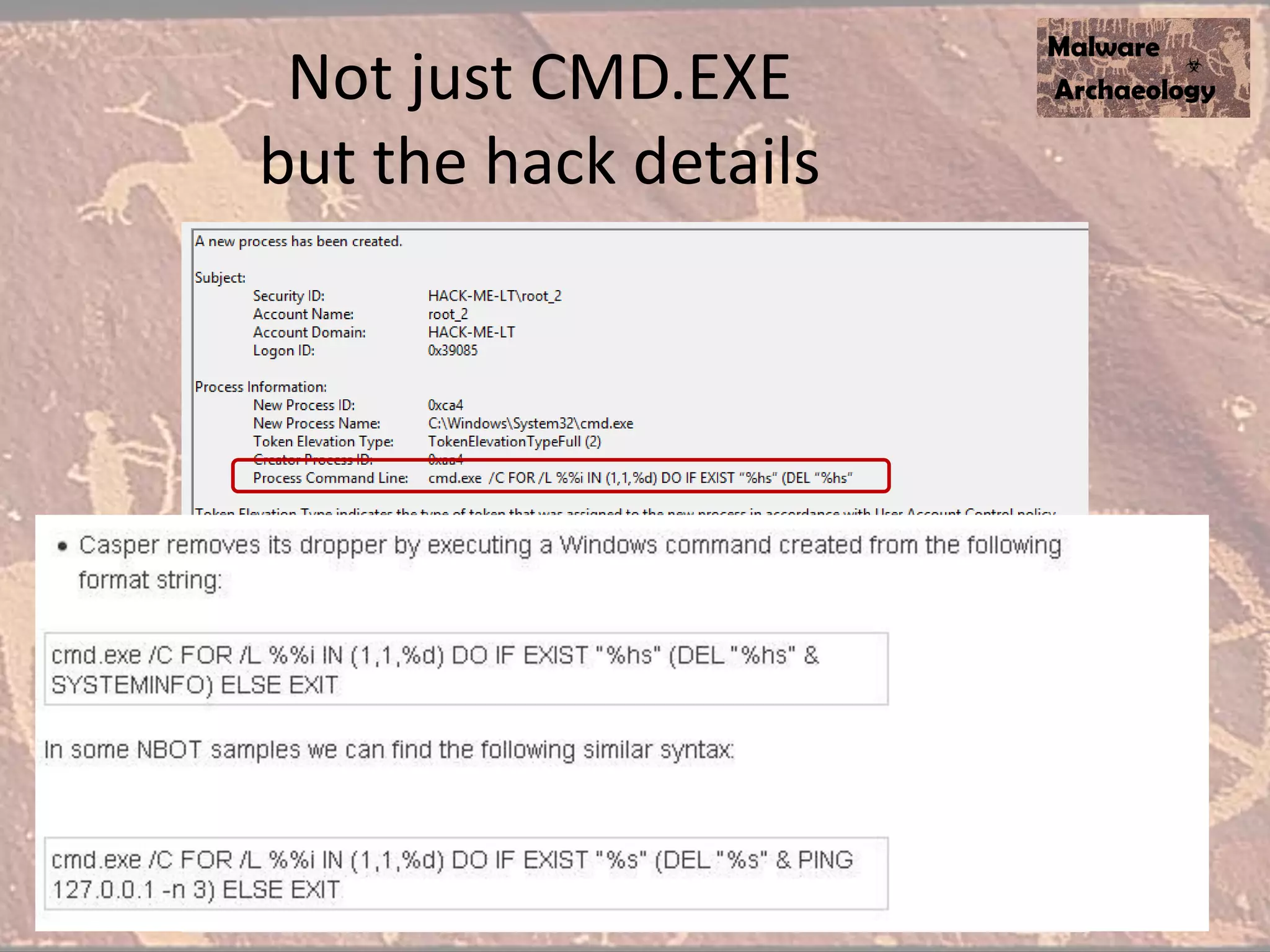
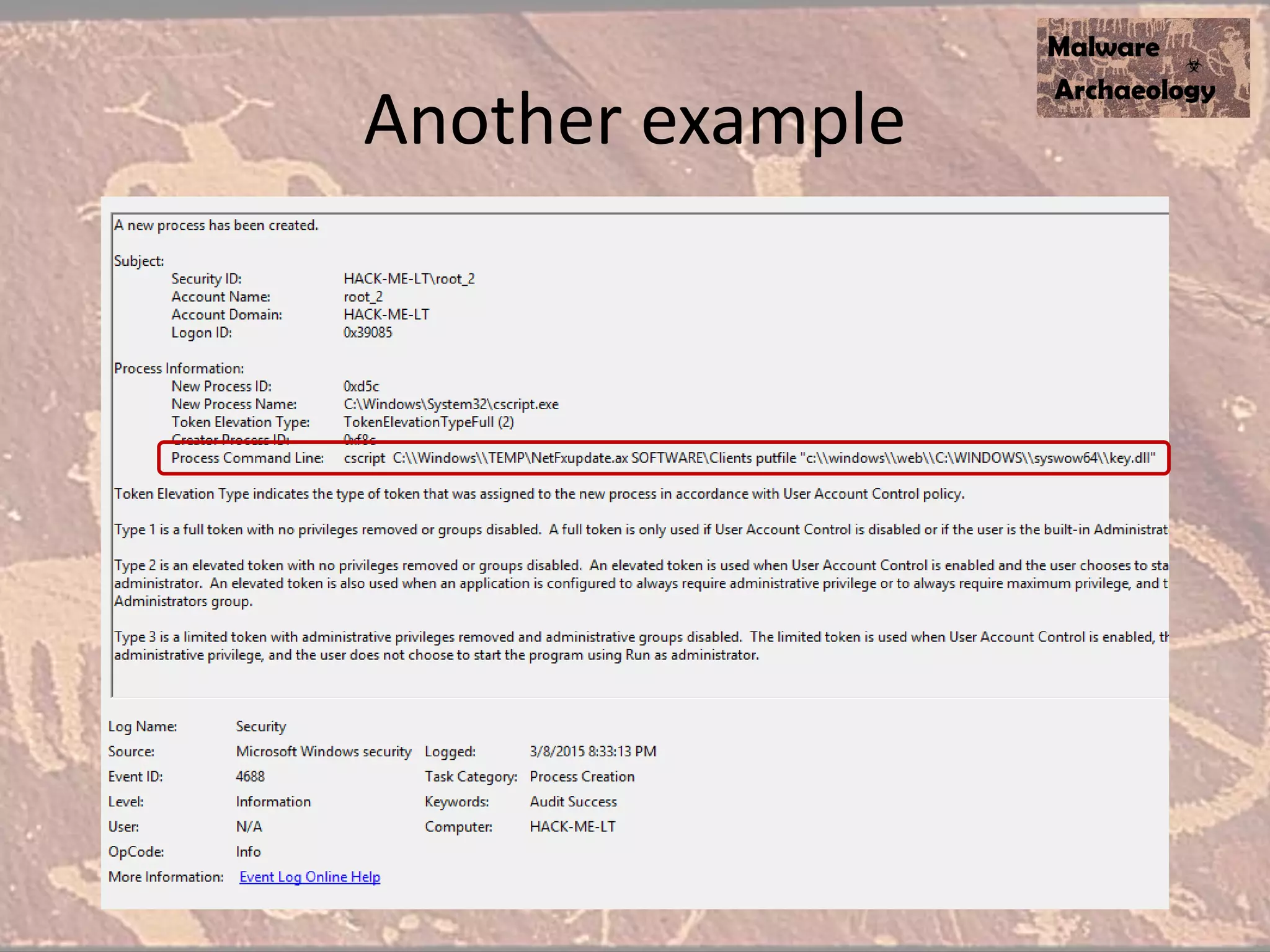
The document discusses how to detect malware through effective logging. It recommends enabling command line logging for events like cmd.exe, powershell, and other processes to see details of malware behavior. The speaker advocates building a "malware matrix" of indicators and monitoring important log events. Effective logging of files, registry, network connections and other activities on internet-facing systems can help detect malware, as demonstrated by the speaker's analysis of real world advanced persistent threats. Logs are crucial for both incident response and prevention when properly configured.














![Enable Powershell command line
• It’s nice to know Powershell executed, but we REALLY want to see what was executed
• Again, Windows SUCKS by default, Powershell v2
• Details on setting PowerShell Preference variables
– http://technet.microsoft.com/en-us/library/hh847796.aspx
• Create a Default Profile for all users:
– C:WindowsSystem32WindowsPowershellv1.0
– Profile.ps1
• Add these to your default profile.ps1 file
– $LogCommandHealthEvent = $true
– $LogCommandLifecycleEvent = $true
• Splunk - Inputs.conf
– # Windows platform specific input processor
– [WinEventLog://Windows PowerShell]
– disabled = 0
• Upgrade to ver 3 or ver 4
• Investigating PowerShell Attacks (DefCon & Blackhat 2014)
– Ryan Kazanciyan TECHNICAL DIRECTOR, MANDIANT
– Matt Hastings CONSULTANT, MANDIANT](https://image.slidesharecdn.com/askamalwarearchaeologistv0-150412181938-conversion-gate01/75/Ask-a-Malware-Archaeologist-30-2048.jpg)