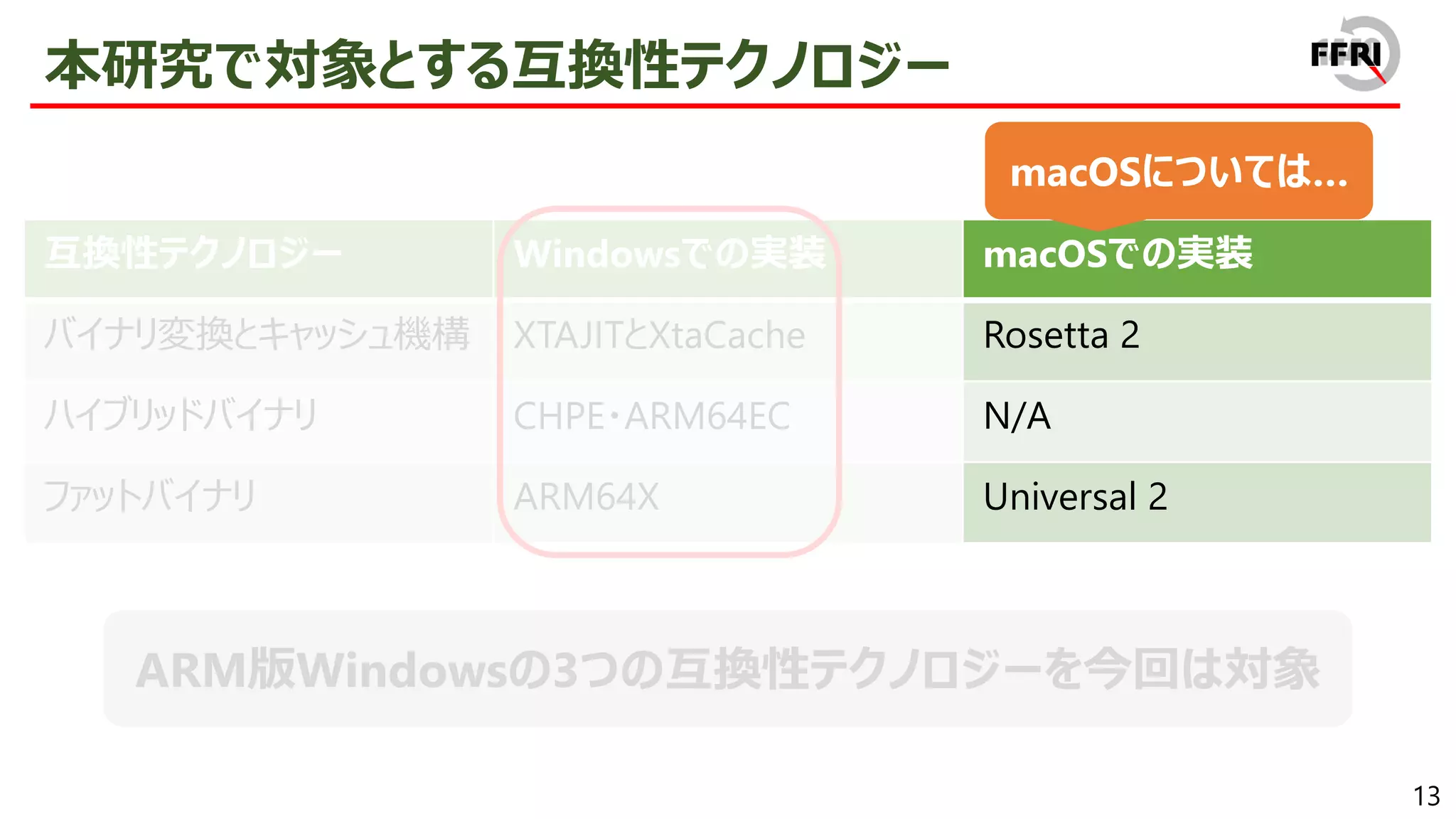
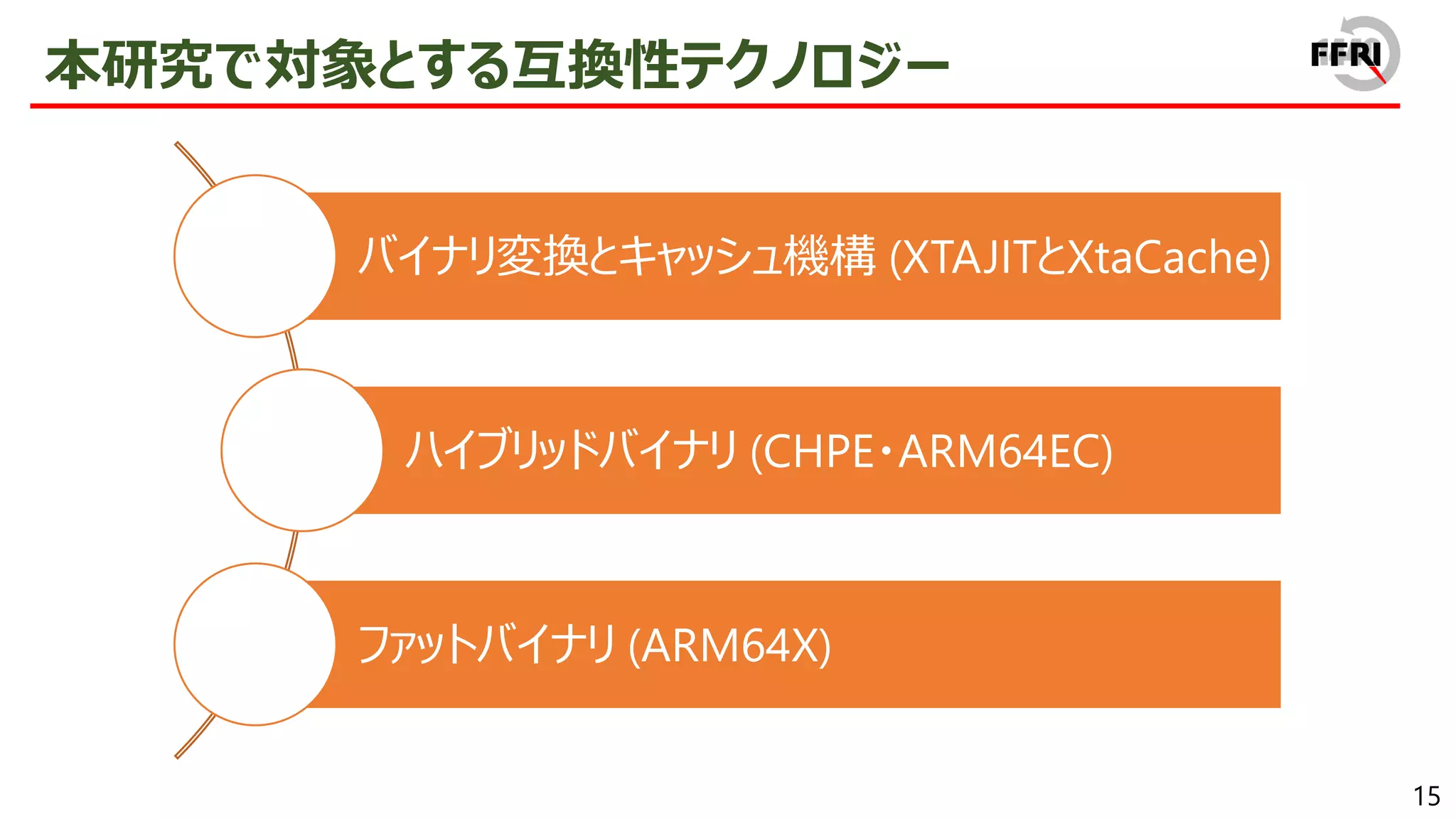
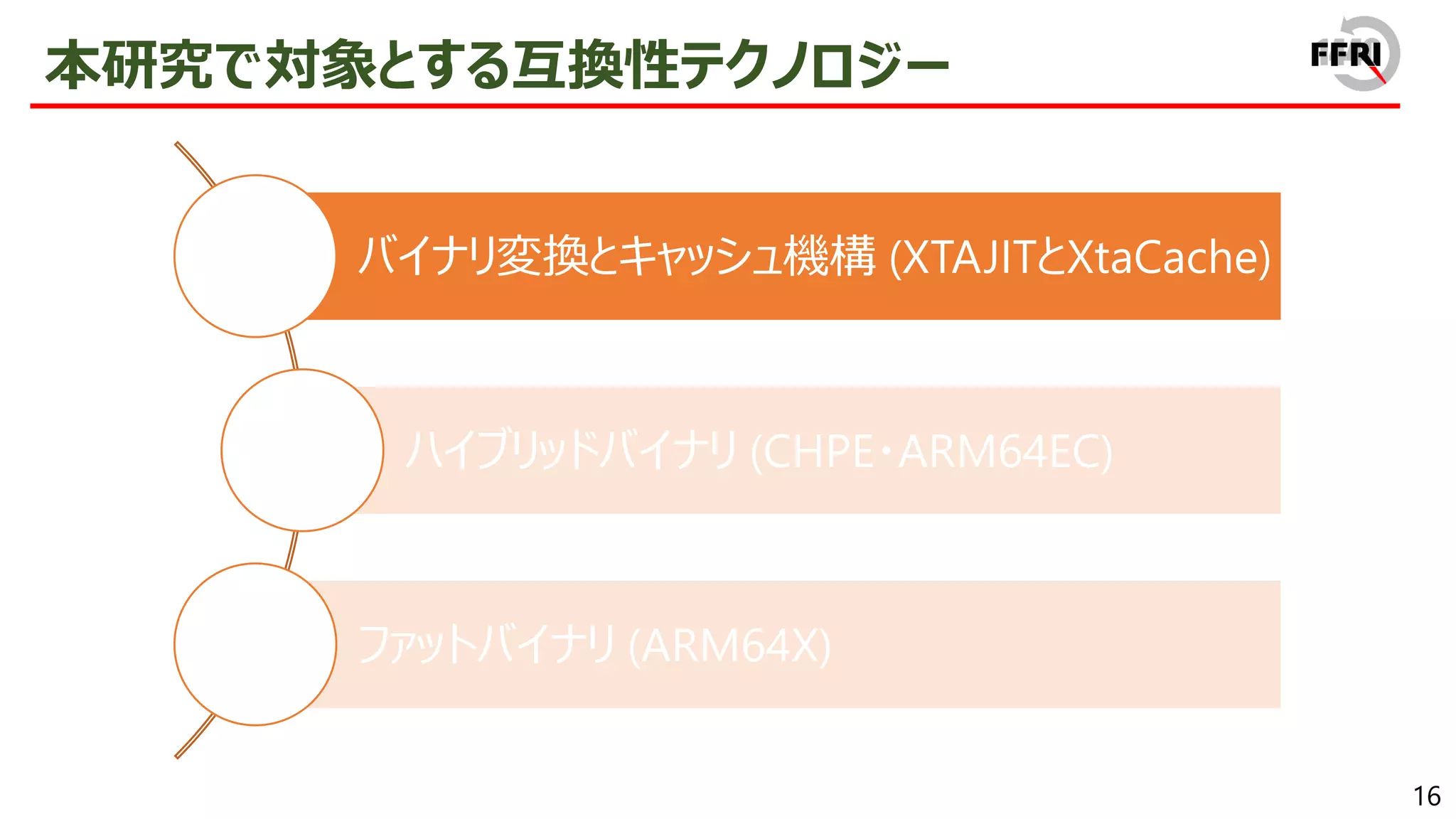
In 2017, Microsoft announced the ARM version of Windows. The number of devices with ARM version of Windows is increasing, such as Surface Pro X series and HP ENVY x2, and it is gradually becoming popular.
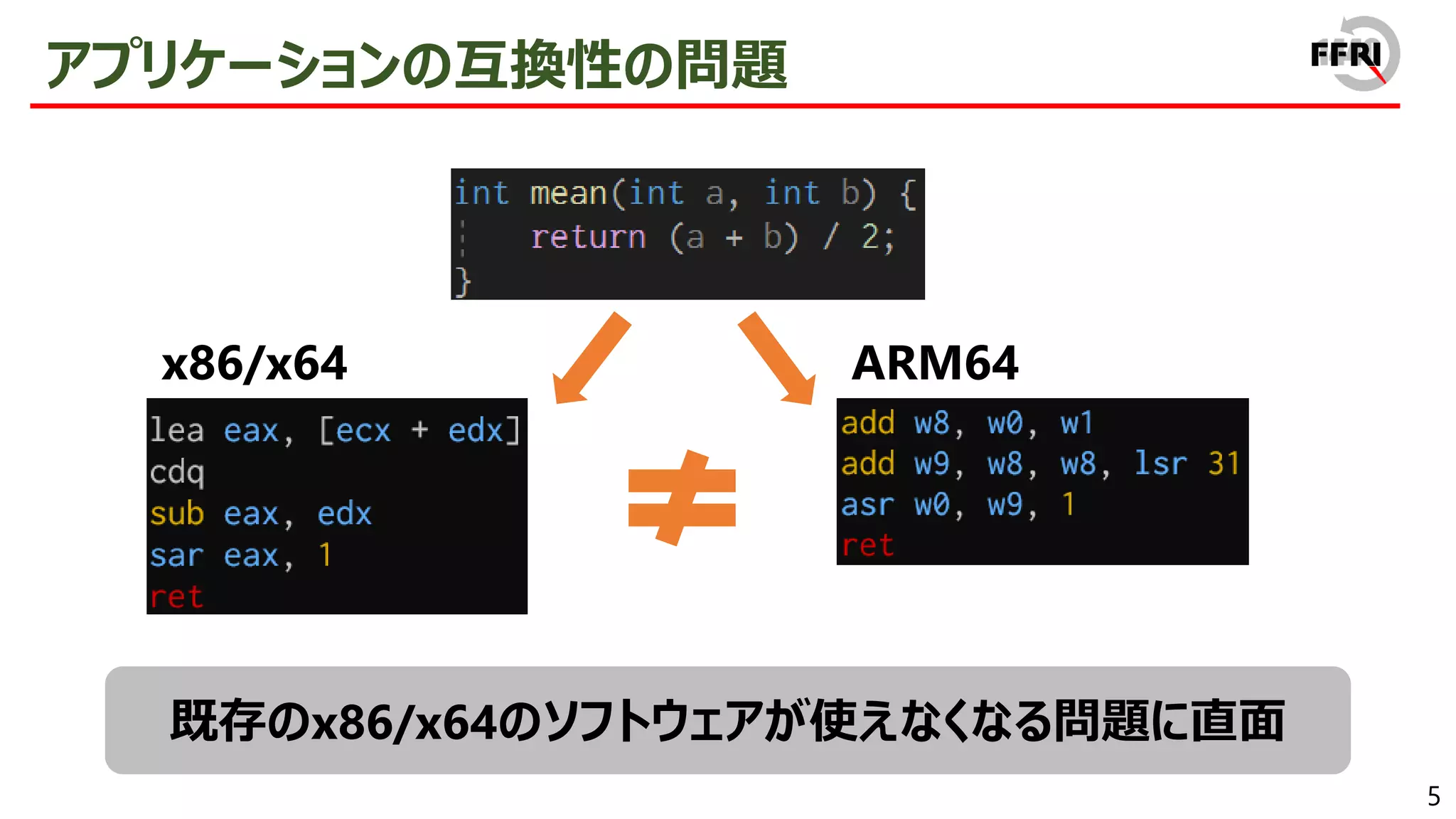
When using these ARM devices, there is a compatibility issue that existing x86/x64 applications cannot be used.
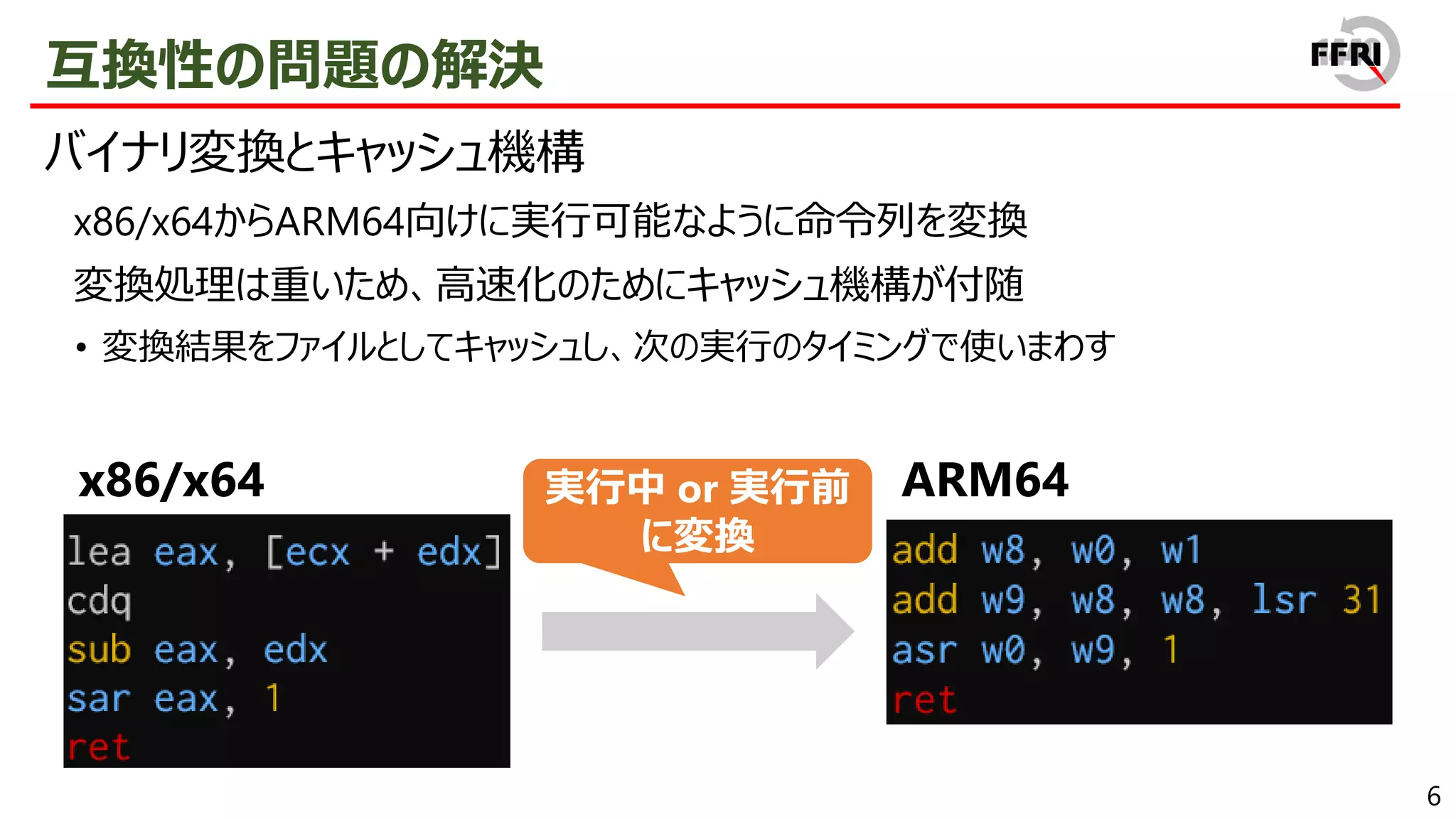
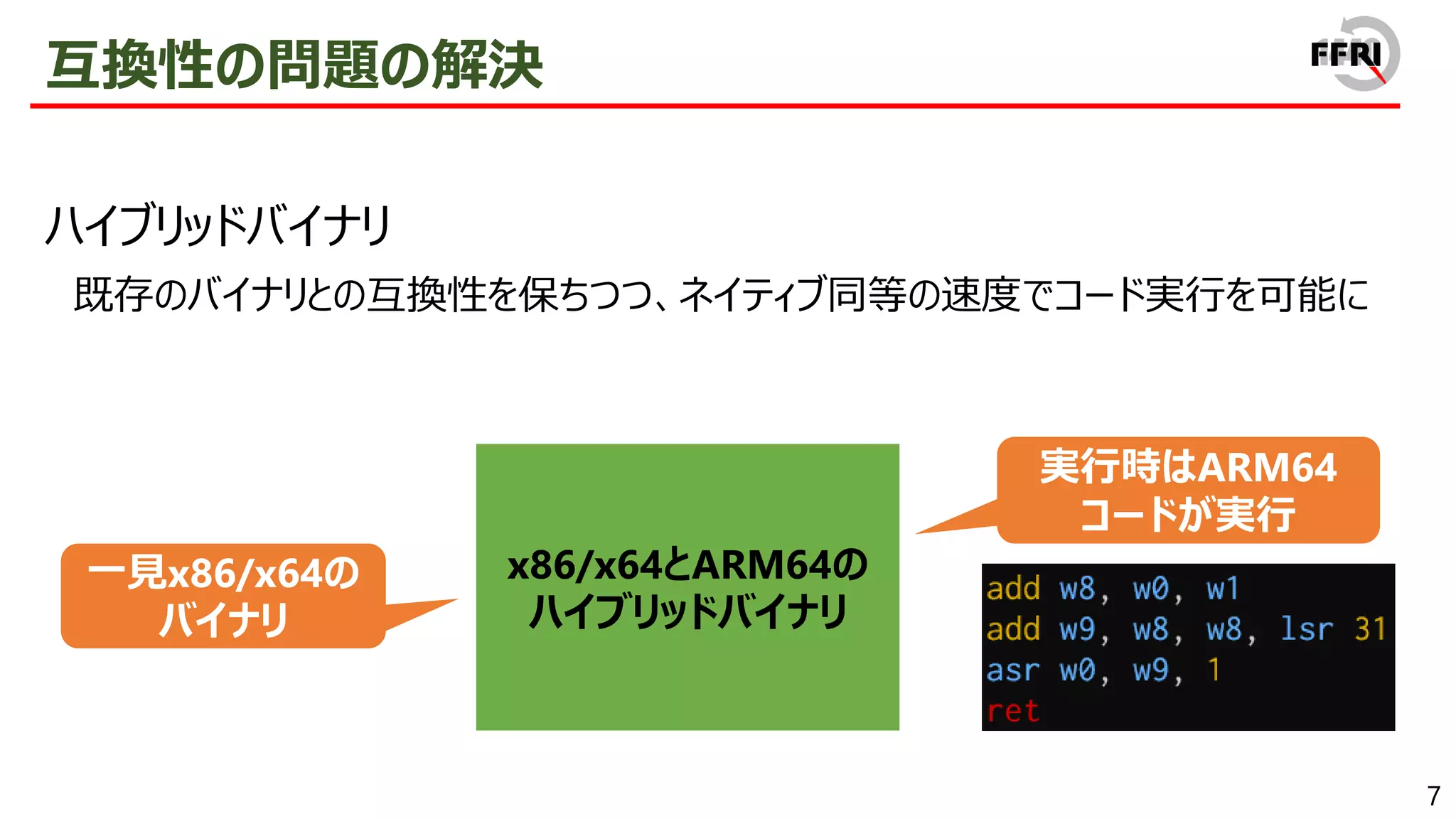
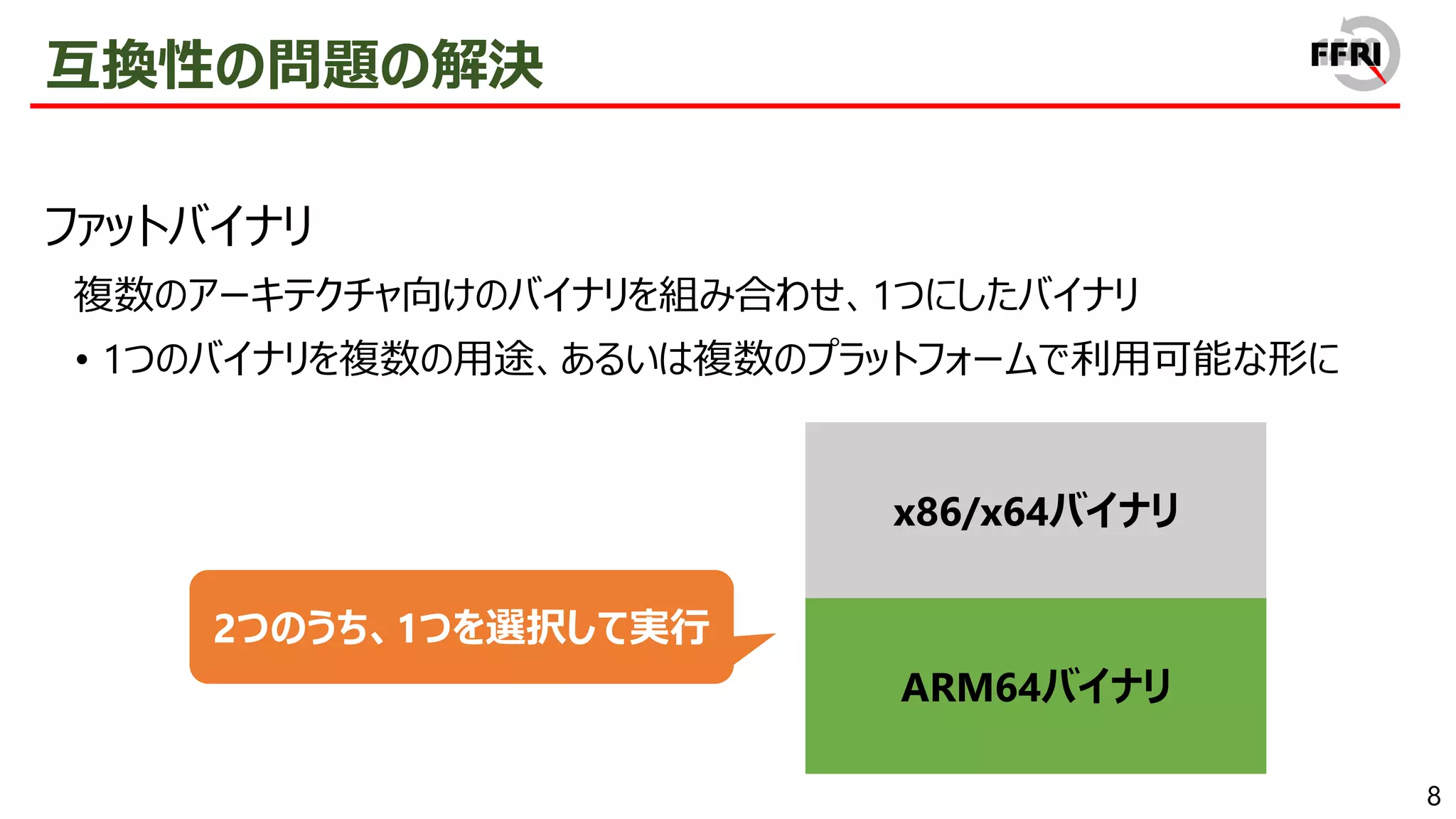
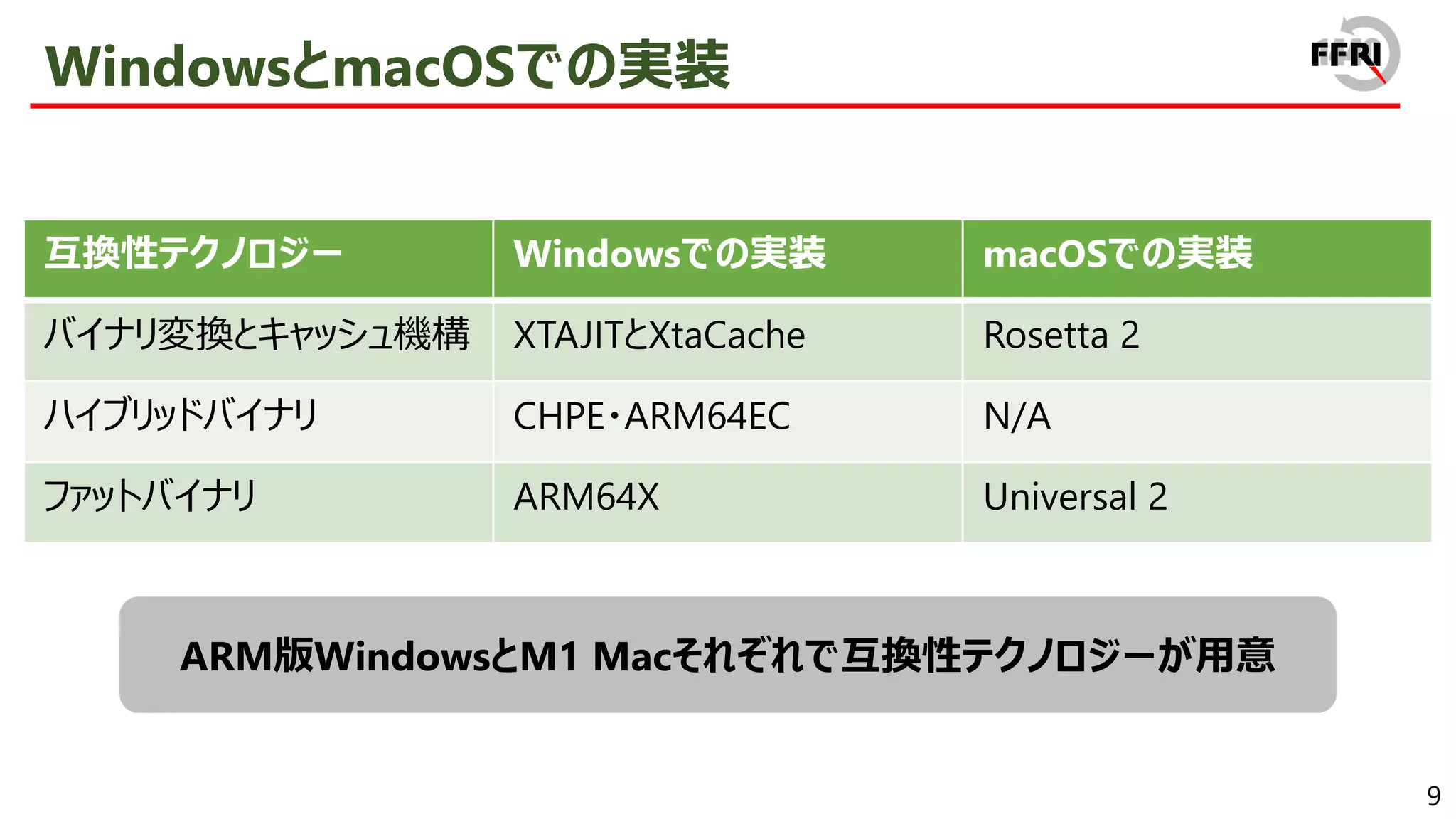
However, this problem has been addressed by providing x86/x64 emulation capabilities. In recent years, ARM64EC has been announced, allowing for the gradual migration of x64 applications to ARM. The aggressive introduction of these compatibility technologies is a sign of Microsoft's strong will to promote the ARM version of Windows.
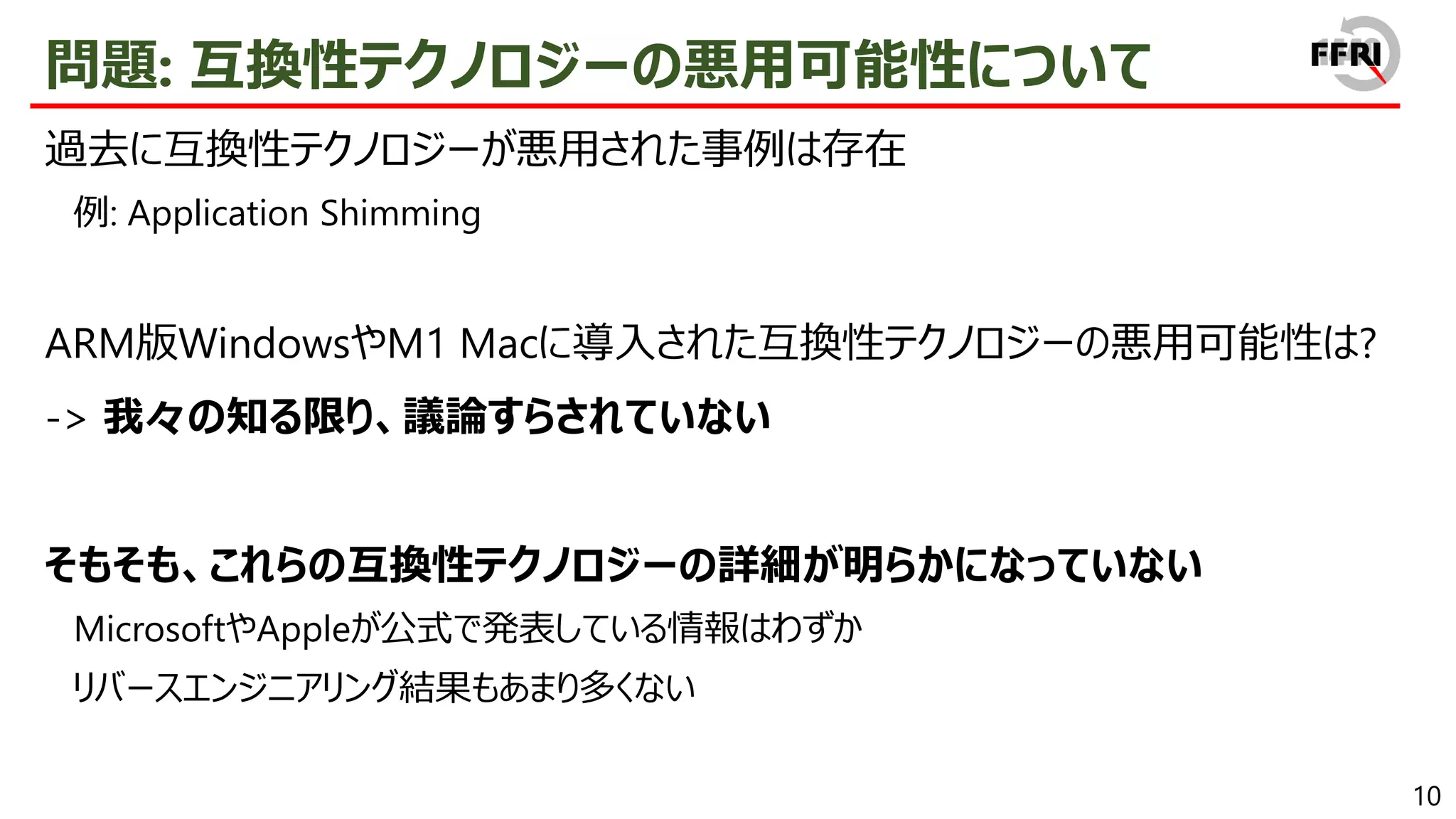
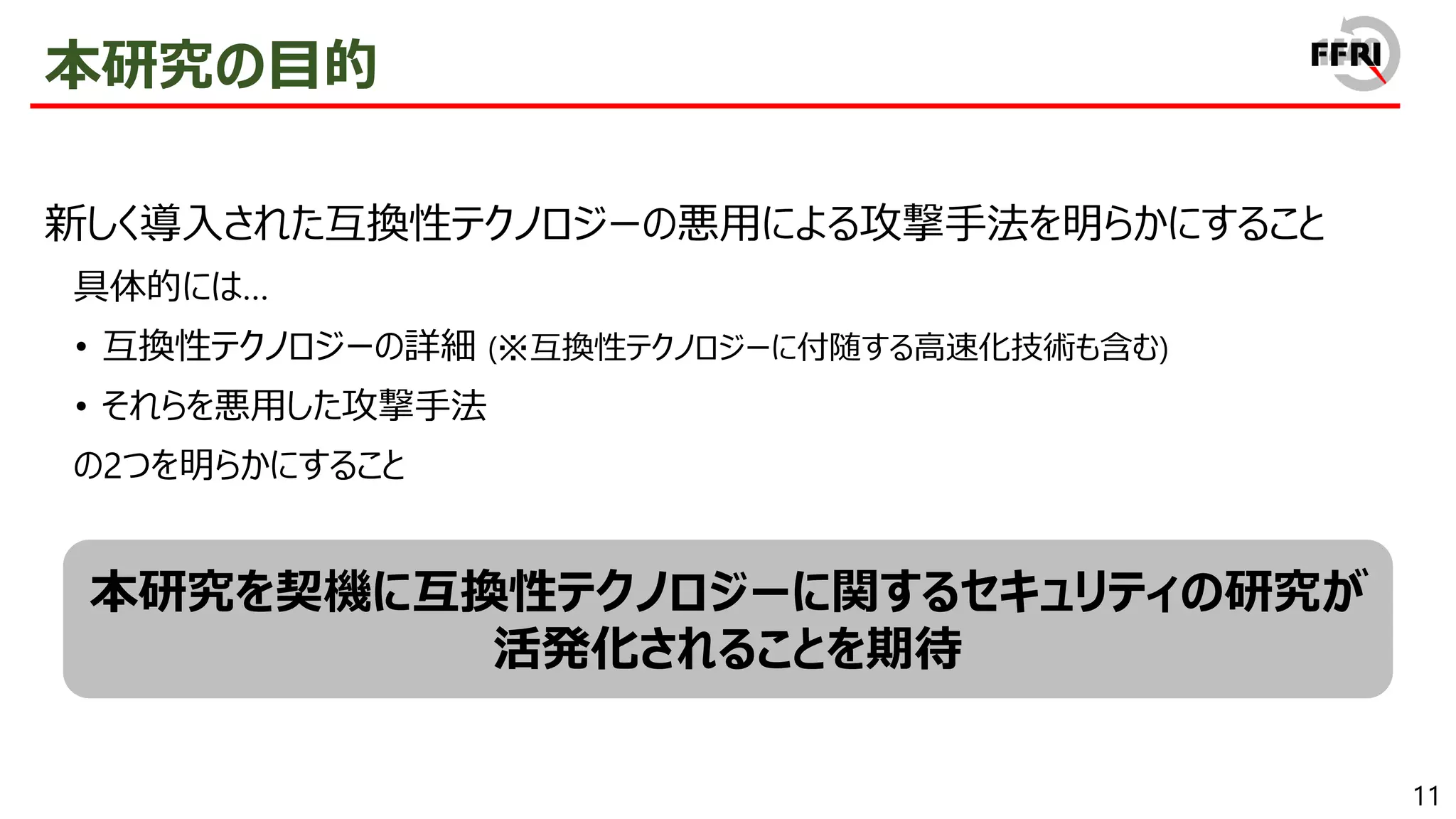
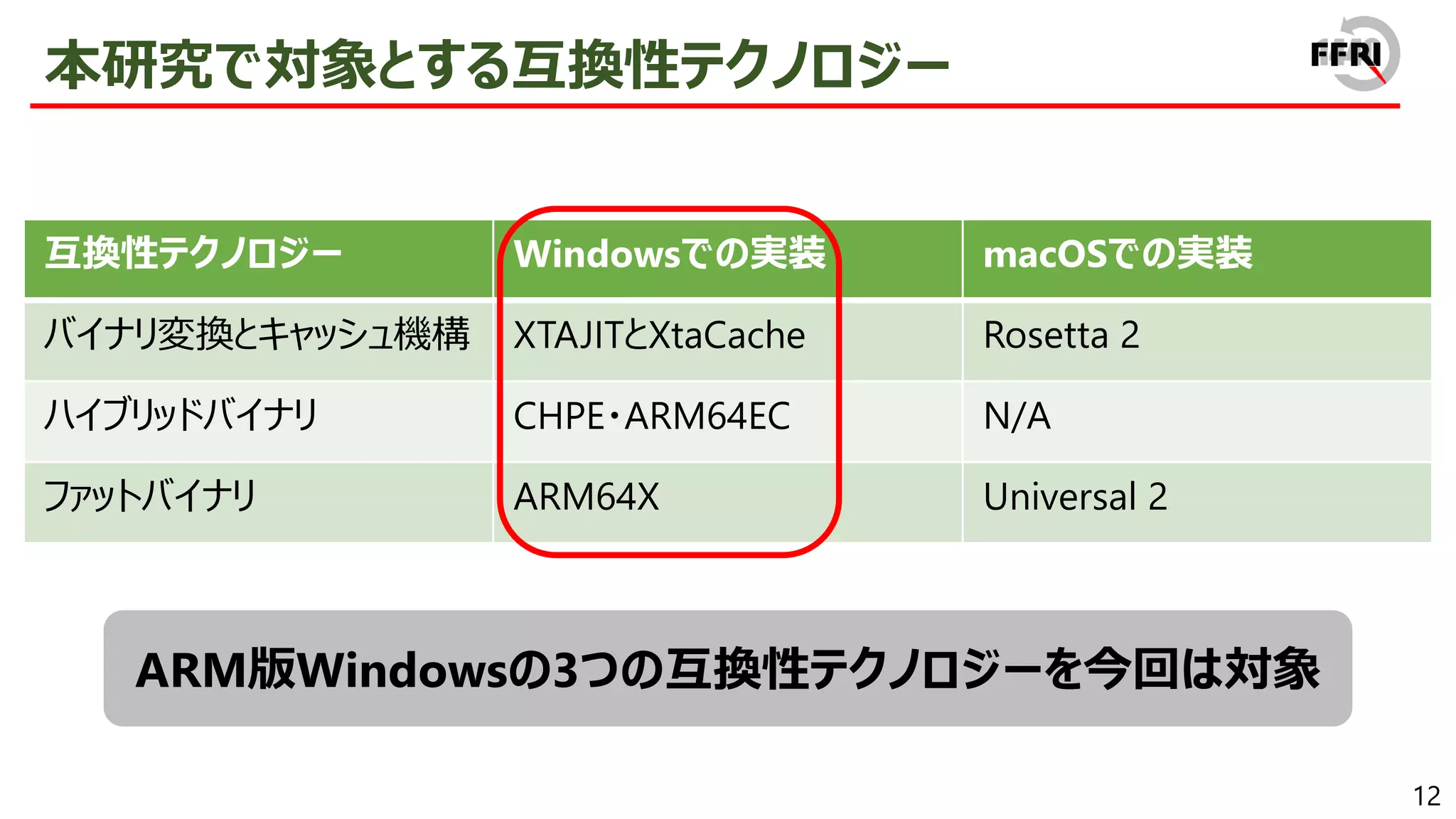
On the other hand, doesn't the introduction of new compatibility technologies provide a new avenue of attack for attackers? As far as we know, this point has not even been discussed much at this point. Therefore, we reverse engineered the compatibility technology that exists in Windows on ARM and examined its exploitability.
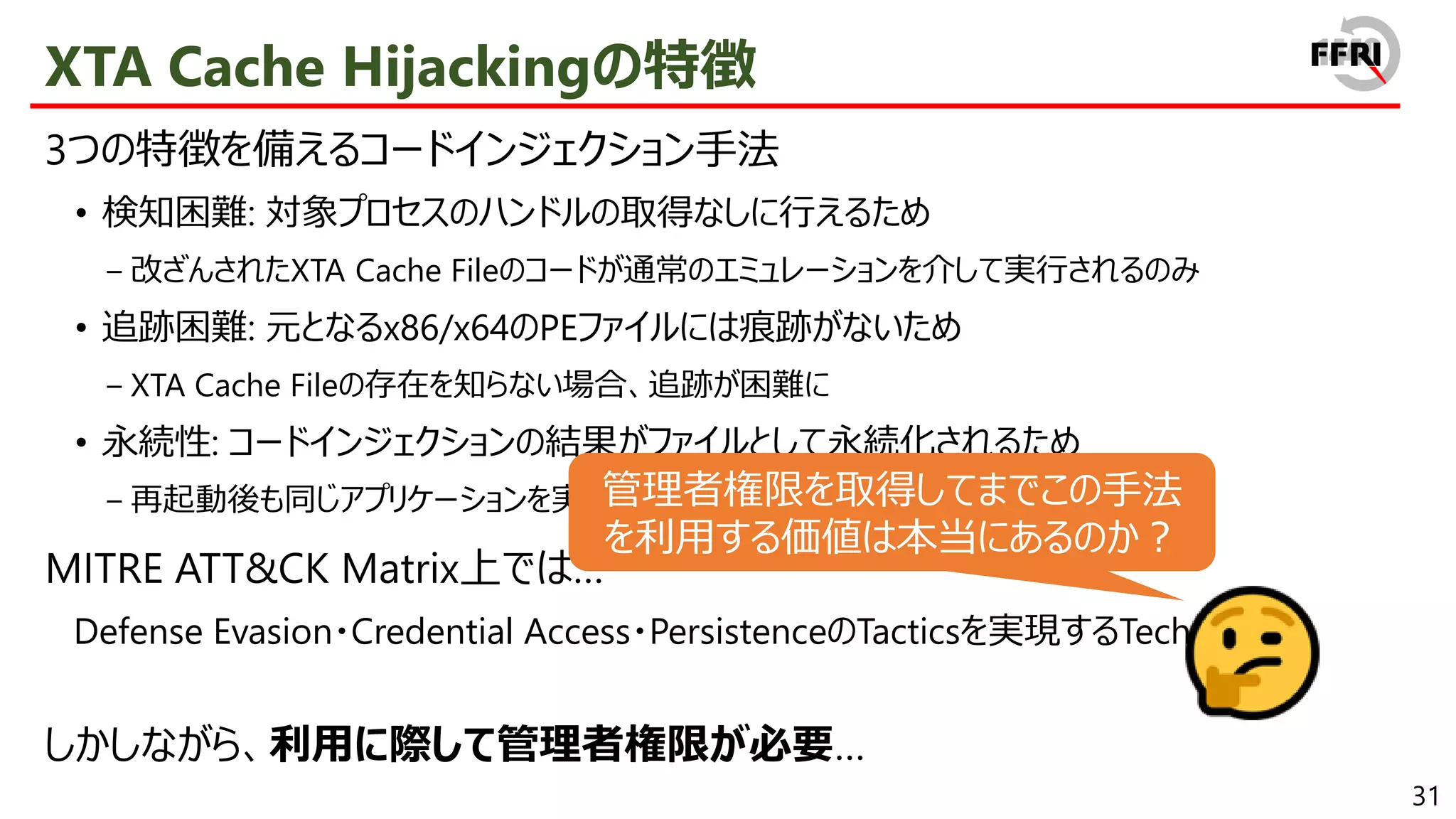
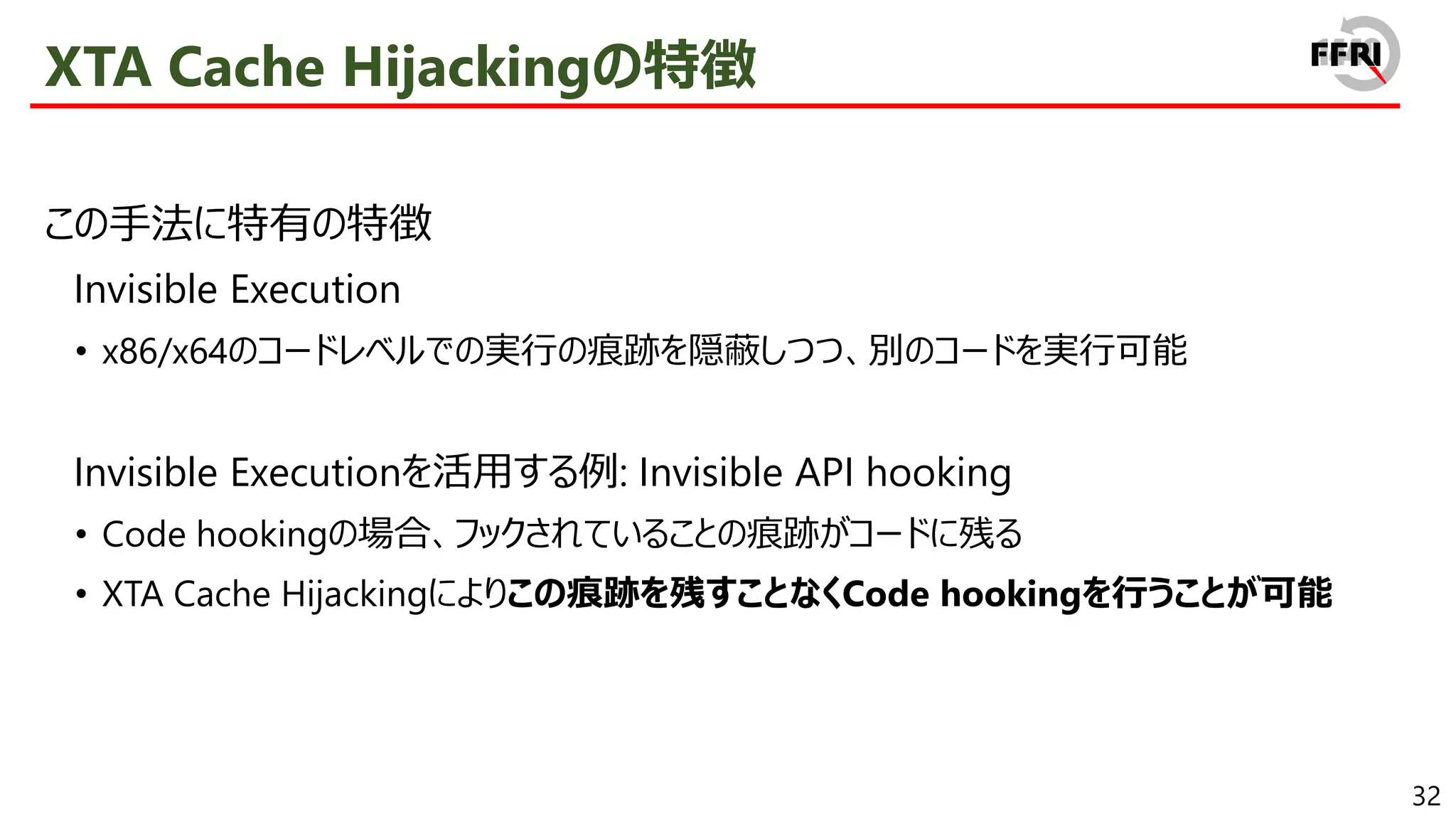
We found that various techniques are available, such as code injection by modifying XTA cache files, and obfuscation by exploiting newly introduced relocation entries. All of these techniques have in common the characteristic that the binary "appearance" and runtime behavior are different, making them difficult to detect and track. In addition, some of the techniques can be widely exploited to interfere with static analysis or sandbox analysis. Therefore, there is a high possibility that they will become a threat to the ARM version of Windows in the future.
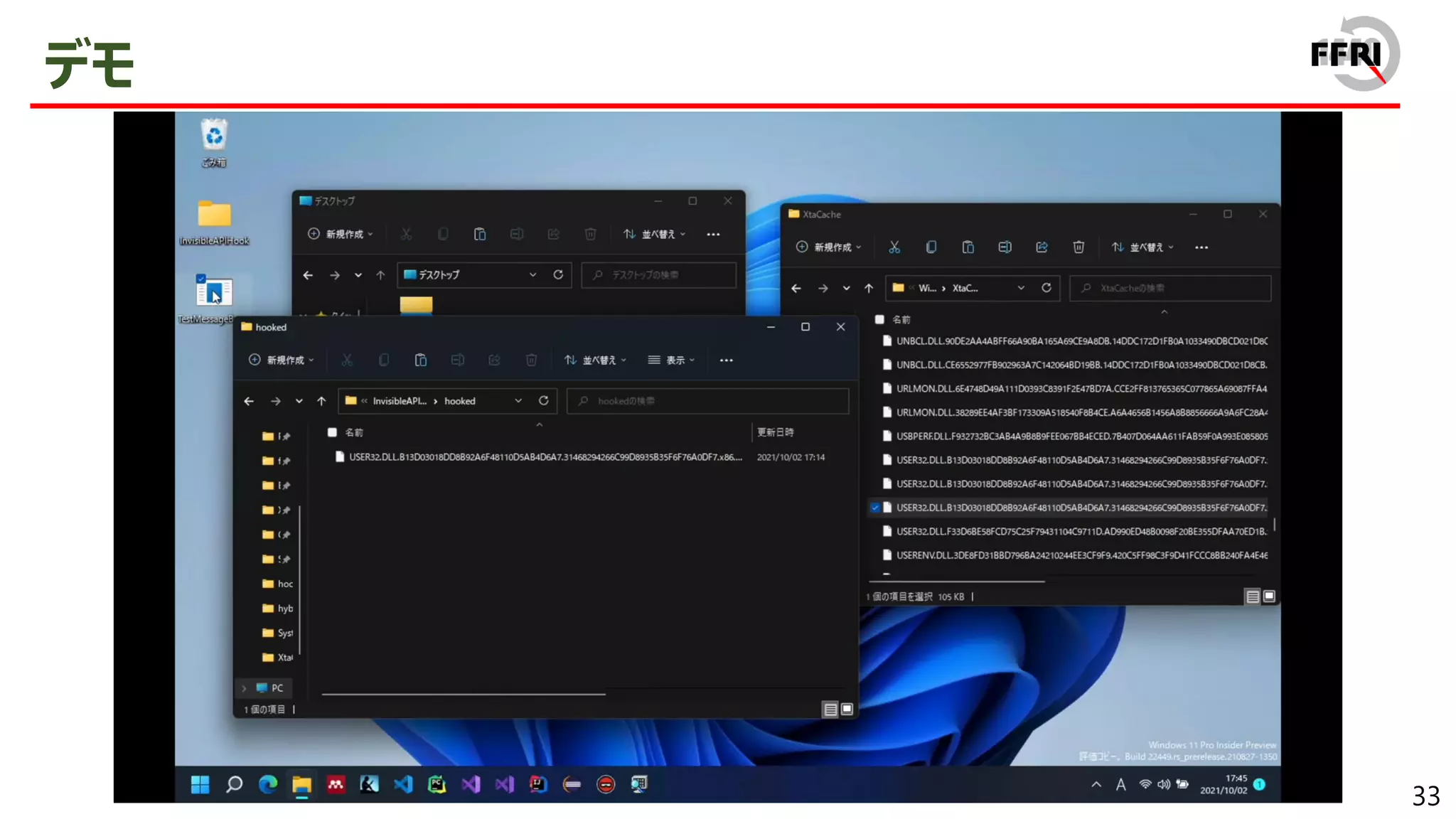
In this presentation, we will explain the details of our new method and its features with demonstrations. We hope that this presentation will be a good opportunity to develop and promote the security research of Windows on ARM.
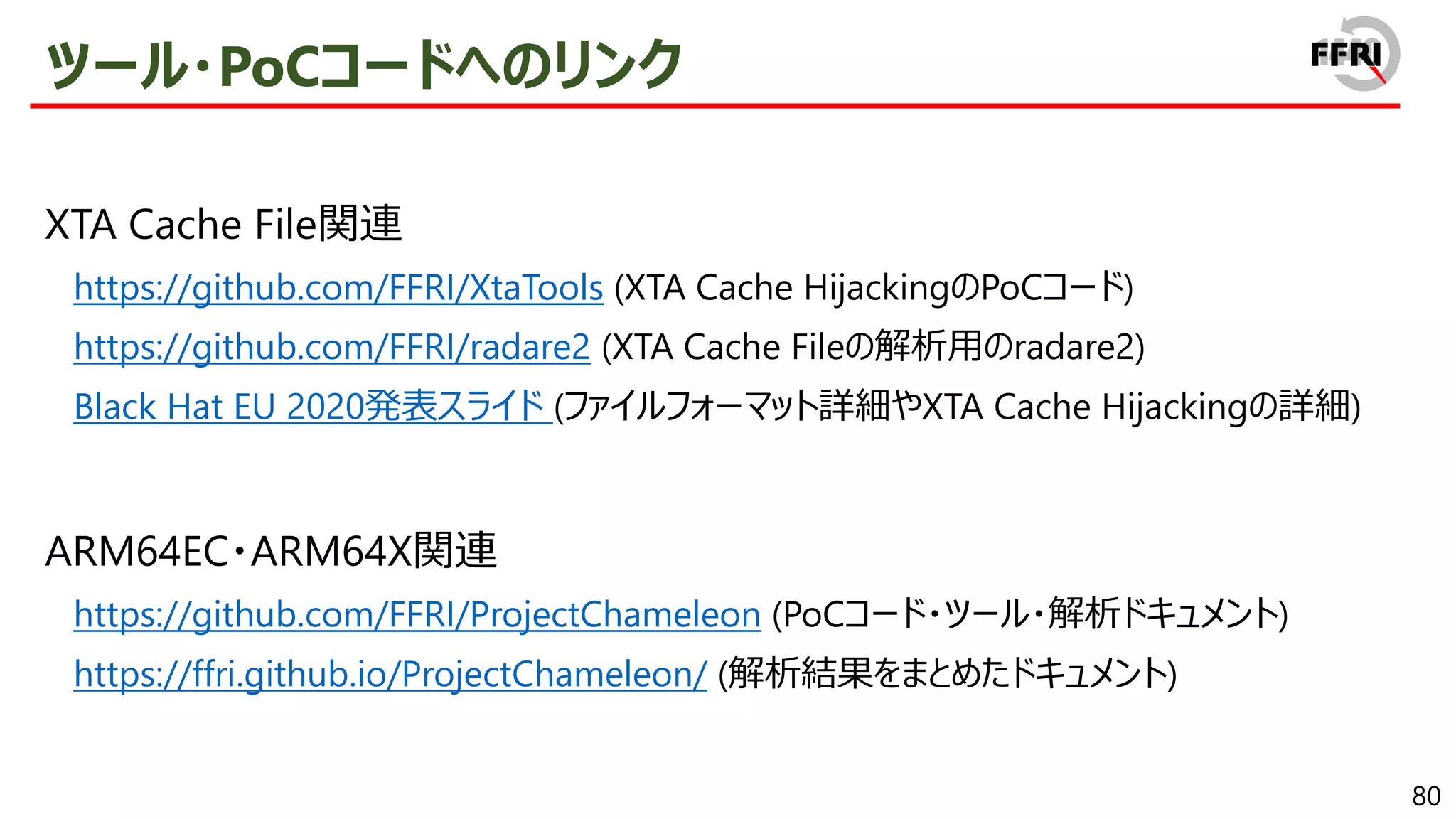
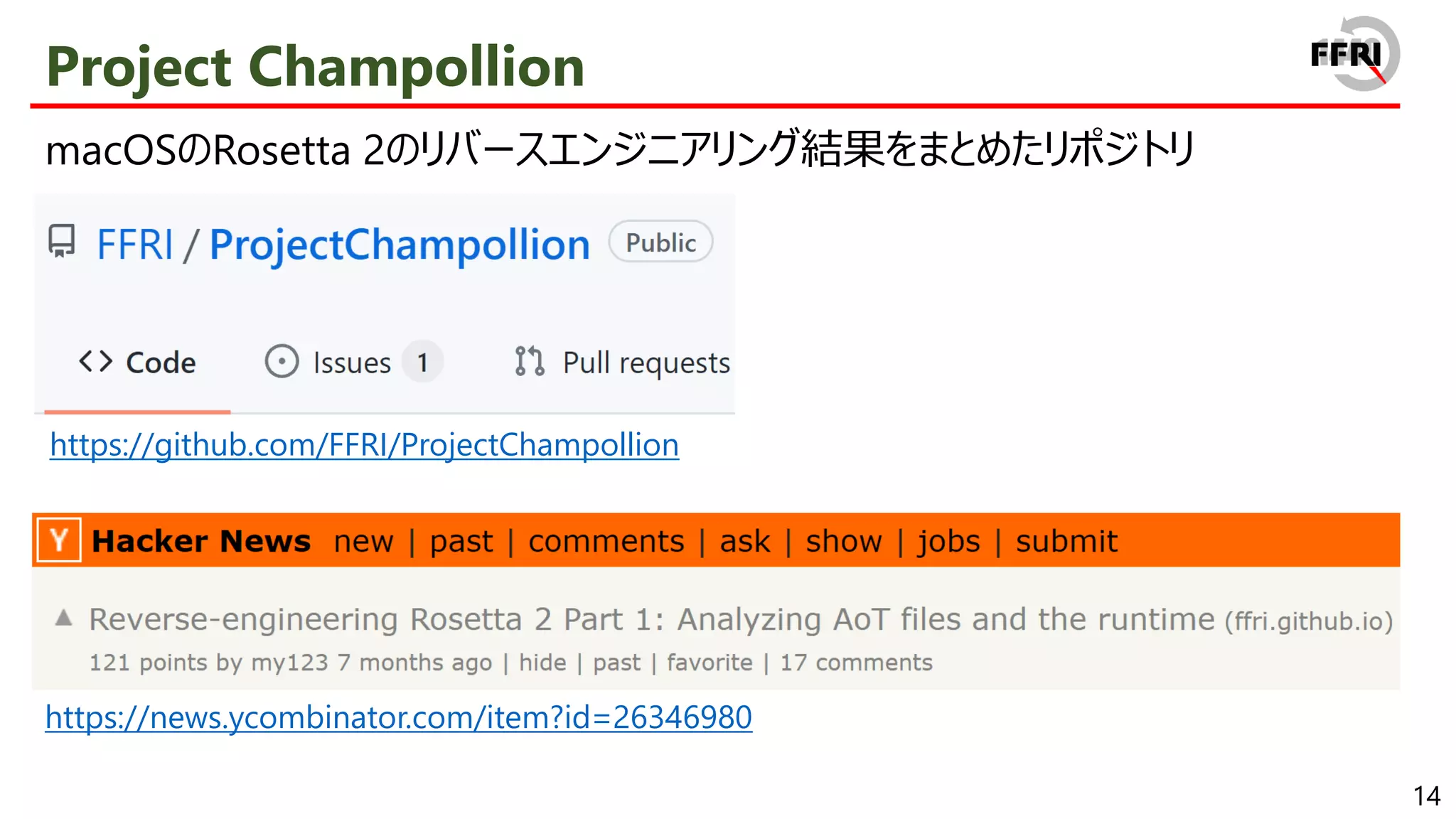
The PoC code and detailed reverse engineering results will be available on GitHub.




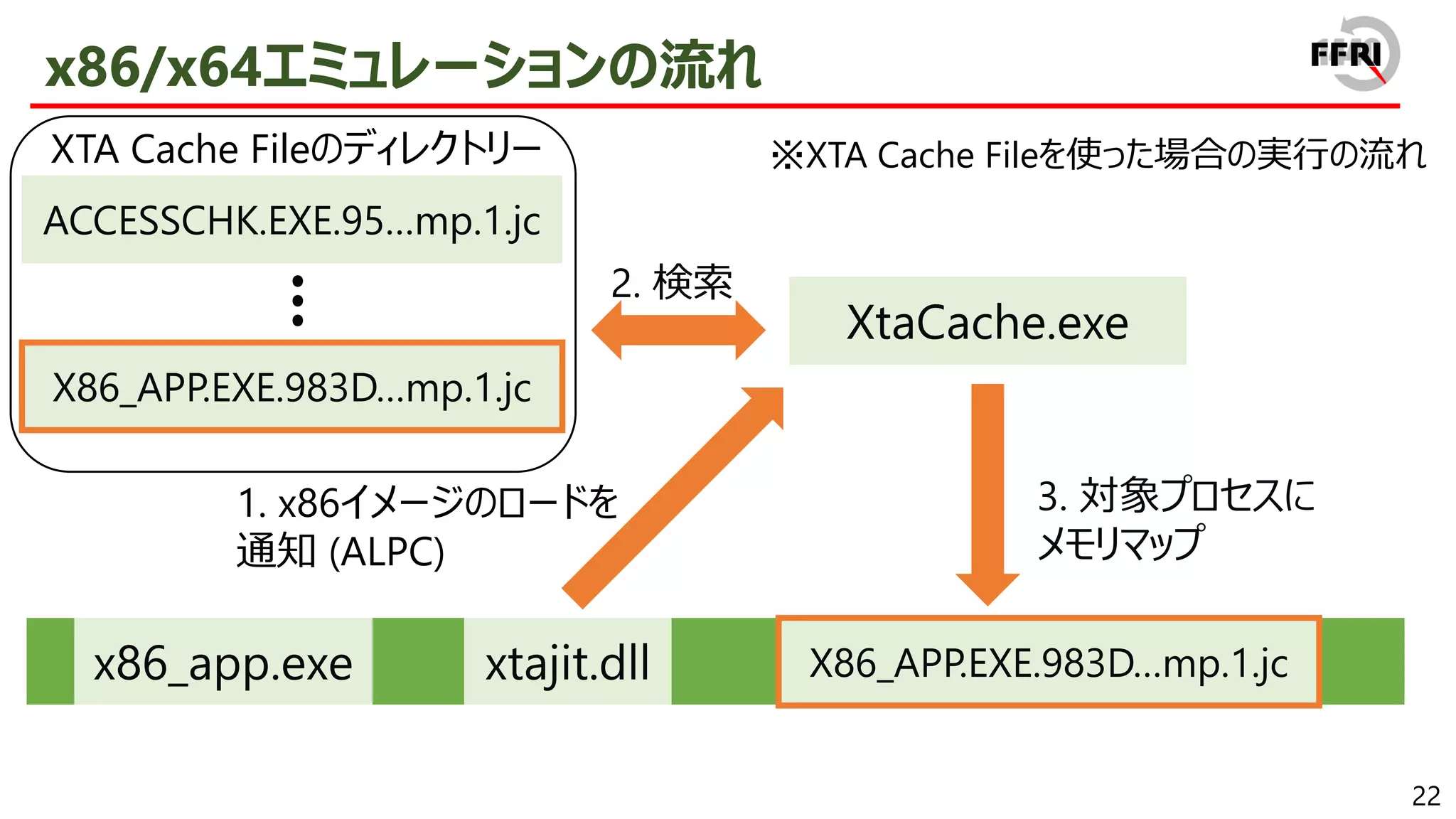
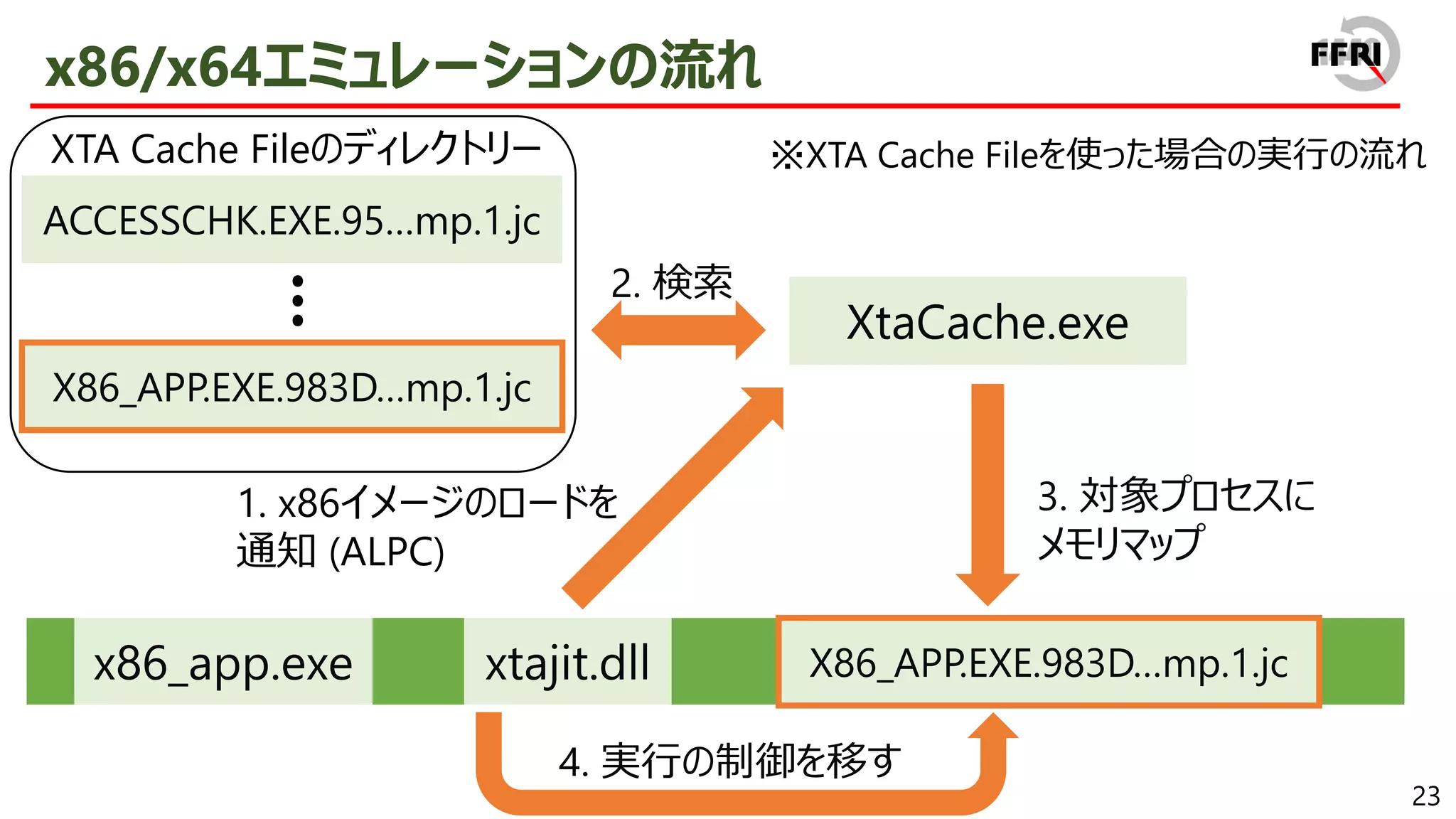
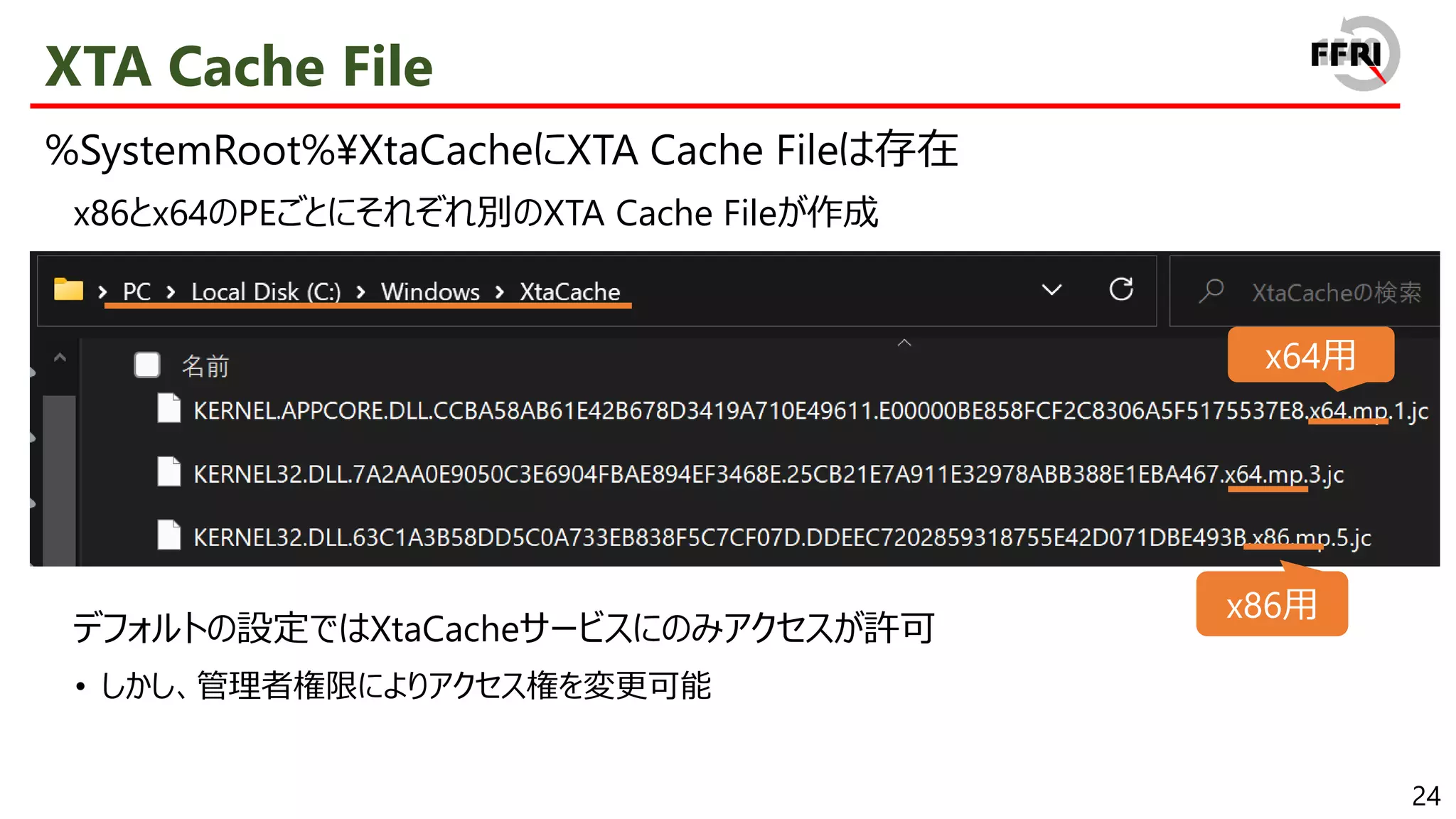
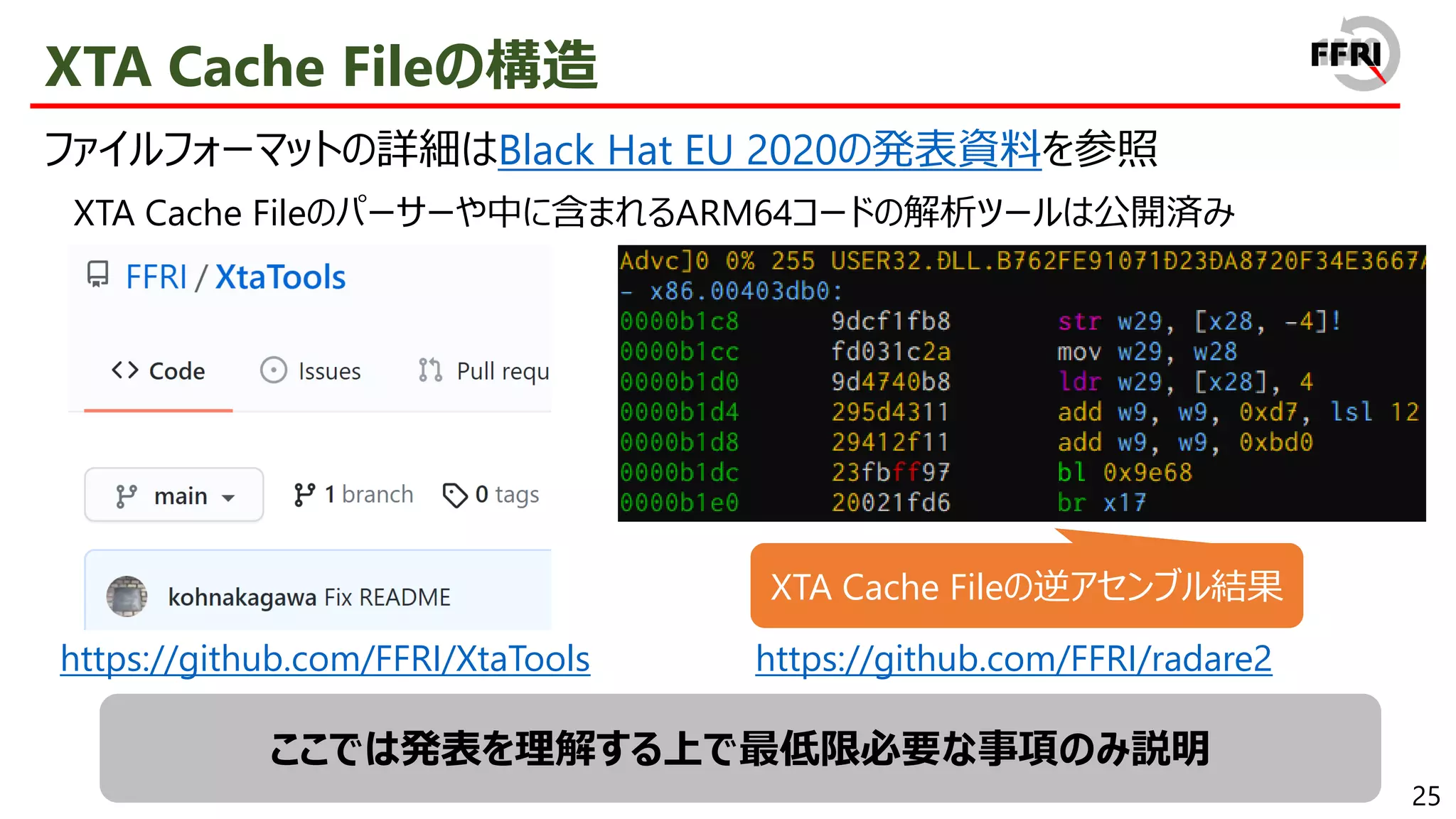



![38
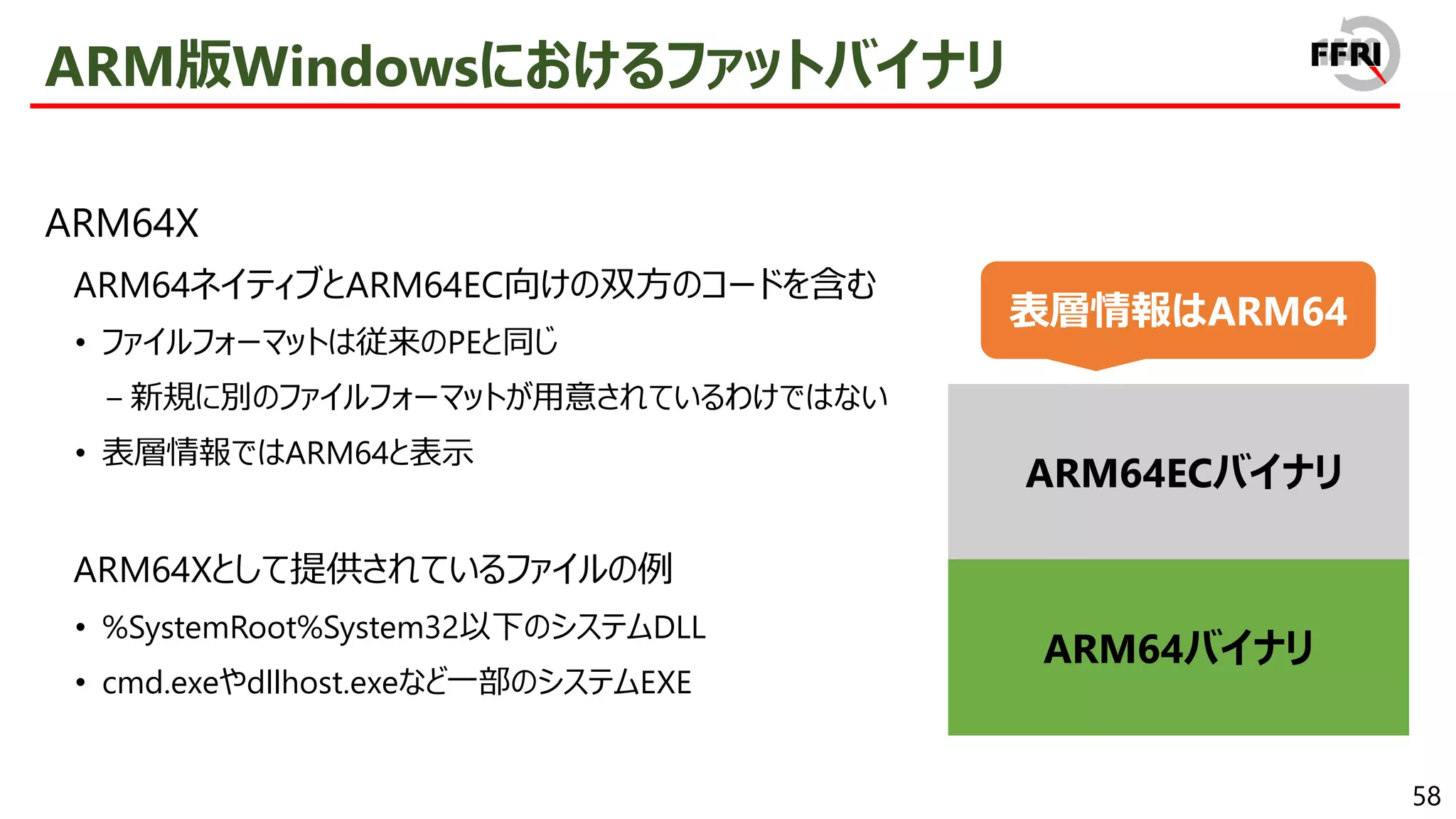
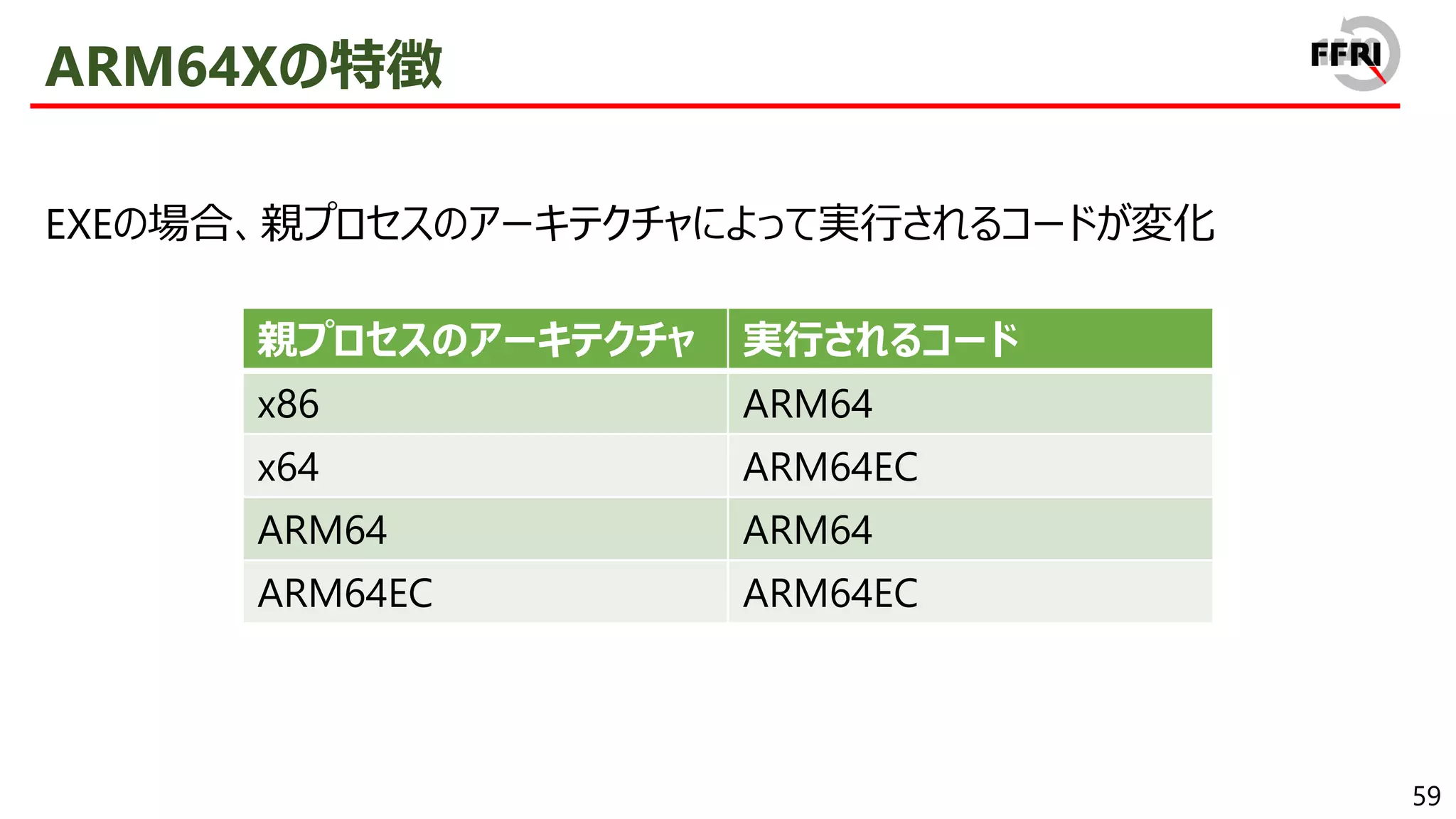
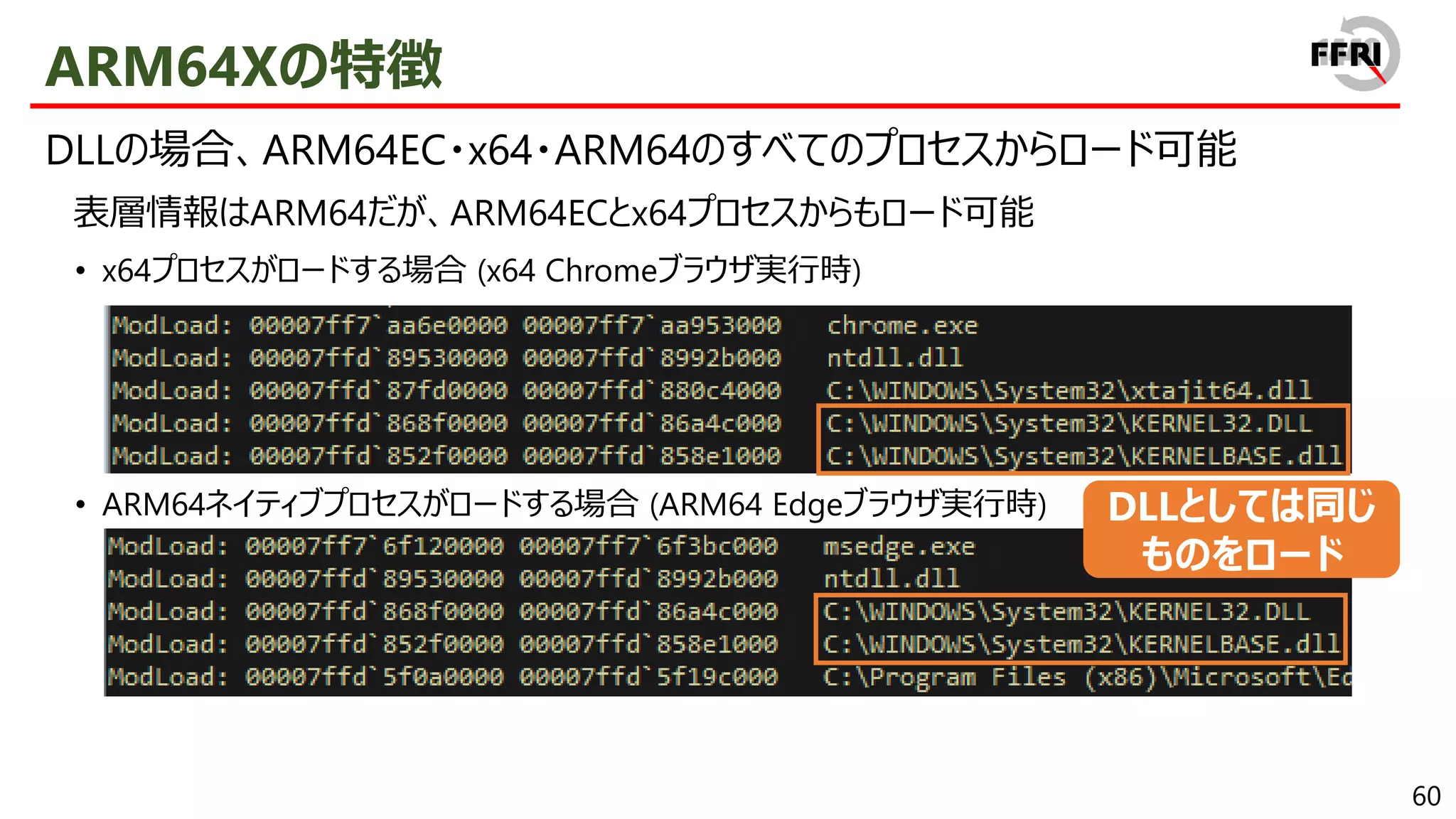
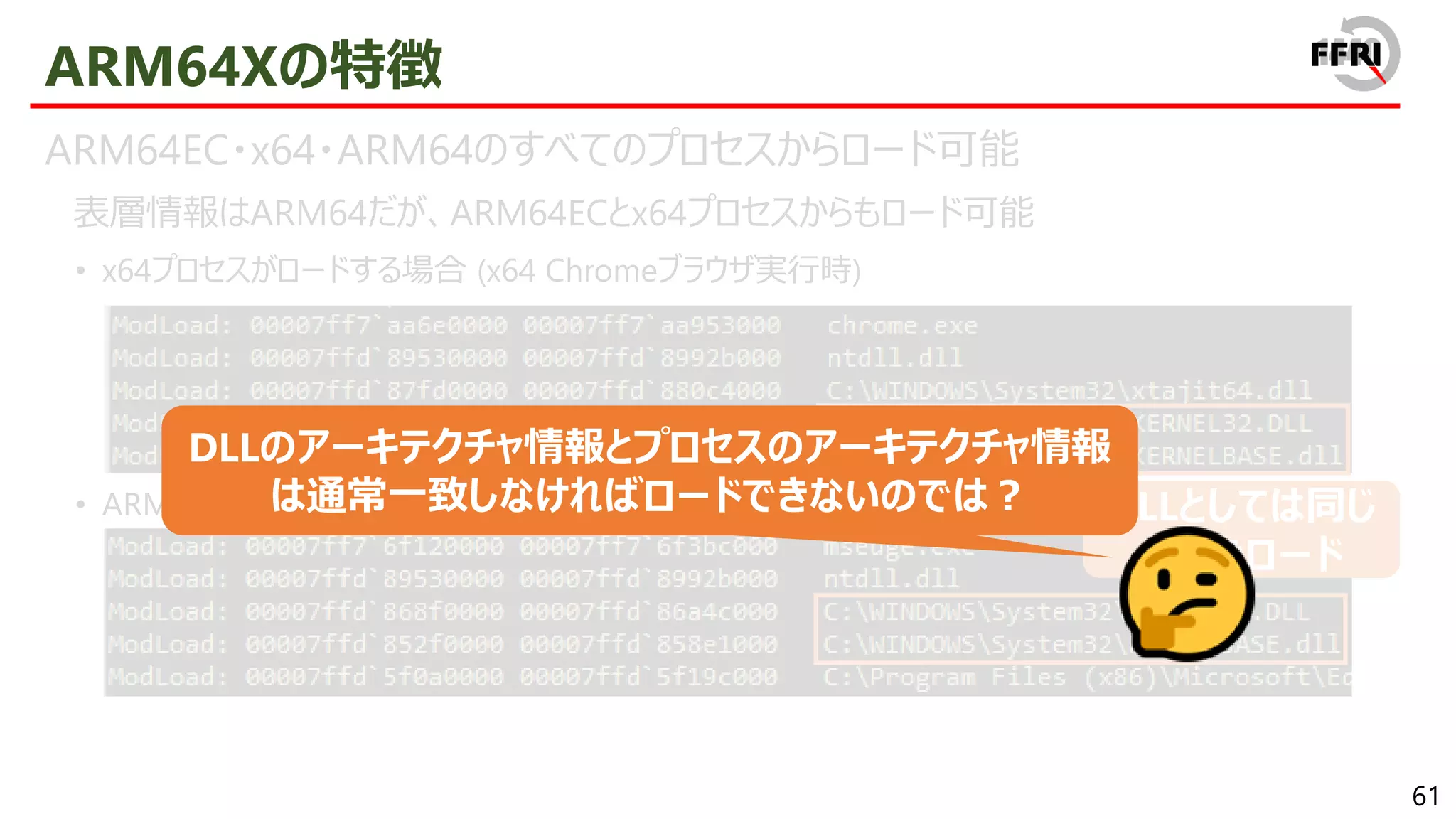
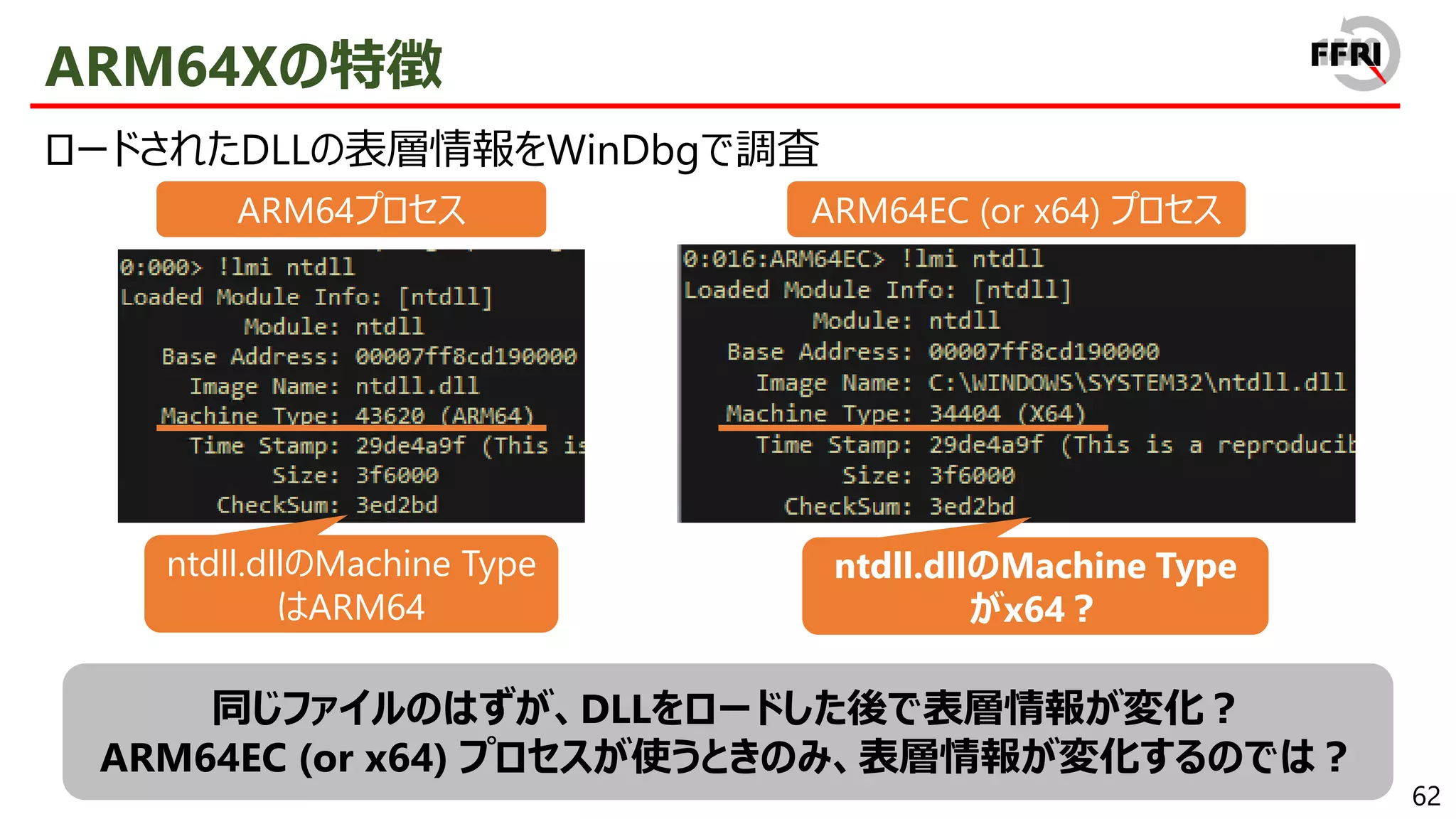
CHPEの特徴
x86 PEとの互換性を保ちつつ、ARM64ネイティブとほぼ同等のパフォーマンスを実現
CHPEは見かけ上x86 PEとして振る舞う
• 表層情報はx86であり、export関数の逆アセンブル結果もx86
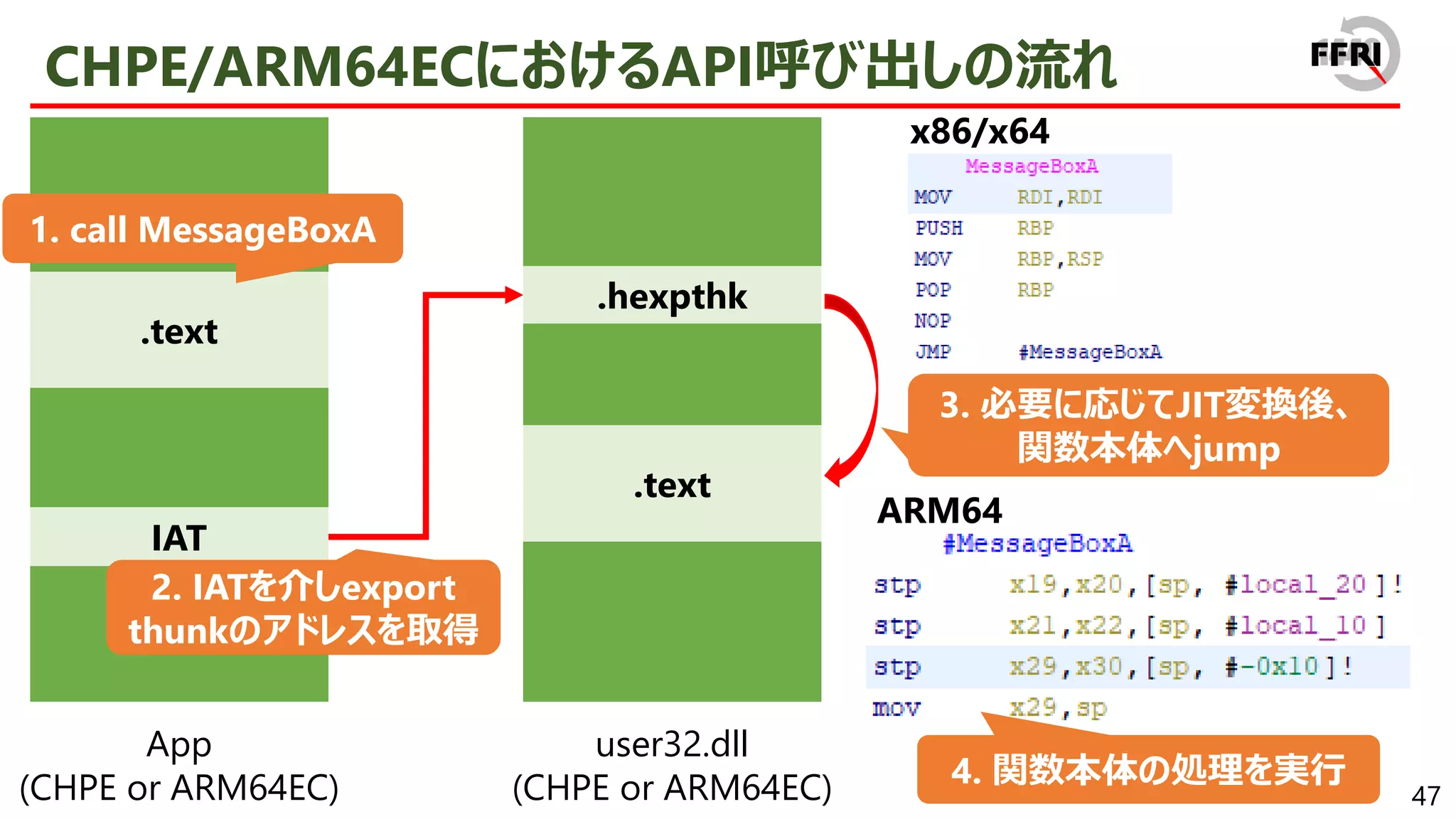
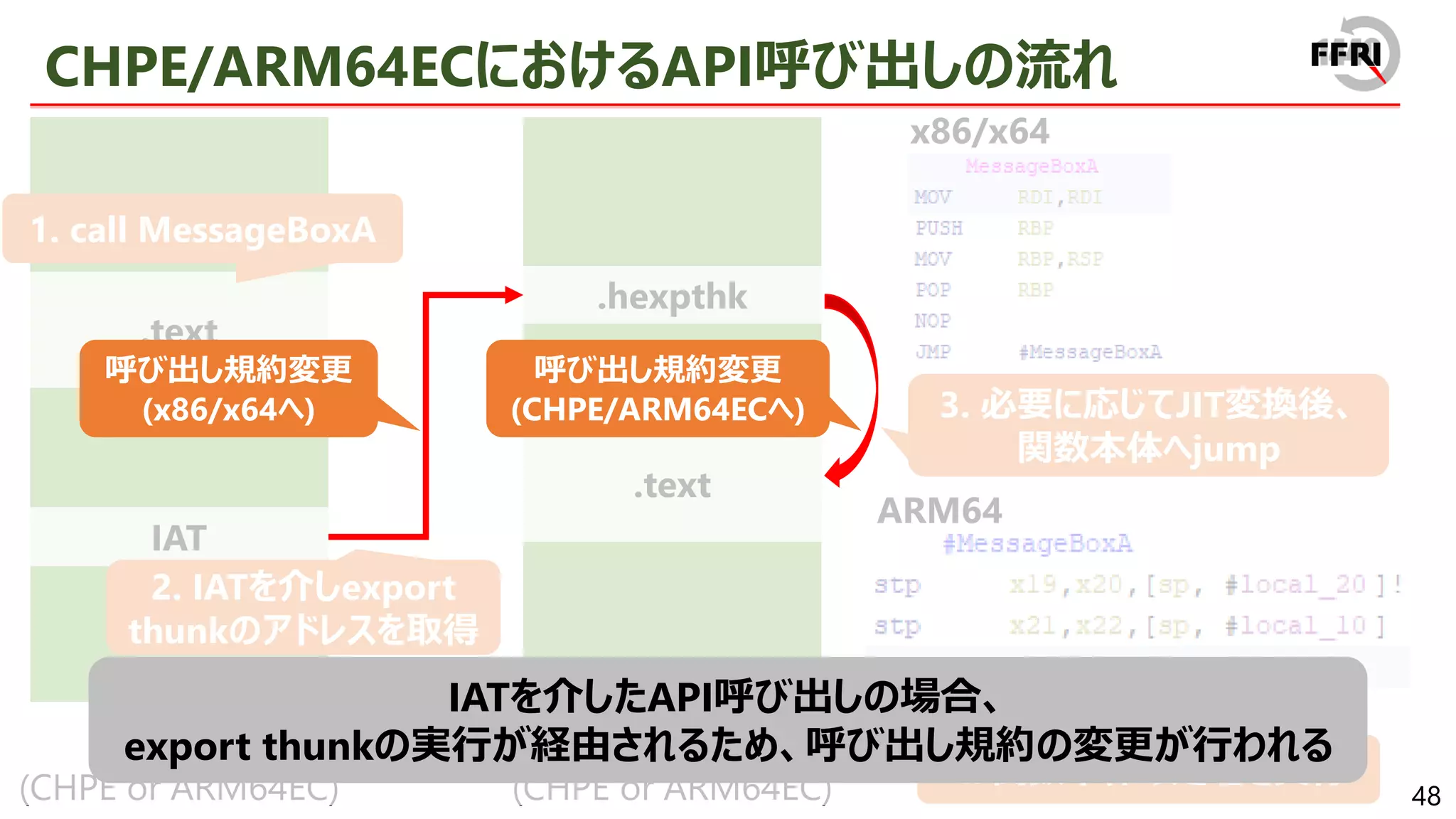
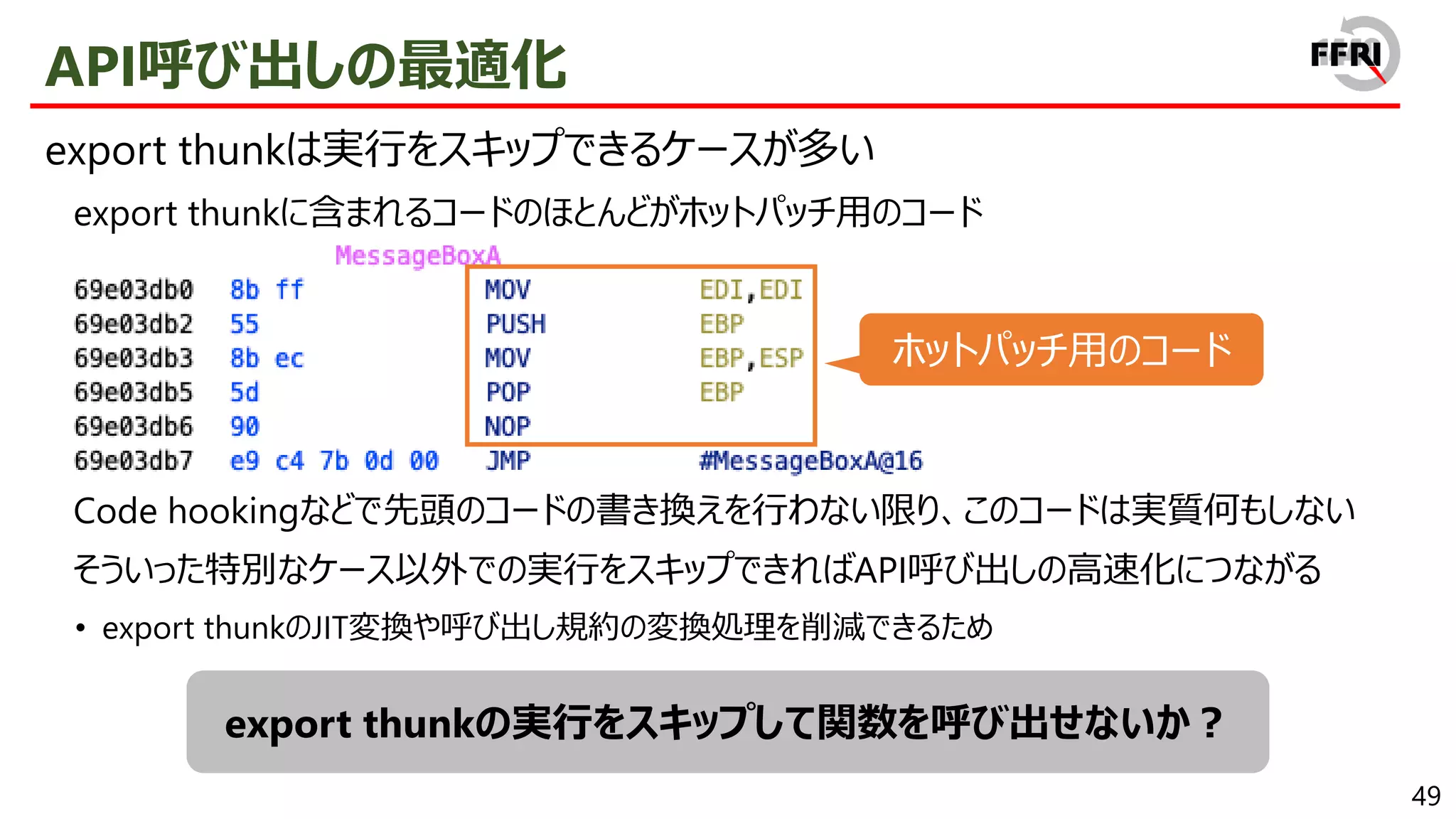
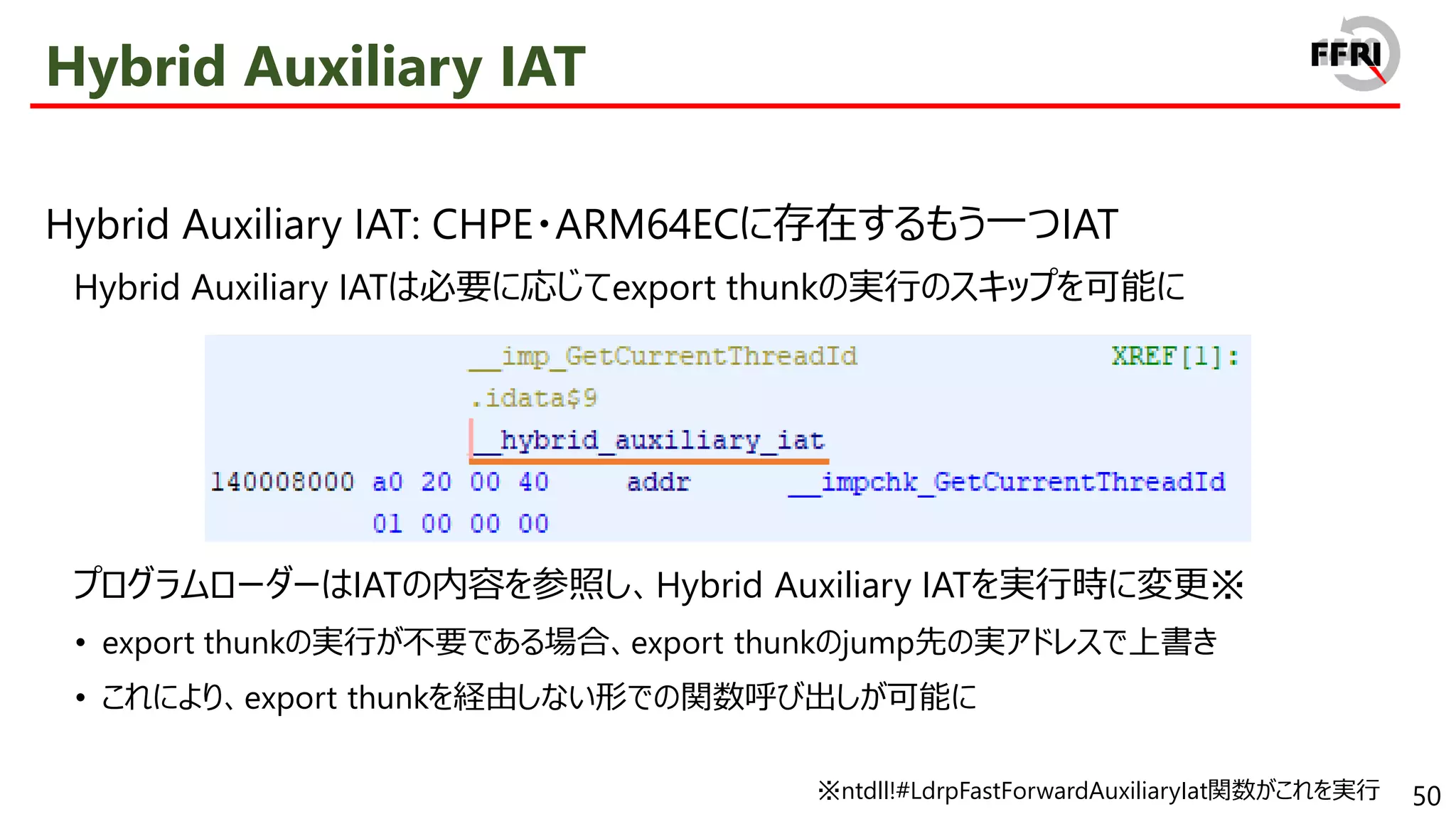
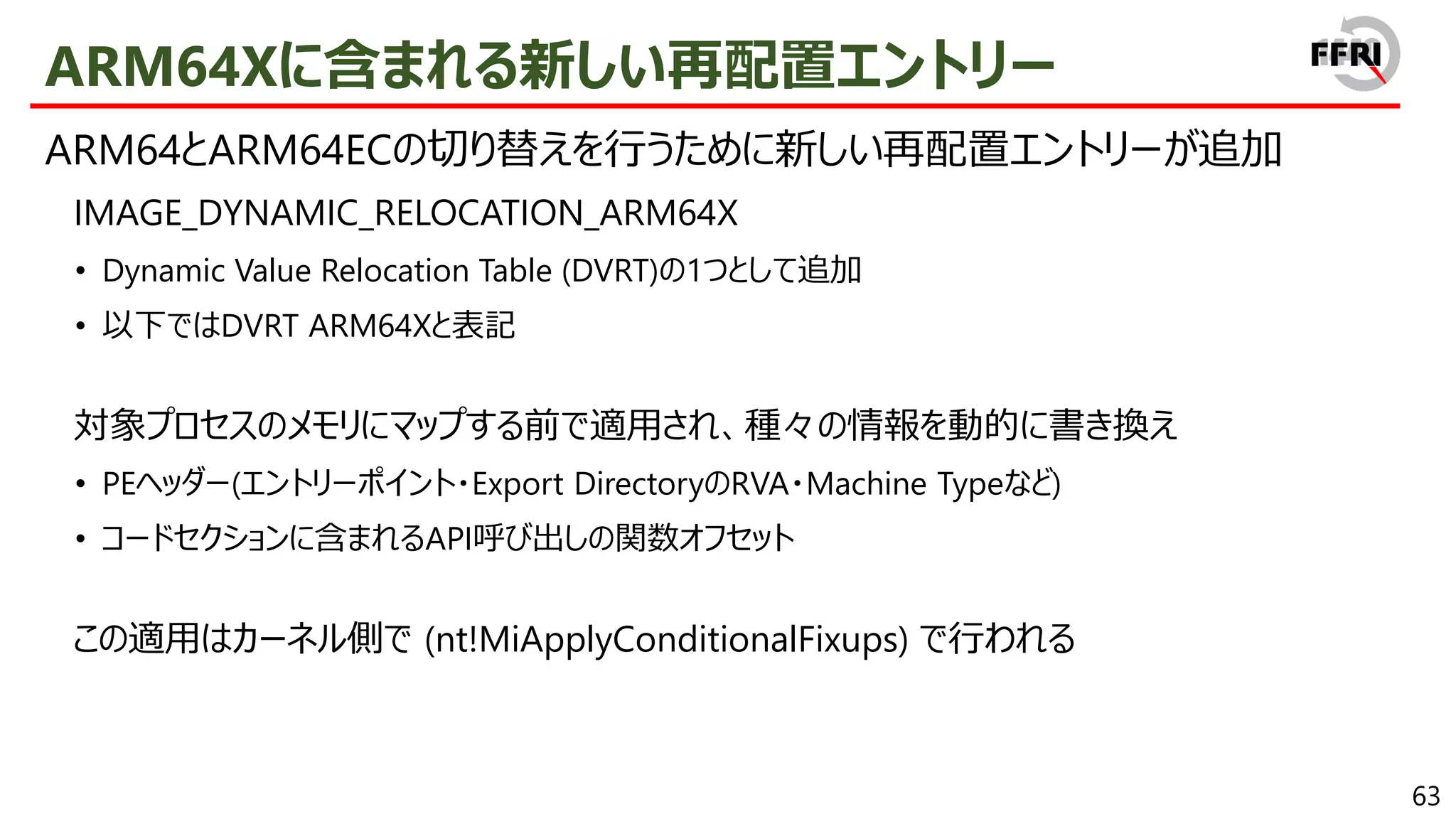
− export関数はexport thunkと呼ばれる
• CHPEは1プロセス内でx86 PEと混在して利用することが可能
export thunkはARM64コードへのjump stub
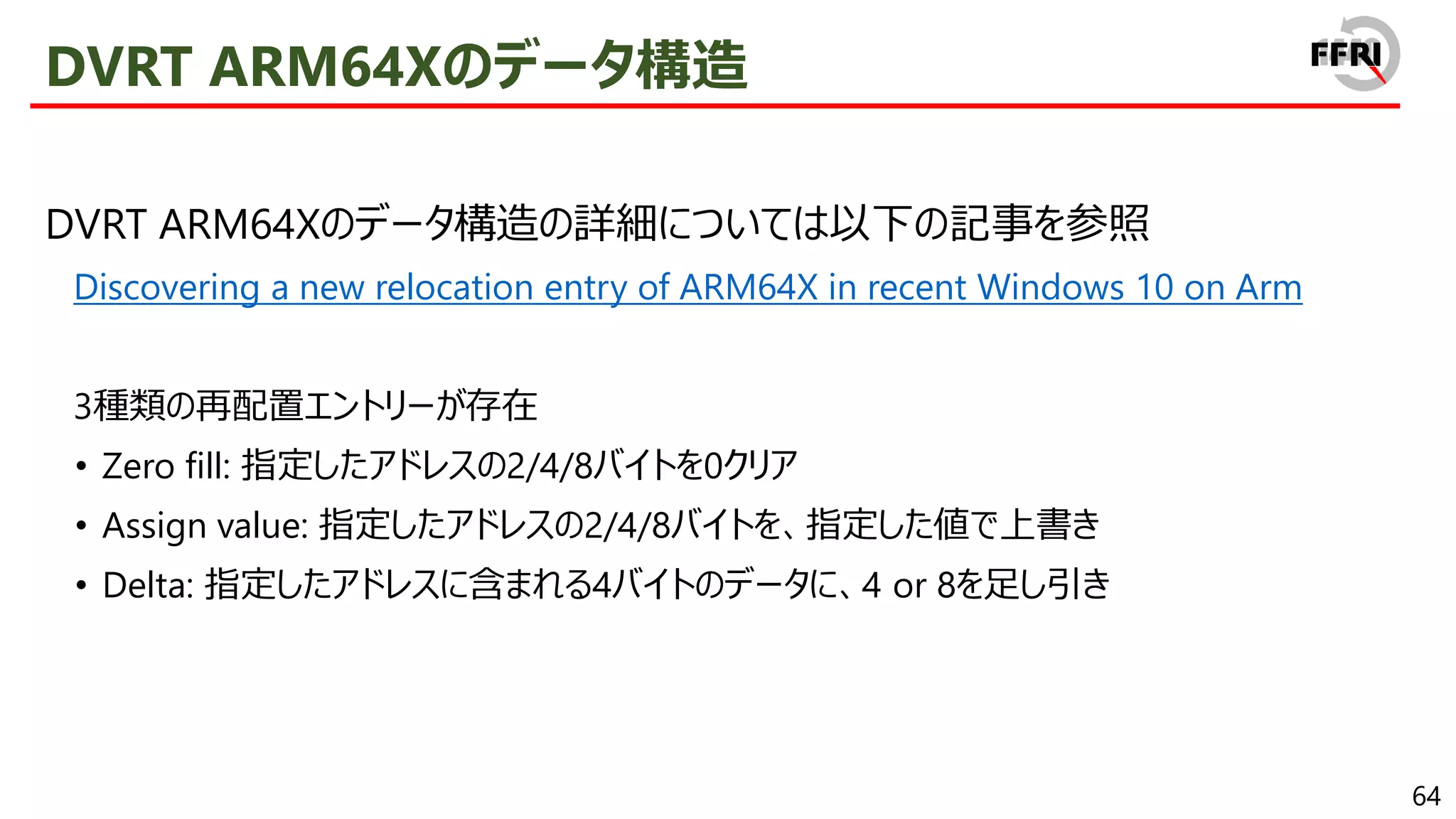
• jump先のARM64コードに関数の本体が含まれる
JITバイナリ変換はexport thunkについてのみ実行
• 関数全体について行う必要がなく、JITバイナリ変換量を削減
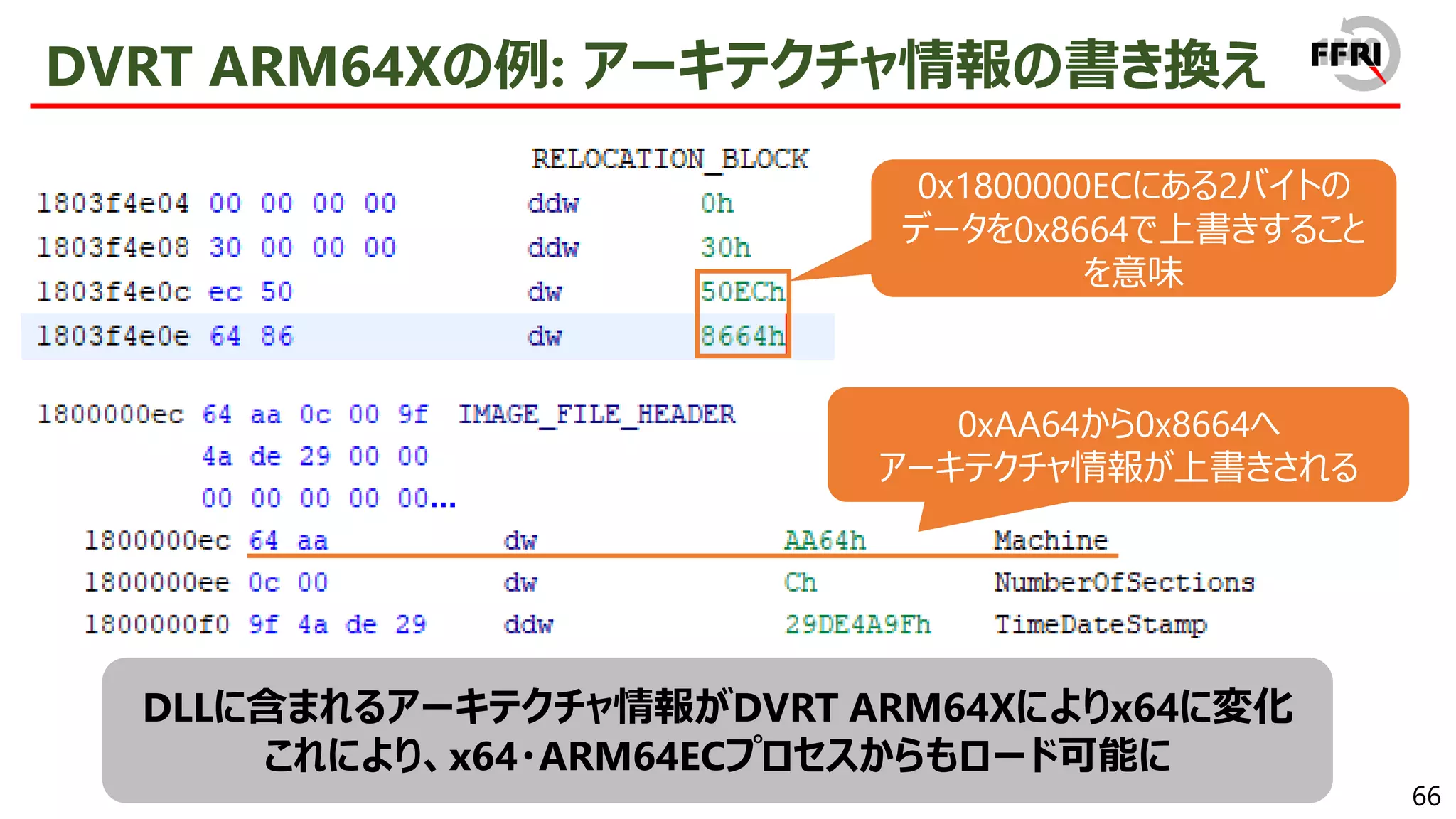
• そのため、パフォーマンス自体はARM64ネイティブで実行するときとほぼ同等に
mov edi, edi
push ebp
…
jmp #func0
x86 (func0のexport thunk)
#func0
stp x29,x30,[sp, #-0x10]!
mov x29, sp
…
ARM64 (func0の関数の本体)](https://image.slidesharecdn.com/kohnakagawaappearancesaredeceivingjapanese-211019042011/75/Appearances-are-deceiving-Novel-offensive-techniques-in-Windows-10-11-on-ARM-38-2048.jpg)