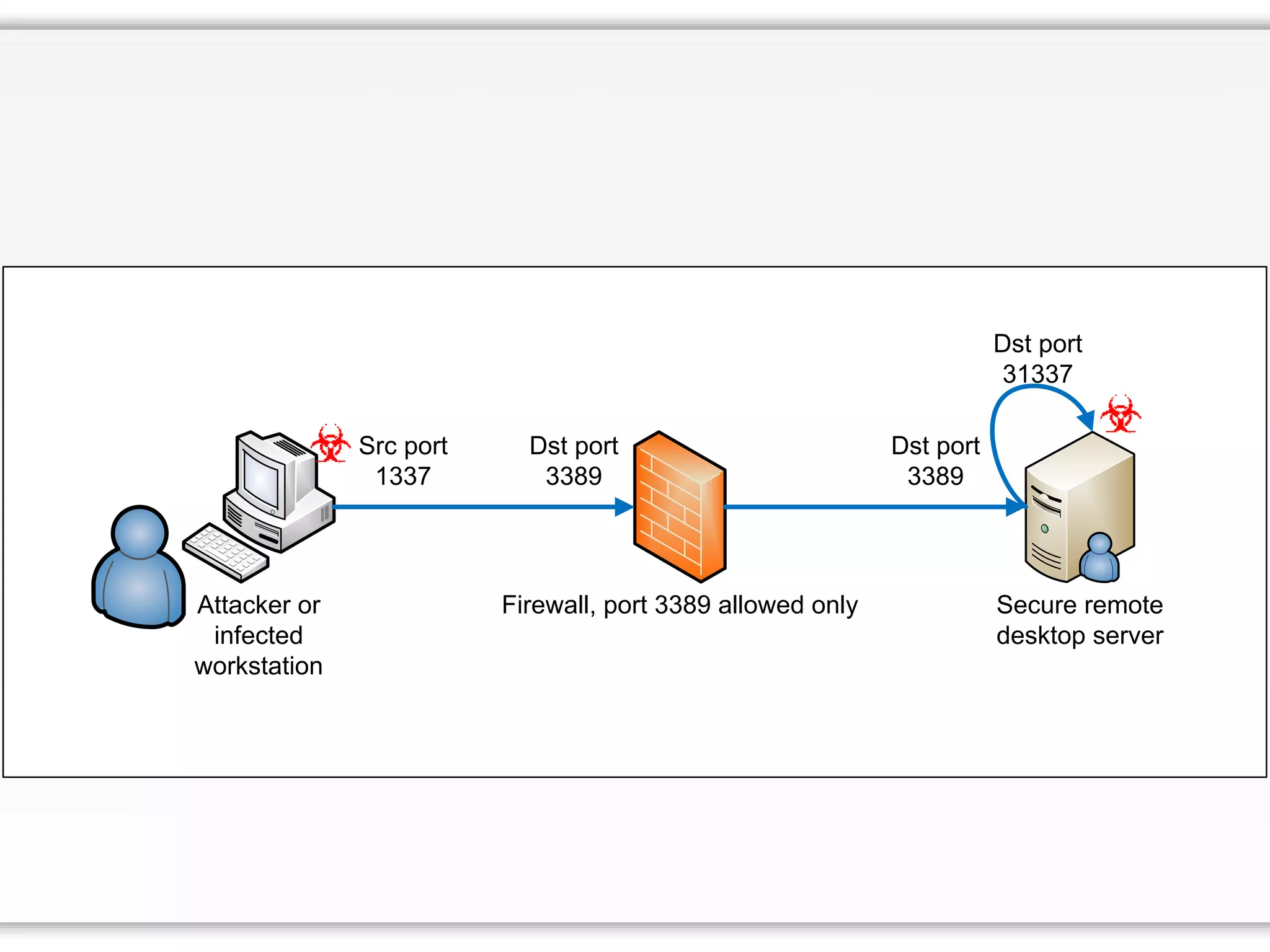
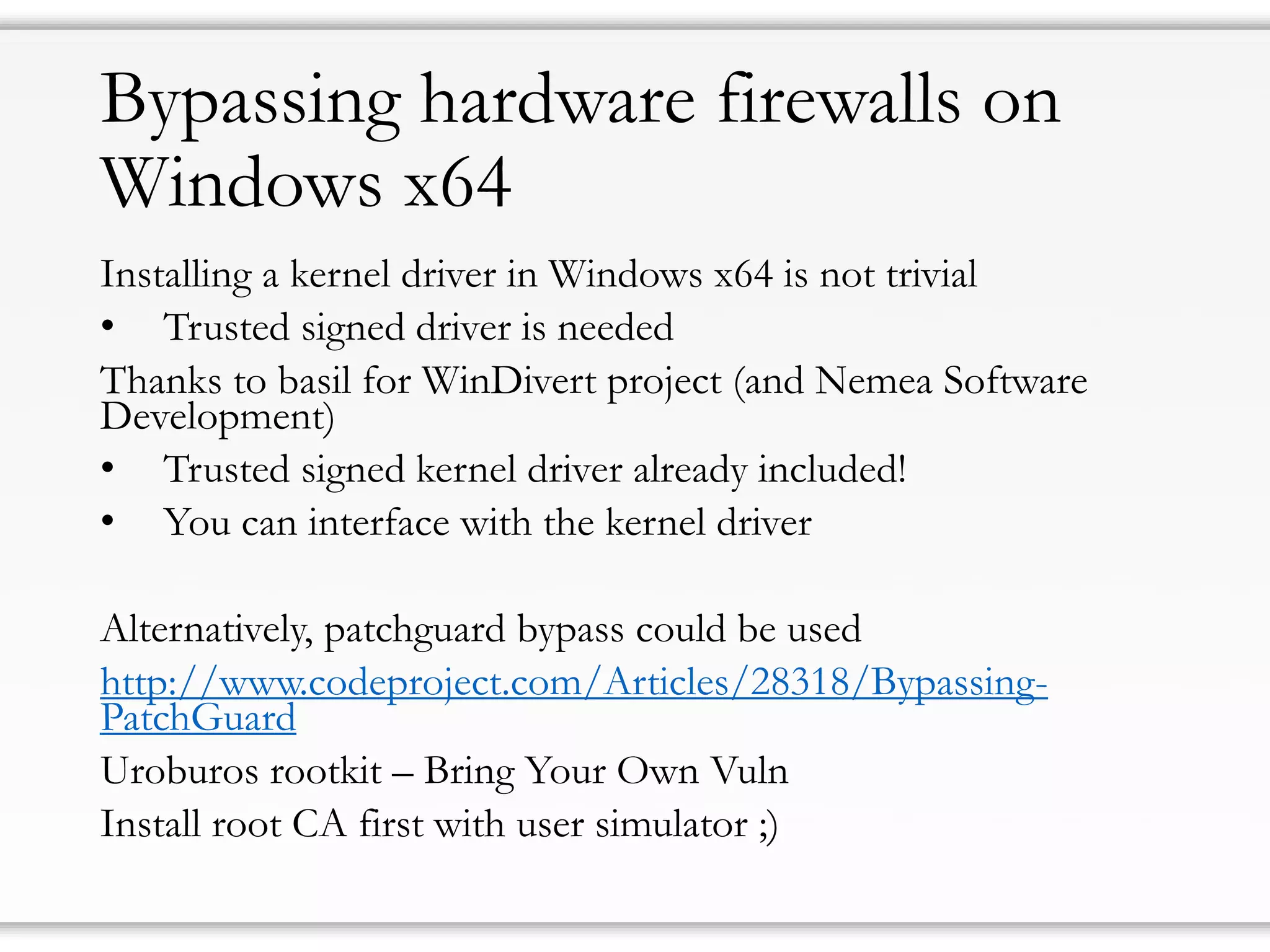
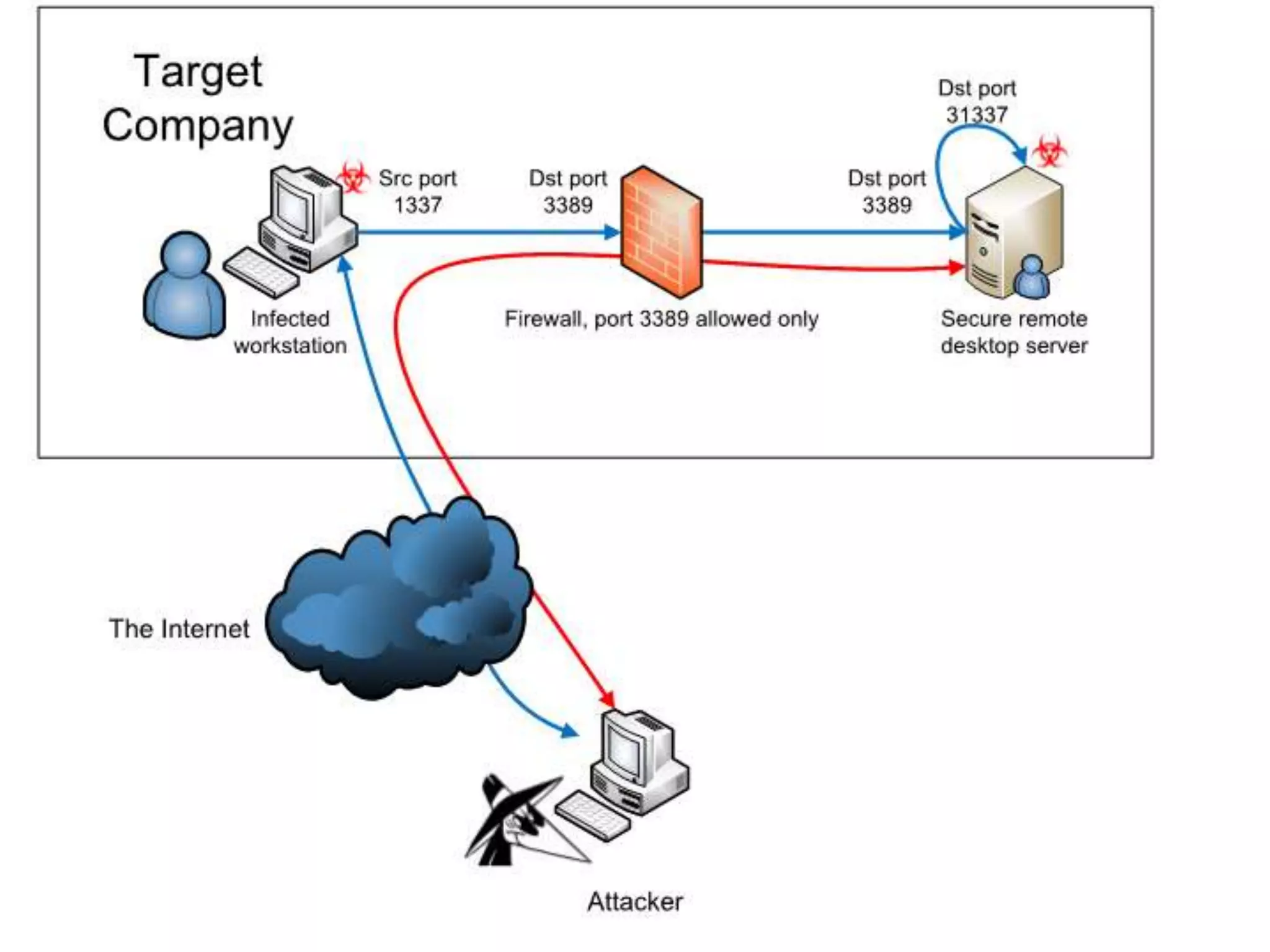
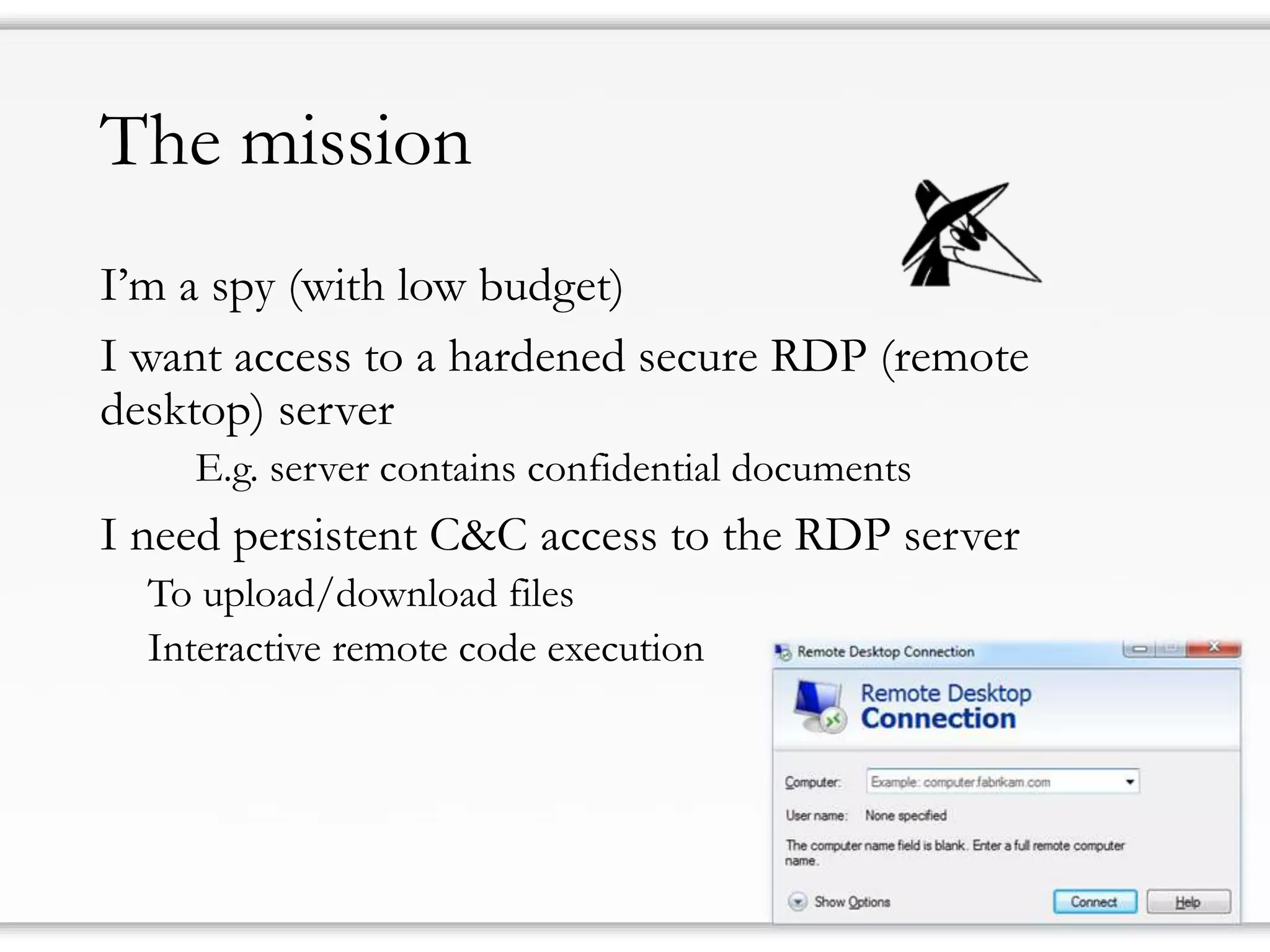
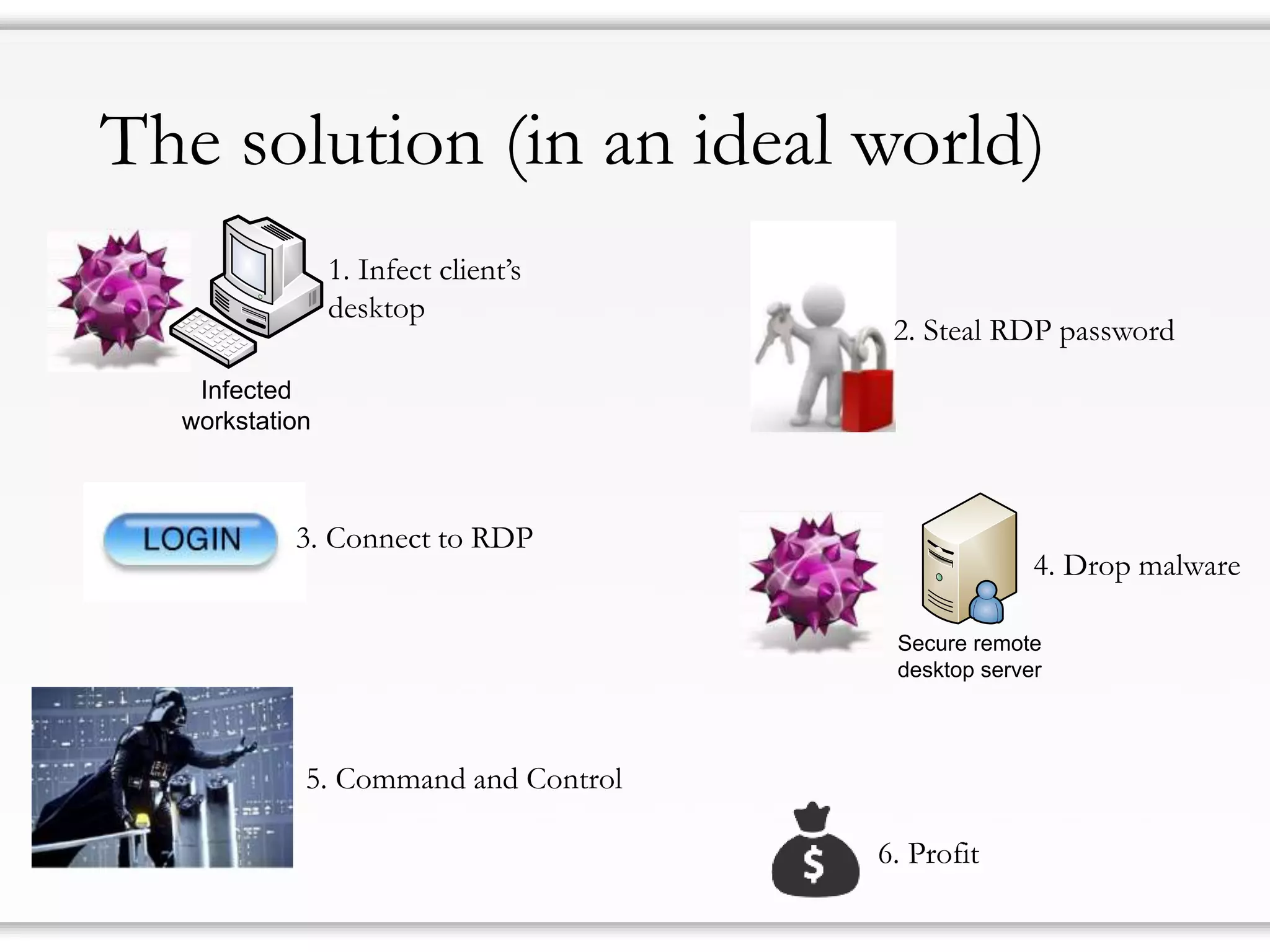
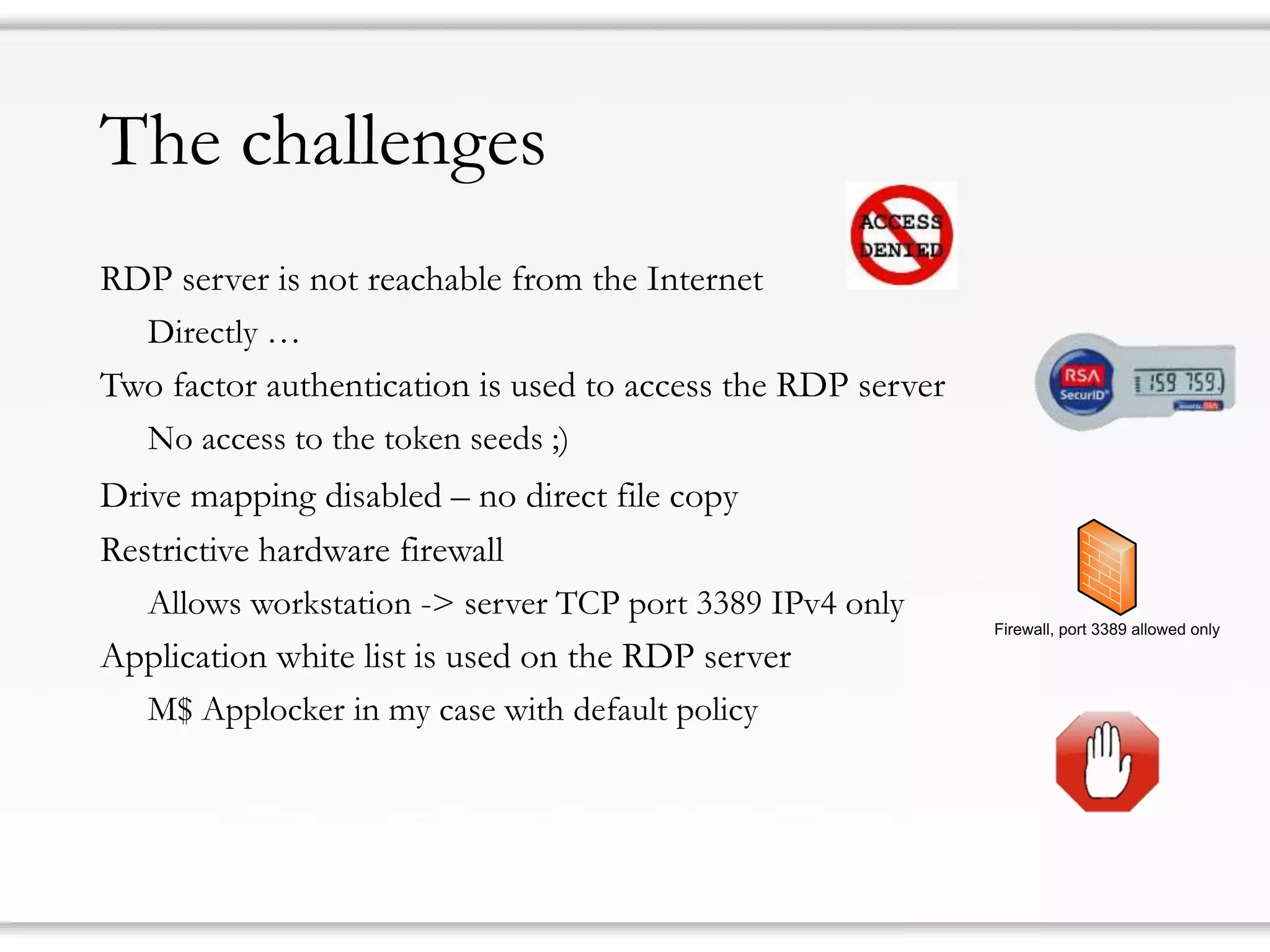
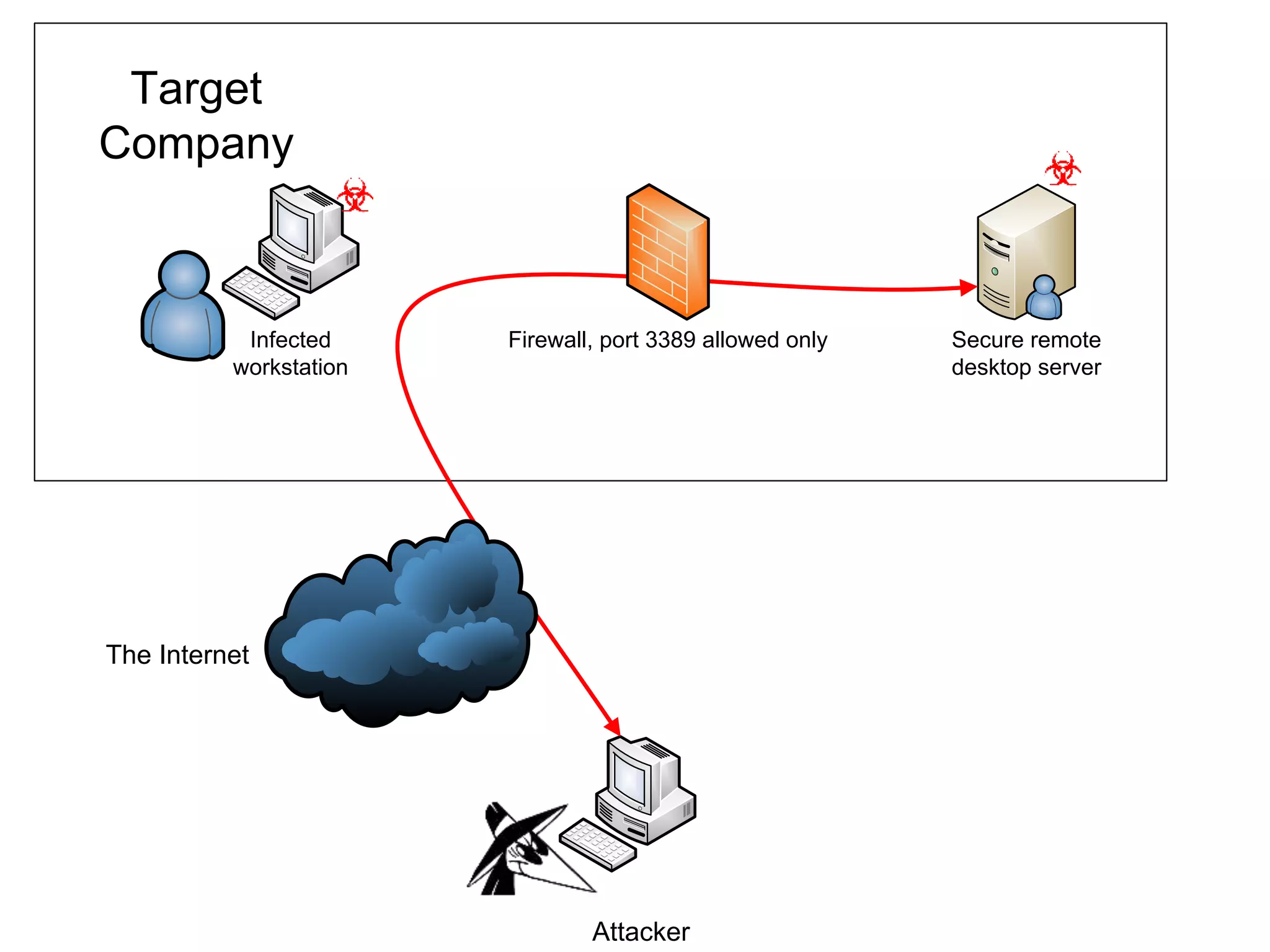
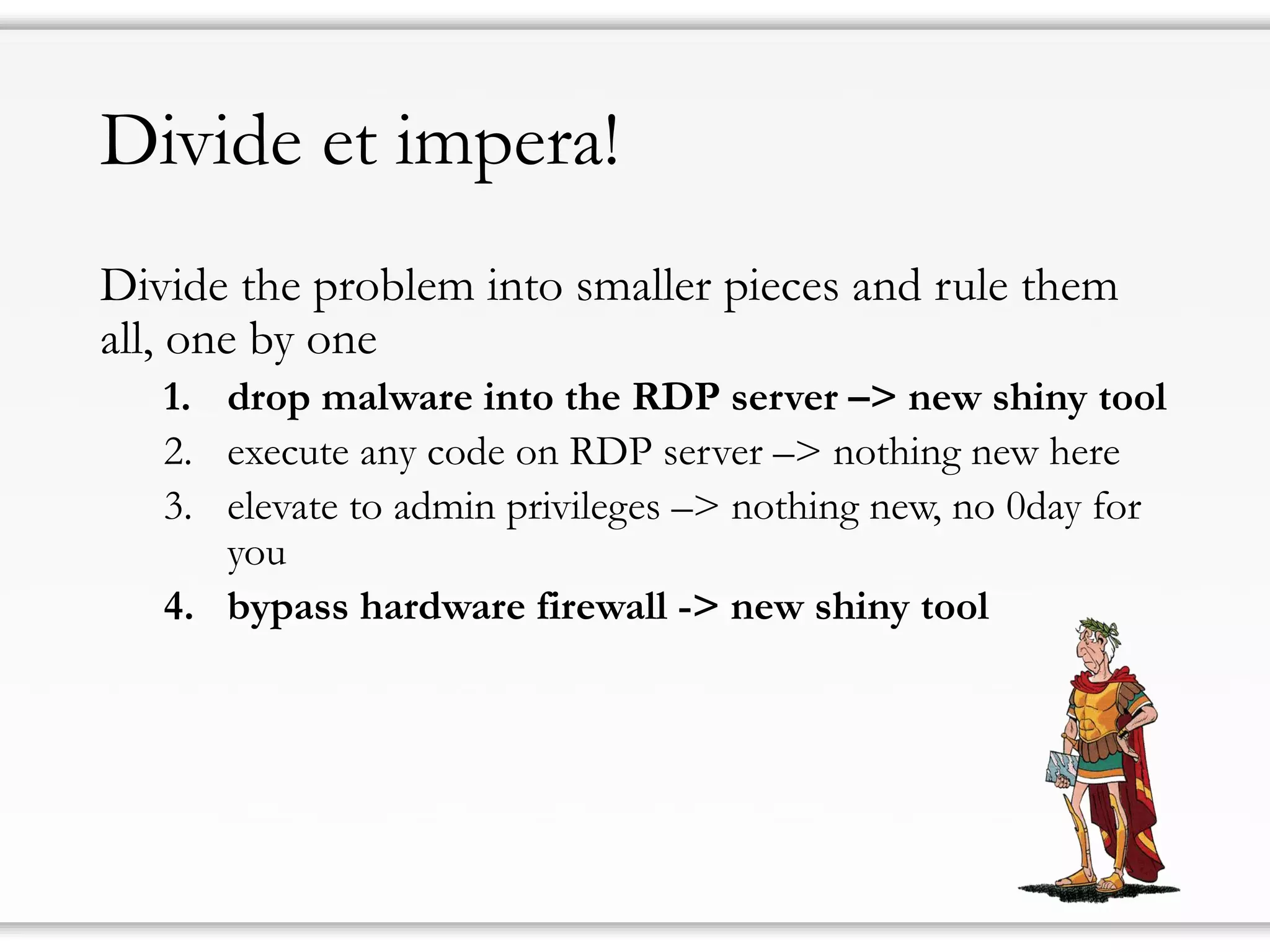
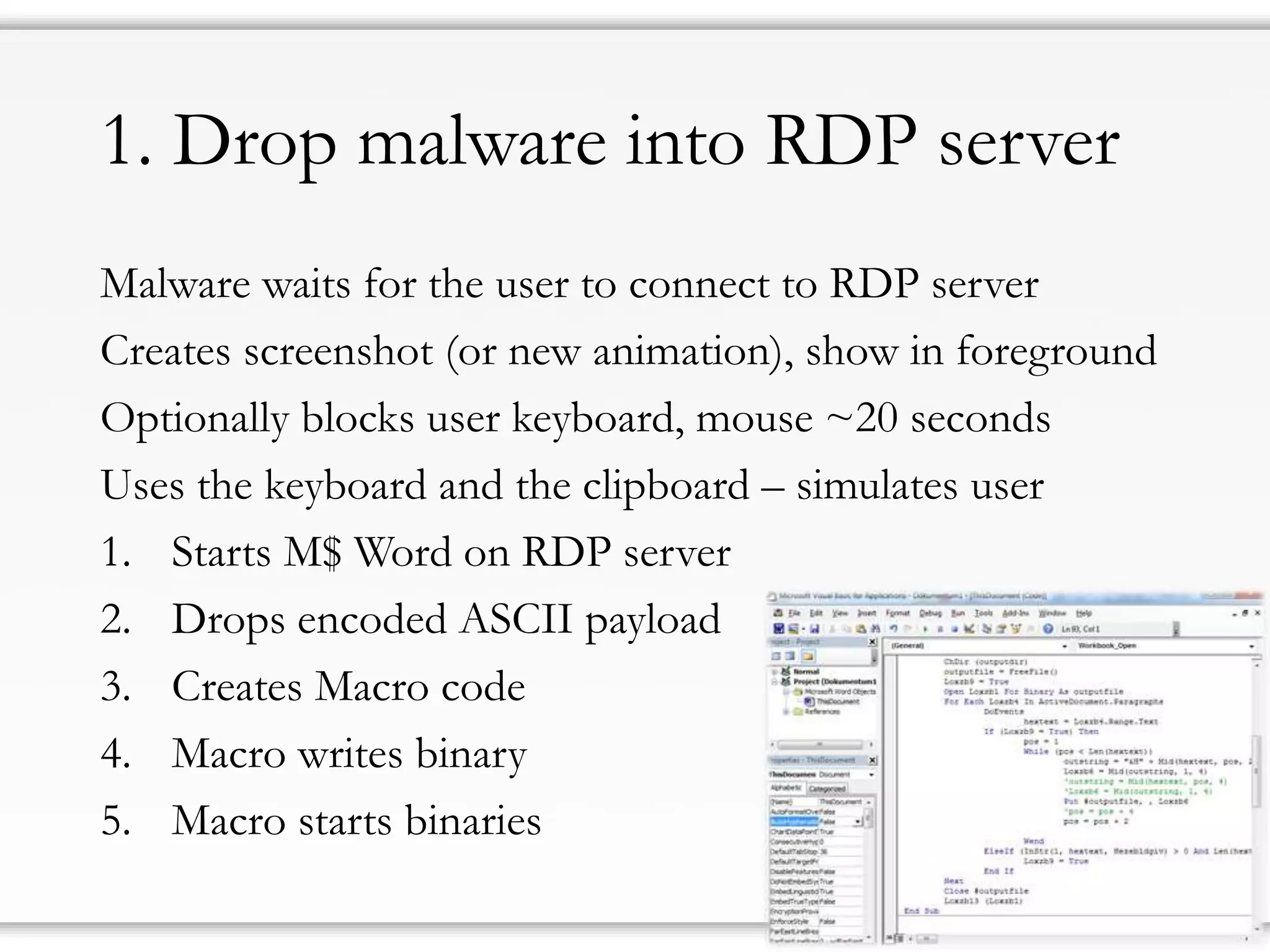
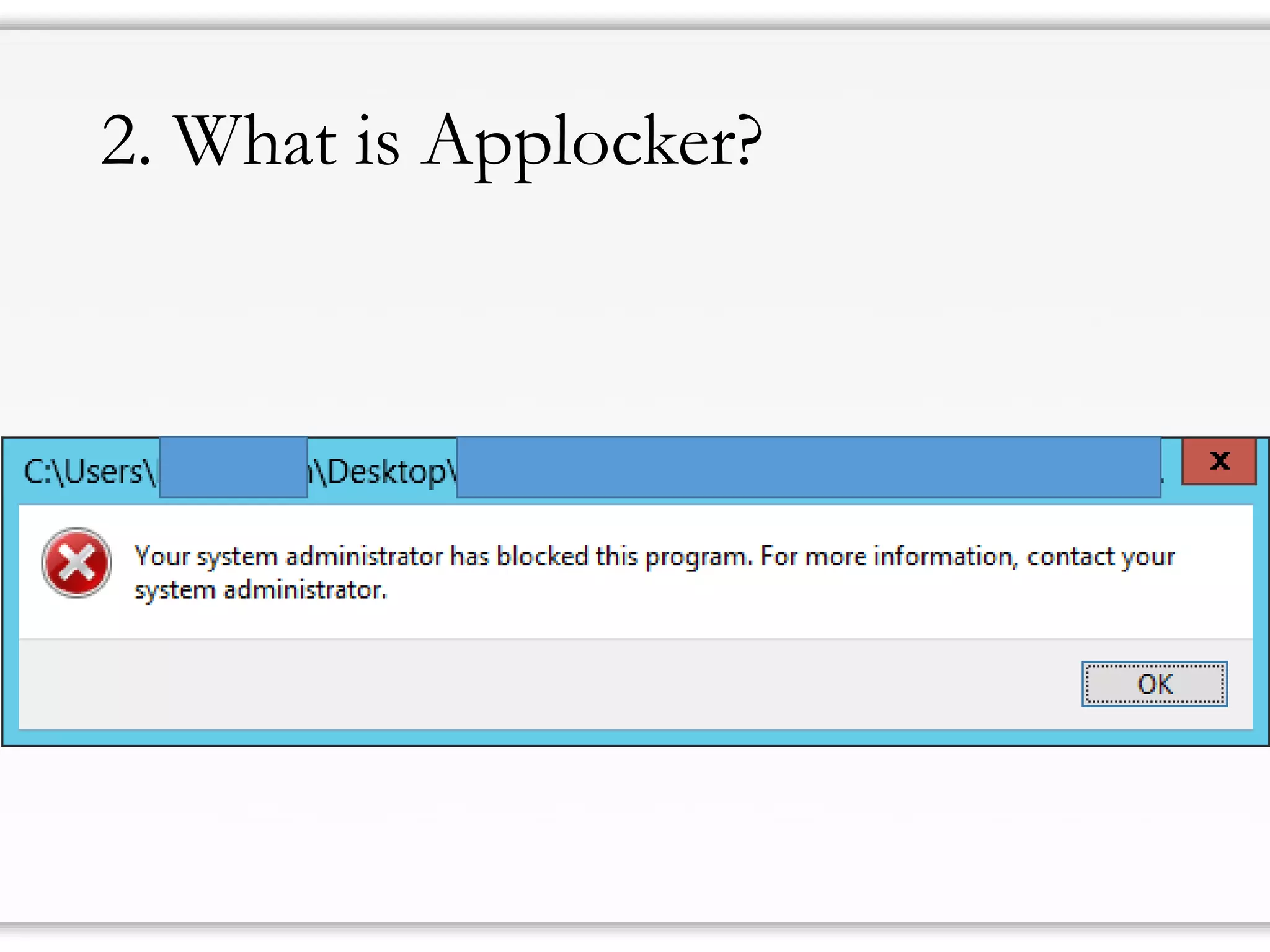
The document details strategies for bypassing firewalls and application whitelists to gain access to secure remote desktop servers. It outlines a systematic approach to hacking involving malware deployment, code execution, privilege escalation, and firewall evasion techniques. Key tools and methods are discussed for both red teams (attackers) and blue teams (defenders) to improve security measures against such attacks.
















![Elevatetoadmin-Service exploit
C:> accesschk.exe–l mvulnservice.exe
[0] ACCESS_ALLOWED_ACE_TYPE: NT AUTHORITYTERMINAL SERVER USER
FILE_APPEND_DATA
FILE_EXECUTE
FILE_READ_ATTRIBUTES
FILE_READ_DATA
FILE_READ_EA
FILE_WRITE_ATTRIBUTES
FILE_WRITE_DATA
FILE_WRITE_EA
SYNCHRONIZE
READ_CONTROLs
C:> scsdshowmyvulnservice
D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)
(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRCRPWP;;;IU)(A;;CCLCSWLOCRRC;;;SU)](https://image.slidesharecdn.com/highsechackredact-140809110411-phpapp01/75/DEFCON-22-Bypass-firewalls-application-white-lists-secure-remote-desktops-in-20-seconds-30-2048.jpg)
![Elevatetoadmin-Service exploit
C:> accesschk.exe–l mvulnservice.exe
[0] ACCESS_ALLOWED_ACE_TYPE: NT AUTHORITYTERMINAL SERVER USER
FILE_APPEND_DATA
FILE_EXECUTE
FILE_READ_ATTRIBUTES
FILE_READ_DATA
FILE_READ_EA
FILE_WRITE_ATTRIBUTES
FILE_WRITE_DATA
FILE_WRITE_EA
SYNCHRONIZE
READ_CONTROLs
C:> scsdshowmyvulnservice
D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)
(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRCRPWP;;;IU)(A;;CCLCSWLOCRRC;;;SU)
Allow
Service start
Service stop
Interactivelyloggedonuser](https://image.slidesharecdn.com/highsechackredact-140809110411-phpapp01/75/DEFCON-22-Bypass-firewalls-application-white-lists-secure-remote-desktops-in-20-seconds-31-2048.jpg)