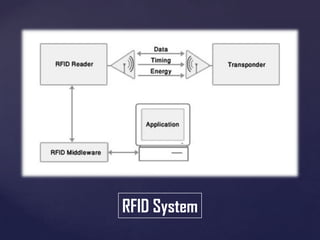
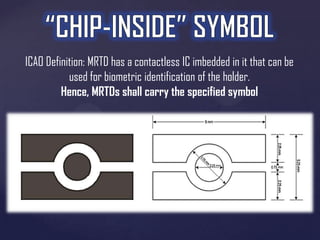
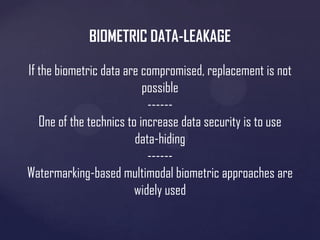
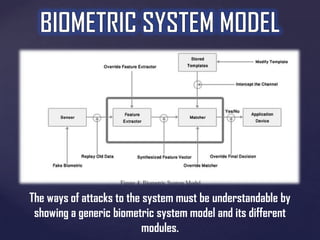
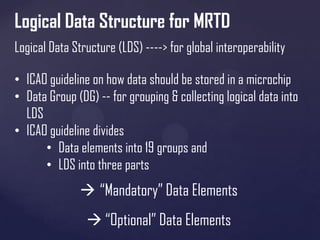
The document discusses the evolution of biometric passports and their security features, highlighting the importance of machine-readable zones and the integration of biometric data for identity verification. It outlines the security mechanisms, including encryption methods, that protect against various threats such as eavesdropping and cloning. Additionally, it notes compliance with International Civil Aviation Organization (ICAO) standards and variations in e-passport implementations across different countries.









![Biometric passport = E-passport
Paper & electronic identity credential
Contains biometrics features for authentication of travellers
Contains chip & antenna enclosed in front/back/central page
Chip storing the user’s information
Also contains biometric identifiers [depending on various
countries choice and technical evolution]
• Recommended file formats & communication protocols
followed
•
•
•
•
•
•](https://image.slidesharecdn.com/machinereadabletraveldocuments-131201064321-phpapp02/85/Machine-Readable-Travel-Documents-MRTD-Biometric-Passport-11-320.jpg)