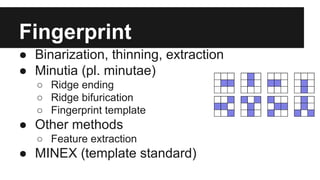
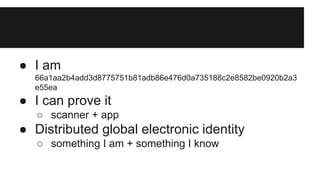
This document discusses biometric identification and its uses and challenges. It describes how biometrics like fingerprints, iris scans, and DNA can be used to identify individuals but also how current biometric systems have security flaws. Centralized biometric databases are vulnerable if hacked and fingerprints can be fooled. The document proposes a future where biometric hashes combined with passwords provide secure, anonymous digital identities without centralized databases's risks.