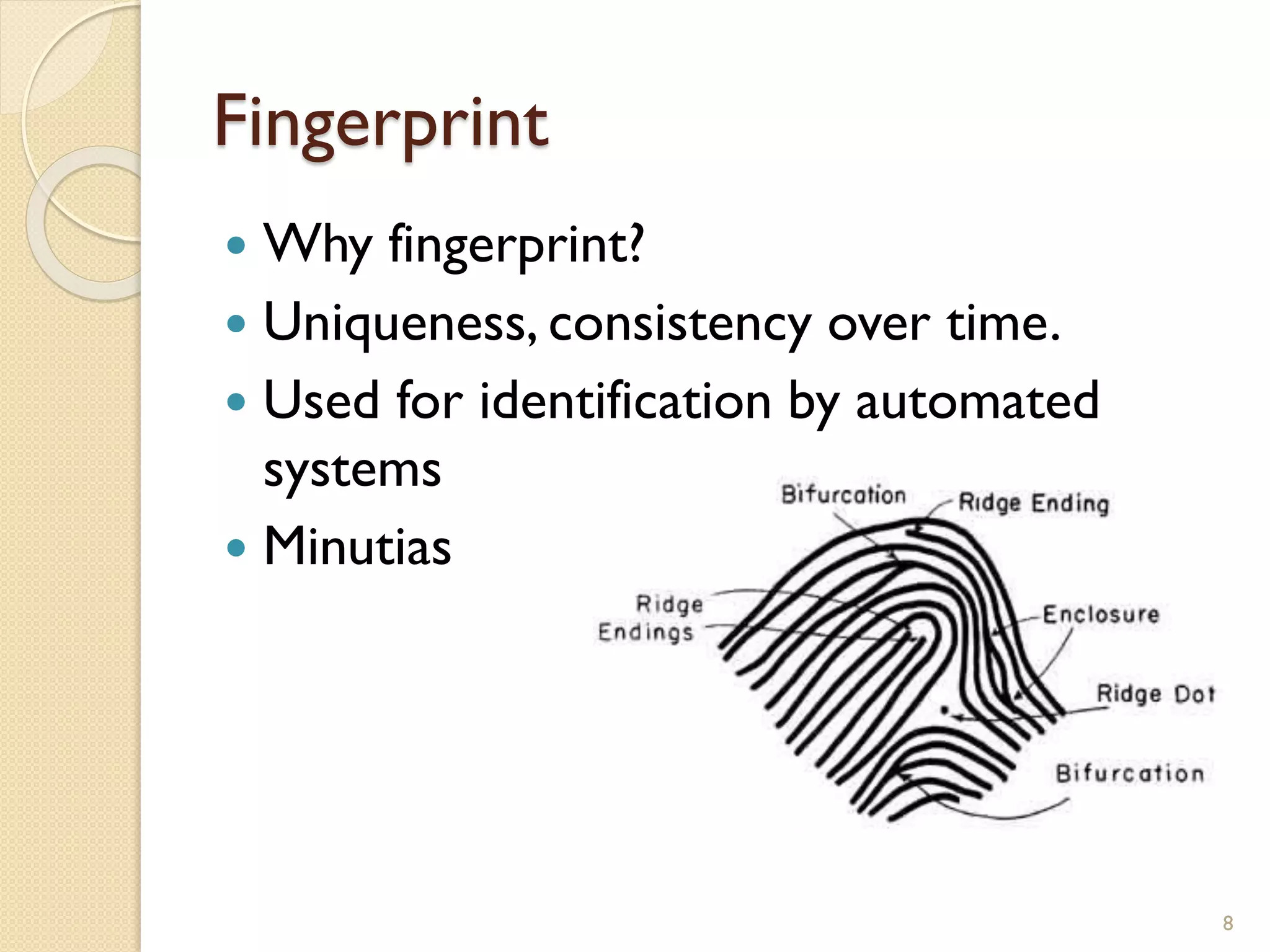
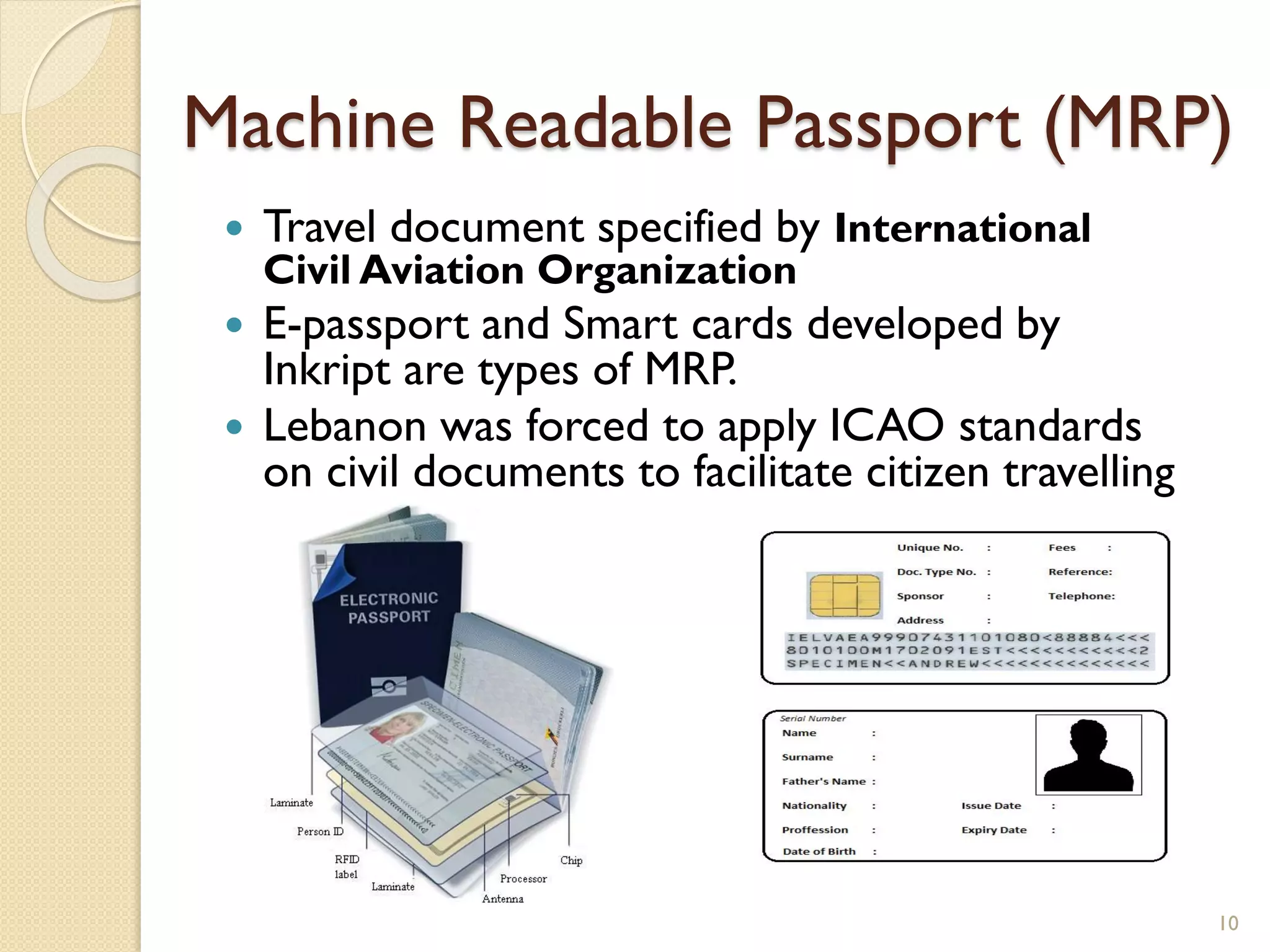
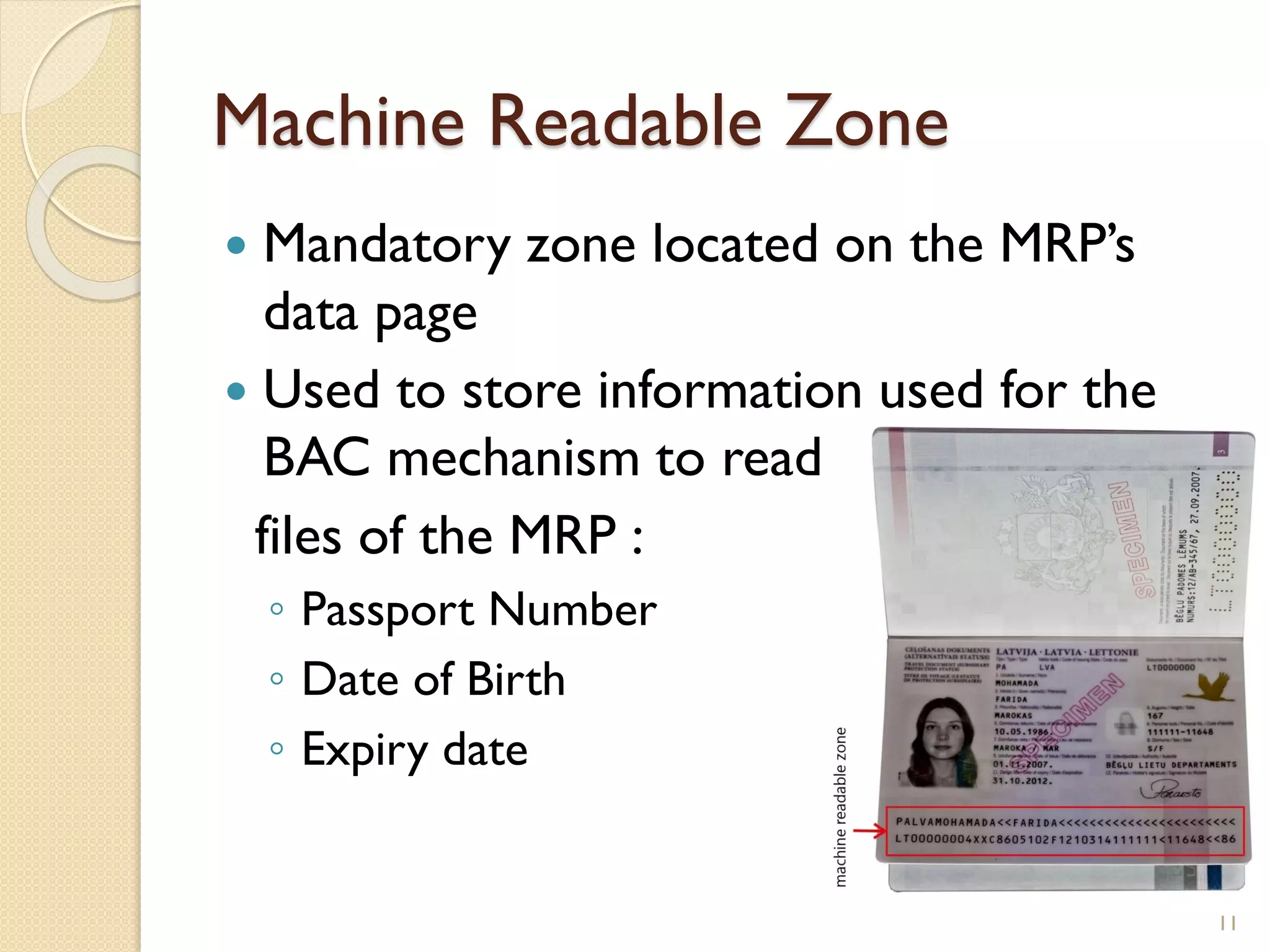
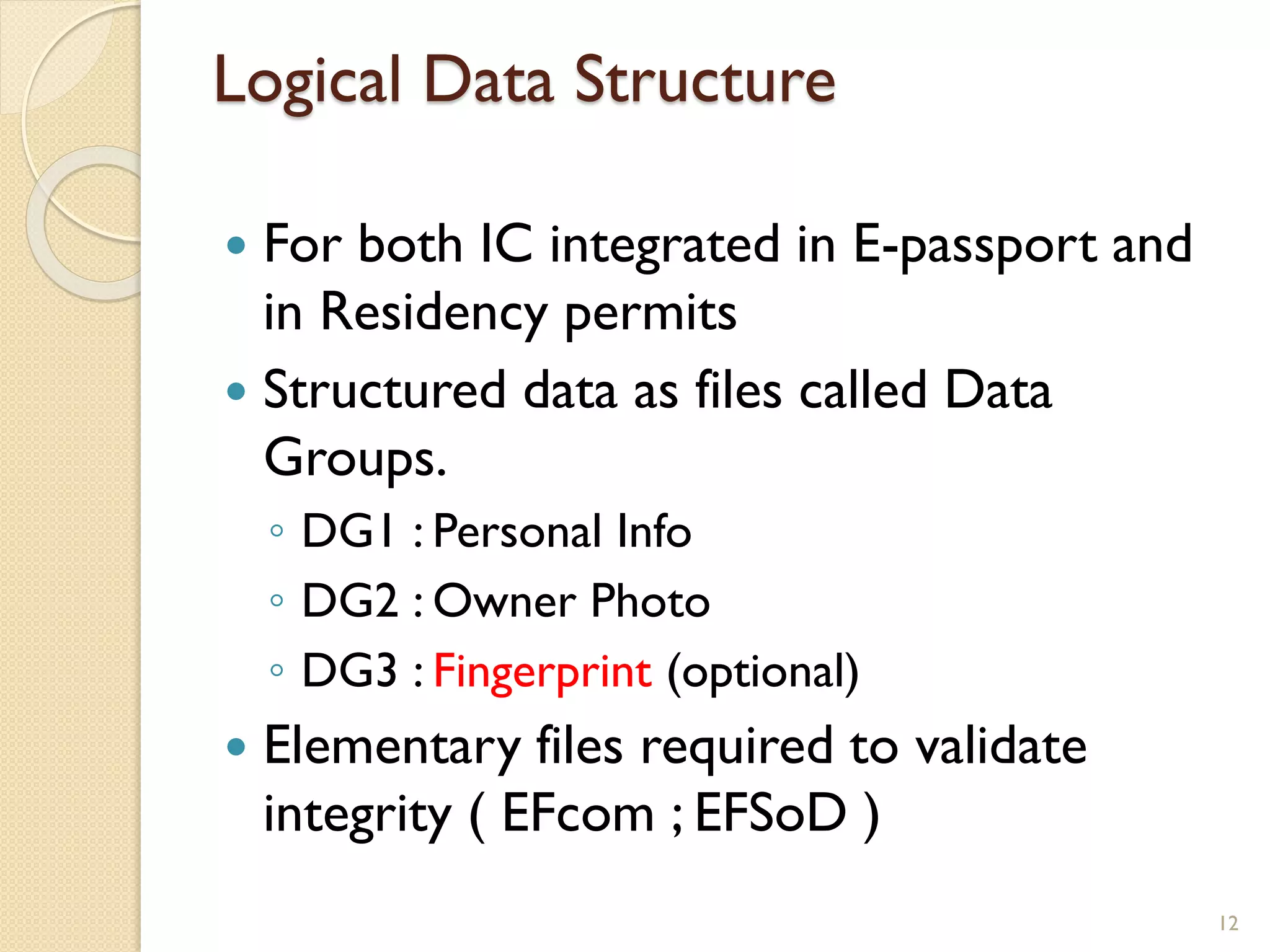
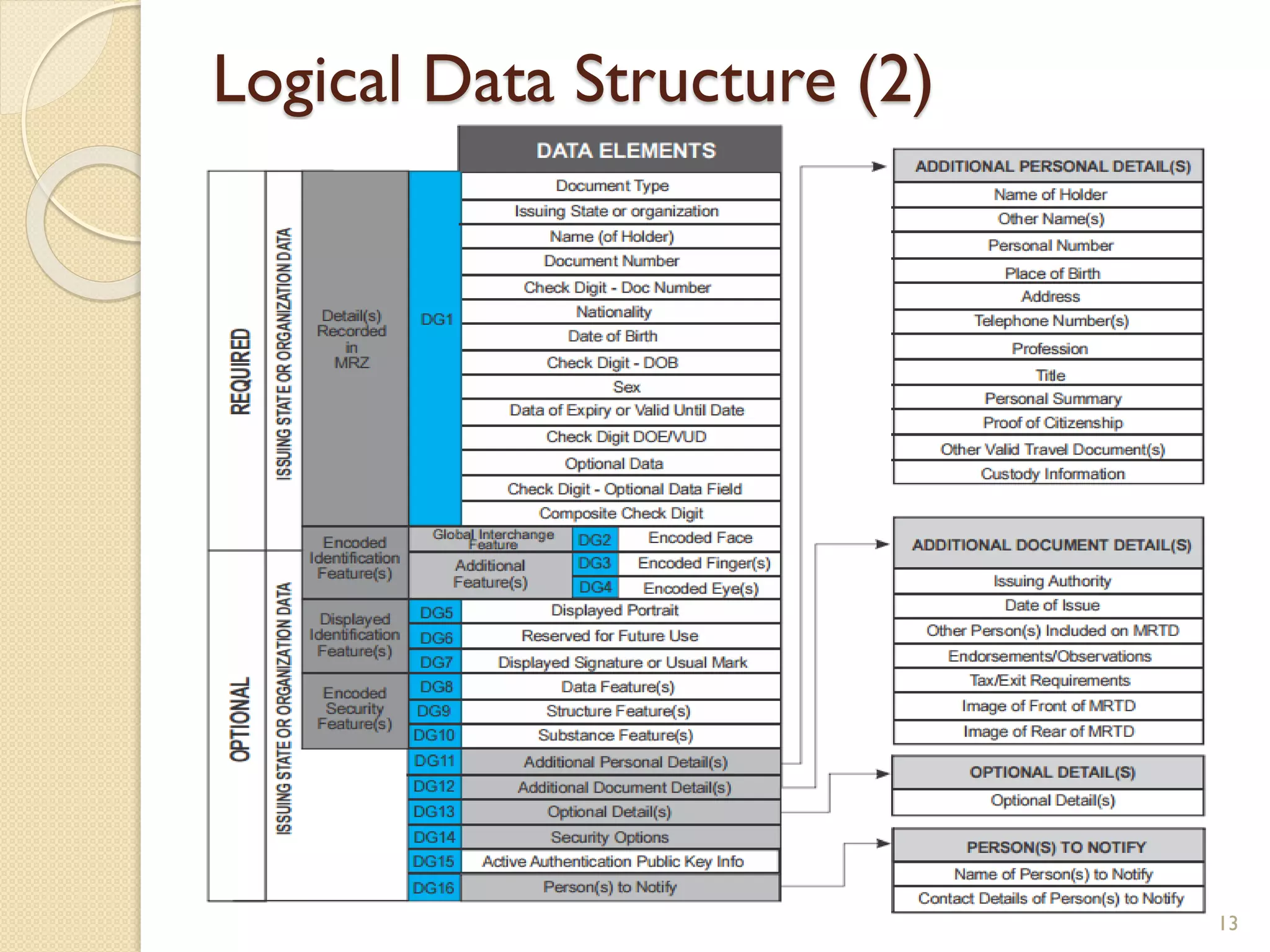
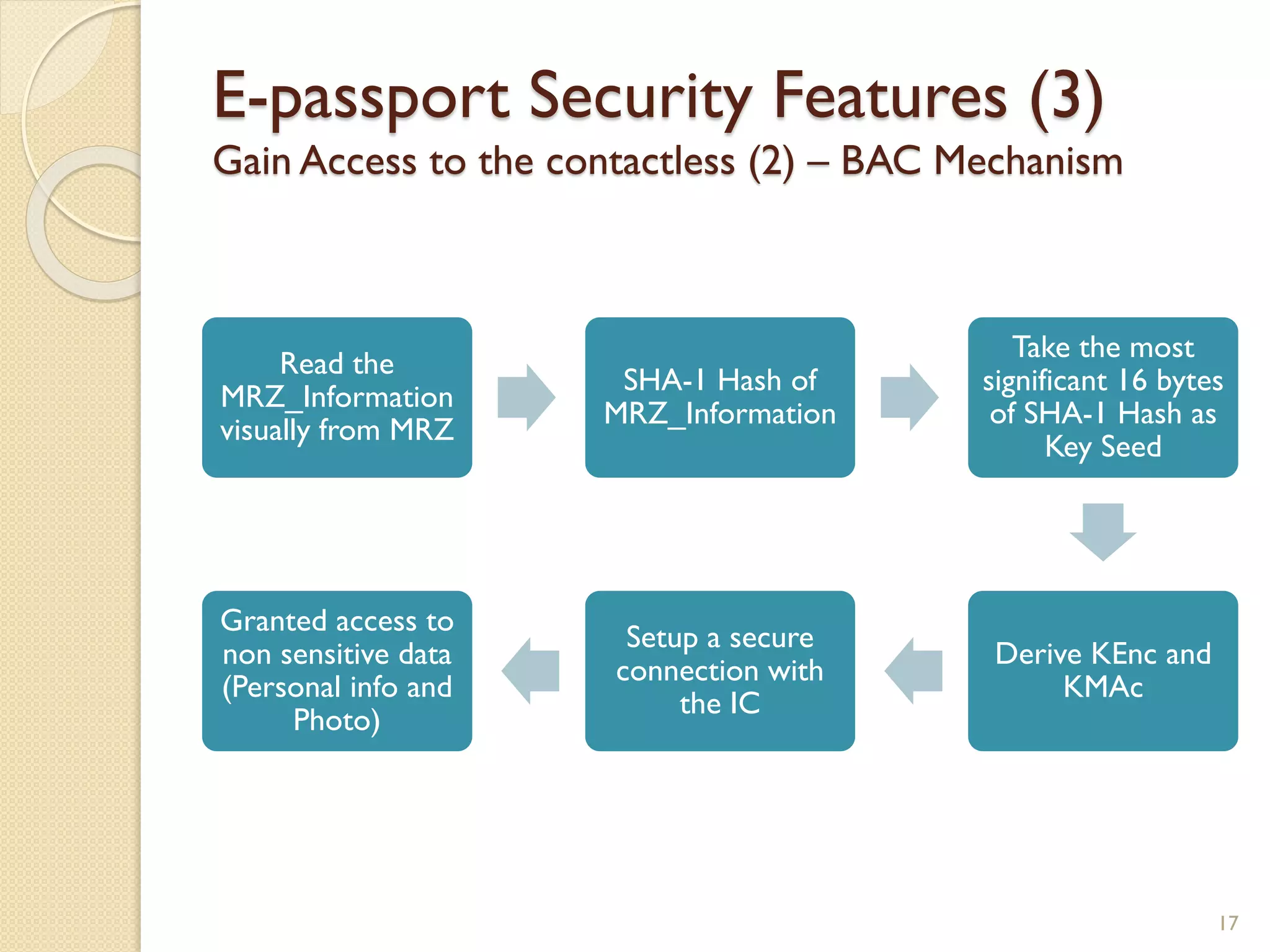
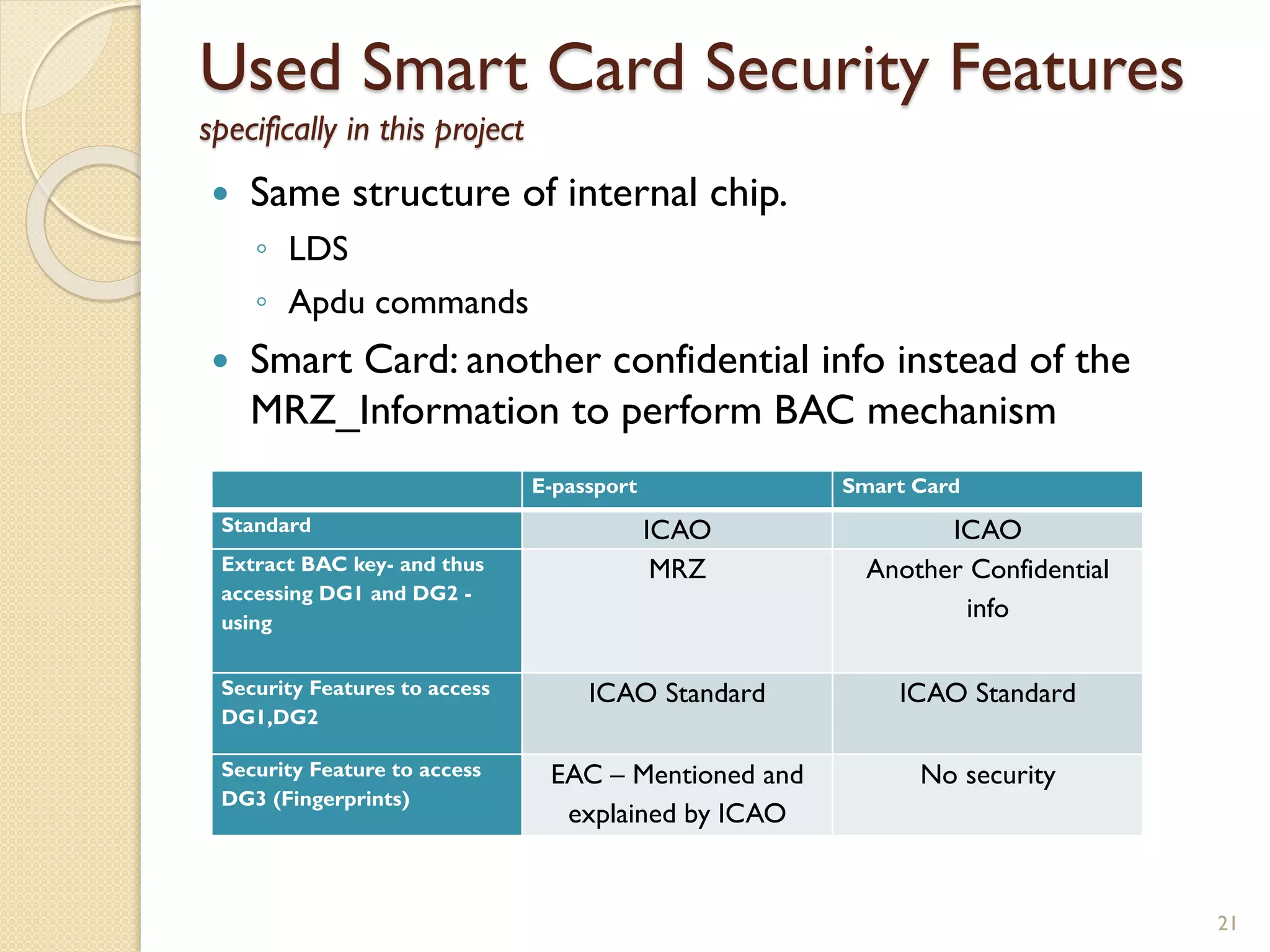
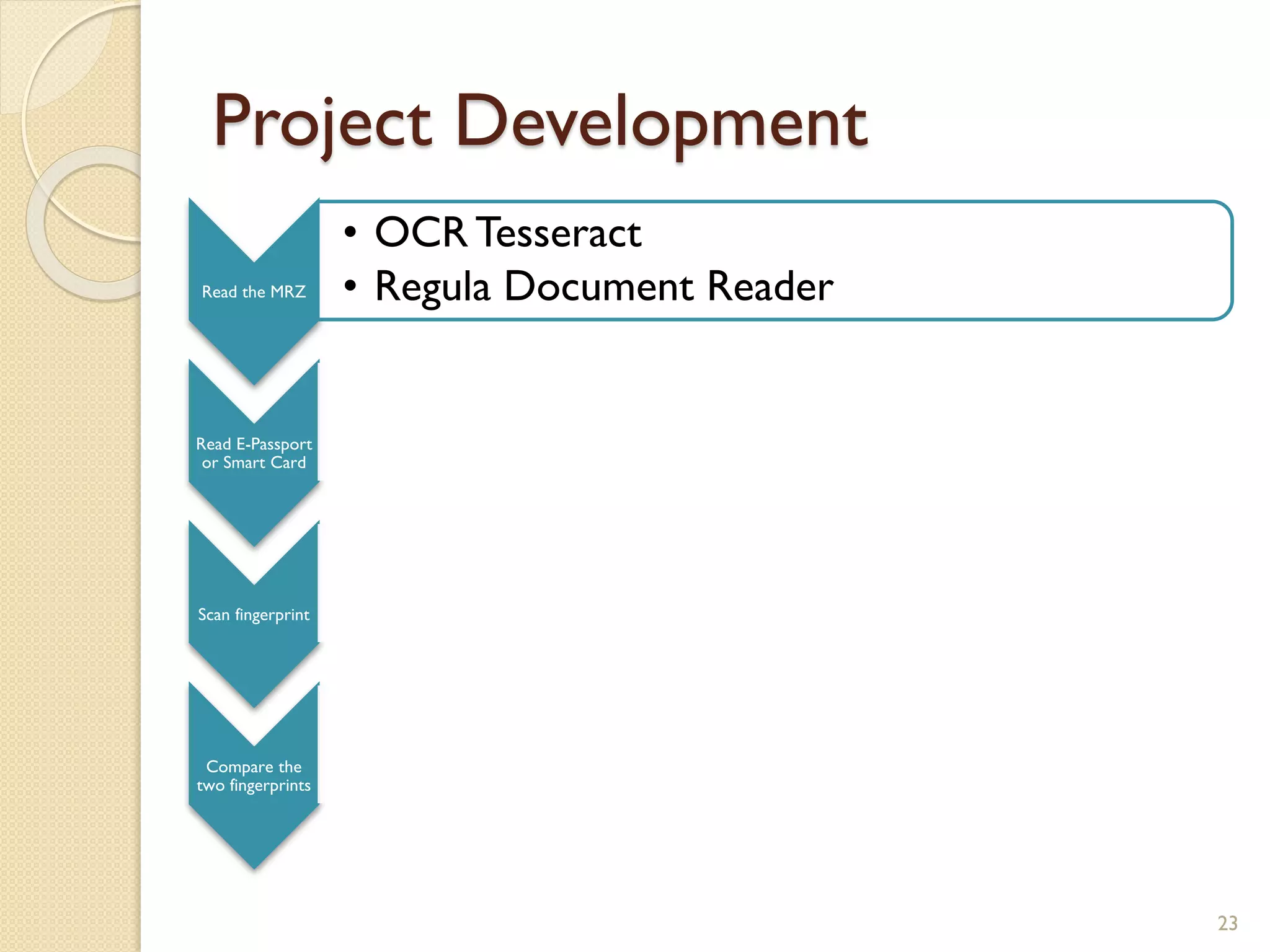
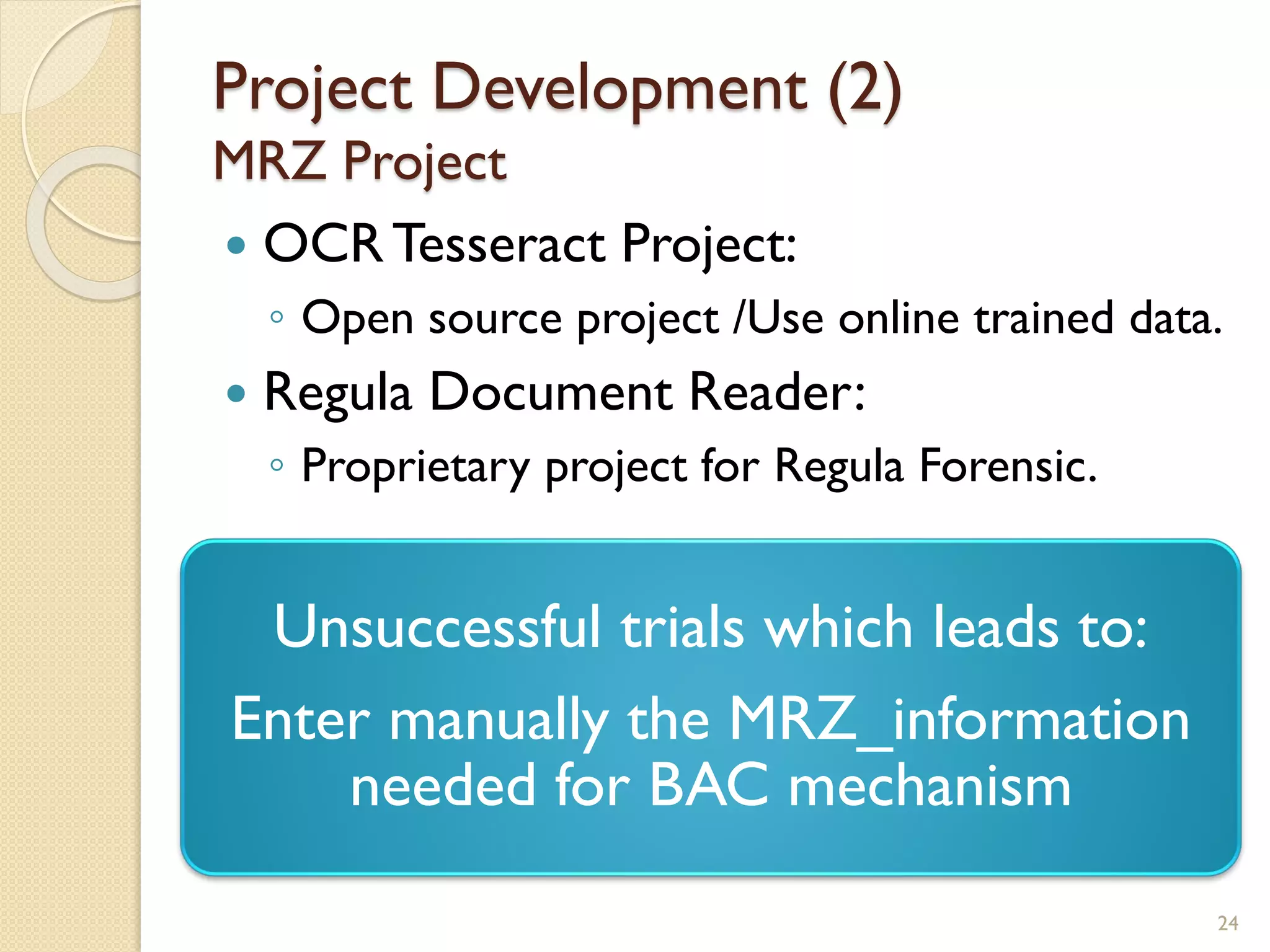
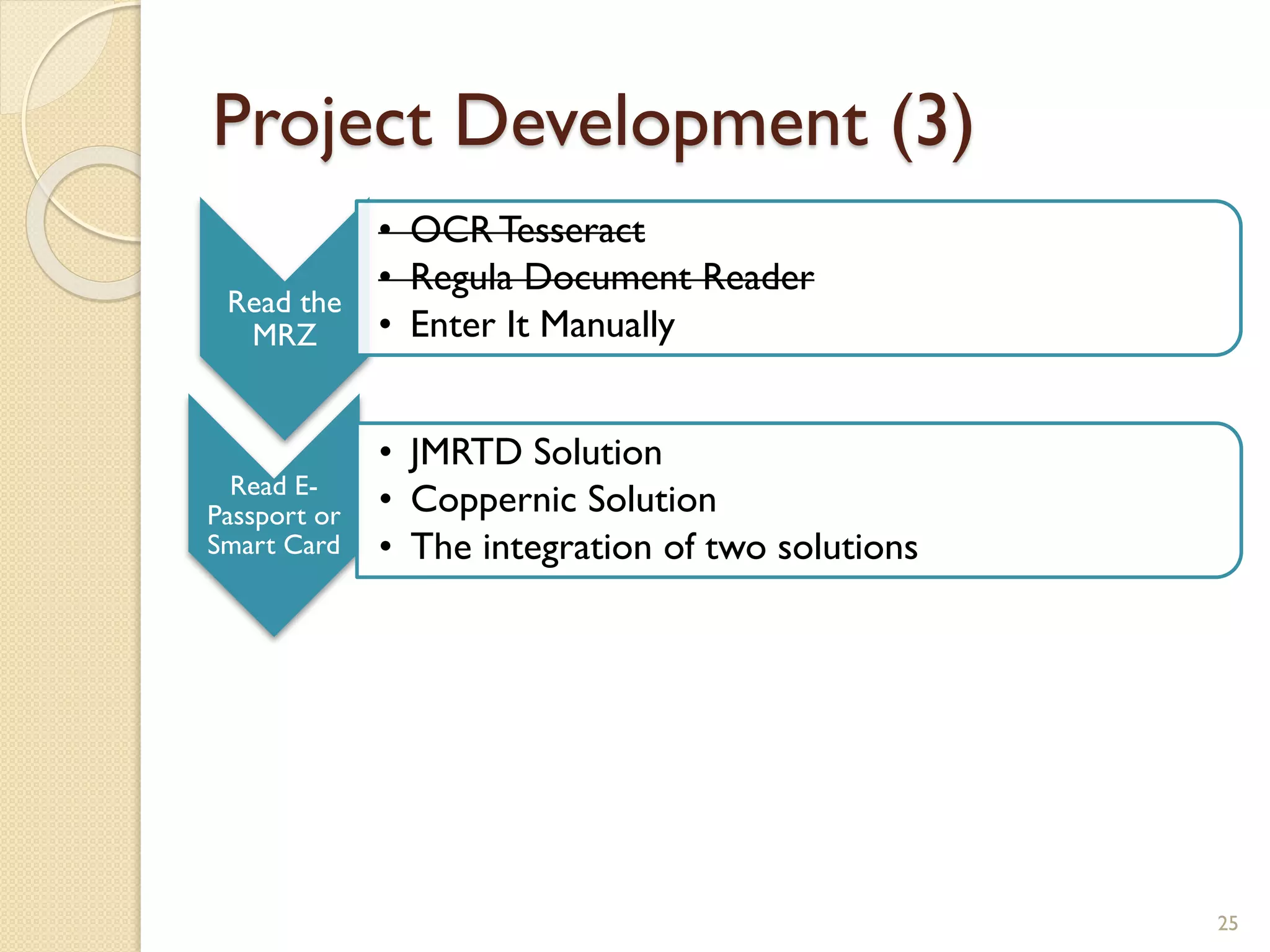
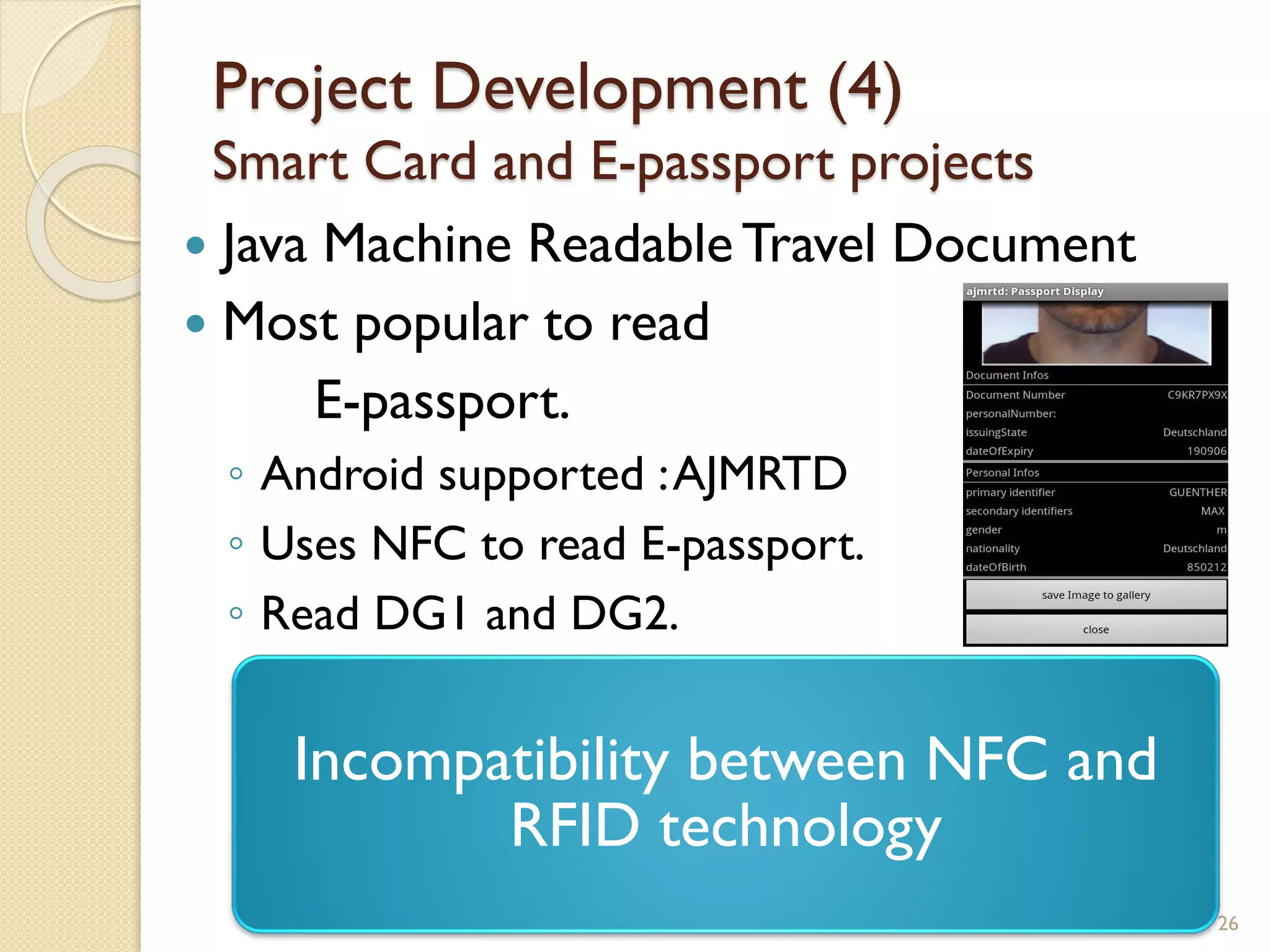
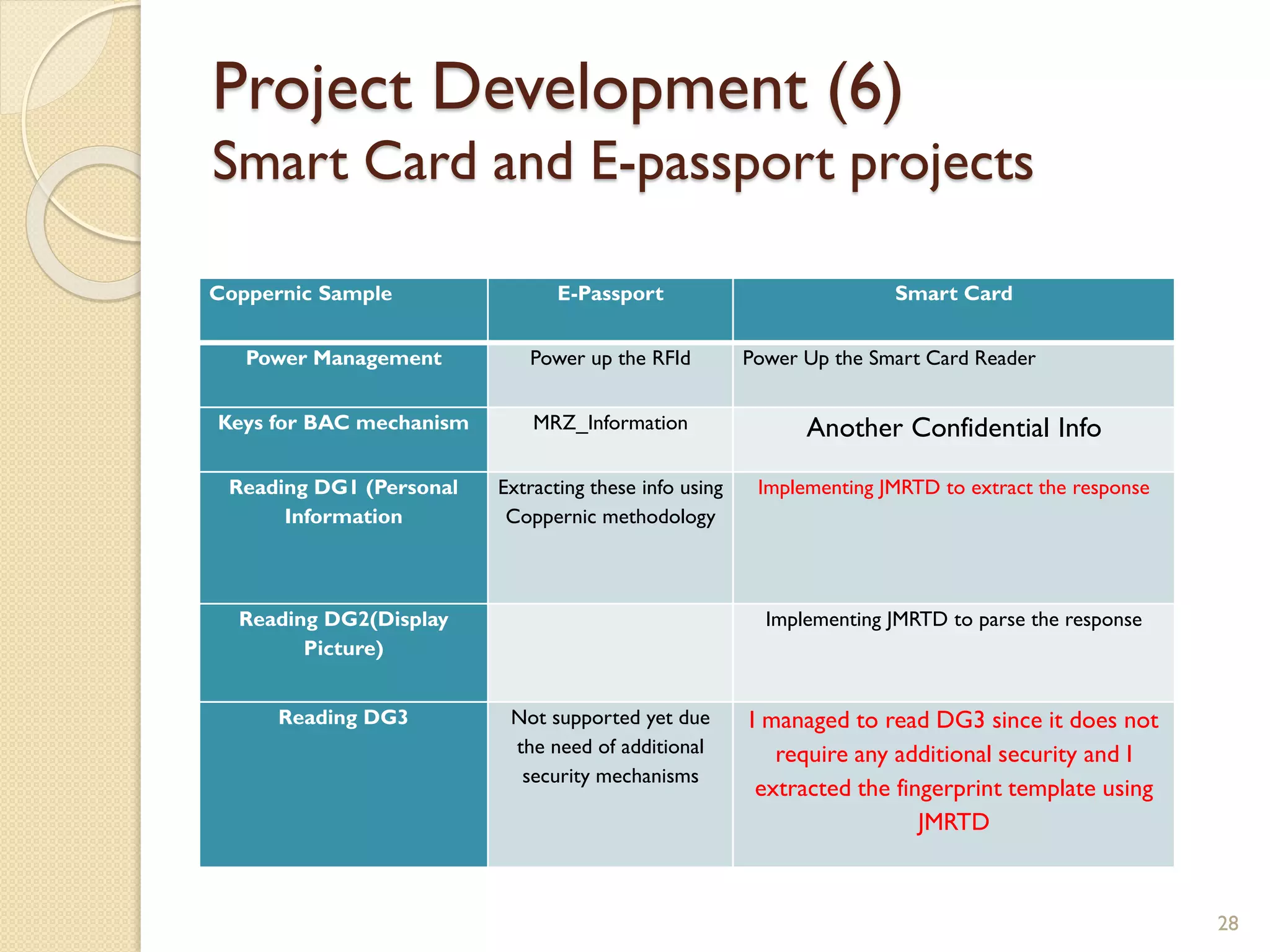
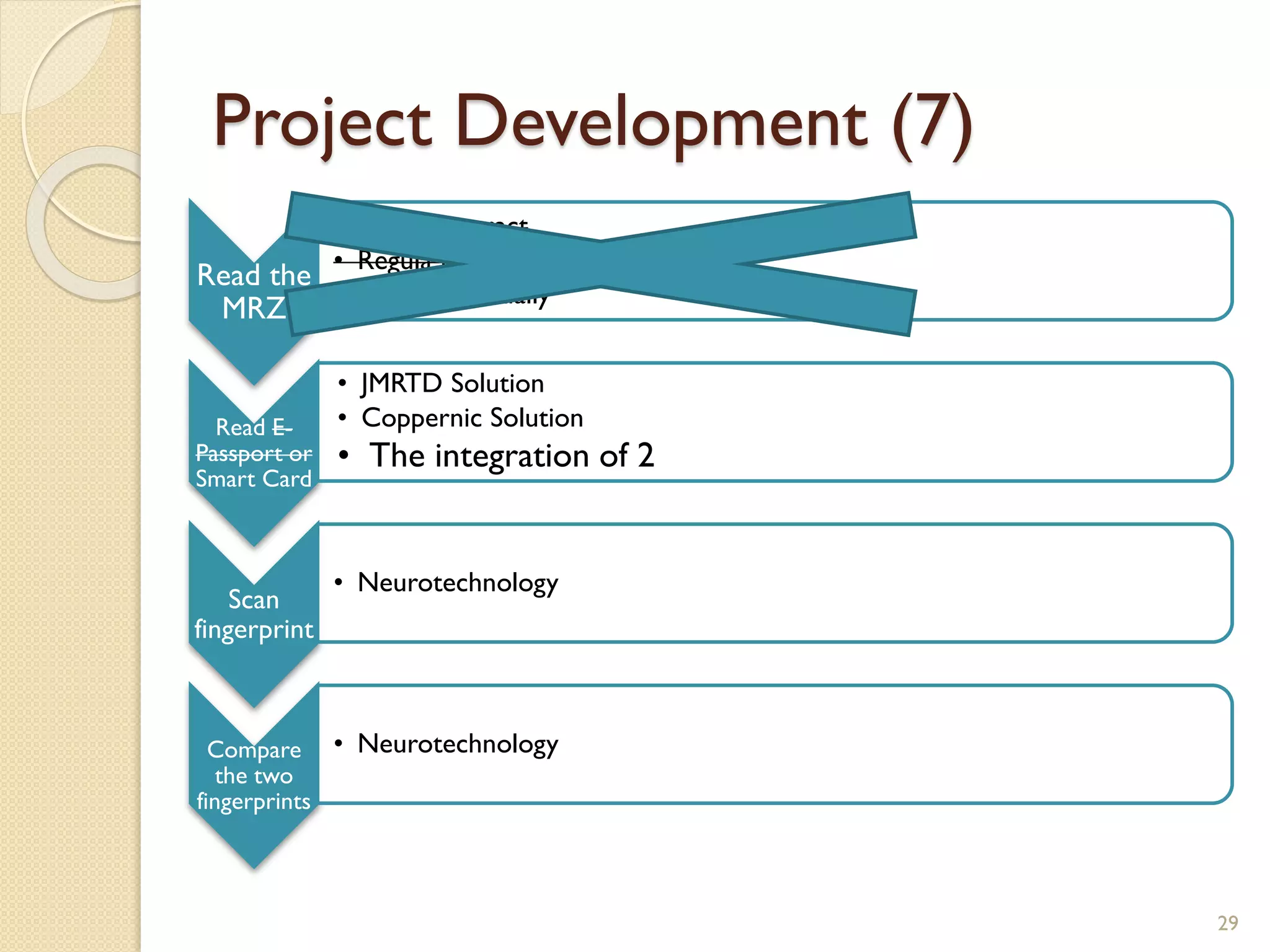
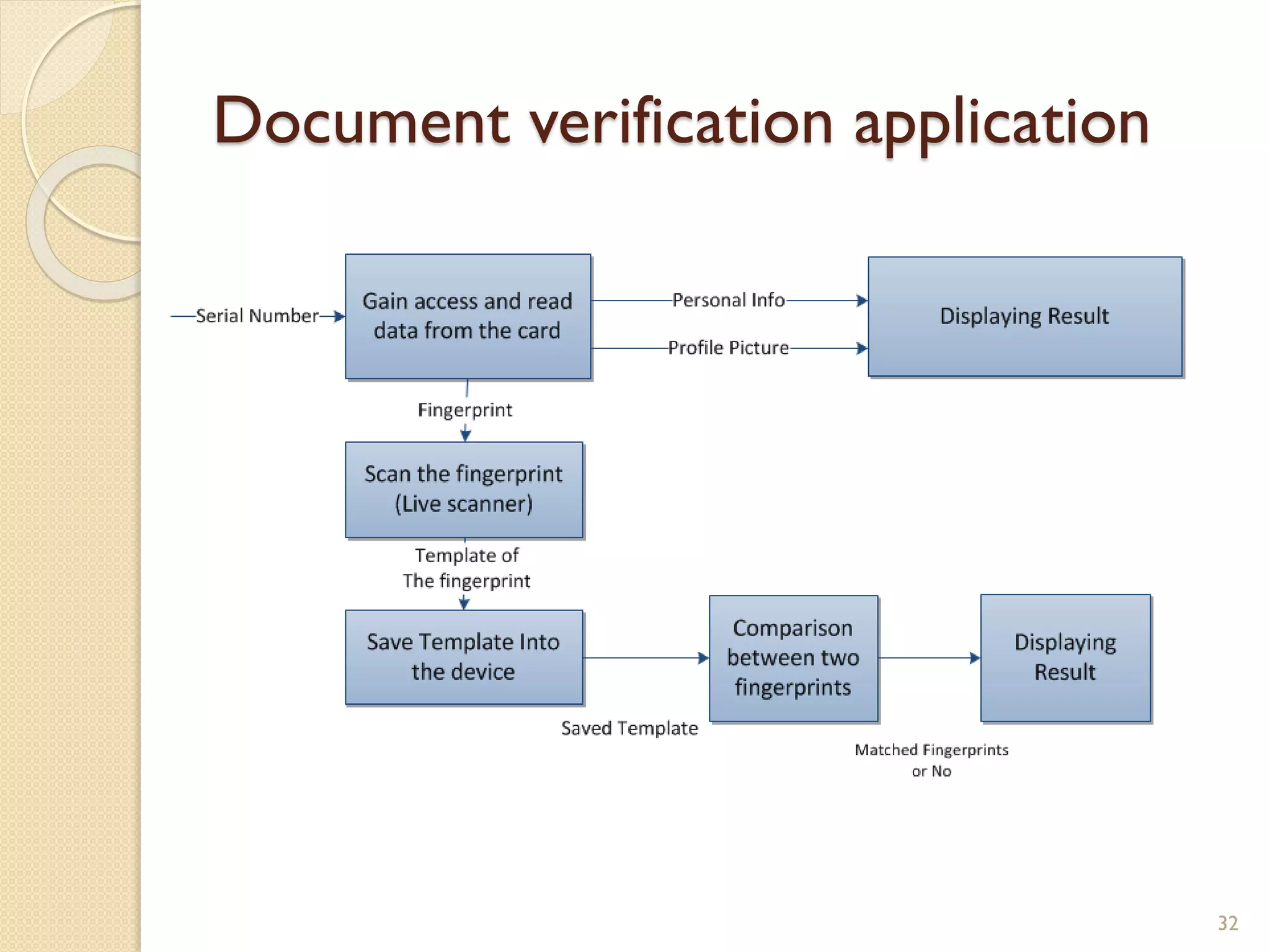
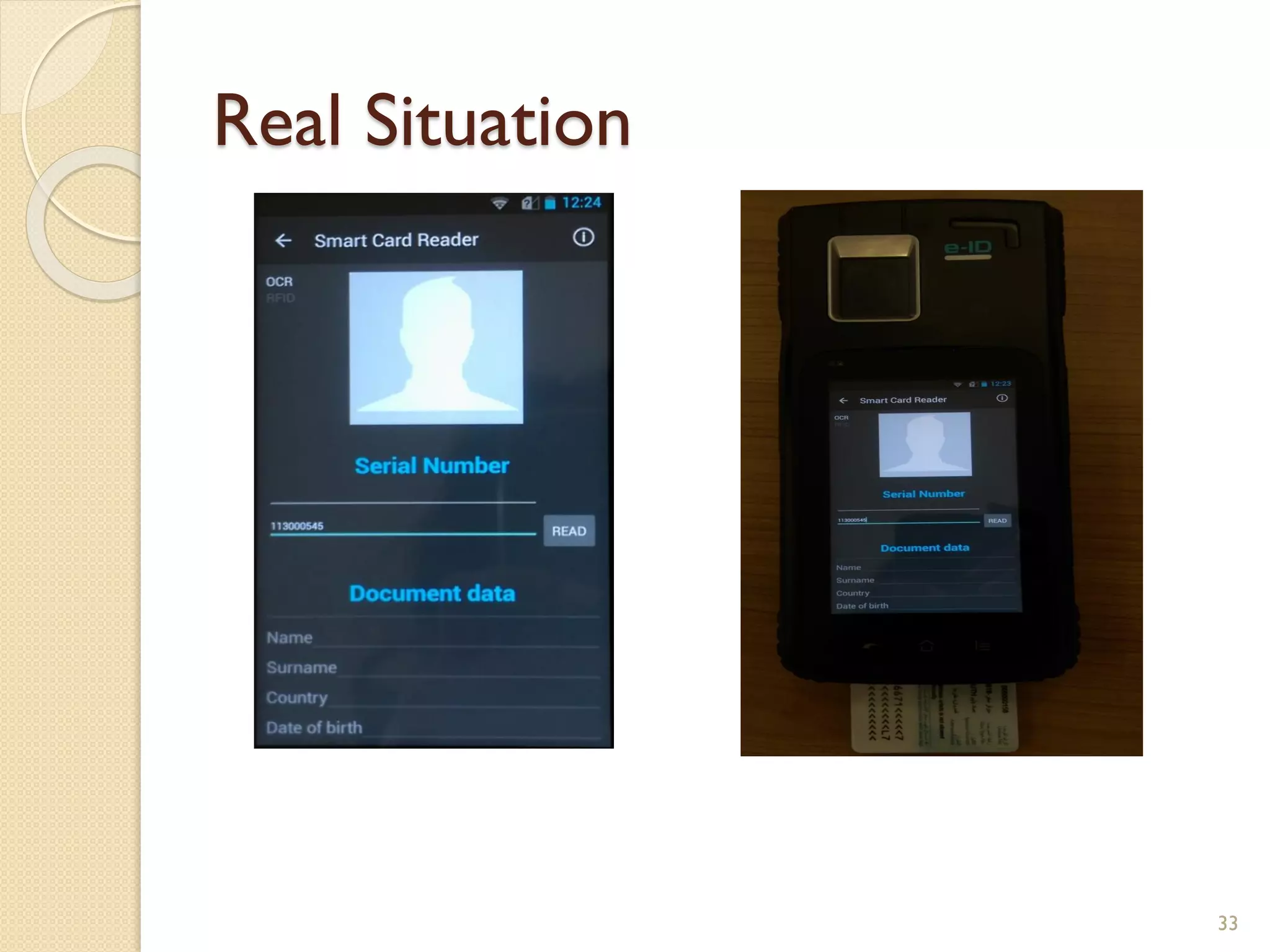
The document discusses a project to develop a mobile application for verifying identity documents using a C-One E-ID handheld device. The application extracts data like fingerprints from documents and ID cards, compares the extracted data to the holder's live fingerprints scanned using the device, and verifies their identity. The document outlines the technologies used including fingerprint biometrics, machine readable travel documents, smart cards, and security features to access identity data. It describes the challenges faced in extracting data from documents and the partial success in developing applications to verify e-passports and smart ID cards by reading selected data fields and fingerprints.