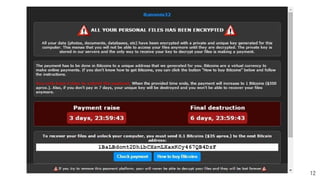
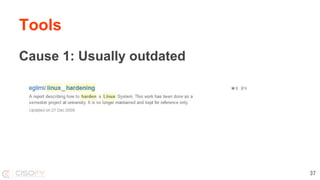
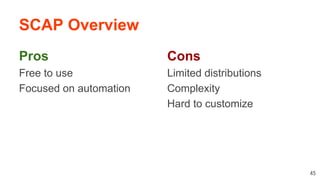
The document discusses the importance of hardening Linux systems to improve security through various strategies, including system hardening, security auditing, and utilizing tools such as Lynis and SCAP. It emphasizes that security is an ongoing process requiring continuous monitoring and improvements. The presentation also covers the benefits and drawbacks of different hardening resources and tools available to enhance system security.