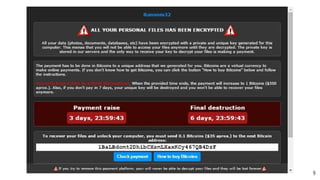
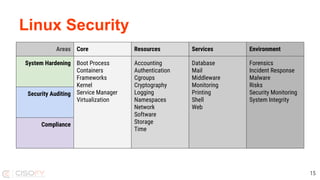
The document outlines a presentation by Michael Boelen on Linux security scanning using Lynis, aimed at performing security audits and system hardening. It covers the importance of an ongoing security process, the function of Lynis as an easy-to-use auditing tool without installation, and various strategies for enhancing Linux system security. The presentation emphasizes simplicity, continuous improvement, and the necessity of open-source contributions to maintain and evolve security practices.