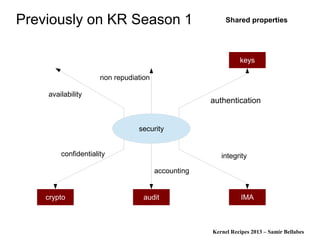
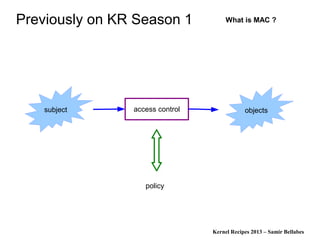
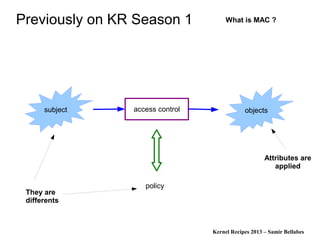
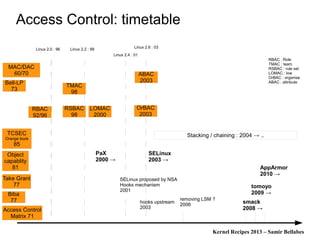
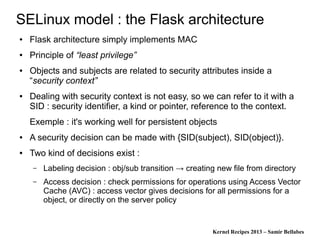
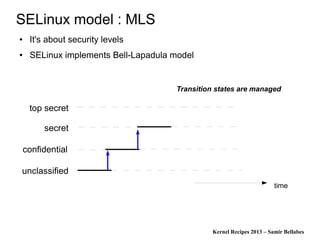
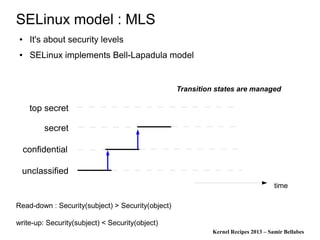
The document discusses various Linux security modules, including SELinux, AppArmor, and Tomoyo, detailing their history, models, and security mechanisms. It outlines their architectures, such as the Flask architecture for SELinux, and covers concepts like role-based access control, type enforcement, and multi-level security. Additionally, it summarizes the Linux Security Summit 2013 and highlights the potential for using Linux Security Module hooks for managing information flow.


















![Kernel Recipes 2013 – Samir Bellabes
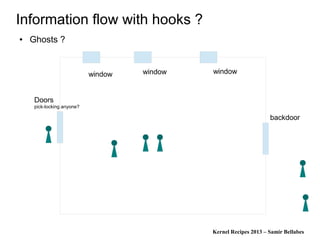
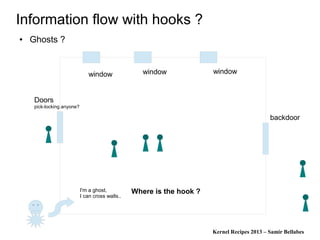
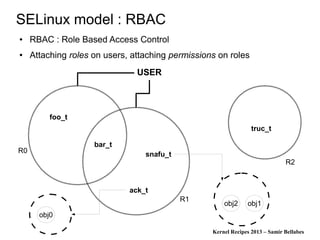
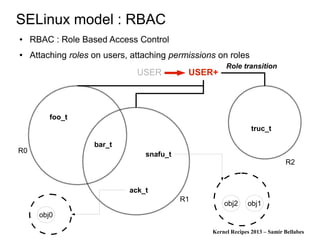
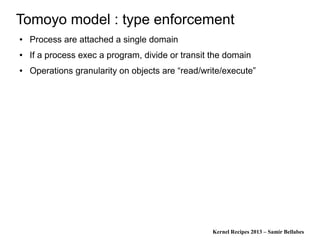
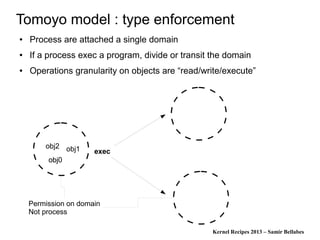
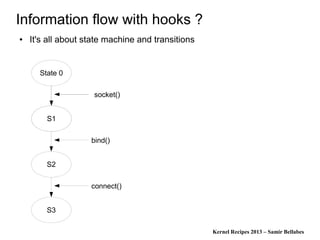
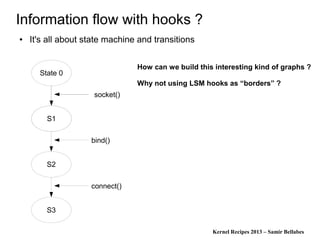
Information flow with hooks ?
● Let's take a memory buffer
● There are lots of functions which can modify m
– write(m,..), mmap(m,..), str*(m,..)
● Let's say you can actually don't miss a function which can modify m
and you can put a trap (hook) inside all this functions.
● So now you can have the graph ..
● What about m[10] = 0; ??
● How can you hook this operation ?](https://image.slidesharecdn.com/2013kernelrecipes-lsm-130930050725-phpapp01/85/Kernel-Recipes-2013-Linux-Security-Modules-different-formal-concepts-45-320.jpg)