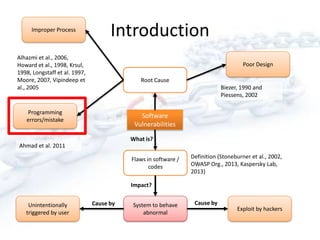
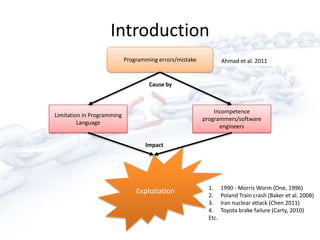
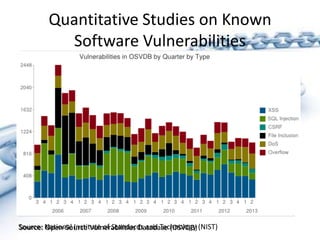
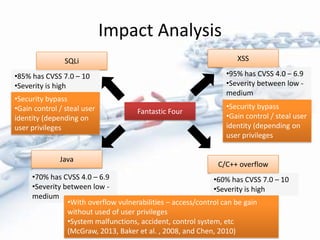
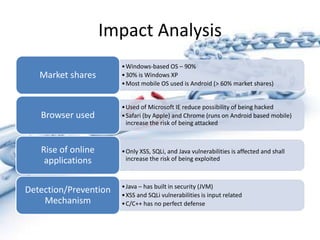
The document discusses past, present, and future vulnerabilities in computer systems, focusing on both software and hardware issues and their exploitation. It highlights significant past incidents of exploitation, the increase in identified vulnerabilities, and the prediction that certain vulnerabilities like C/C++ will remain critical threats. Quantitative studies reveal a persistent rise in vulnerabilities and underscore the impact of exploitation on various systems.