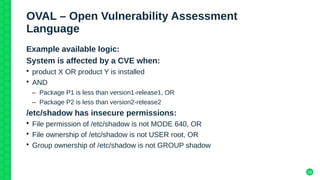
The document discusses the importance of security automation in managing the growing complexity of the software supply chain, particularly in response to vulnerabilities like SolarWinds and Log4Shell. Key topics include the Secure Content Automation Protocol (SCAP) and its various components such as CVE, CVSS, and SBOM, as well as the evolution of security reporting formats like CVRF and CSAF. The presentation emphasizes the need for effective inventory and security measures as software becomes increasingly interconnected and susceptible to attacks.