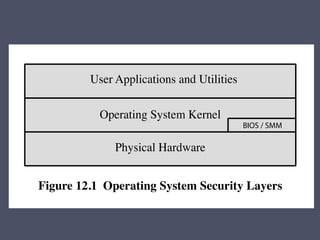
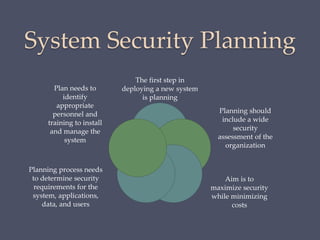
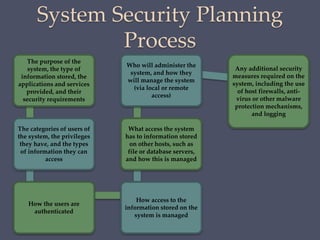
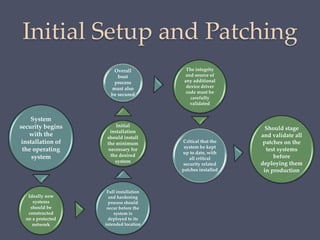
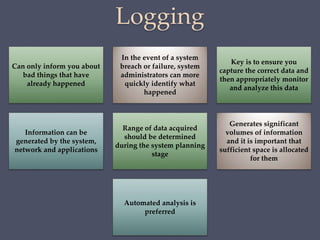
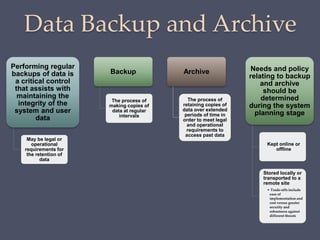
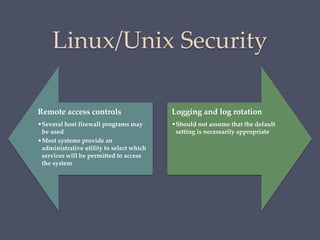
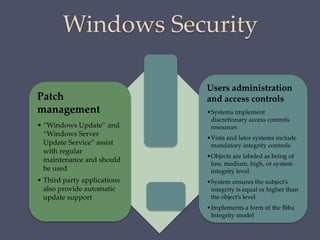
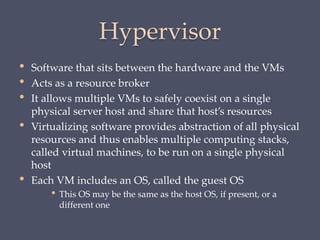
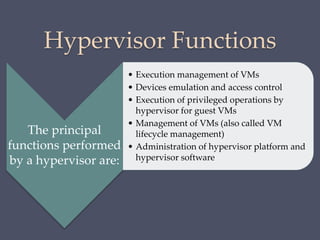
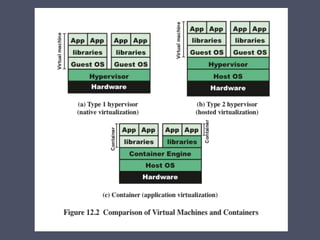
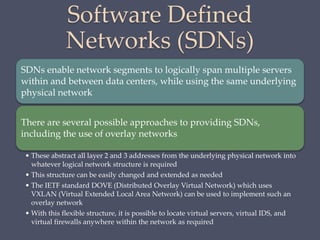
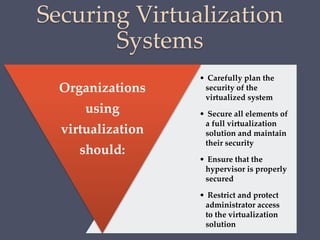
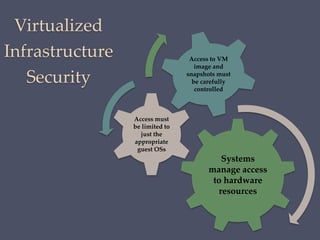
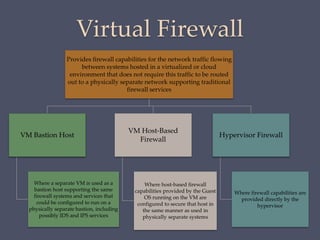
The document discusses strategies for securing operating systems and virtualized systems. It recommends planning security from the start, hardening the base OS by removing unnecessary software and configuring users/groups properly. Key steps include patching, additional security tools like antivirus, and testing security. For virtual systems, the hypervisor and virtual infrastructure need protection, and network traffic between VMs requires firewalls. Overall secure configuration of all system elements is important for maintaining security.