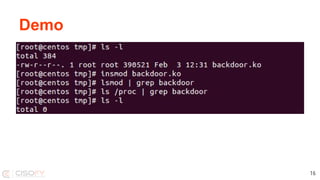
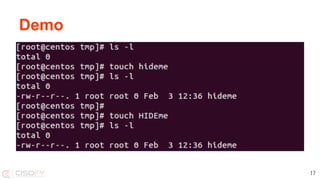
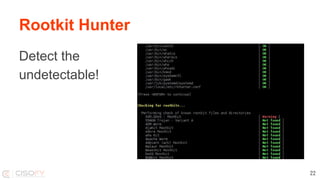
The document discusses strategies for understanding and mitigating Linux system intrusions, focusing on rootkits, malware handling, and potential defenses. It highlights common vulnerabilities, detection challenges, and the necessity for security tools and practices such as system hardening and continuous scanning. The presentation concludes with the importance of detection, restoration, and ongoing learning to enhance security measures.