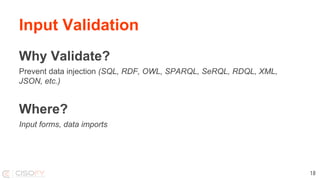
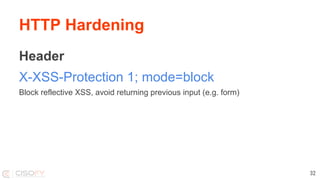
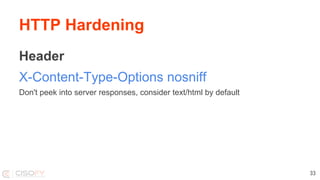
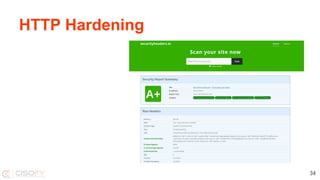
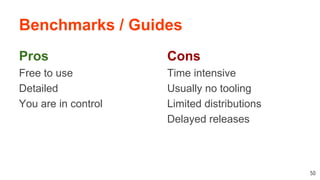
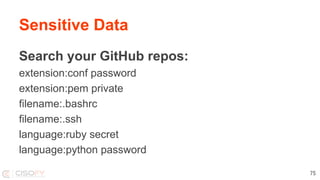
This document discusses securing Linux systems and applications as a developer. It begins by outlining common security risks like weak passwords, lack of input validation, and unintended data exposure. It then provides strategies to improve security in three levels: basics like validation and encryption; taking ownership of code and systems; and performing security audits. Specific techniques are covered like hardening operating systems, software, and network configuration. The document recommends using the Lynis security auditing tool for its flexibility and simplicity. It concludes by discussing the importance of continuous auditing and leveraging security to save time instead of crisis management.