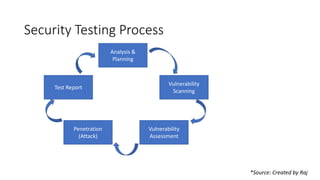
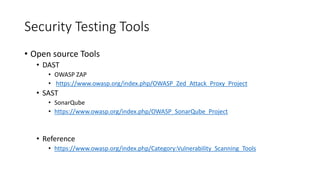
Security testing is the process of identifying vulnerabilities in a system to protect data and ensure intended functionality. It involves testing confidentiality, integrity, authentication, availability, authorization, and non-repudiation. The security testing process includes planning, vulnerability scanning, assessment, penetration testing, and reporting. Types of security testing include static application, dynamic application, and penetration testing. The OWASP Top 10 list identifies the most critical web application security risks.