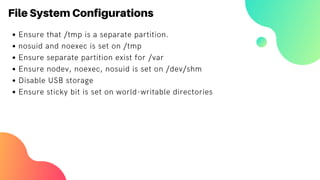
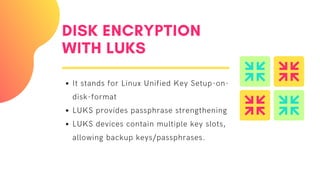
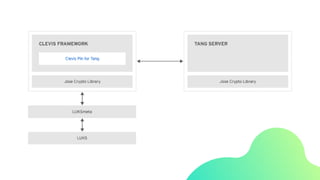
The document elaborates on server hardening methodologies, emphasizing the importance of enhancing server security through hardware and software measures. Key topics include disk encryption using LUKS, network-bound disk encryption (NBDE), filesystem configurations, and user security settings. It also introduces the OpenSCAP tool for evaluating security compliance and vulnerability assessments on Linux systems.






![CONFIGURING
TANG SERVER
# yum install tang
# systemctl enable tangd.socket -
-now
[enabling socket activation]
# firewall-cmd --zone=public --
add-service=http --permanent
[setting up the firewall]
# firewall-cmd --reload](https://image.slidesharecdn.com/serverhardeningmethedologies1-191020170744/85/Server-hardening-methedologies-10-320.jpg)

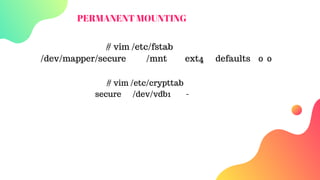
![Configuring clevis
# yum install clevis clevis-luks clevis-dracut -y
# cfg = $'{"t"=1,"pins":{"tang":[{"url":"http://192.168.0.5"}]}}'
# clevis luks bind -d /dev/vdb1 sss "$cfg"
or #clevis bind luks -d /dev/vdb1 tang '{"url":"http://tang.srv"}'
# systemctl enable clevis-luks-askpass.path
# vim /etc/crypttab
encryptedvdb1 /dev/vdb1 none _netdev
# vim /etc/fstab
/dev/mapper/encryptedvdb1 /encrypt xfs _netdev 1 2](https://image.slidesharecdn.com/serverhardeningmethedologies1-191020170744/85/Server-hardening-methedologies-12-320.jpg)