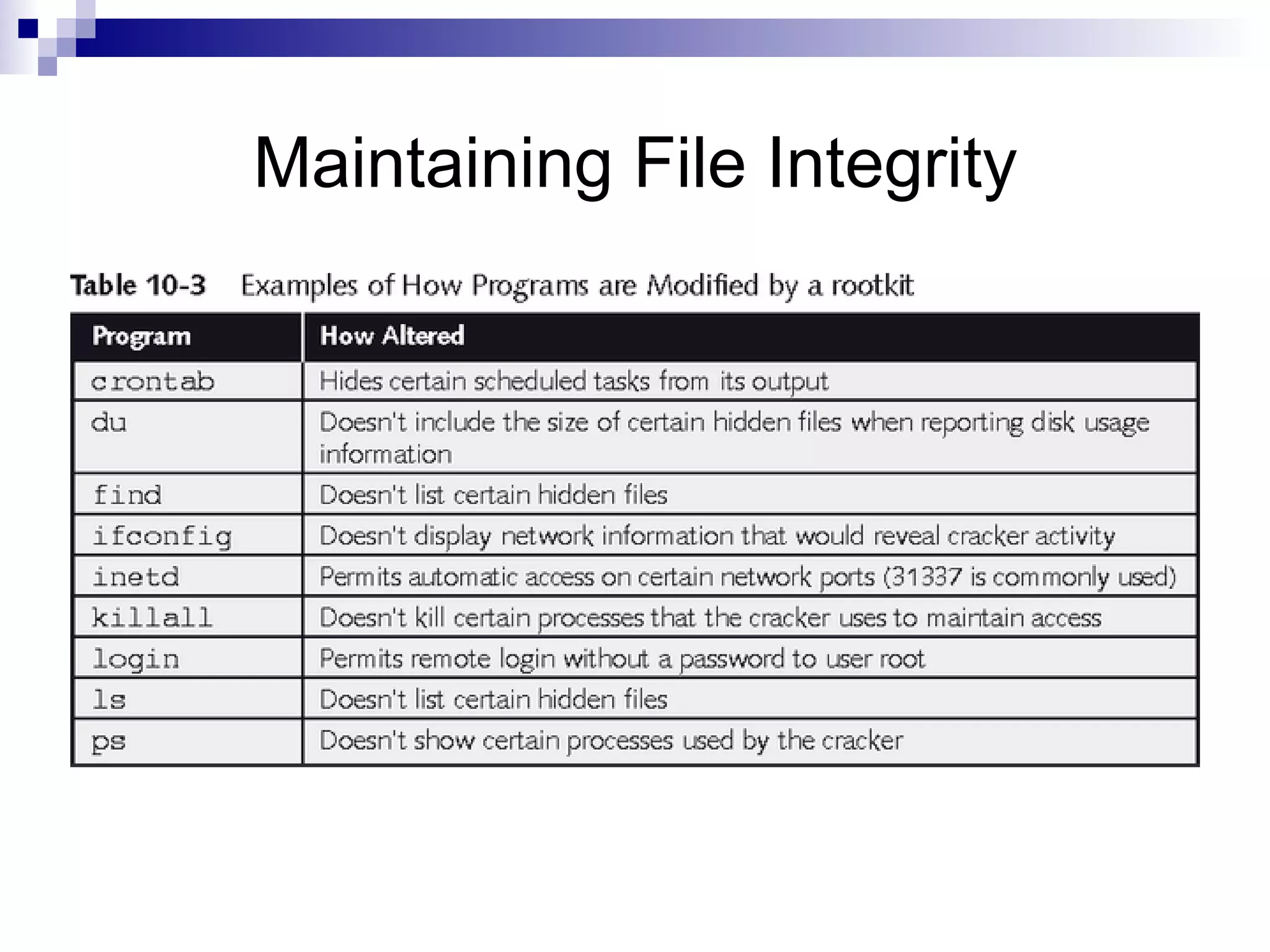
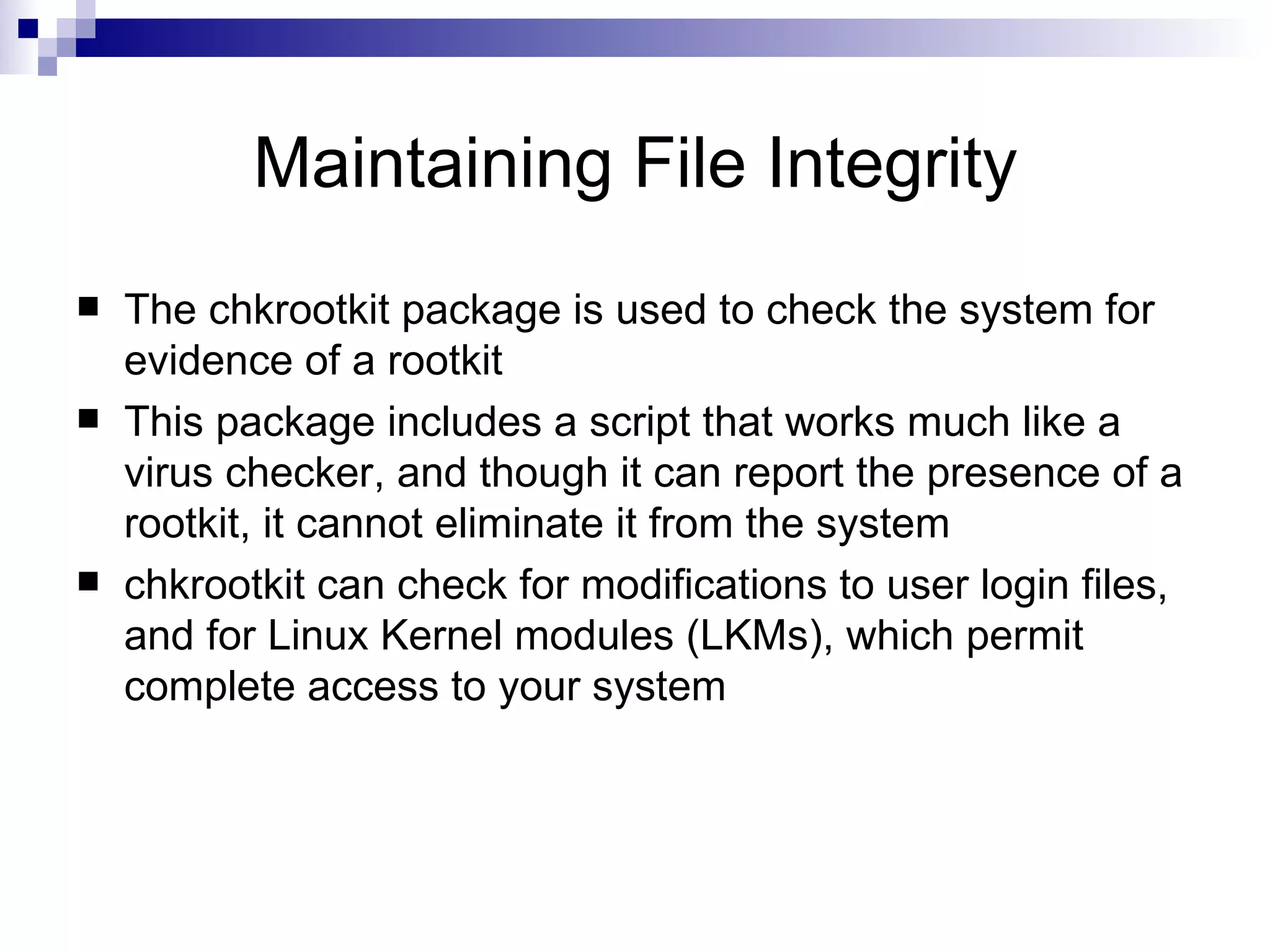
The document discusses various methods for securing Linux files, including setting proper file permissions, monitoring log files for suspicious activity, and automating checks for unauthorized file modifications through tools like Tripwire and Samhain. It emphasizes the importance of carefully configuring file permissions, reviewing log files regularly, and detecting any changes to important system files to maintain security and integrity.