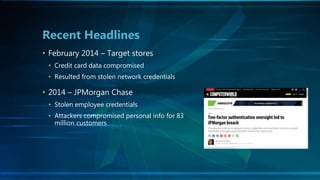
This document summarizes a presentation on two-factor authentication (2FA). It discusses the different types of authentication factors including something you know (e.g. passwords), something you have (e.g. security tokens), and something you are (e.g. biometrics). Software token apps like Google Authenticator and Authy that generate one-time passwords for 2FA are also covered. The document outlines the security issues with passwords and why 2FA is needed based on recent data breaches. It provides an overview of standards like FIDO and implementation recommendations for adding a second authentication factor.