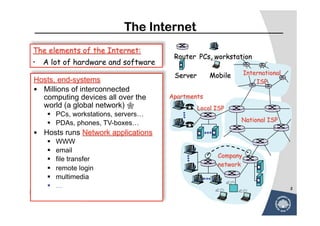
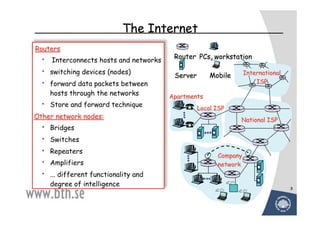
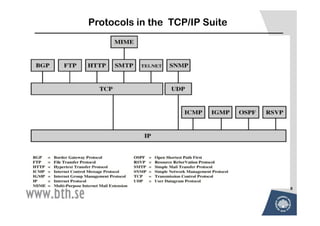
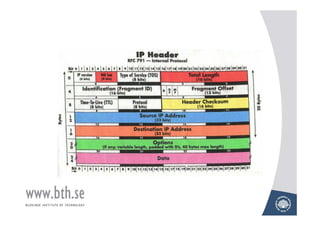
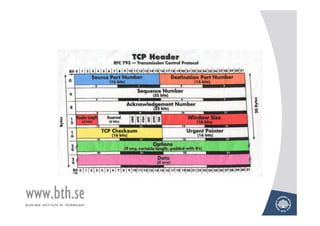
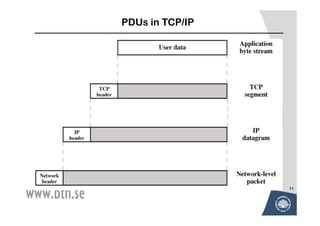
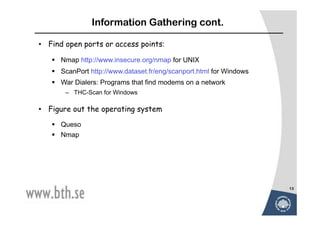
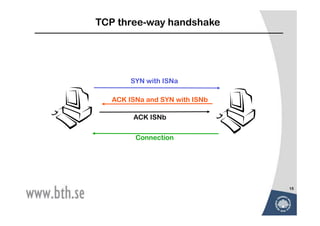
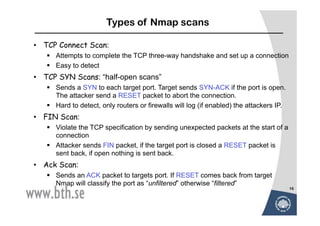
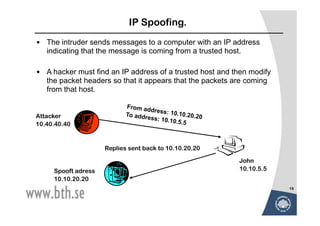
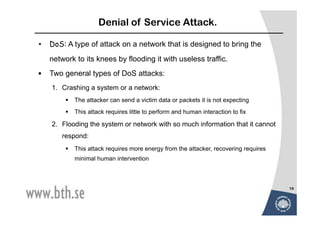
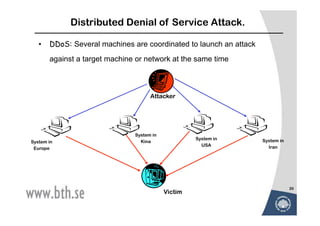
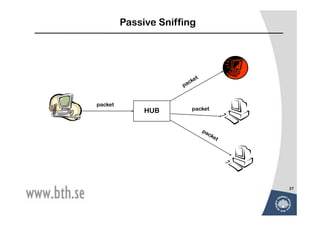
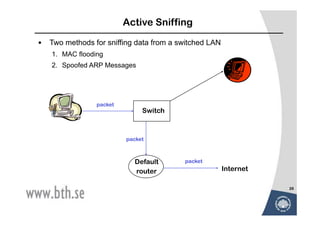
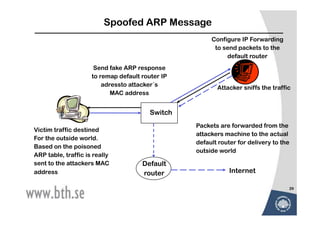
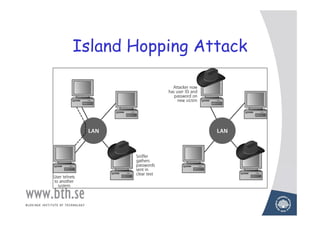
The document discusses various techniques for attacking computer networks, beginning with gathering initial information about a target network through techniques like whois lookups and traceroutes. It then describes methods for port scanning with tools like Nmap to identify open ports and services. The document outlines spoofing attacks, denial of service attacks, sniffing tools like tcpdump, and other hacking methods such as password cracking and buffer overflows.




![Buffer overflow
#include <stdio.h>
sample_function(char *string){
char buffer[16]; Local buffer can hold 16 characters
strcpy(buffer, string);
strcpy loads characters into buffer until it
return;}
finds the end of the string
main (){ Create buffer that can hold 256 characters
char big_buffer [256]; int i;
for (i=0; i<255; i++){
big_buffer[i]='A'; } Shove the character A into the buffer 255
times
sample_function (big_buffer);
Sent big_buffer to sample_function
22
FREDRIK ERLANDSSON ET2437 - NETWORK SECURITY](https://image.slidesharecdn.com/lecture2-networkattack2-120612174128-phpapp02/85/Lecture2-network-attack-22-320.jpg)

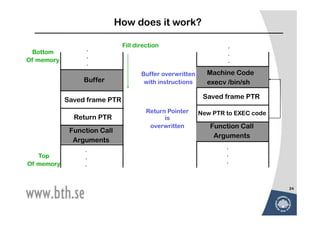
![Example
• Some different buffer overflow attacks:
NetMeeting Buffer Overflow
Outlook Buffer Overflow
Linuxconf Buffer Overflow
IIS 4.0/5.0 Phone Book Server Buffer Overflow
char shellcode[] =
"xebx1fx5ex89x76x08x31xc0x88x46x07x89x46x0cxb0x0b"
"x89xf3x8dx4ex08x8dx56x0cxcdx80x31xdbx89xd8x40xcd"
"x80xe8xdcxffxffxff/bin/sh";
void main() {
int *ret;
ret = (int *)&ret + 2;
(*ret) = (int)shellcode;}
25
FREDRIK ERLANDSSON ET2437 - NETWORK SECURITY](https://image.slidesharecdn.com/lecture2-networkattack2-120612174128-phpapp02/85/Lecture2-network-attack-25-320.jpg)




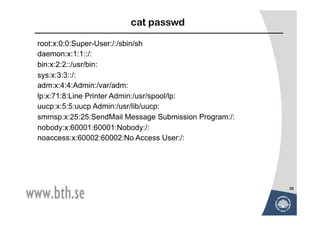
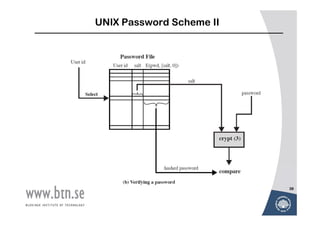
![UNIX Password Scheme I
salt password
Password File
12 bits 56 bits User id salt E(pwd, [salt, 0])
•
Load •
crypt (3)
11 characters •
(a) Loading a new password
37
FREDRIK ERLANDSSON ET2437 - NETWORK SECURITY](https://image.slidesharecdn.com/lecture2-networkattack2-120612174128-phpapp02/85/Lecture2-network-attack-37-320.jpg)