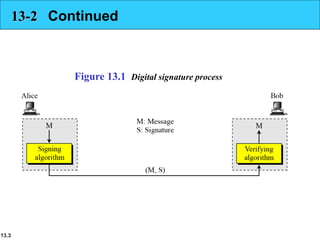
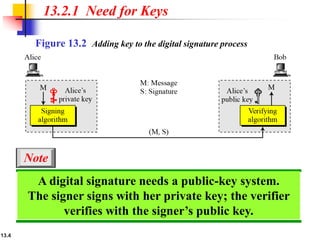
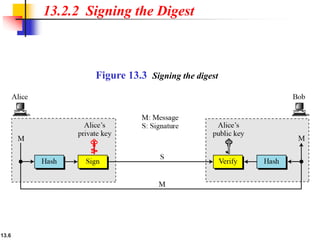
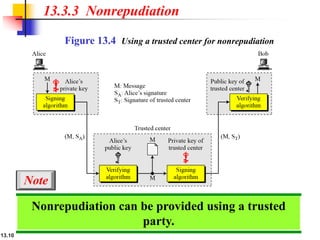
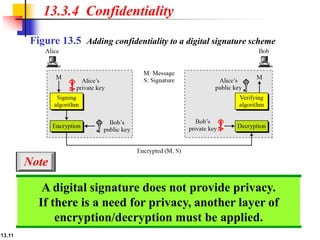
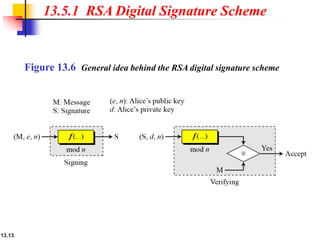
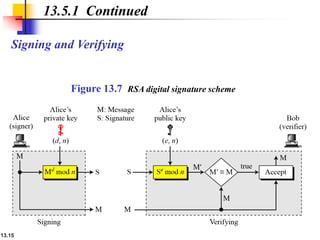
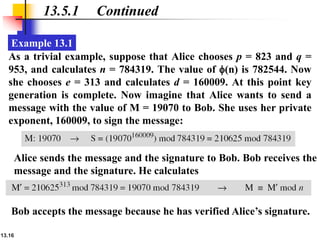
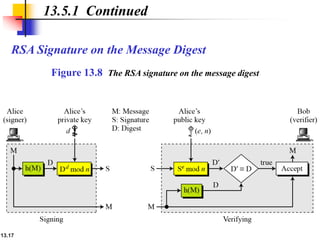
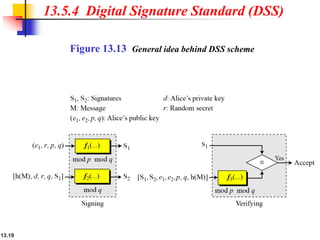
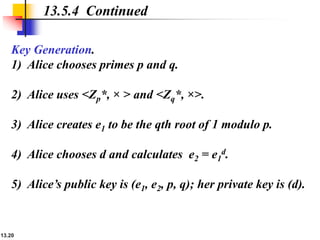
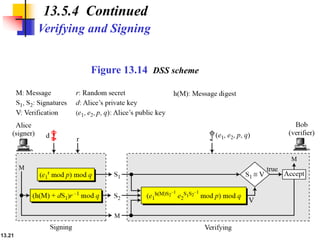
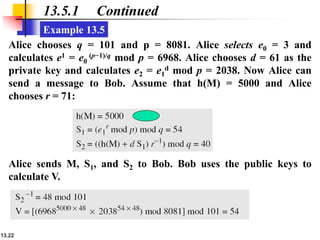
The document explains the digital signature process, which involves the sender signing a message with a private key and the receiver verifying it with the sender's public key. It details the necessity of both public and private keys, the provision of message authentication, integrity, and nonrepudiation by digital signatures, and emphasizes that confidentiality requires additional encryption. It also highlights different digital signature schemes, including the RSA and Digital Signature Standard (DSS), detailing their key generation and signing processes.