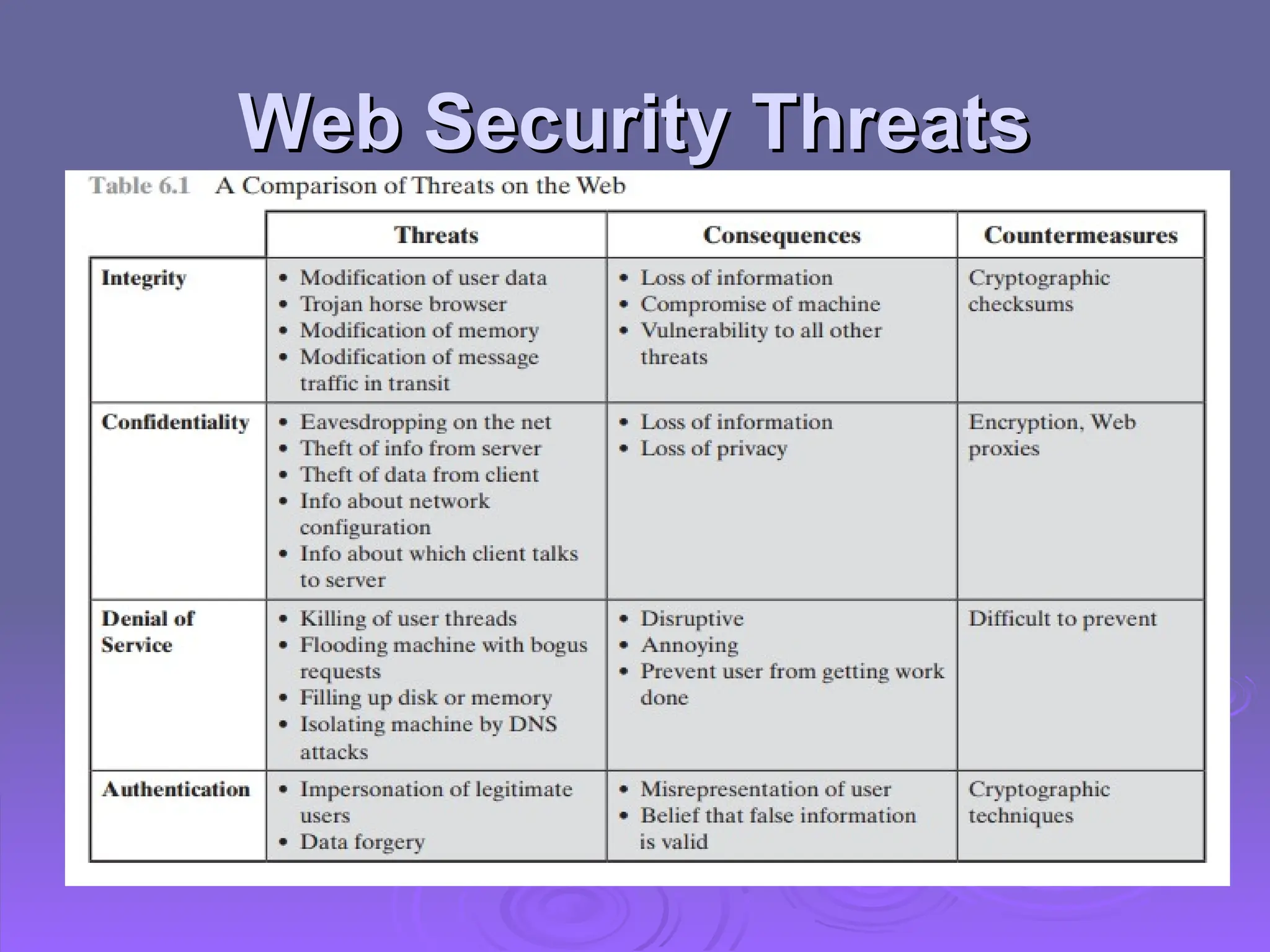
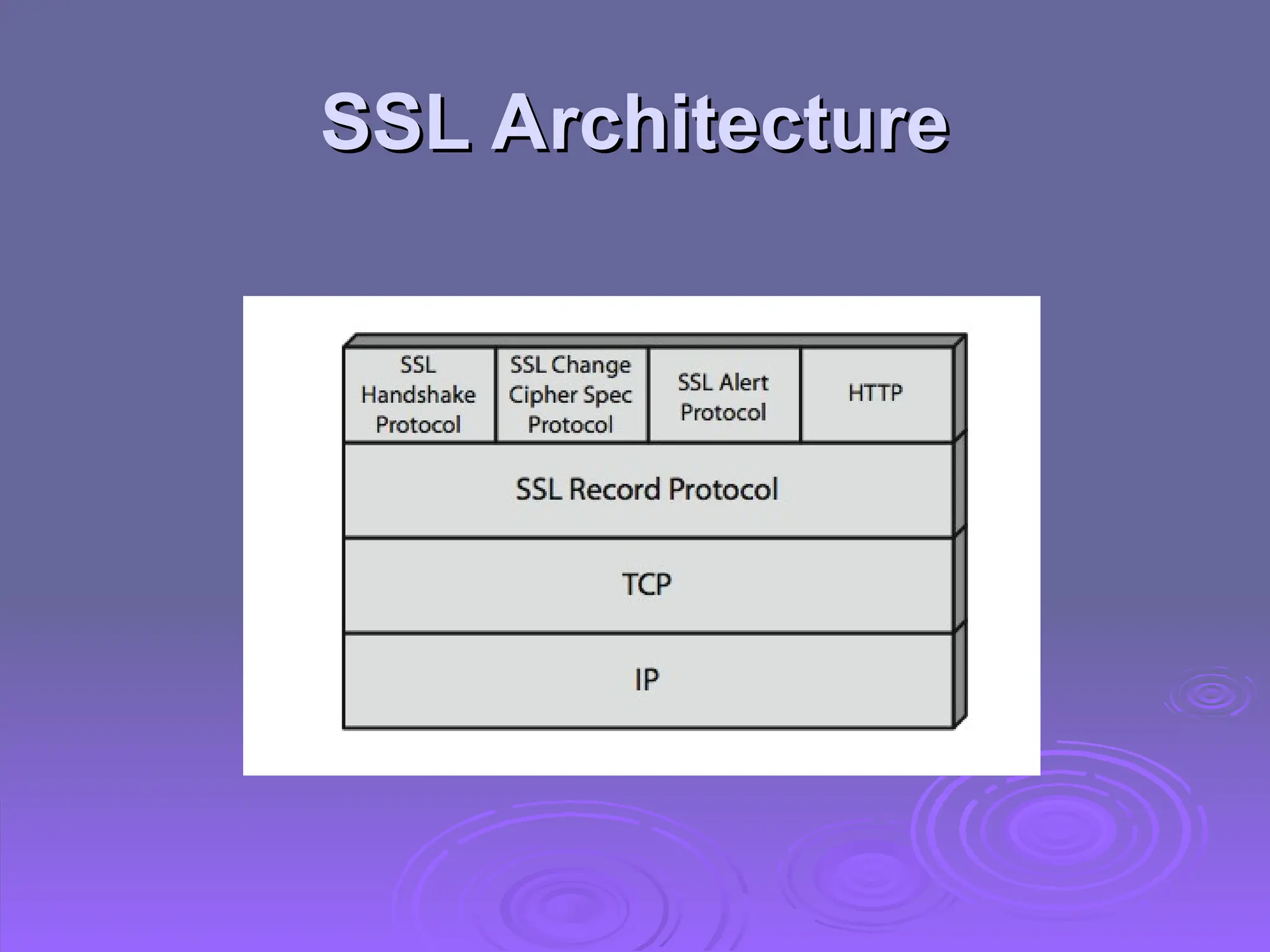
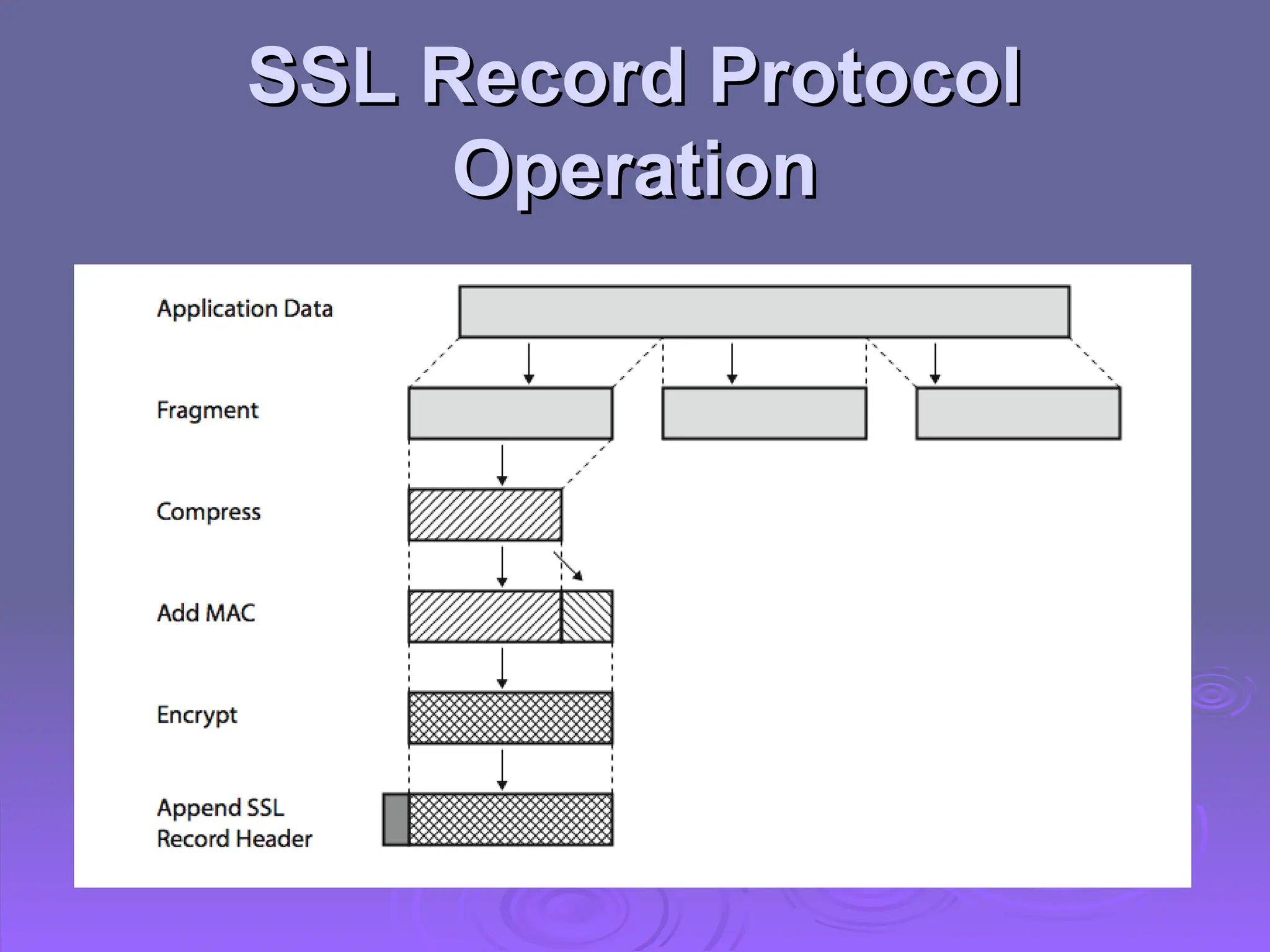
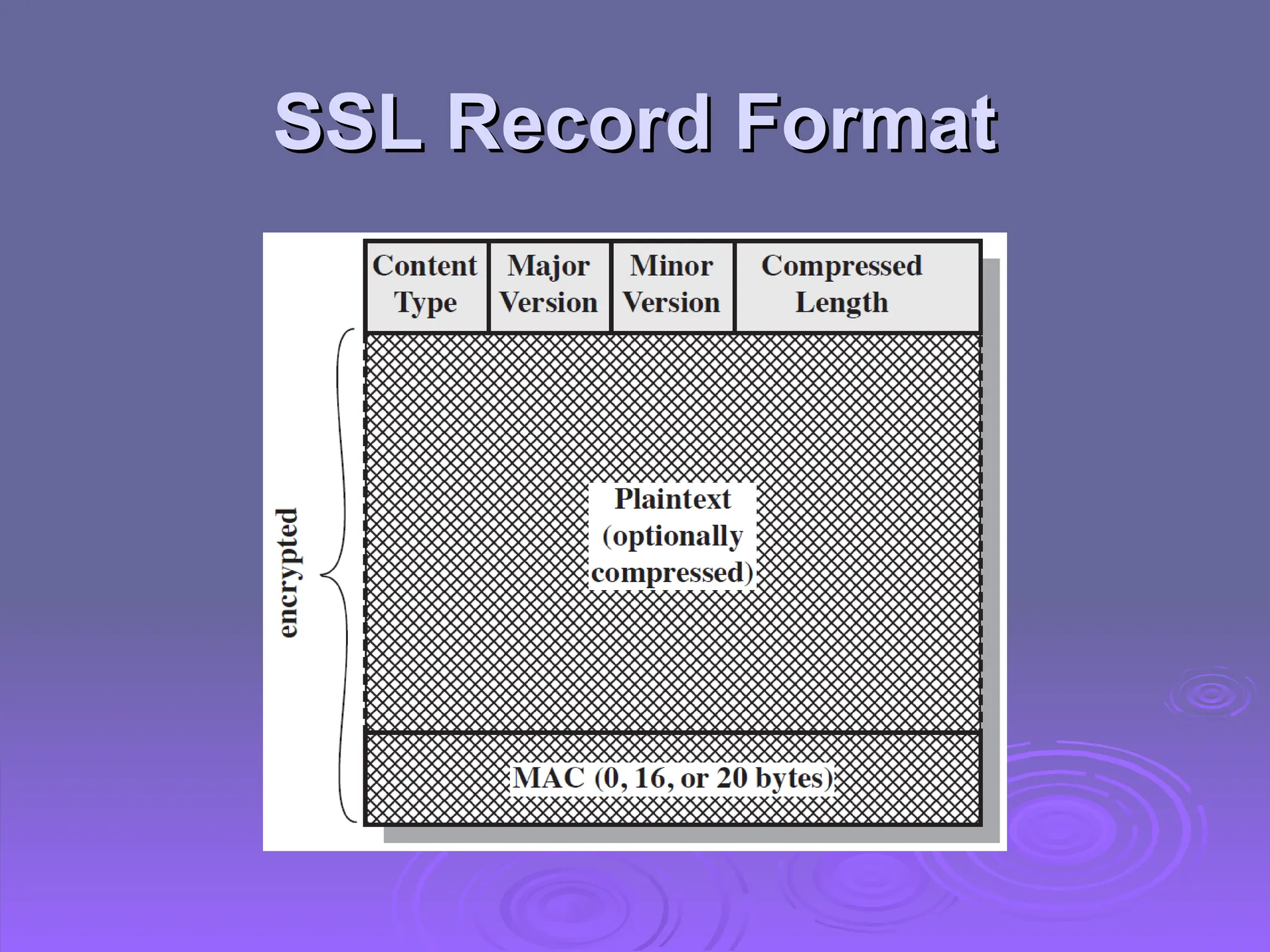
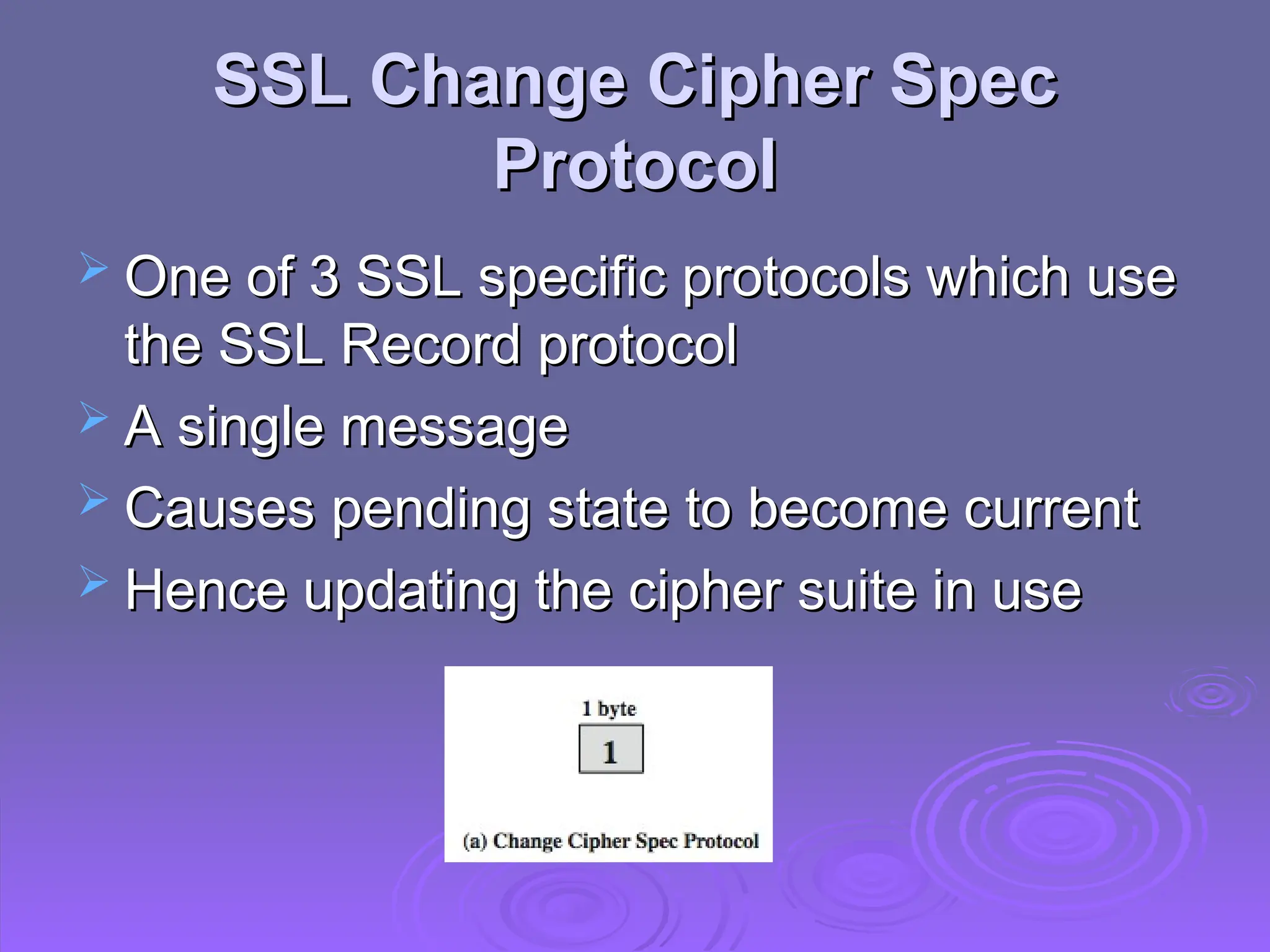
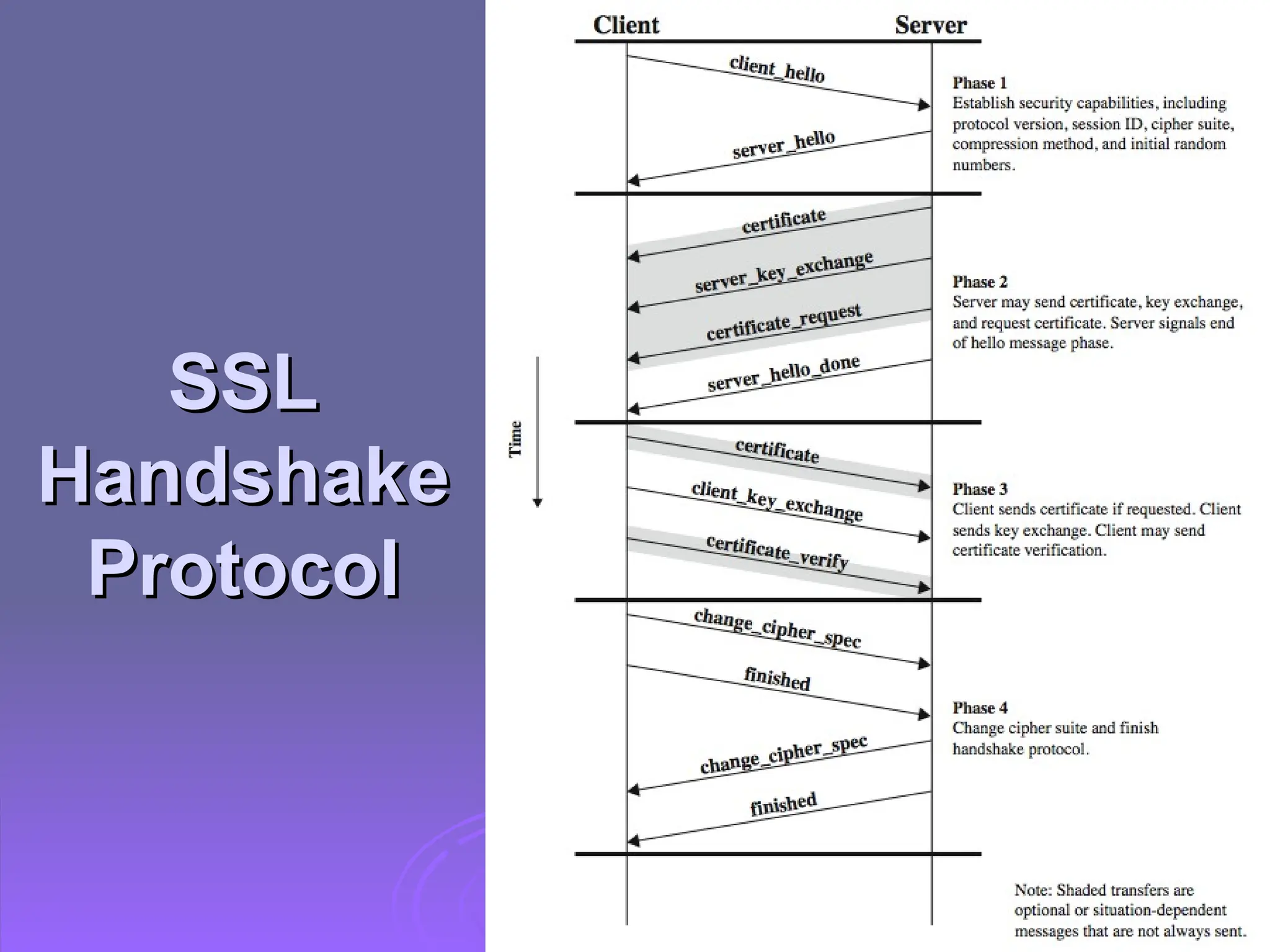
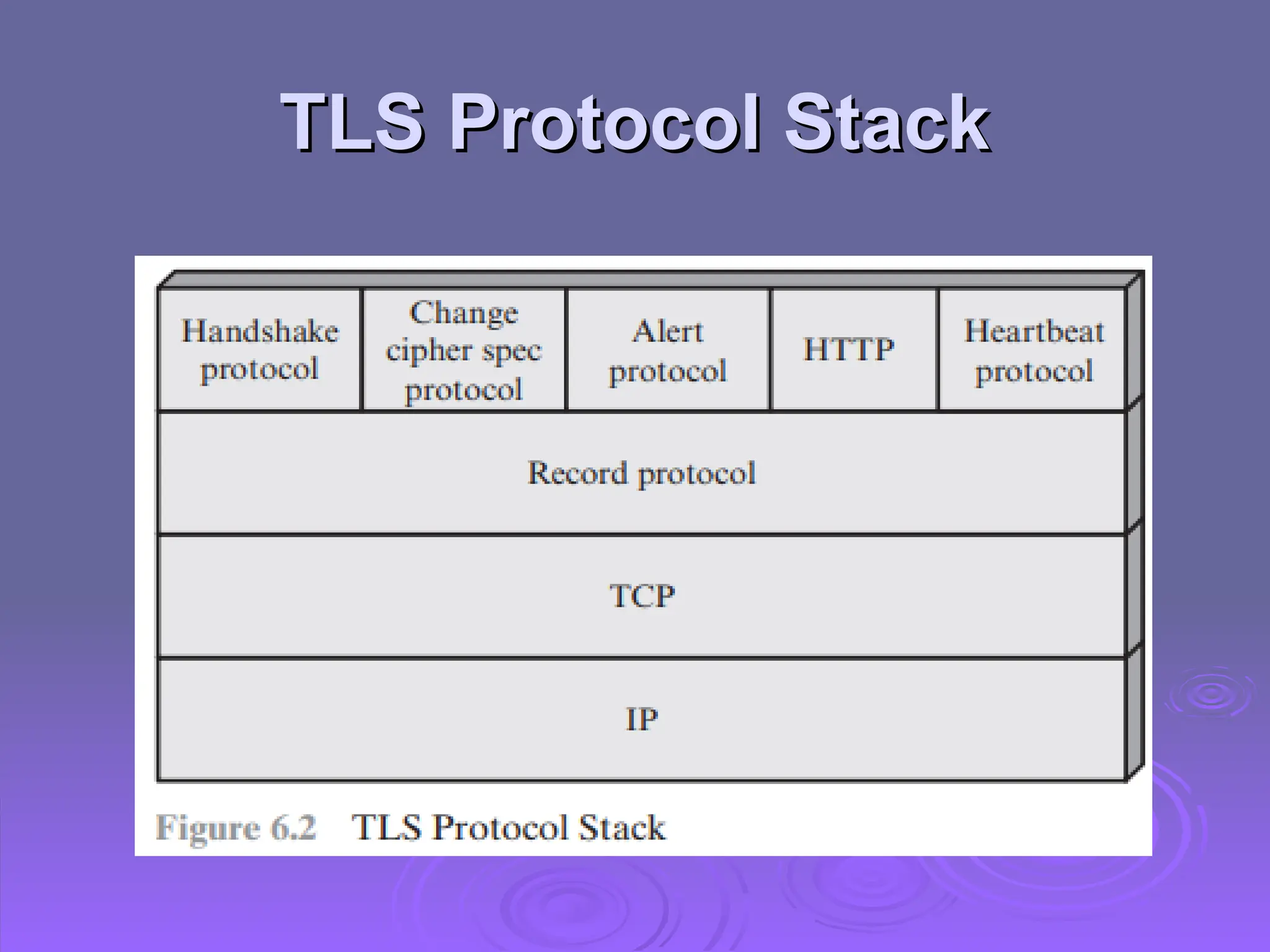
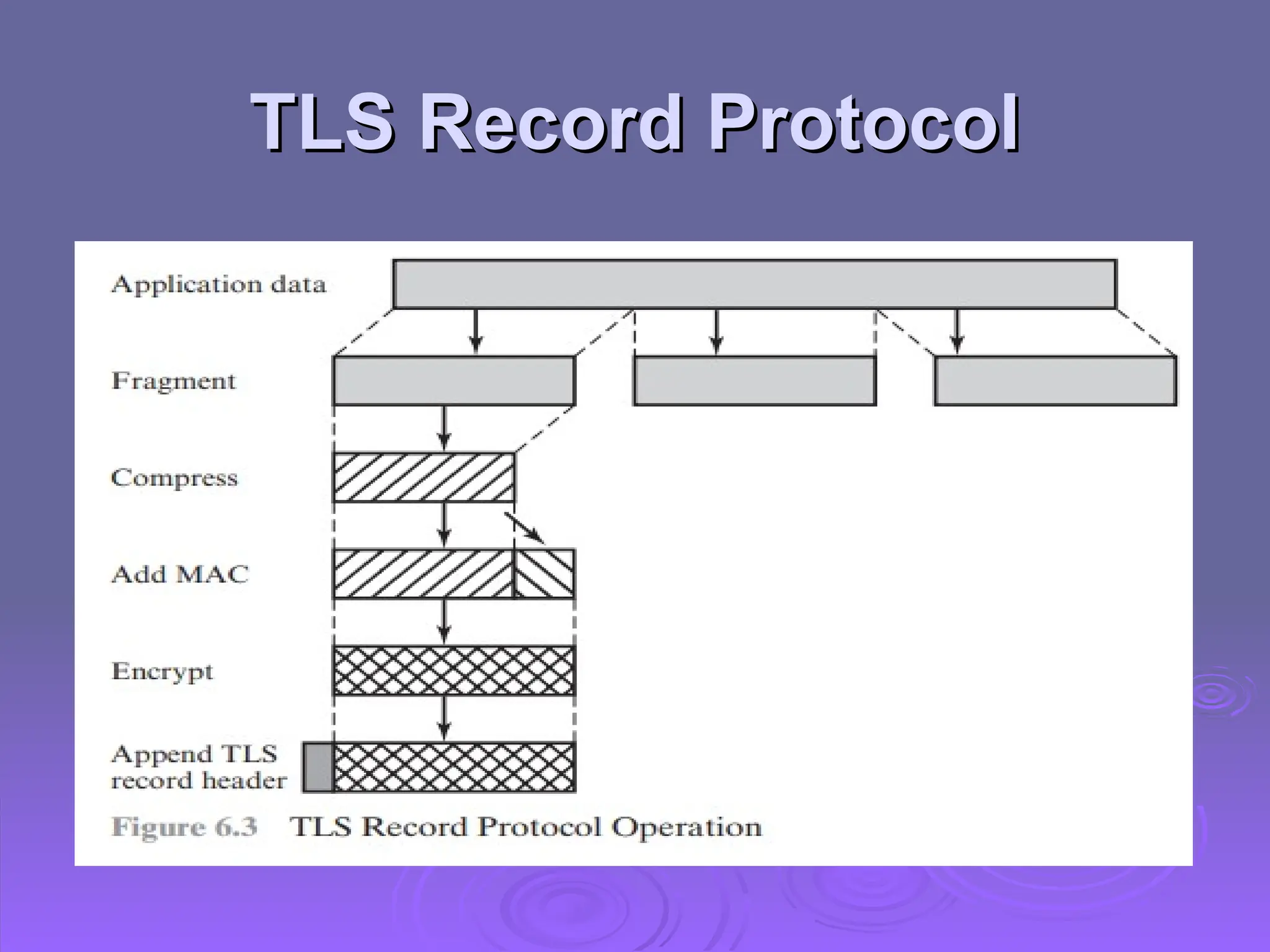
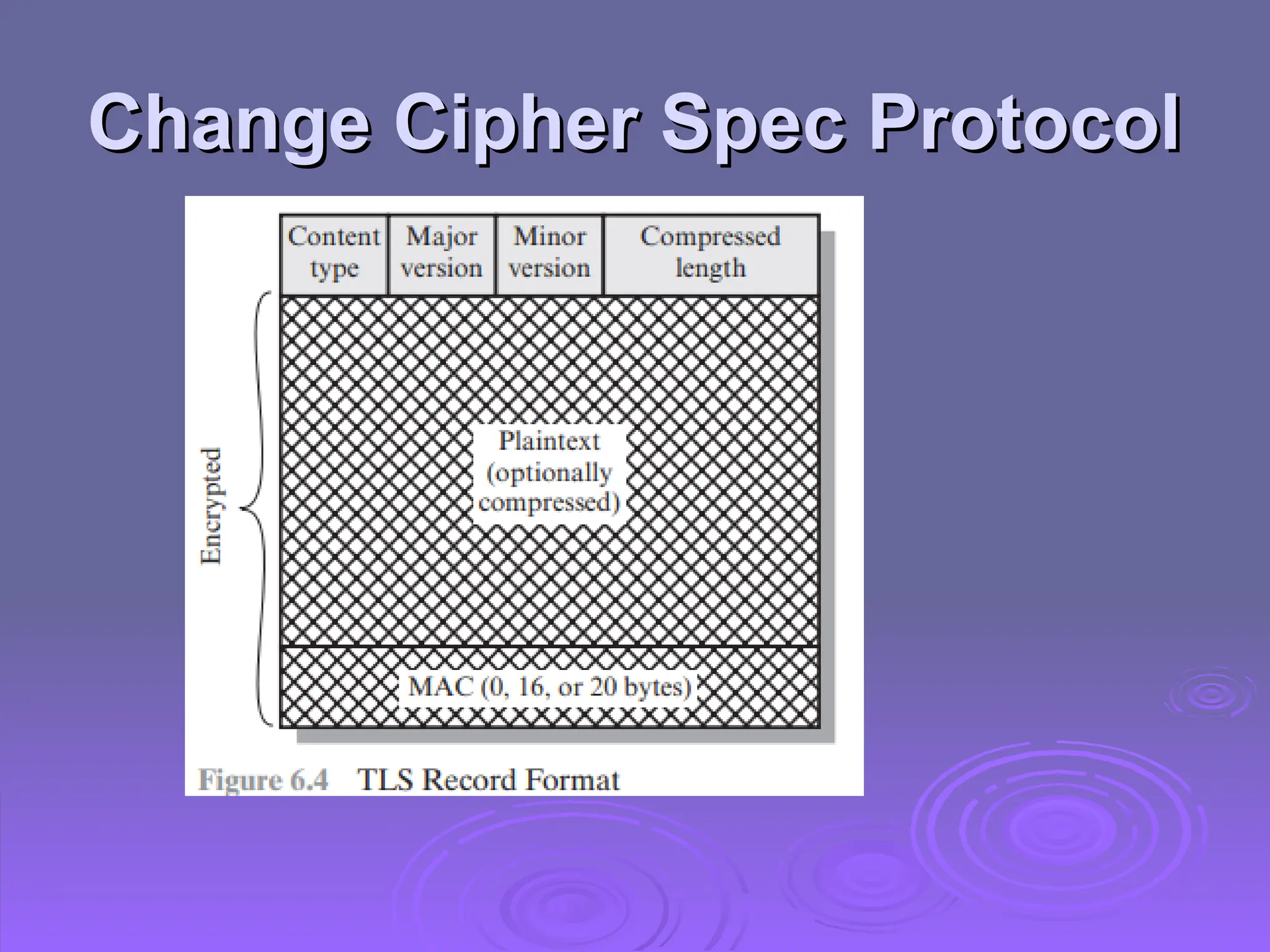
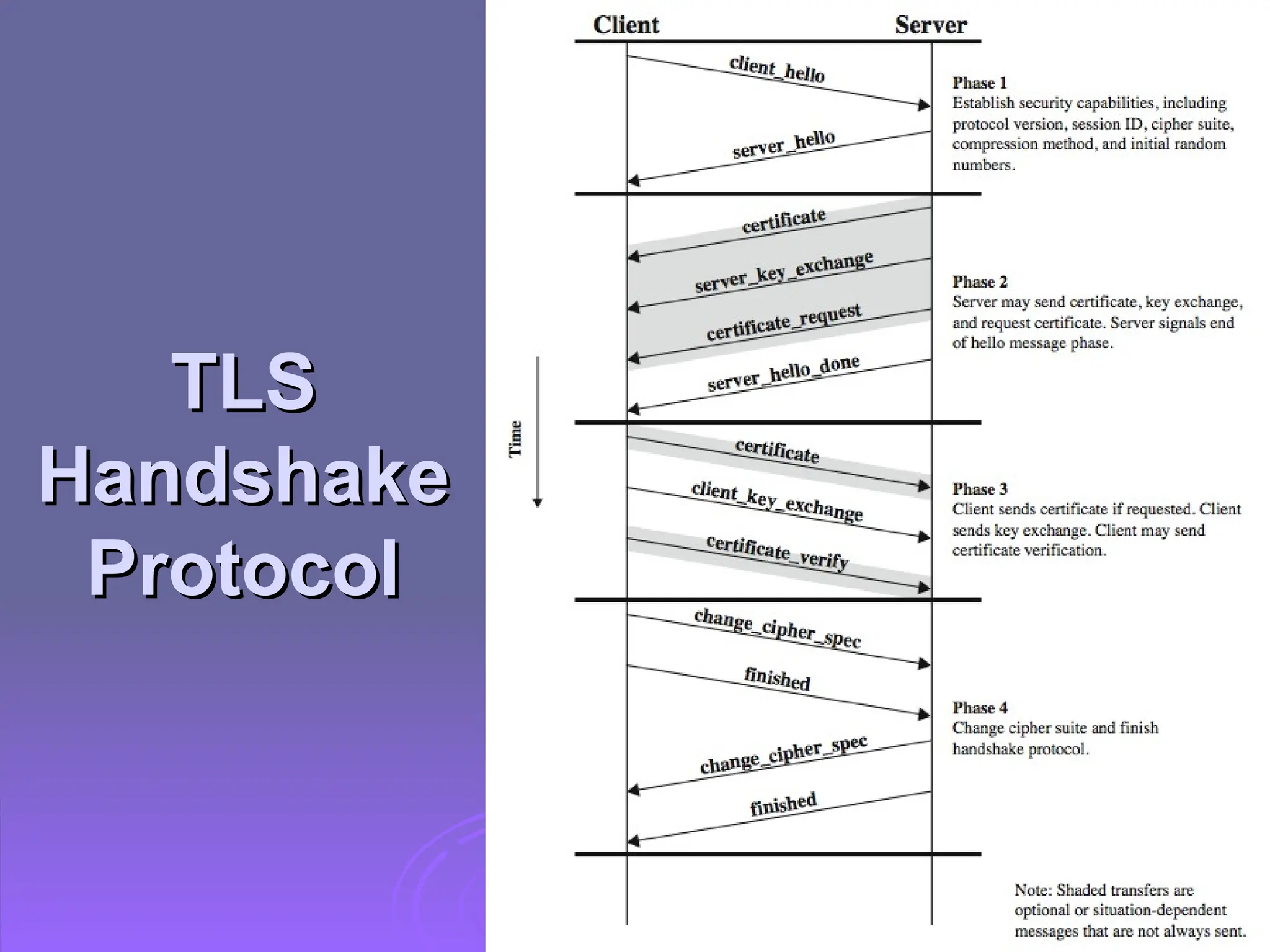
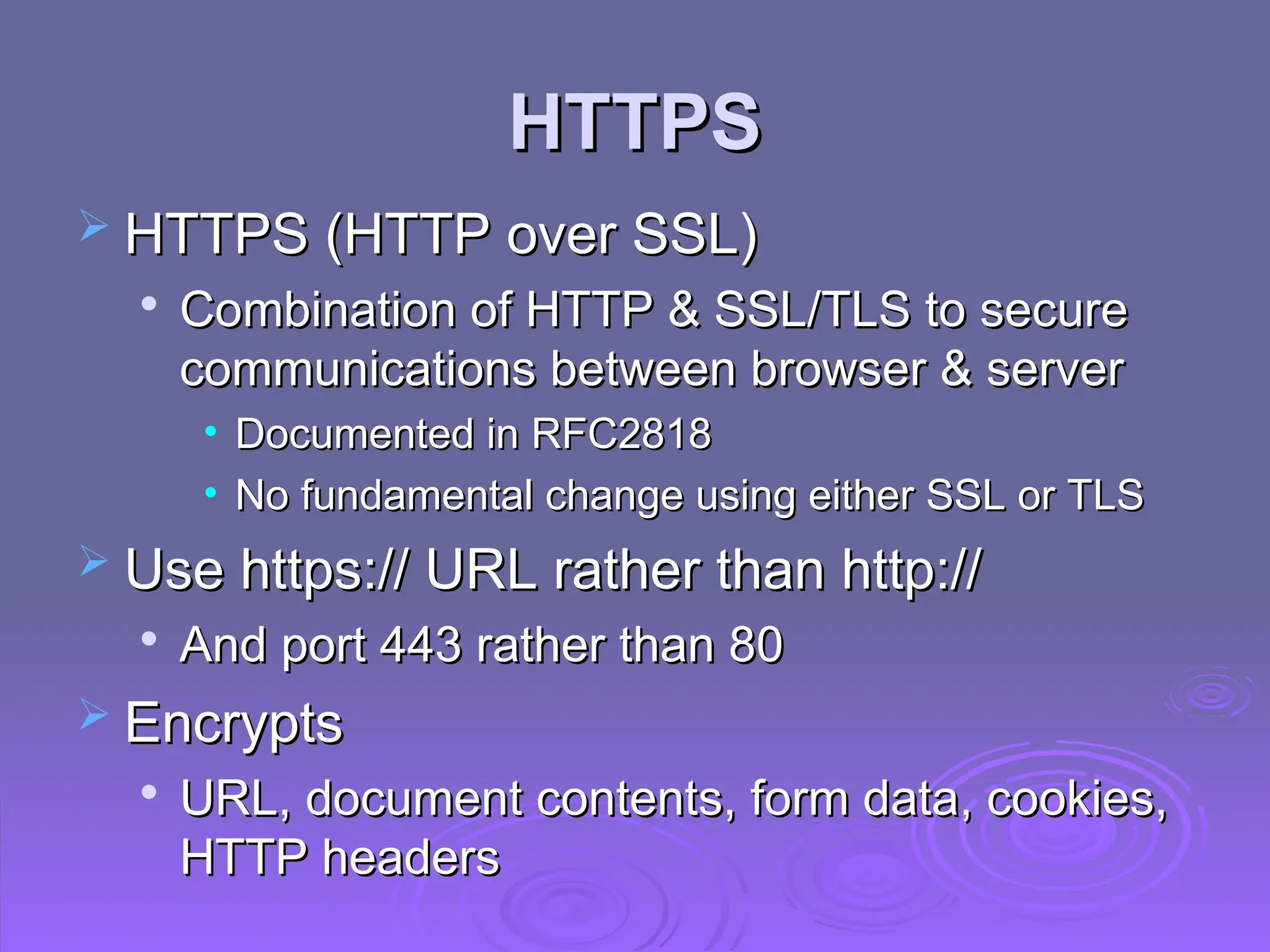
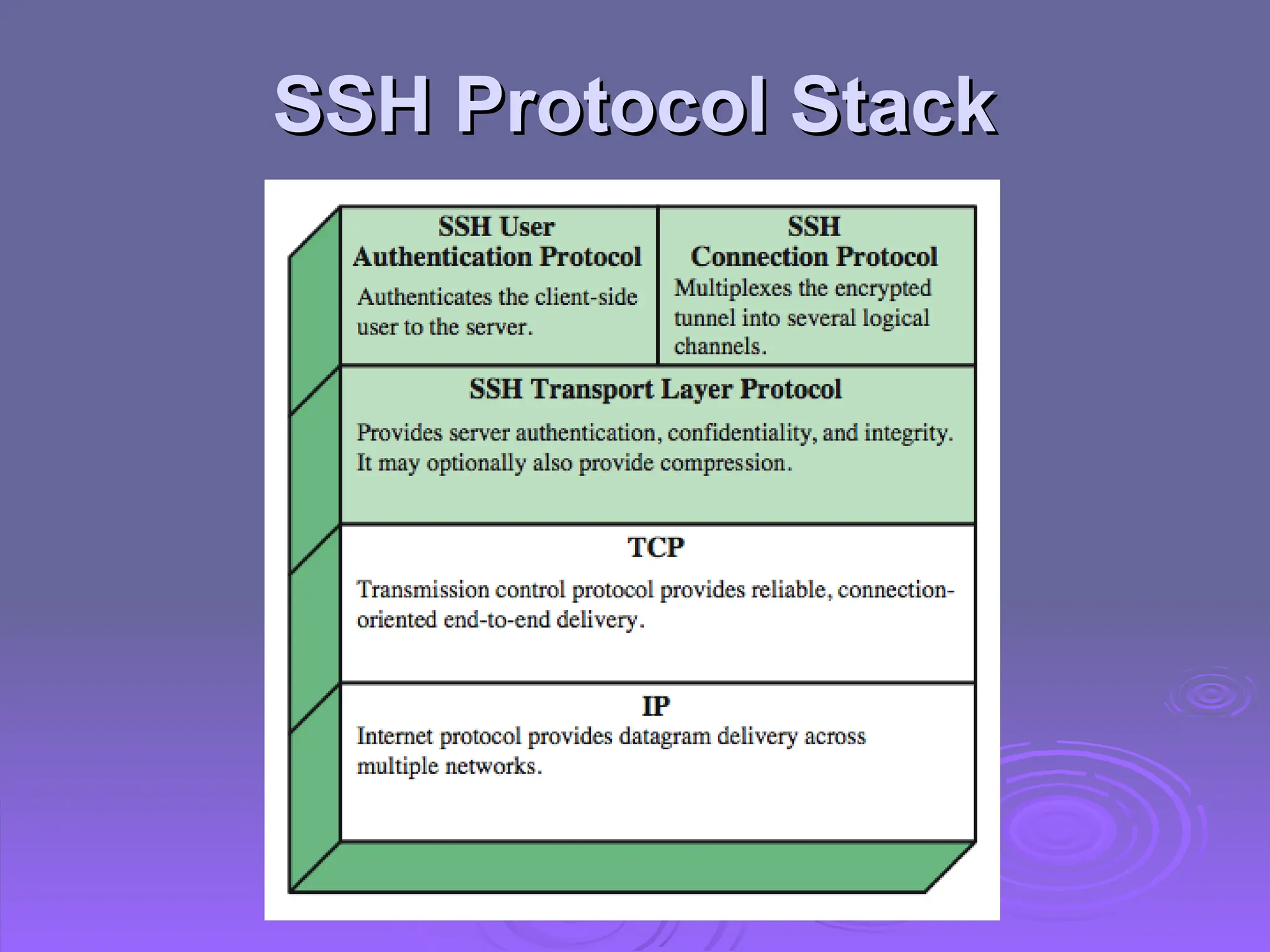
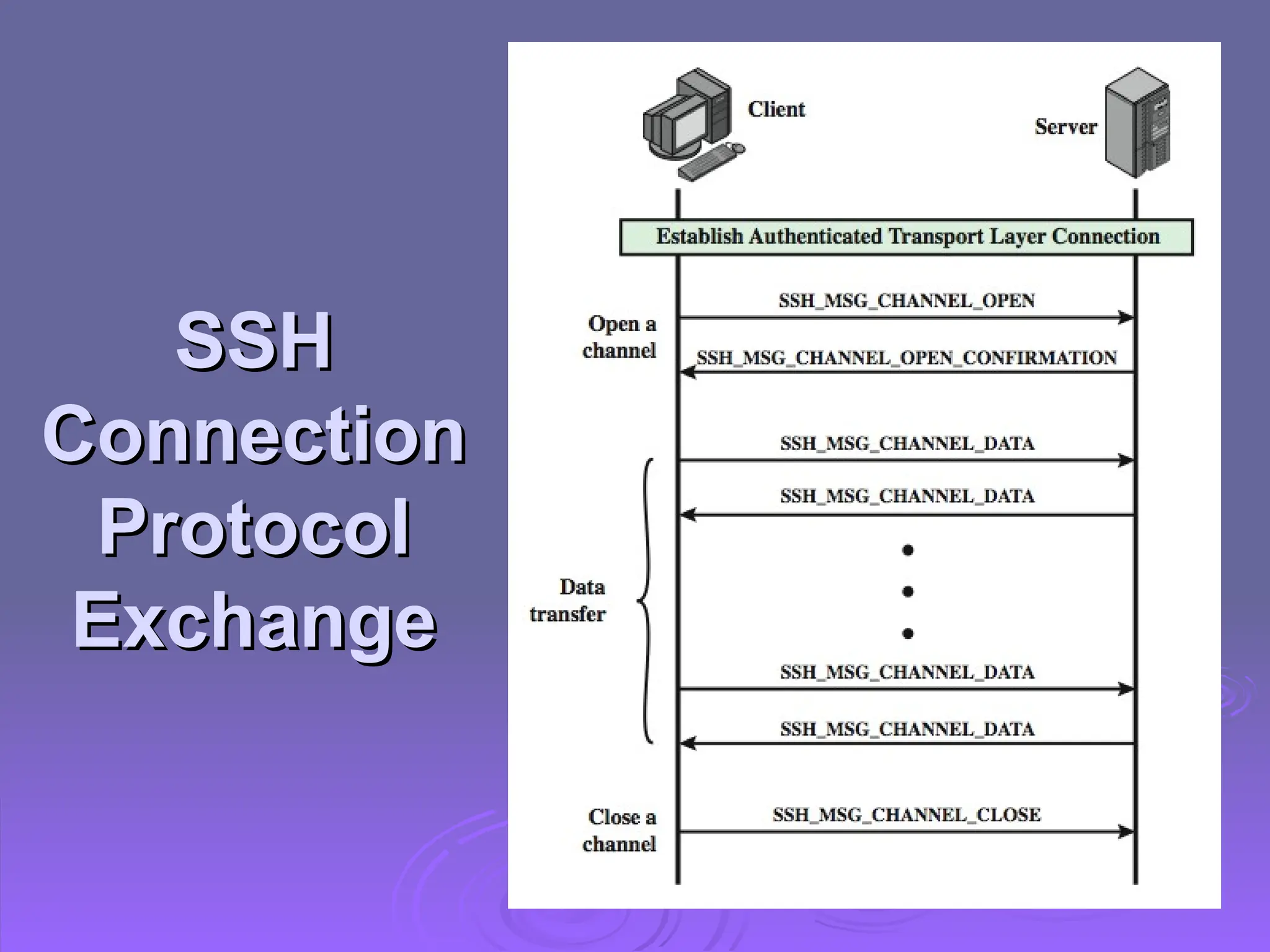
The document discusses the importance of web security, highlighting threats to web servers, including integrity, confidentiality, and denial of service. It explains security mechanisms such as SSL/TLS, HTTPS, and SSH for safe communication, detailing how they work to protect data during transmission. The document emphasizes the need for added security measures due to the vulnerabilities inherent in internet technology.