This document discusses LAN and WAN network architectures. It covers key topics such as:
- LANs are privately owned networks that connect devices within a single building, while WANs provide long-distance transmission across large geographic areas.
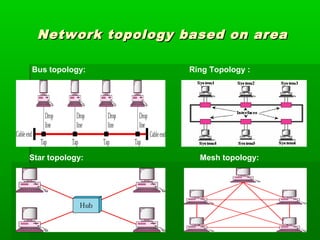
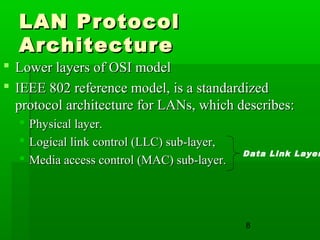
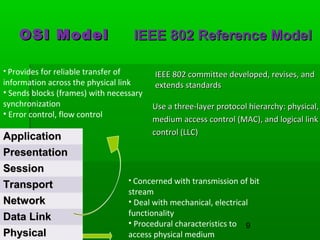
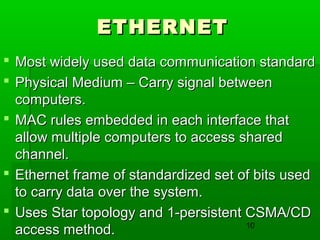
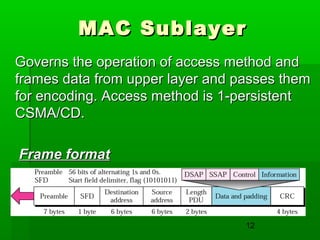
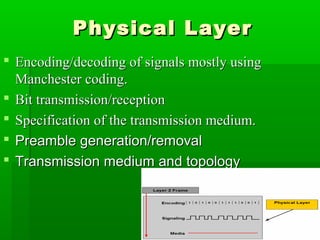
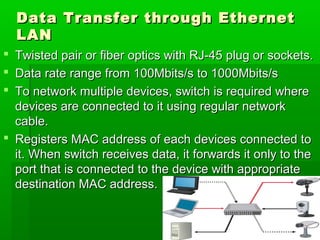
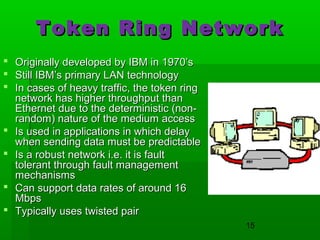
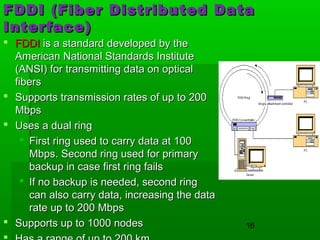
- Common LAN technologies include Ethernet, Token Ring, and FDDI, with Ethernet being the most widely used standard.
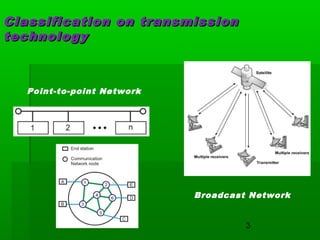
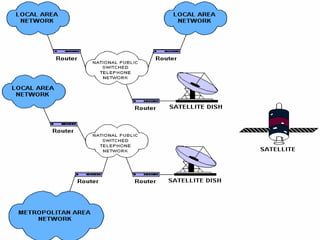
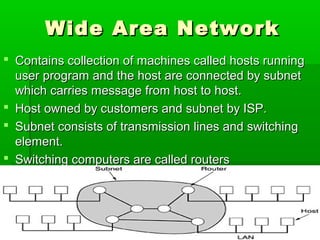
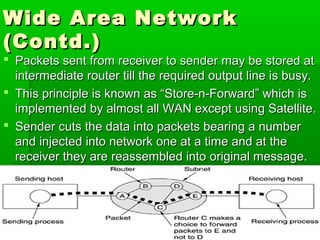
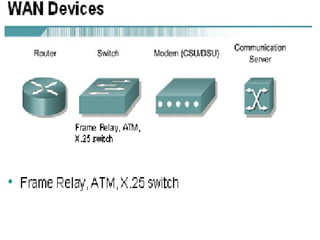
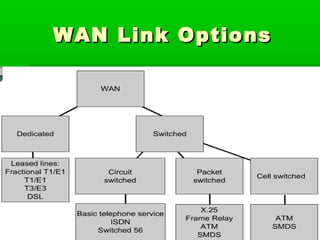
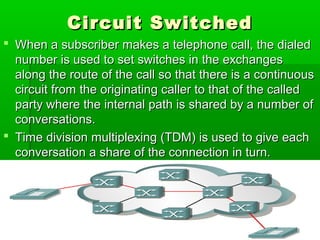
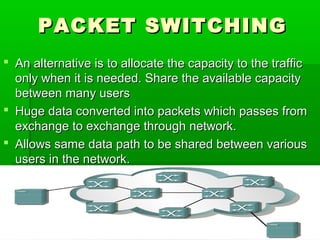
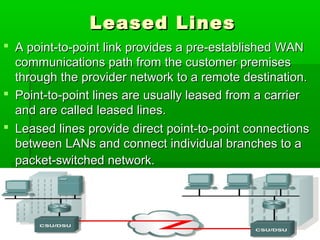
- WANs connect multiple LANs and use transmission technologies like leased lines, circuits switching, and packet switching to transmit data over large distances.
- The document provides an overview of LAN and WAN components, protocols, topologies and transmission methods.