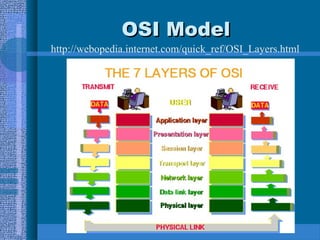
The document outlines LAN fundamentals, detailing various network models such as shared processing, peer-to-peer, and client-server architectures. It discusses the components required for managing LANs, such as file servers, application software, and network interface cards, along with RAID configurations for server storage. Additionally, it covers network topologies, access types, cable types, and the OSI model, providing a comprehensive overview of networking principles and practices.