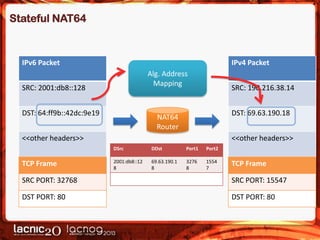
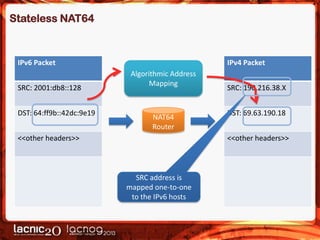
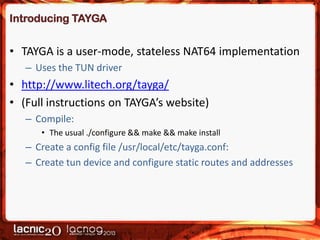
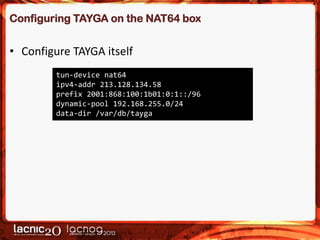
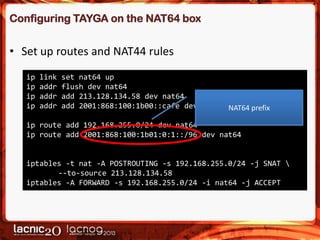
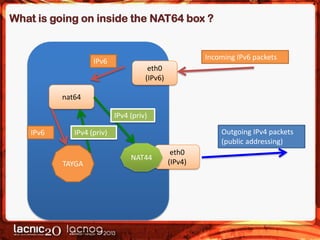
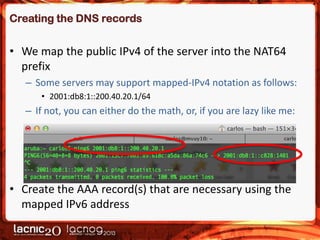
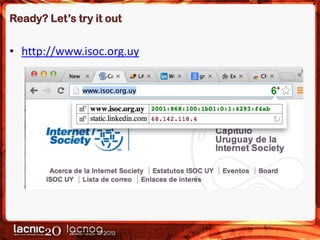
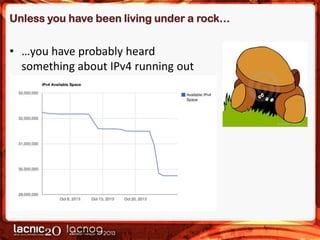
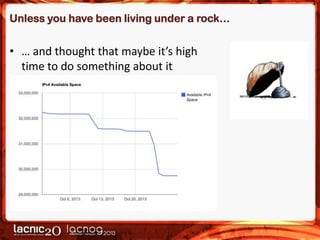
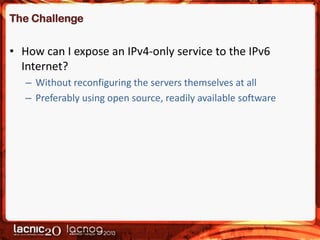
The document discusses methods to expose IPv4-only services on the IPv6 internet, particularly focusing on the necessity of transitioning from IPv4 due to its exhaustion. Two main approaches are detailed: an application-layer solution using HTTP reverse proxy and a network-layer solution utilizing NAT64 for address and protocol translation. Additionally, the document provides instructions for configuring NAT64 with a user-mode implementation called Tayga, emphasizing its importance for connectivity between IPv6 and IPv4 networks.


![HTTP Reverse Proxy
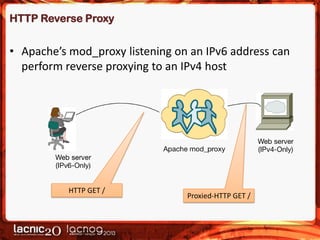
• Apache’s mod_proxy can listen on an IPv6 address and
perform reverse proxying to an IPv4 address:
<VirtualHost [2001:13c7:7001:4000::10]:80>
# Server names
ServerName www.mnav.gub.uy
ServerAlias www.mnav.gub.uy.prx64.labs.lacnic.net
# Logs
CustomLog
/home/v6v4Proxy/logs/mnav/access.log combined
ErrorLog
/home/v6v4Proxy/logs/mnav/error.log
ProxyPass
/ http://www.mnav.gub.uy/
ProxyPassReverse
/ http://www.mnav.gub.uy/
</VirtualHost>](https://image.slidesharecdn.com/cmartinez-ipv6-services-notouch-00-131213082138-phpapp02/85/Enabling-IPv6-Services-Transparently-8-320.jpg)