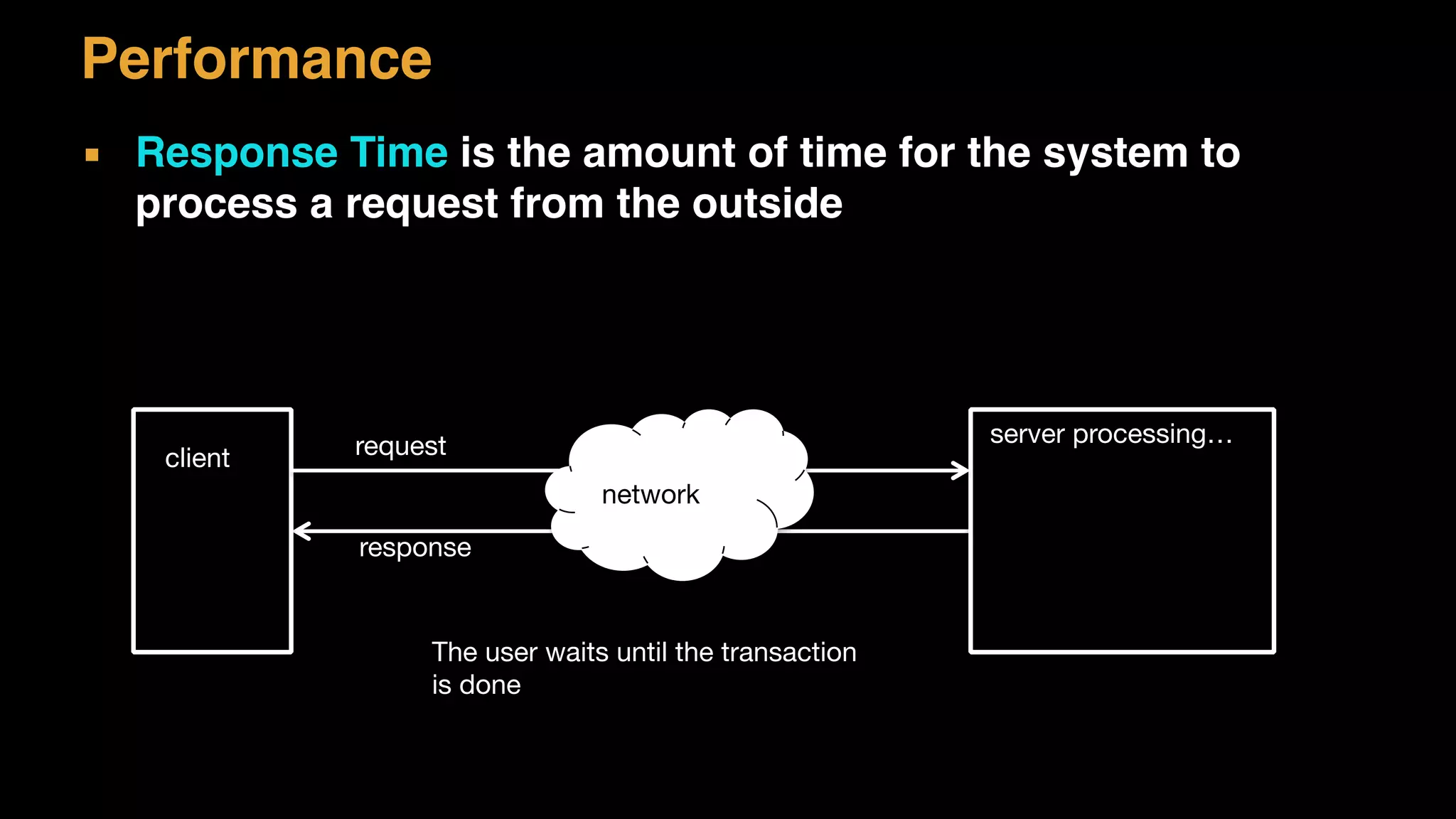
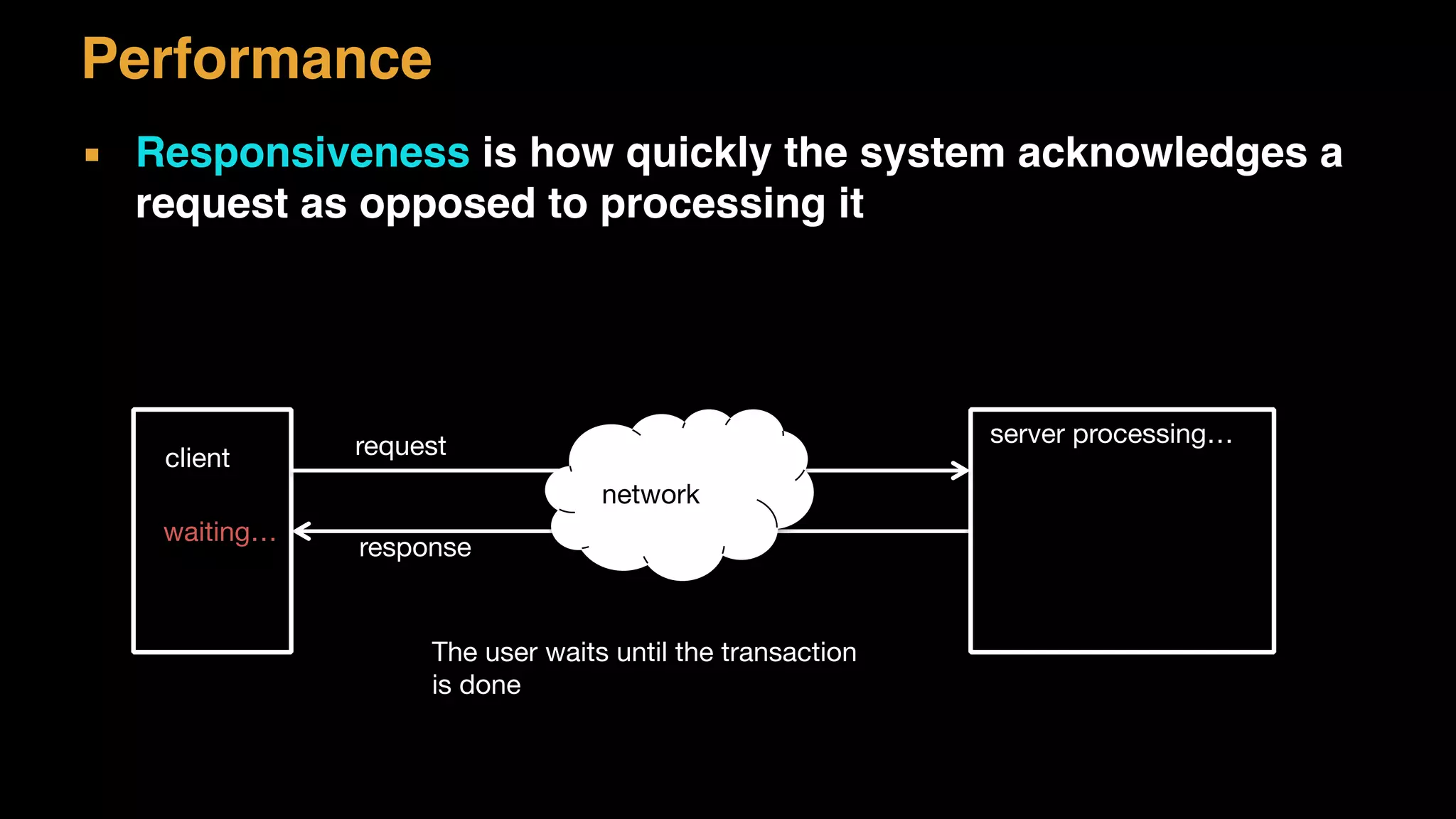
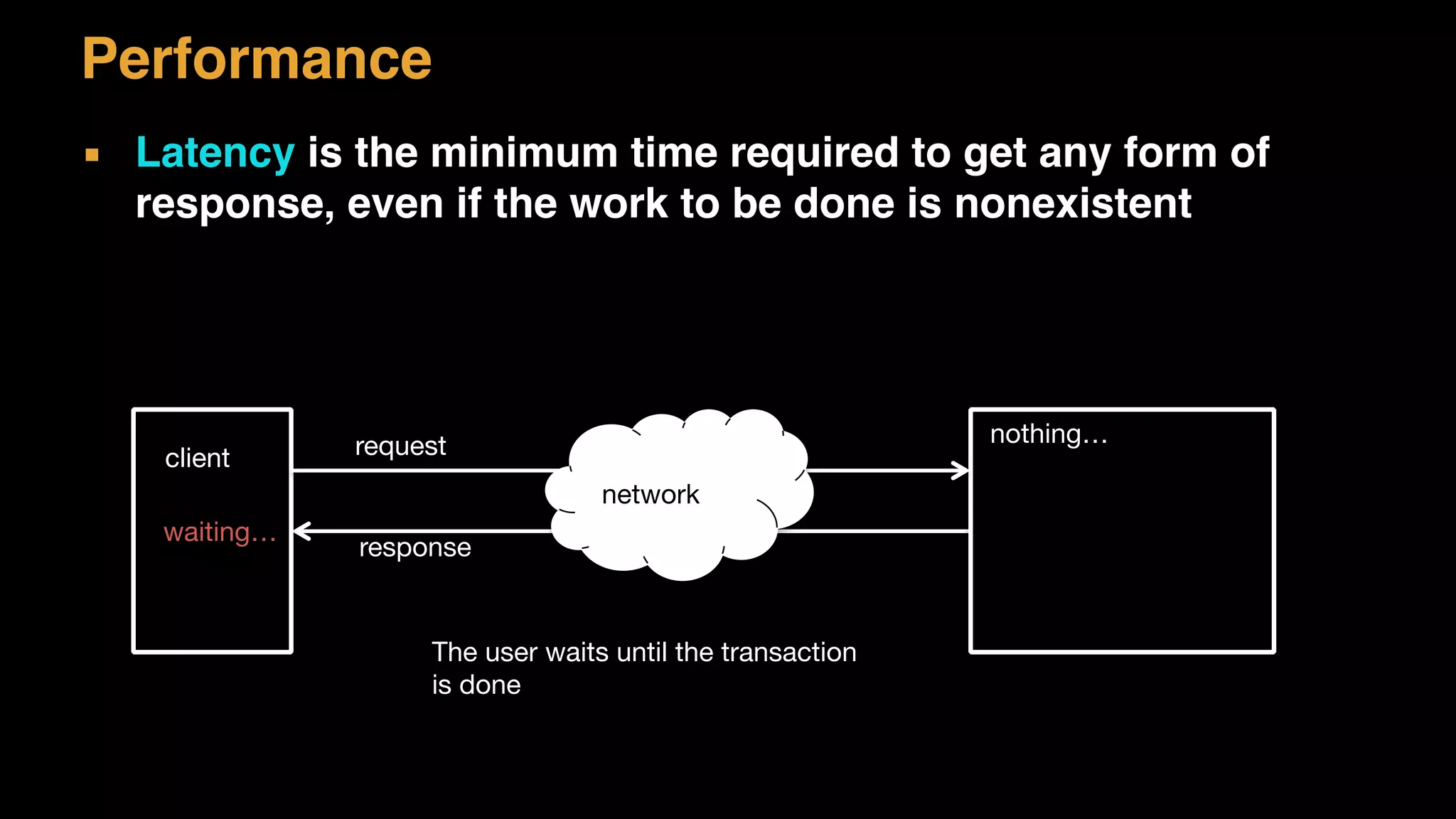
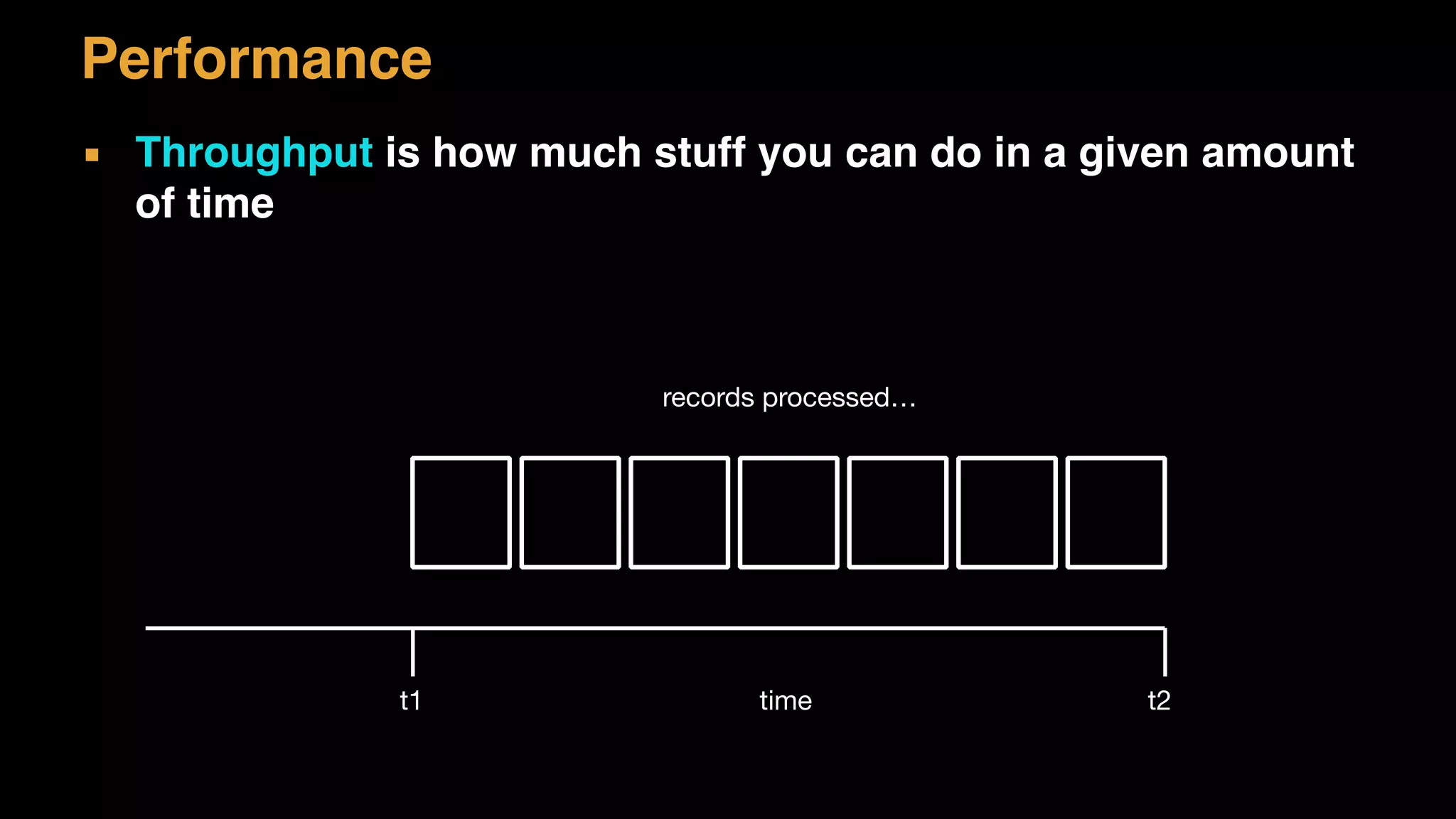
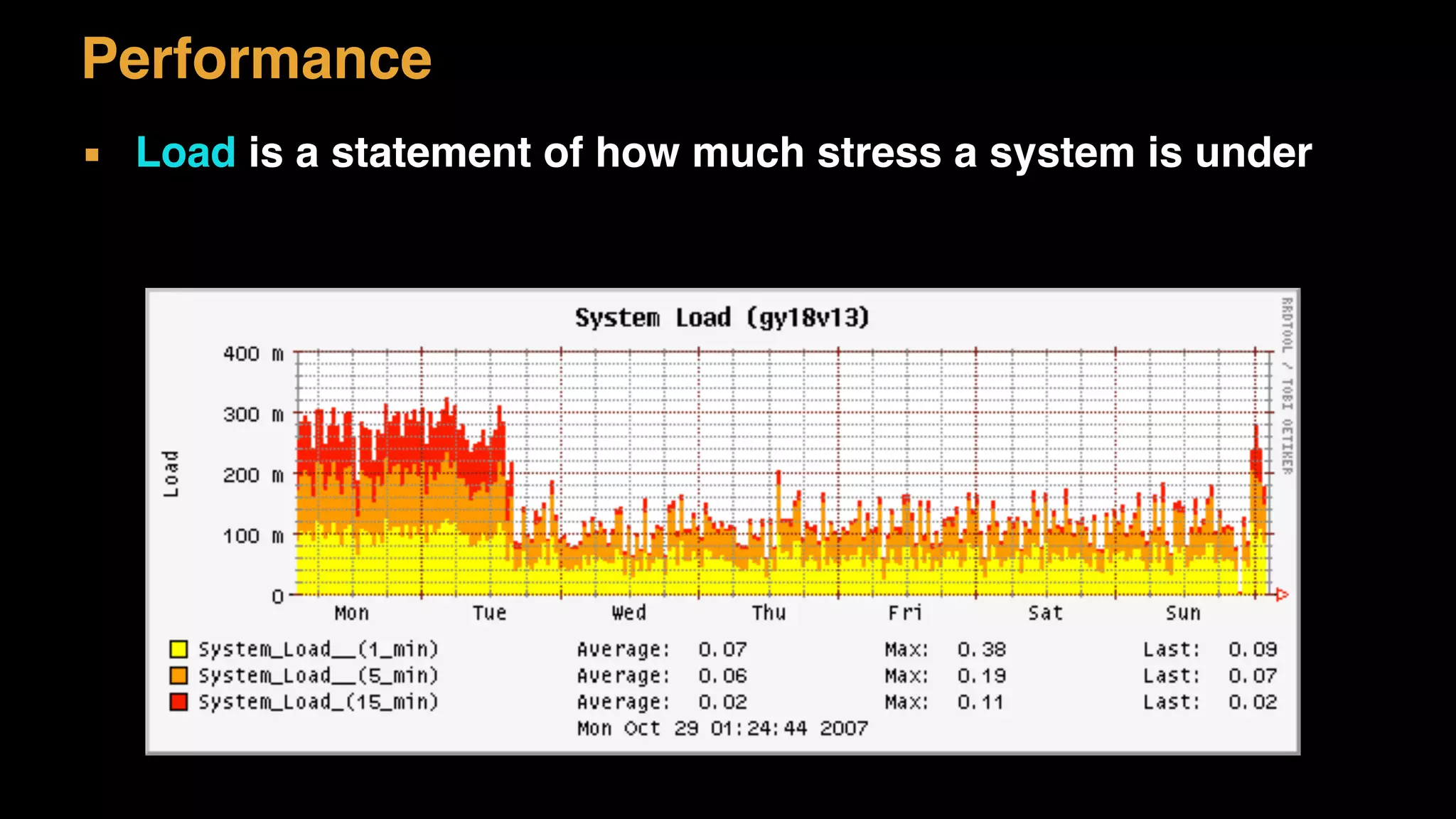
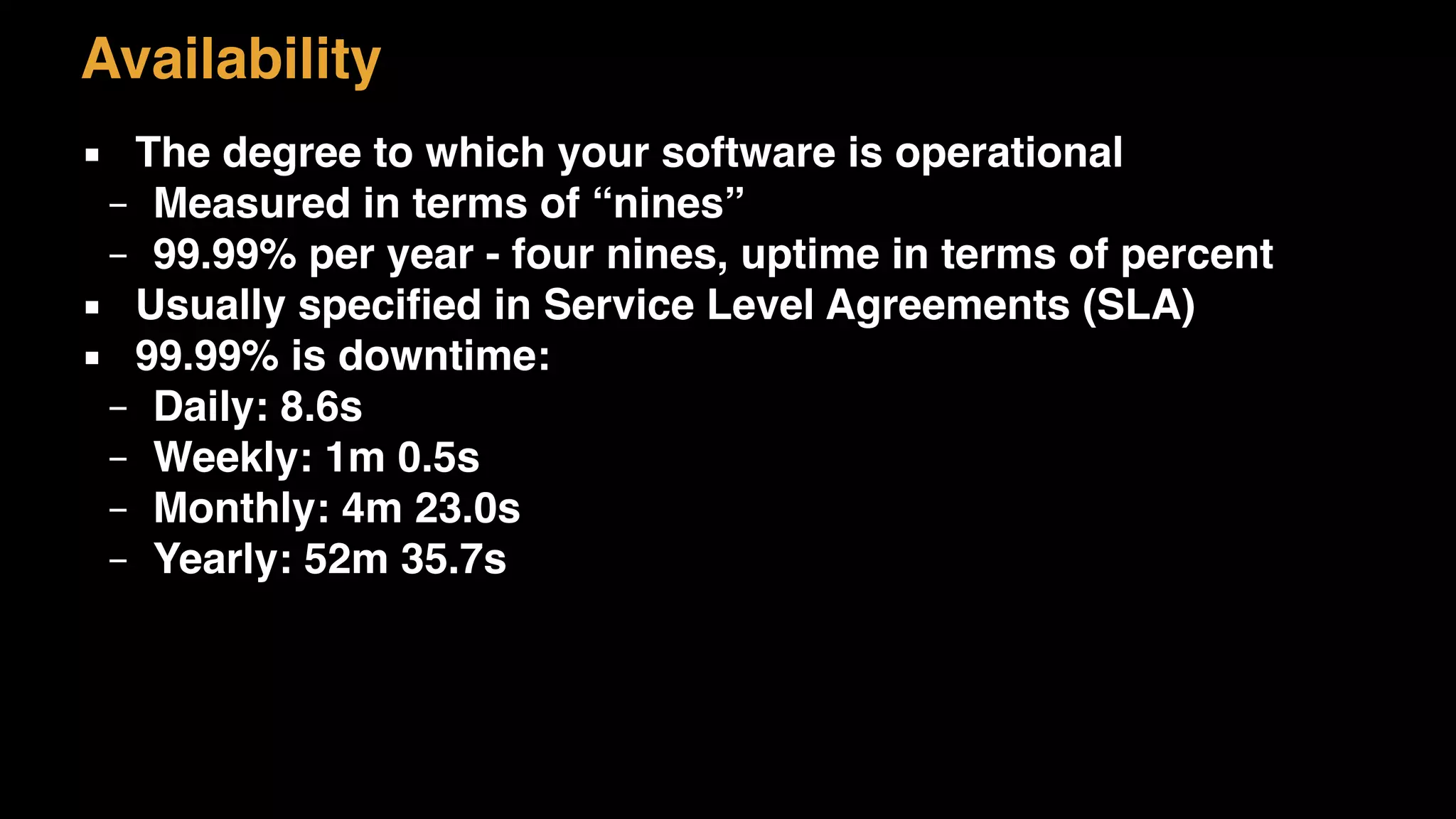
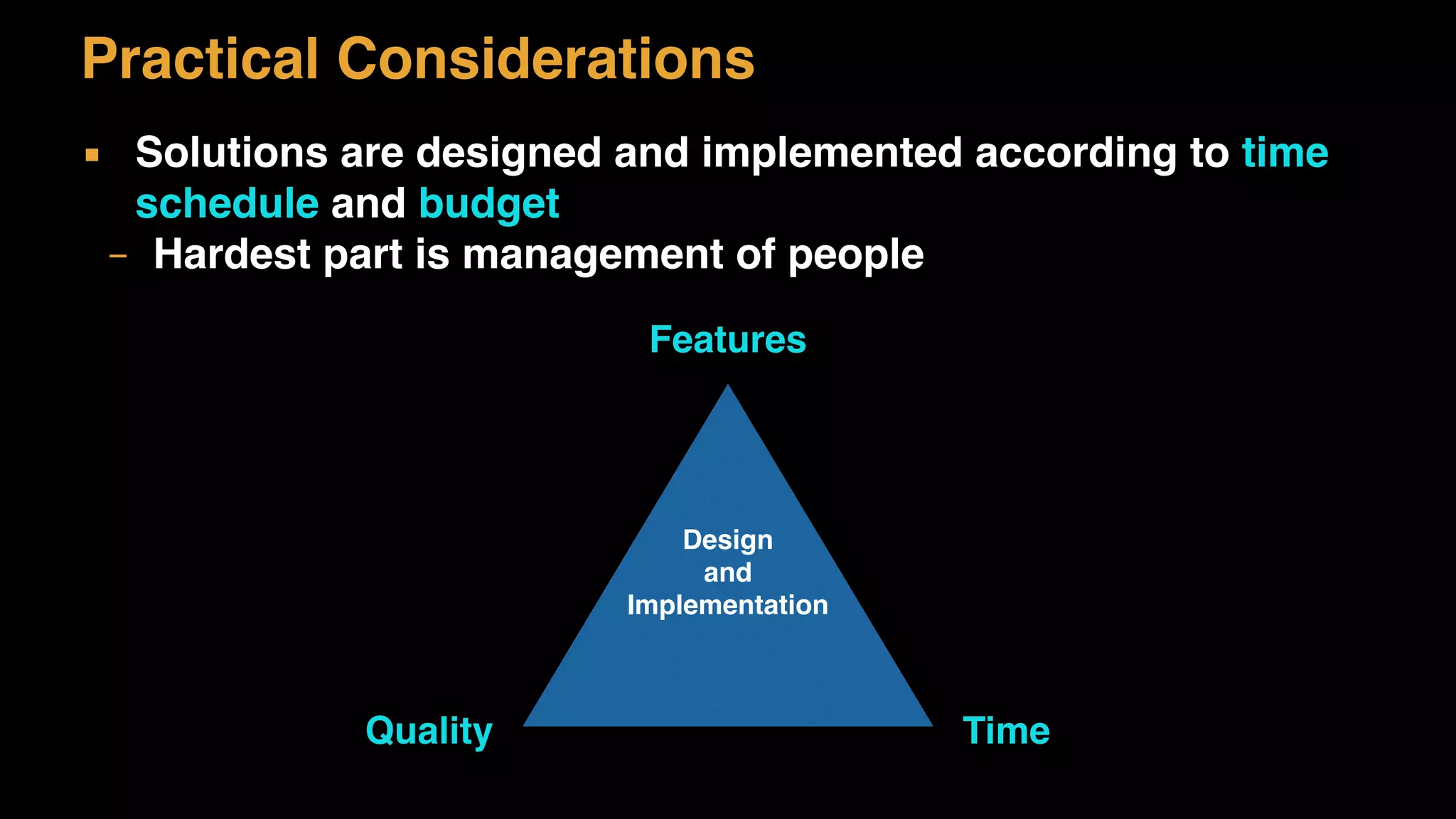
The document discusses architecture considerations for a software project. It outlines goals of having a robust, performant, scalable architecture following object oriented principles. It discusses non-functional requirements like performance, availability, security and constraints. It emphasizes understanding architecture drivers like functional requirements, quality attributes and principles to guide architectural decisions.