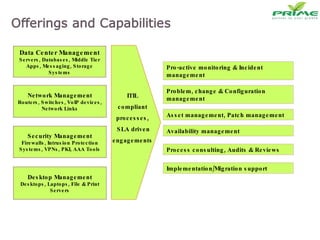
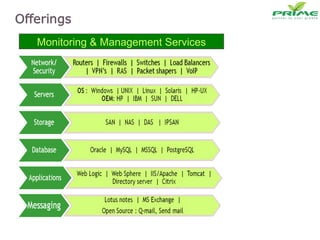
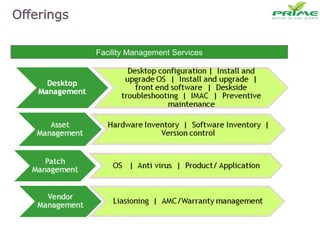
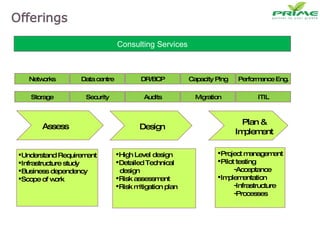
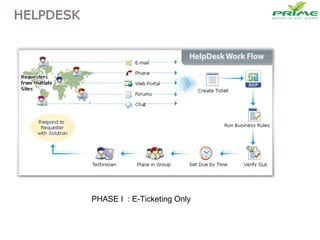
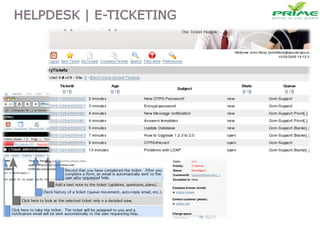
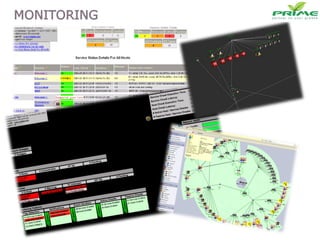
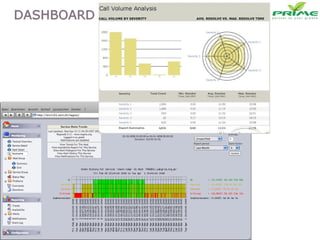
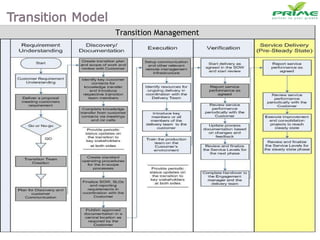
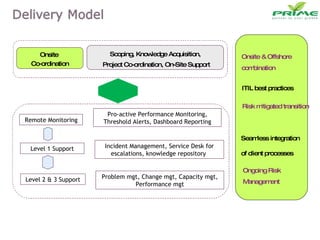
The document discusses various infrastructure management services including network management, security management, data center management, desktop management, database management, mail management, firewall management, and application management. It also discusses monitoring and management services, facility management services, consulting services, and disaster recovery and business continuity planning. The last section discusses different phased approaches to outsourcing infrastructure management services.