The document provides an in-depth analysis of SQL injection, detailing its definition, prevalence, and risks, as well as classification of various types of attacks. It outlines methods for preventing SQL injection attacks, including novel models and algorithms for detection and protection. Additionally, the document reviews significant cases of SQL injection incidents and the impacts they have had on organizations.






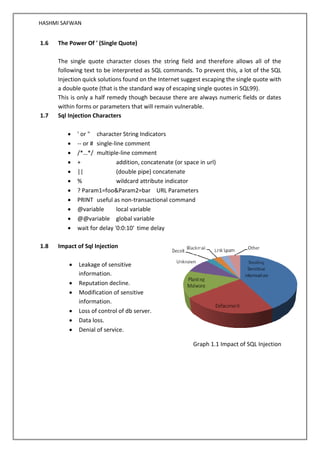
![HASHMI SAFWAN
1. SQL INJECTION
SQL injection is a type of security exploit in which the attacker adds SQL statements through
a web application's input fields or hidden parameters to gain access to resources or make
changes to data [1].
It's a serious vulnerability, which can lead to a high level of compromise - usually the ability
to run any database query.
1.1 What Is Sql?
SQL stand for Structured Query Language [2][3]. It allows us to access a database. SQL
is based on ANSI and ISO standard Computer Language. The most current standard is
SQL99. SQL statements are used to perform tasks such as retrieve, create, update or
delete data from a database.
Some common relational database management systems that use SQL are: Oracle, MS
SQL Server, MS Access, Ingres, DB2, Sybase, Informix, etc. Although there are many
versions of SQL language, However, the standard SQL commands such as "Select",
"Insert", "Update", "Delete", "Create", and "Drop" can be used throughout all
database with little changes. All of the core functions, such as adding, reading and
modifying data, are the same.
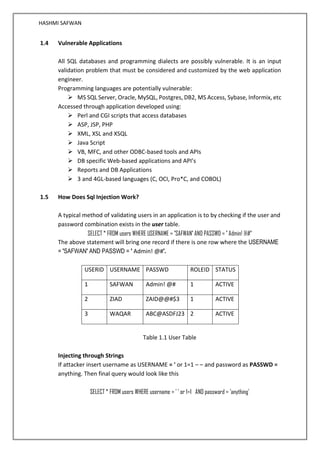
1.2 What Is Sql Injection?
The ability to inject SQL commands into the database engine through an existing
application.
It is an attack on web-based applications that connect to database back-ends in which
the attacker executes unauthorized (and unexpected) SQL commands by taking
advantage of insecure code and bad input validation. It is very often done on systems
connected to the Internet because it allows to completely bypass the firewall. SQL
injection attacks can be used to steal information from a database from which the
data would normally not be available and to gain access to host computers through
the database engine.
1.3 How Common Is It?
The principle issue with SQL Injection is that the weakness is begun when the web
application is coded. Most software engineers are still not mindful of the issue.
Instructional exercises and demo "layouts" on the Internet and even some that have
been transported with business databases advance building inquiries by connecting
strings, which is the primary hotspot for SQL Injection vulnerabilities.](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-7-320.jpg)

![HASHMI SAFWAN
1.9 Latest Sql Injection Statistics in 20016
SQL Injection logs ratio from one monitored network in the past 60 days (over 8000 events):
Fig 1.2 SQL Injection Log Ratio [4]
Fig 1.3 Identification of the attacking sources in the TP events [4]](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-11-320.jpg)
![HASHMI SAFWAN
Fig 1.4 Distribution by country of the attacking sources in the TP events [4]](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-12-320.jpg)


![HASHMI SAFWAN
3. PREVENTING SQL INJECTION ATTACKS (SQLIA)
3.1 Novel Model for Preventing SQLIA
Gaurav Srivastava and Kshitij Pathak Presented an architecture for preventing SQL Injection
Attack.
Fig 3.1 Web Architecture (a) [6]
3.2 Propose Architecture (b) [6]
This model proposes double authentication process on both relational and hierarchical
databases by applying tokenization approach on both databases. This task is performed via
three steps.
Step 1: Query Forward.
Step 2: Tokenization process on query.
Step 3: Comparison of array index.
Figure 3.2 shows the proposed architecture of SQLIA prevention through double
authentication via tokenization by using above three essential steps.
Step 1: Query Forwarding- When a query comes from a user via user interface, the input
query is forwarded to both databases, one which is created by relational approach and other
based on hierarchical approach.
Step 2: Tokenization Process on Query- the input query is divided into various tokens on the
basis of space, single quotes and double dashes between them. Once the tokens are decided,
they are stored in array. Tokenization process is applied on both databases.](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-15-320.jpg)
![HASHMI SAFWAN
Step 3: Comparison of Array Index- In this step, the array length of both the arrays are
compared. If the length of L1 and L2 are same, there is no injection present in the query and
the query is proceeding further to main database for retrieving result. But if the lengths
L1andL2are different, then injection exists and query is not forwarded to the database. The
result is a NULL value.
3.2 Pattern Matching Algorithm
This proposed scheme has following two modules [7],
1) Static Phase
Step 1: User generated SQL Query is send to the proposed Static Pattern Matching
Algorithm
Step 2: The Static Pattern Matching Algorithm.
Step 3: The Anomaly patterns are maintained in Static Pattern List, during the
pattern matching process each pattern is compared with the stored Anomaly
Pattern in the list
Step 4: If the pattern is exactly match with one of the stored pattern in the
Anomaly Pattern List then the SQL Query is affected with SQL Injection Attack
2) Dynamic phase
Step 1: Anomaly score value us calculated for the user generated SQL Query, if
this value is more than threshold value, then Alarm is given and query will pass to
the administrator.
Step 2: If the Admin receive any alarm then query is manually analyzed. If this
query is infected by SQLIA then a pattern is generated and will be added to static
pattern list.
Fig 3.3 Pattern Matching Algorithm for Preventing SQLIA [7]](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-16-320.jpg)
![HASHMI SAFWAN
3.3 SQLrand Architecture
➢ Apply Instruction-set randomization to SQL
➢ Creating instances of the language that are unpredictable to the attacker
➢ Queries injected by the attacker will be caught by the database parser.
➢ An intermediary proxy that translates the random SQL to its standard
language.
➢ Mechanism imposes negligible performance overhead to query processing and
can be easily retrofitted to existing systems.
Fig. 3.4 SQLrand Architecture [8]
Mechanism provides a tool reads an SQL statement(s) and rewrites all keywords
with the random key appended.
select gender, avg(age) from cs101.students
where dept = %d
group by gender
The utility will identify the six keywords in the example query and append the key to
each one (e.g., when the key is “123”):
select123 gender, avg123 (age)
from123 cs101.students
where123 dept = %d
group123 by123 gender
Built proxy server that sits between the client (web server) and SQL server, de-
randomizes requests received from the client, and conveys the query to the server.
If an SQL injection attack has occurred, the proxy’s parser will fail to recognize the
randomized implementation focused on CGI scripts as the query generators, a similar
approach applies when using JDBC query and will reject it.](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-17-320.jpg)
![HASHMI SAFWAN
3.4 Comparative Analysis of All Existing Models
Model Advantages Disadvantages
Sania 1) It can detect SQL
vulnerabilities during the
development and
debugging phase of a web
application.
2) It identifies vulnerable
spots by analysing SQL
queries.
1) It requires knowledge of
database in lack of
knowledge attack cannot be
handled.
SBSQLID 1) The main advantage of
this approach is, error
massage generated does
not contain any Metadata.
(Information about the
database which could help
the attacker)
1) Web service is not
integrated with the web
application. Any
modification that should be
done to the system should
be done in such a way that
it should be supported by
the web service.
RDUD 1) It uses supervised
learning approach using
SVM to learn and to classify
a query at run time.
2) It is based on
classification task.
1) Special care is taken for
maintaining the integrity of
the web profile files to avoid
poisoning of web profiles.
2) Not applicable for by pass
Authentication
Trans SQL 1) It is a server side
application. So, it does not
change the legacy web
application.
2) Query is checked twice
before retrieving
information.
1) This model is unable to
prevent against set
operations, instances, alias
directly.
Query Tokenization 1) It converts query into
tokens which contains
between space, single
quotes and double dashes.
2) Applied for all types of
SQLIA.
1) The original query of
input query which contain
injection, must be stored.
Table 3.1 Comparative Analysis of All Existing Models [9]](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-18-320.jpg)
![HASHMI SAFWAN
4. Top Most 5 Victim of SQL Injection Attacks
4.1 TalkTalk Cyber-attack [10]
A cyber-attack exploits vulnerabilities in three webpages which are operated by
TalkTalk. The exploitation of this vulnerability allows access to an underlying database
holding customers’ personal data including names, addresses, dates of birth, phone
numbers, email addresses and financial information.
The attack type - SQL injection - was identified shortly after midday on 21 October,
and around an hour later TalkTalk removed its websites and replaced them with a
holding page.
TalkTalk says 156,959 customers' personal details accessed, 15,656 bank account
numbers & sort codes stolen
The investigation found there had been two previous SQL injection attacks on 17 July
2015 and between 2-3 September 2015 but TalkTalk did not take any action due to a
lack of monitoring of the webpages.
The ICO decides to issues its biggest ever fine – £400,000 – to TalkTalk, Firm settles
ICO fine for £320,000 - Saves £80,000 by coughing up early.
4.2 Russian Hackers Amass Over a Billion Internet Password[11]
A Russian crime ring has amassed the largest known collection of stolen Internet
credentials, including 1.2 billion user name and password combinations and more
than 500 million email addresses, security researchers say.
So far, the criminals have not sold many of the records online. Instead, they appear to
be using the stolen information to send spam on social networks like Twitter at the
behest of other groups, collecting fees for their work
the Russian hackers have been able to capture credentials on a mass scale using
botnets — networks of zombie computers that have been infected with a computer
virus — to do their bidding. Any time an infected user visits a website, criminals
command the botnet to test that website to see if it is vulnerable to a well-known
hacking technique known as an SQL injection, in which a hacker enters commands that
cause a database to produce its contents. If the website proves vulnerable, criminals
flag the site and return later to extract the full contents of the database.
4.3 Human Rights Foundation Website Hacked, Thousands of Accounts Exposed [12]
The Hungarian Human Rights Foundation website was hacked by Kapustkiy and
CyberZeist, who managed to get access to over 20,000 accounts and personal
information, including phone numbers and home addresses.](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-19-320.jpg)
![HASHMI SAFWAN
Security pentester Kapustkiy told us that the data breach was possible with a SQL
injection, which provided him with access to databases that included thousands of
accounts, including some that are related to the US government (using the @state.gov
suffix).
4.4 Hackers exploit vBulletin flaw to access 27M accounts on 11 websites [13]
Attackers used a flaw in the internet forum software vBulletin to breach 11 websites,
exposing the personal information of 27 million accounts, according to the breached
data monitoring service Leaked Source.
The breached websites used outdated versions of the vBulletin software that
contained SQL Injection flaws in the Forum Runner add-on
Several other domains were also breached, including expertlaw.com,
ageofconan.com, anarchy-online.com, freeadvice.com, gamesforum.com,
longestjourney.com, ppcgeeks.com, and thesecretworld.com.](https://image.slidesharecdn.com/sqlinjection-171022063807/85/Sql-injection-20-320.jpg)

