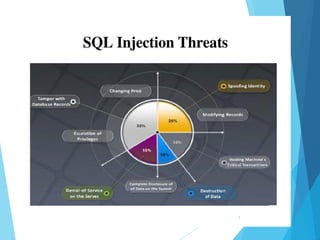
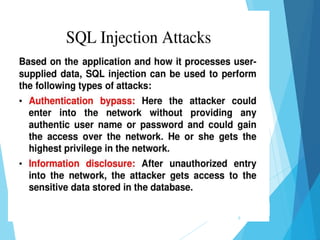
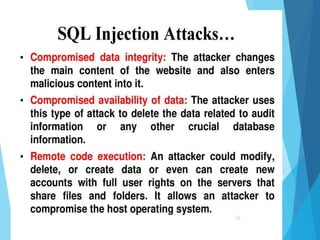
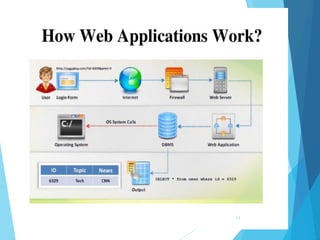
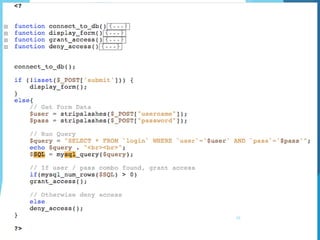
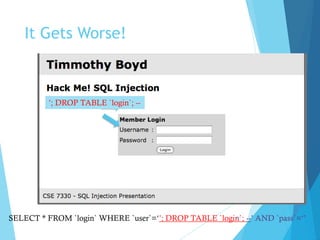
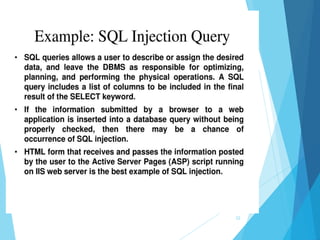
This document discusses SQL injection, including what it is, real world examples, important SQL syntax, and prevention methods. SQL injection is a code injection technique that exploits security vulnerabilities in user input handlers to expose sensitive data from a database. It provides examples of SQL injection attacks, such as retrieving hidden data or subverting application logic. The document emphasizes that SQL injection is a serious threat and outlines techniques for preventing vulnerabilities like validating user input and using prepared statements.