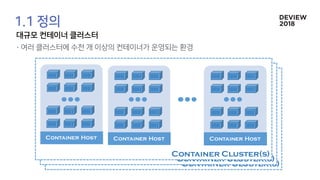
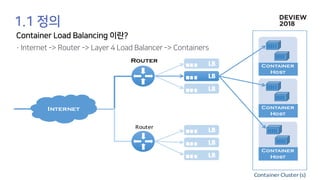
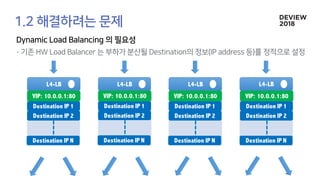
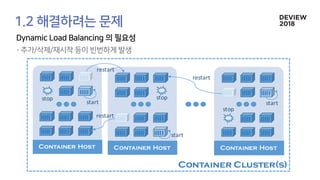
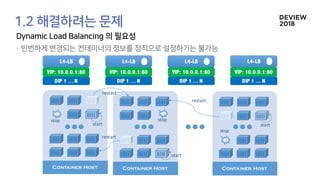
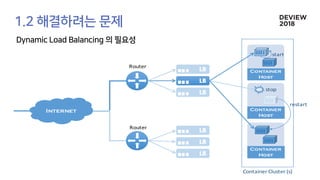
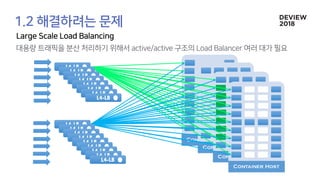
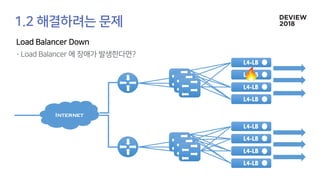
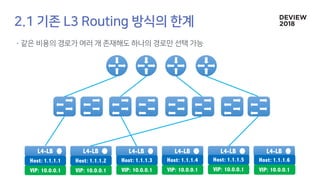
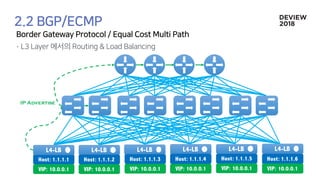
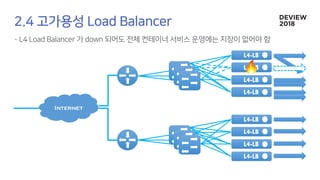
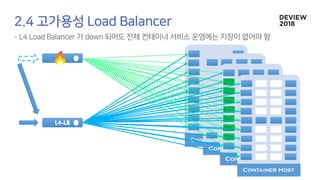
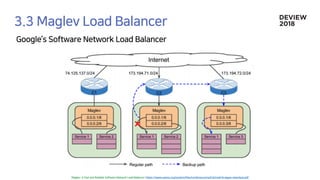
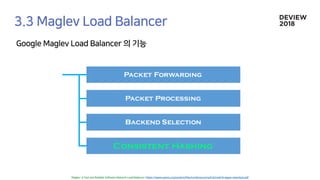
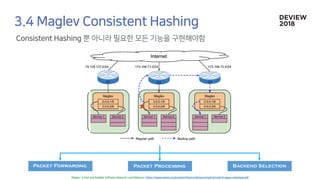
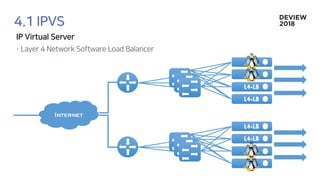
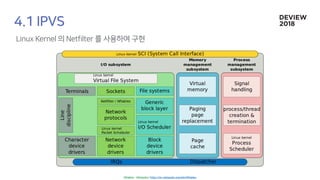
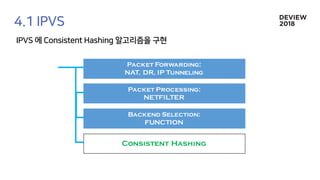
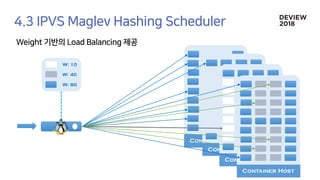
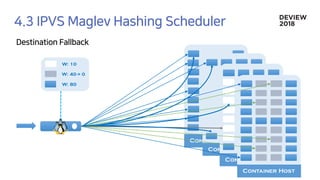
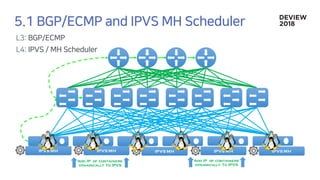
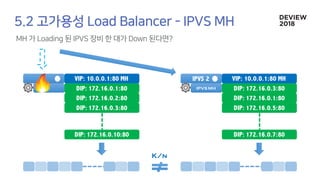
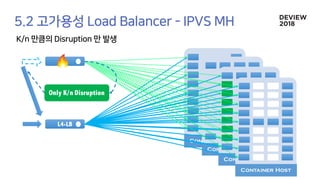
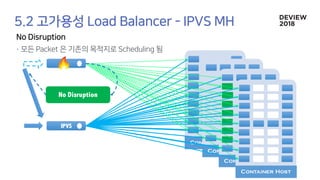
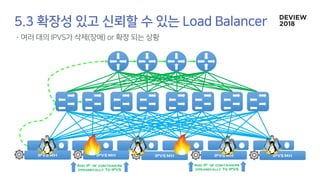
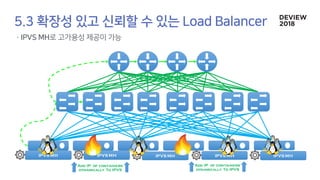
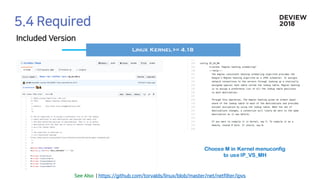
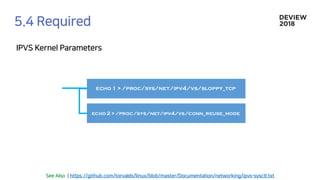
The document discusses the architecture and functionality of a load-balancing system involving container clusters and hosts. It emphasizes high availability, efficient load balancing techniques, and the use of IPVS with Maglev hashing scheduler for handling traffic. It also outlines connection management during load balancer disruptions and suggests dynamic updates to the IPVS configuration for reliability.



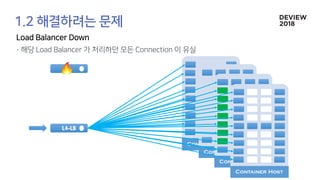

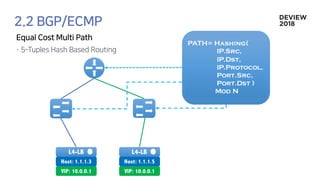
![192.68.0.2
Container[0]
Container[1]
Container[2]
Container[3]
L4-LB
1. Connection
Established With
Container[2]
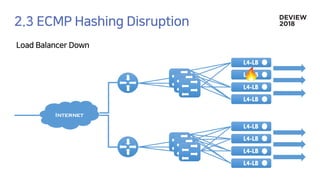
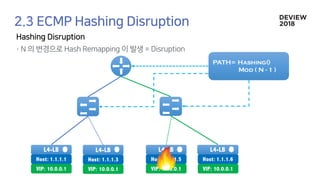
2. A Load
Balancer Down
3. ECMP Disruption.
Forward packet
another l4
4. Container[0] has no
idea about connection
with container[2]
5. Container[0] Send RST.
Connection Closed](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-20-320.jpg)
![192.68.0.3
Container[0]
Container[1]
Container[2]
Container[3]
L4-LB
L4-LB
1. Connection
Established With
Container[3]
2. A Load
Balancer Down
3. ECMP Disruption.
Forward packet
another l4 although
the serving LB is
alive. 4. Container[1] has no
idea about connection
with container[3]
5. Container[1] Send RST.
Connection Closed
L4-LB](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-21-320.jpg)



![192.68.0.1 Hashing(IP) % 2
Container[0]
Container[1]
Hashing(IP) % 2
Hashing(IP) % 2
Hashing(IP) % 2
192.68.0.2
192.68.0.3
192.68.0.4](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-27-320.jpg)
![192.68.0.1 Hashing(IP) % 4
Hashing(IP) % 4
Hashing(IP) % 4
Hashing(IP) % 4
192.68.0.2
192.68.0.3
192.68.0.4
Container[0]
Container[1]
Container[2]
Container[3]](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-28-320.jpg)
![192.68
.0.2
Container[0]
192.68
.0.3
Container[2]
192.68
.0.4
Container[0]
Container[3]
Container[2]
192.68
.0.1
Container[1]
Container[3]
Container[1]
Guarantee
to remap
K/n only](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-29-320.jpg)
![192.68
.0.2
Container[0]
192.68
.0.3
Container[2]
192.68
.0.4
Container[0]
Container[3]
Container[2]
192.68
.0.1
Container[1]
Container[3]
Container[1]
Efficient
Load
Balancing](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-30-320.jpg)
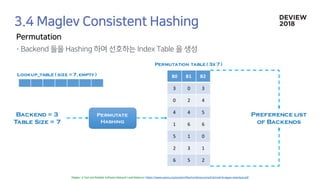
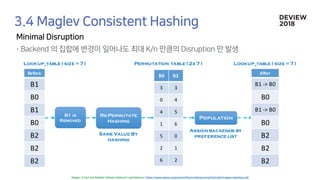
![Population
Permutation table ( 3x 7 )
B1 B0 B1 B0 B2 B2 B0
Lookup_table ( size =7 )
B0 B1 B2
3 0 3
0 2 4
4 4 5
1 6 6
5 1 0
2 3 1
6 5 2
[0] [1] [2] [3] [4] [5] [6]
Assign backends by
preference list](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-34-320.jpg)
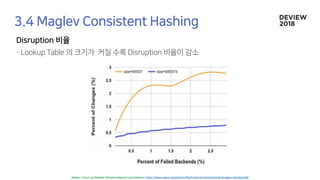
![B1 B0 B1 B0 B2 B2 B0
each backend will receive an
almost equal numberof
connections.
[0] [1] [2] [3] [4] [5] [6]
L4-LB
L4-LB
B0 =3 * connection
B1 =2 * connection
B2 =2 * connection](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-35-320.jpg)


![IPVS 1 VIP: 10.0.0.1:80 MH
DIP: 172.16.0.1:80
DIP: 172.16.0.2:80
DIP: 172.16.0.3:80
DIP: 172.16.0.10:80
IPVS 2 VIP: 10.0.0.1:80 MH
DIP: 172.16.0.3:80
DIP: 172.16.0.1:80
DIP: 172.16.0.5:80
DIP: 172.16.0.7:80
ip_vs_mh_Lookup[ ] of 10.0.0.1:80in ipvs 1
ip_vs_mh_permutate() &
ip_vs_mh_populate()
ip_vs_mh_Lookup[ ] of 10.0.0.1:80in ipvs 2
ip_vs_mh_permutate() &
ip_vs_mh_populate()
IPVS MH IPVS MH](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-52-320.jpg)
![192.68.0.2
IPVS
IPVS MH
IPVS
IPVS MH
IPVS
IPVS MH
Container[0]
Container[1]
Container[2]
Container[3]
[2]
[2]
[2]](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-53-320.jpg)

![IPVS MH
IPVS 1 VIP: 10.0.0.1:80 MH
DIP: 172.16.0.1:80
DIP: 172.16.0.2:80
DIP: 172.16.0.3:80
DIP: 172.16.0.10:80
IPVS 2 VIP: 10.0.0.1:80 MH
DIP: 172.16.0.1:80
DIP: 172.16.0.2:80
DIP: 172.16.0.3:80
DIP: 172.16.0.10:80
IPVS MH
ip_vs_mh_Lookup[ ] of 10.0.0.1:80in ipvs 1 ip_vs_mh_Lookup[ ] of 10.0.0.1:80in ipvs 2](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-58-320.jpg)
![192.68.0.2
Container[0]
Container[1]
Container[2]
Container[3]
IPVS
1. Connection
Established With
Container[2]
2. A Load
Balancer Down
3. ECMP Disruption.
Forward packet
another l4
4. IPVS MH can forward
the packet to same
destination by hashing.
IPVS MH
5. Continue the
Established connection.](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-60-320.jpg)
![192.68.0.3
Container[0]
Container[1]
Container[2]
Container[3]
IPVS
1. Connection
Established With
Container[3]
2. A Load
Balancer Down
3. ECMP Disruption.
Forward packet
another l4 although
the serving LB is
alive.
IPVS
IPVS MH
4. IPVS MH can forward
the packet to same
destination by hashing
With no connection info.
5. Continue the
Established connection.](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-61-320.jpg)
![Old version: [233]대형 컨테이너 클러스터에서의 고가용성 Network Load Balancing](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-67-320.jpg)
![Old version: [233]대형 컨테이너 클러스터에서의 고가용성 Network Load Balancing](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-68-320.jpg)
![Old version: [233]대형 컨테이너 클러스터에서의 고가용성 Network Load Balancing](https://image.slidesharecdn.com/233largecontainerclusternetworkloadbalancing-181012024225/85/Old-version-233-Network-Load-Balancing-69-320.jpg)