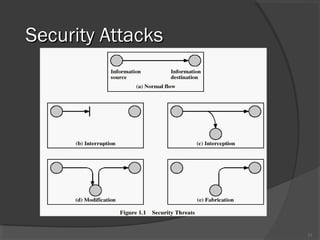
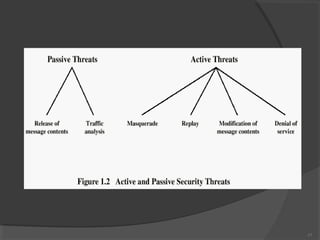
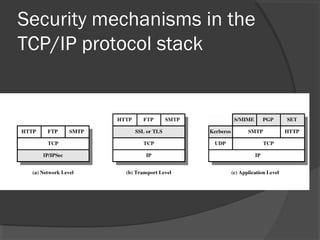
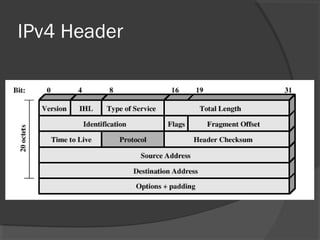
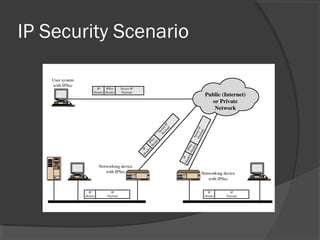
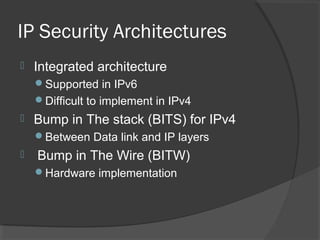
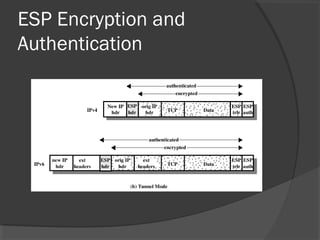
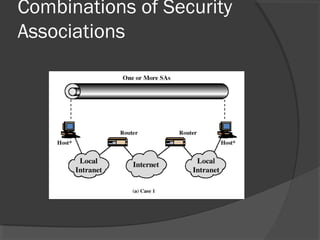
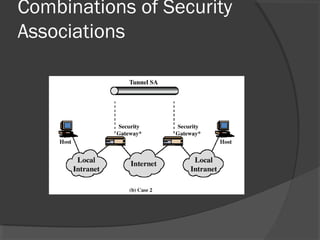
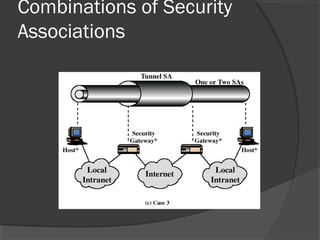
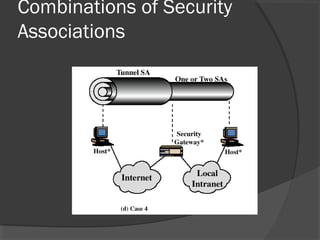
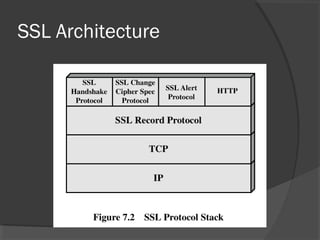
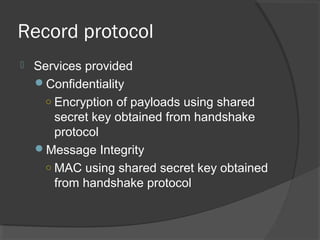
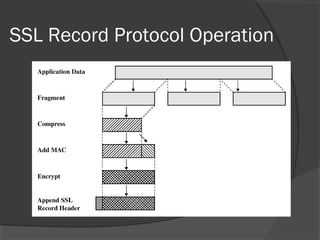
The document discusses web security and information security. It covers topics such as security attacks, security services defined by OSI, security mechanisms like encryption and digital signatures, and security protocols like SSL/TLS and IPSec. It provides an overview of how these different aspects of security work together to protect data and network communications.















































![Dual Signature
H(OI))]||)(([ PIHHEDS cKR=](https://image.slidesharecdn.com/websecurity-090721044112-phpapp02-130528170751-phpapp02/85/Websecurity-74-320.jpg)
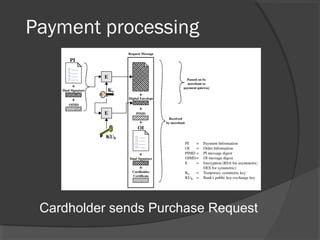


![Payment Request
Purchase request by card holder
Forwarded to payment gateway
○ Incl: EKs[PI+Dual sig+OIMD], EKUch[Ks]
To merchant
○ OI+dual sig+PIMD, CH certificate
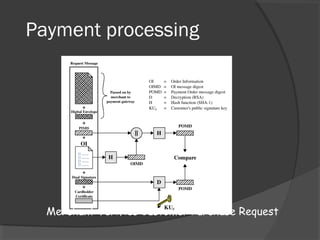
Purchase response by merchant
Incl: Trans ID, response block with order ack
signed by merchant using Kr, merchant’s
signature certificate
Card holder
Verifies merchant’s signature on response block](https://image.slidesharecdn.com/websecurity-090721044112-phpapp02-130528170751-phpapp02/85/Websecurity-79-320.jpg)
![Payment Authorization
Authorization Request to payment gateway from merchant
forwarded
○ PI+dual sig+OIMD+EKUch[Ks]
Generated
○ Auth block: EKms[SignKrm[Trans ID]]
○ EKUpg[EKms]
Certificates
○ Card holder signature key, merchant signature key and merchant key exchange certificates
Payment gateway
Verifies all certificates, obtains EKms, decrypts auth block, verifies merchant’s sign, verifies dual
sign, verifies trans ID, requests and receives an auth from issuer
Authorisation response by payment gateway to merchant
Auth block:
○ EKpgs[SignKrpg[authorisation]]
○ EKUm[EKpgs]
Capture token info:
○ EKpgs[SignKrpg[capture token]]
Certificate
○ Gateway’s signature key certifixcate](https://image.slidesharecdn.com/websecurity-090721044112-phpapp02-130528170751-phpapp02/85/Websecurity-80-320.jpg)
