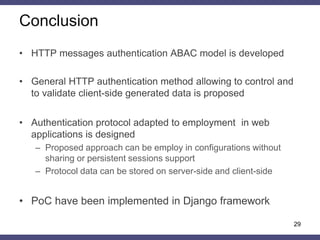
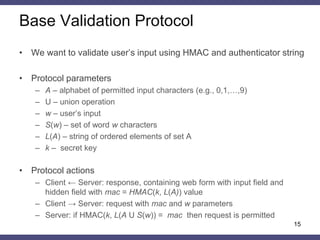
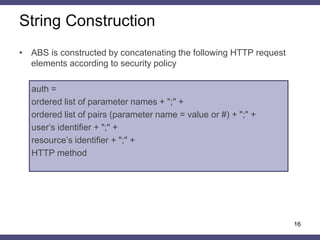
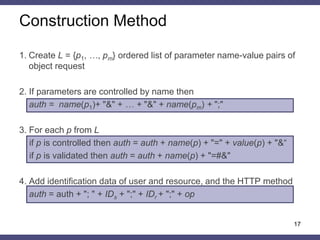
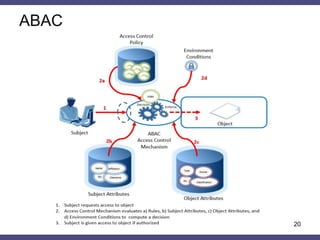
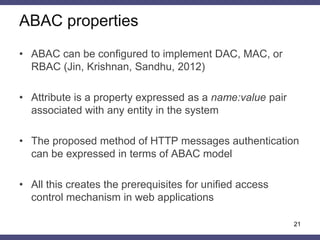
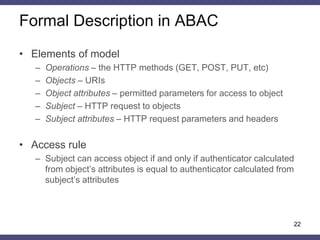
The document discusses a general method for HTTP message authentication using hash functions, aimed at enhancing web application security against common threats such as CSRF attacks and insecure direct object reference. It outlines various protection methods, the limitations of existing strategies, and presents a proposed authentication protocol that incorporates client-side data validation and various policies for secure user input. Additionally, it highlights the implementation of the proposed method in a Django framework as a proof of concept.



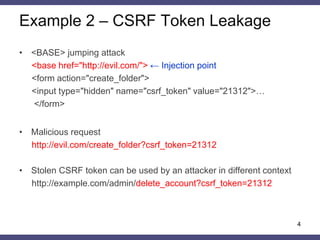
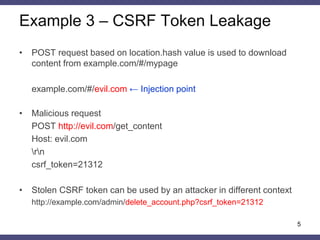
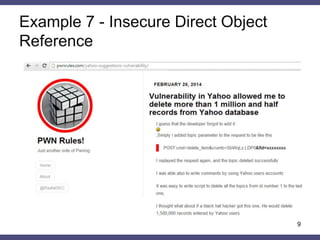
![Example 4 – CSRF Token Leakage
•Content from http://example.com includes the following form
<form action="$_SERVER['REFERER_URI']"> ← Injection point
<input type="hidden" name="csrf_token" value="21312">…
</form>
•http://site.com//evil.com/../search corresponds to the following form
<form action="//evil.com/../search">
<input type="hidden" name="csrf_token" value="21312">…
</form>
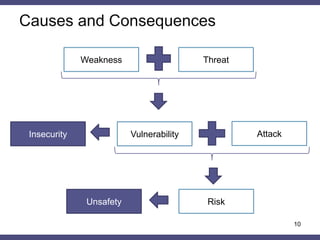
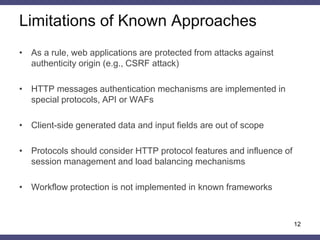
•Malicious request
http://evil.com/../search?csrf_token=21312
•Stolen CSRF token can be used by an attacker in different context
http://example.com/admin/delete_account.php?csrf_token=21312
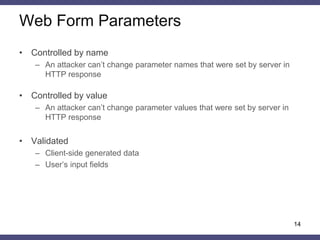
6](https://image.slidesharecdn.com/09092014-2-140916011602-phpapp02/85/General-Method-of-HTTP-Messages-Authentication-Based-on-Hash-Functions-in-Web-Applications-6-320.jpg)
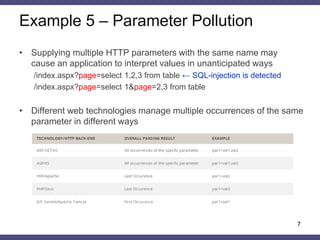









![Policy Example
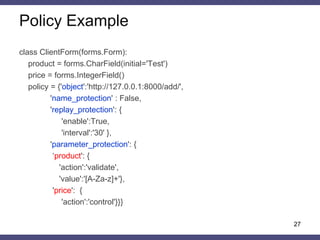
class ClientForm(forms.Form):
product = forms.CharField(initial='Test')
price = forms.IntegerField()
policy = {'object':'http://127.0.0.1:8000/add/',
'name_protection' : False,
'replay_protection': {
'enable':True,
'interval':'30' },
'parameter_protection': {
‘product': {
'action':'validate',
'value':'[A-Za-z]+'},
'price': {
'action':'control'}}}
28](https://image.slidesharecdn.com/09092014-2-140916011602-phpapp02/85/General-Method-of-HTTP-Messages-Authentication-Based-on-Hash-Functions-in-Web-Applications-28-320.jpg)