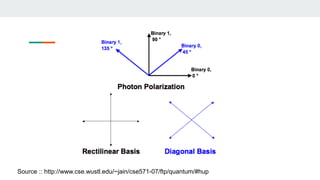
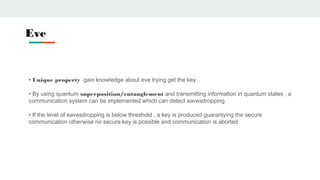
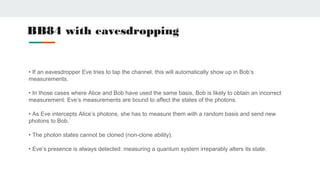
Quantum cryptography uses photons polarized in different quantum states to securely transmit encryption keys. It relies on principles of quantum mechanics rather than computational complexity. The BB84 protocol is an early quantum cryptography method where a sender and receiver use different polarization bases to encode and read bits, allowing them to detect if an eavesdropper has accessed the quantum channel. Quantum coin tossing protocols use polarized photons in superposition states for two parties to randomly generate a shared bit without communicating or trusting a third party. While promising for secure communication, quantum cryptography still faces challenges from practical implementation and transmission over long distances.