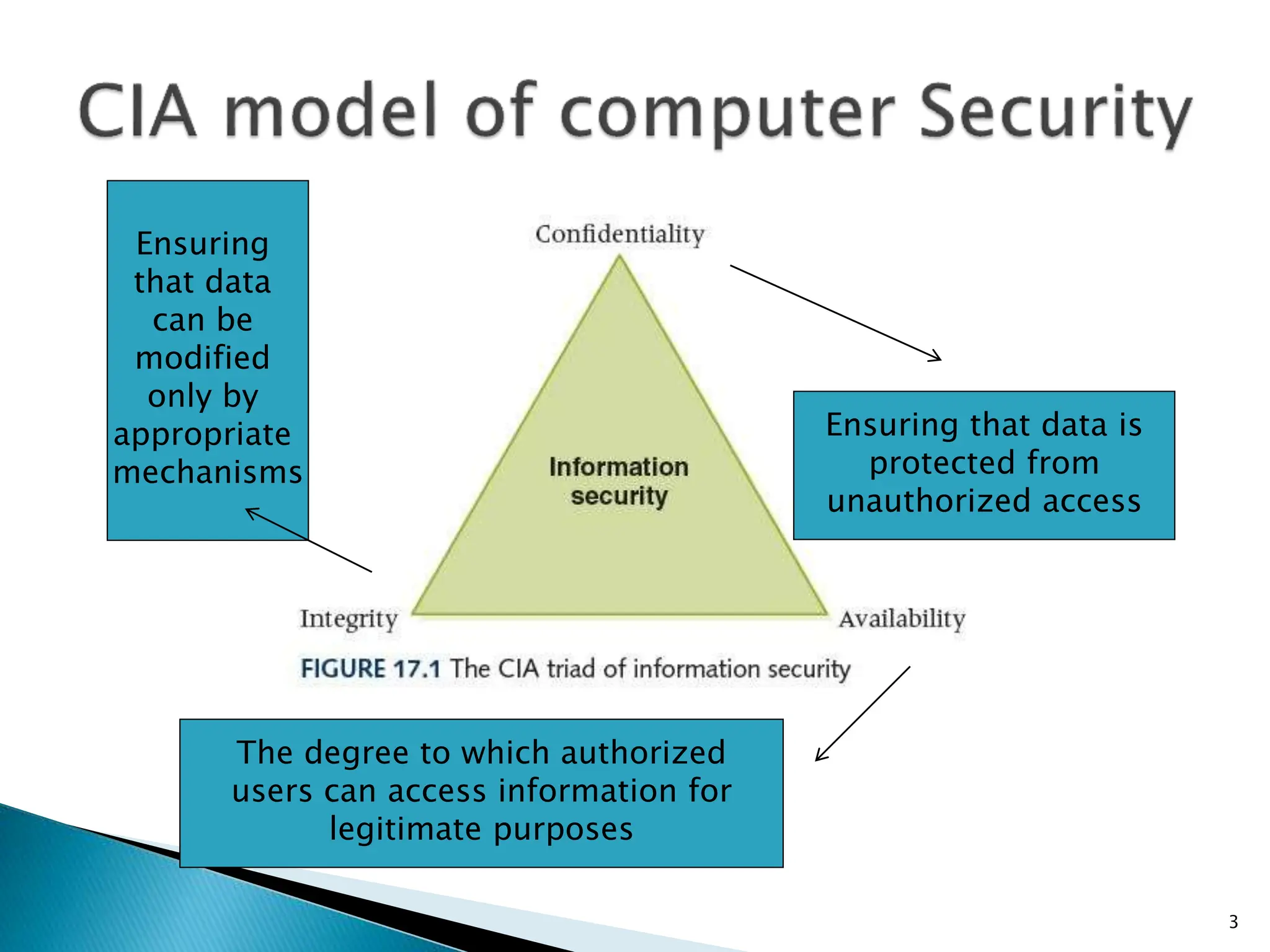
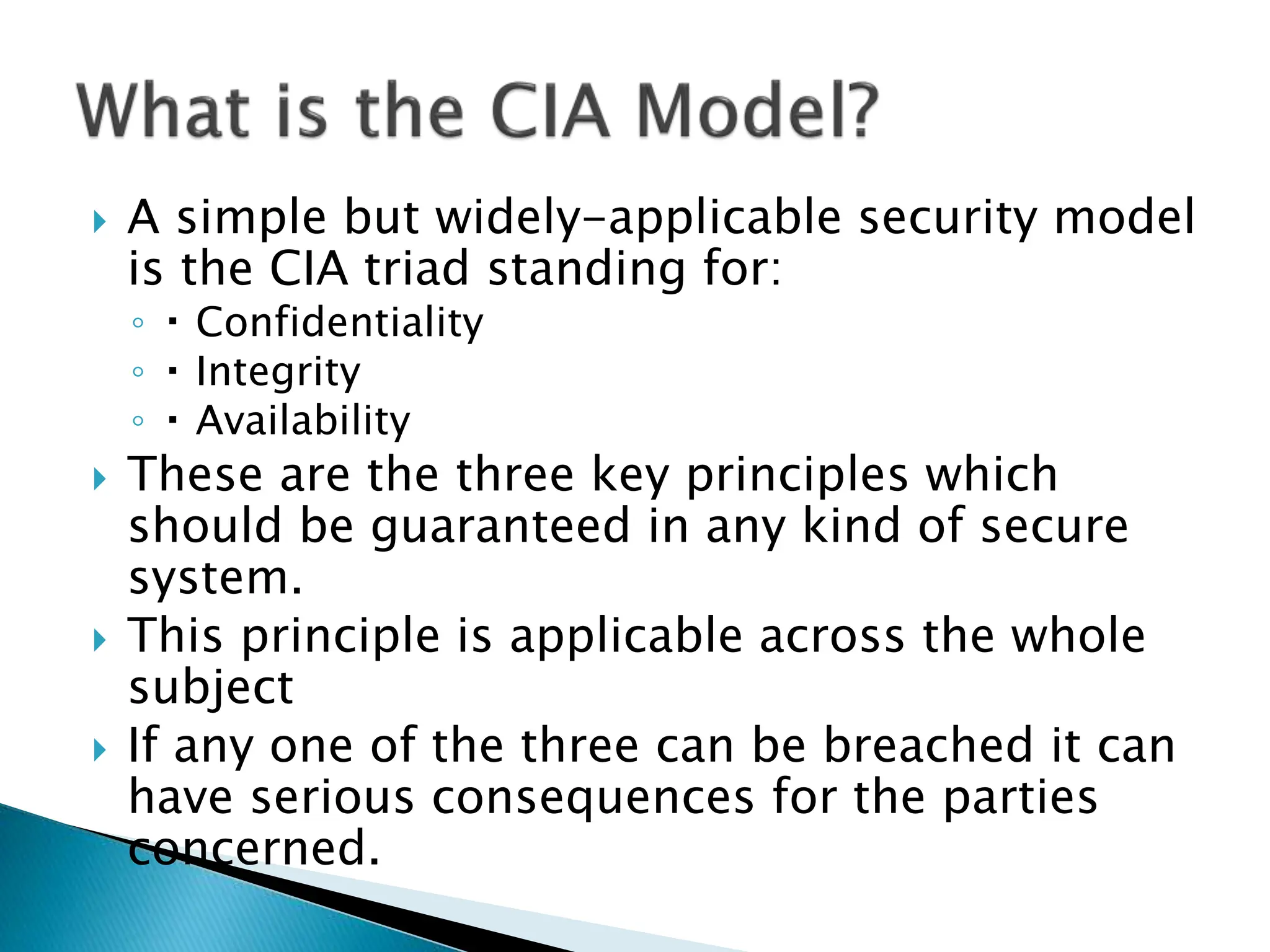
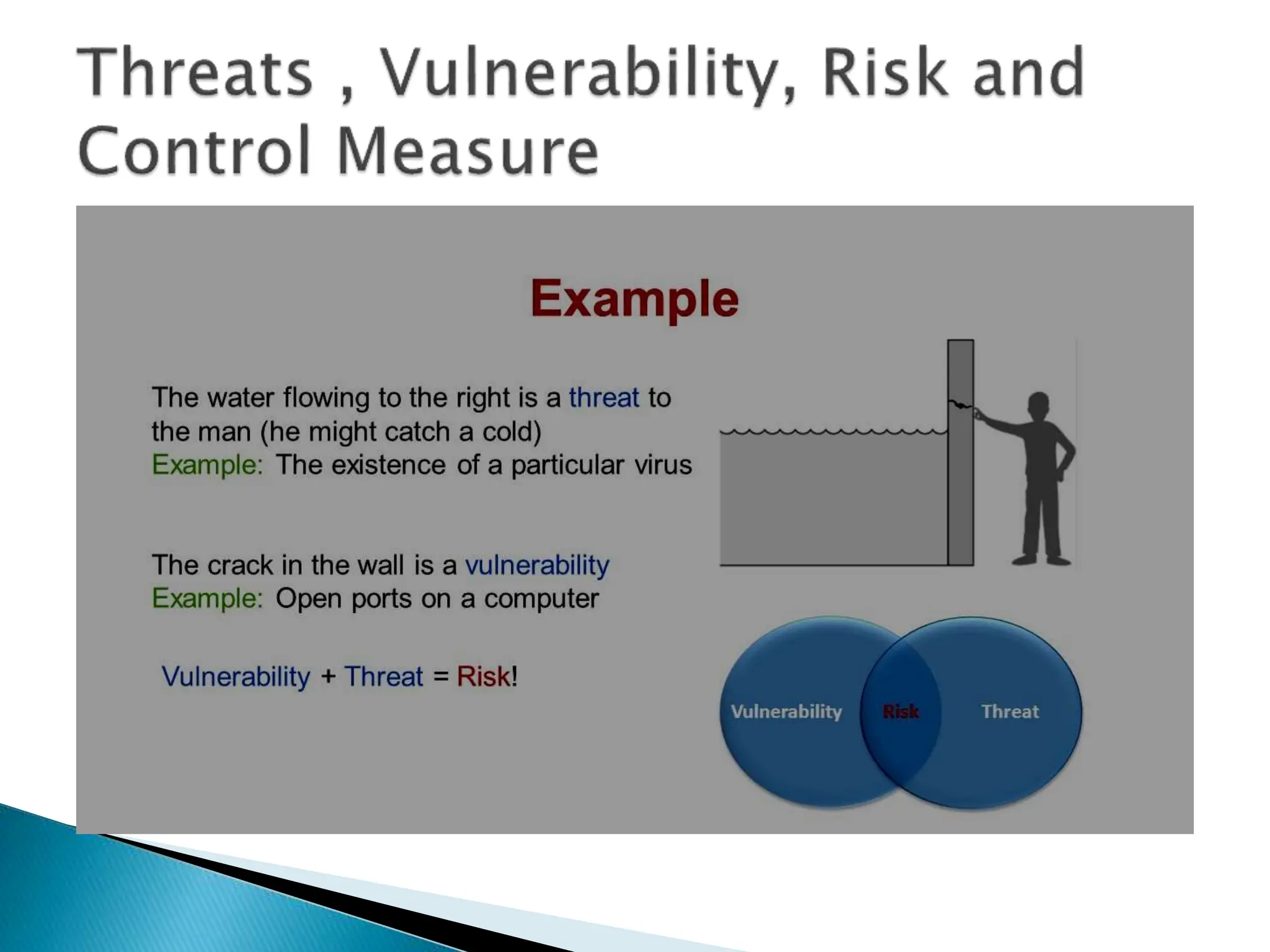
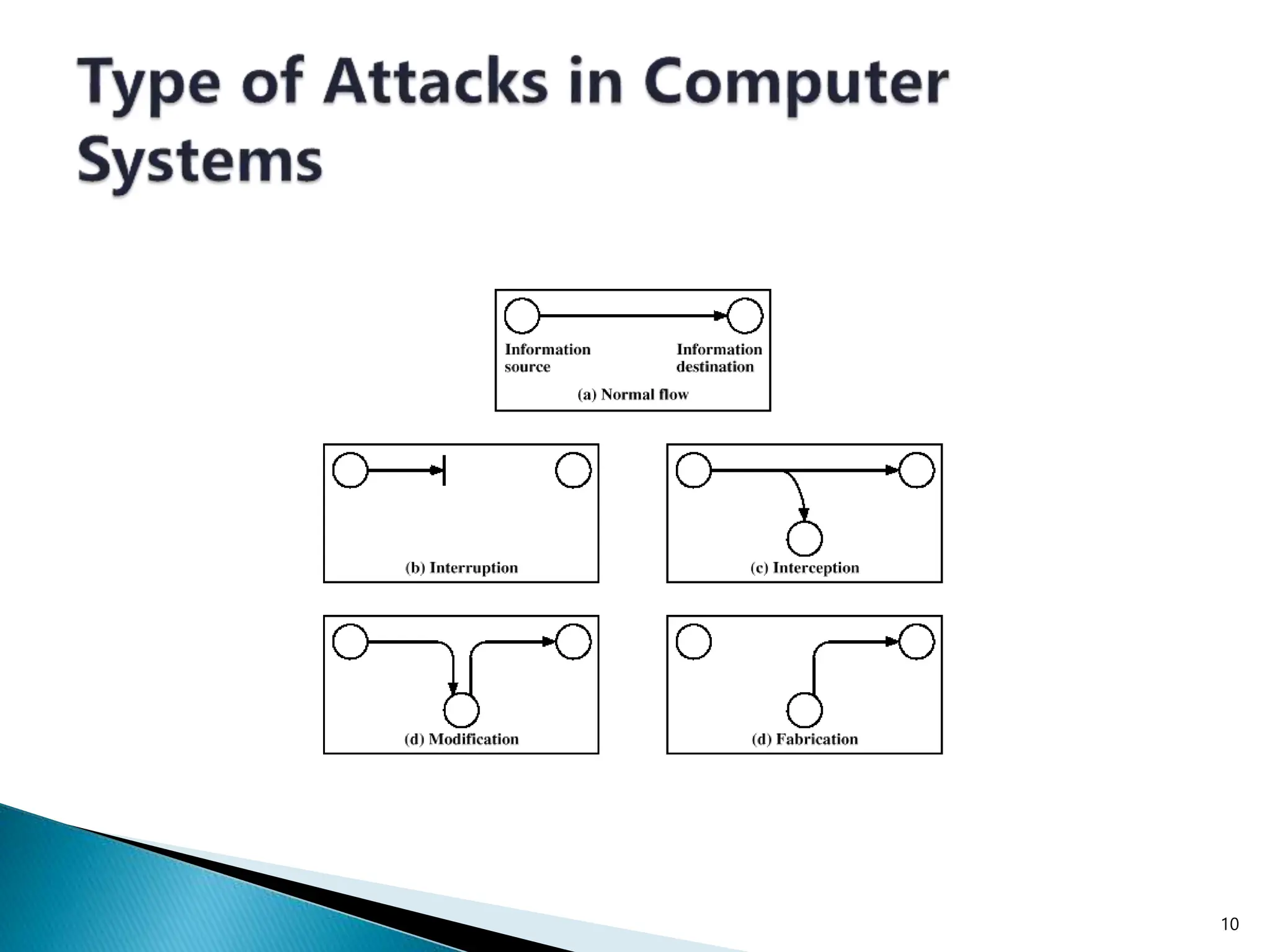
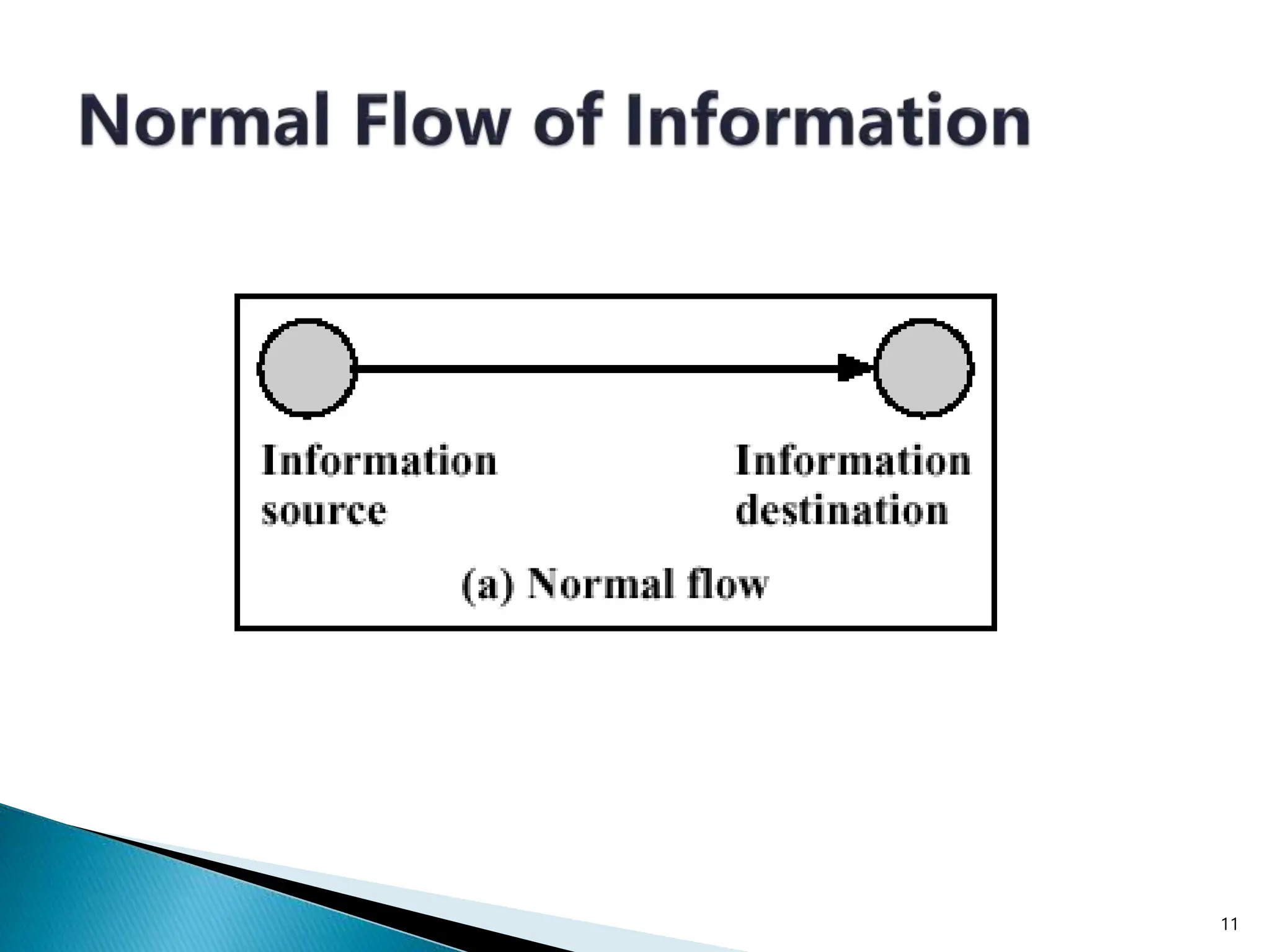
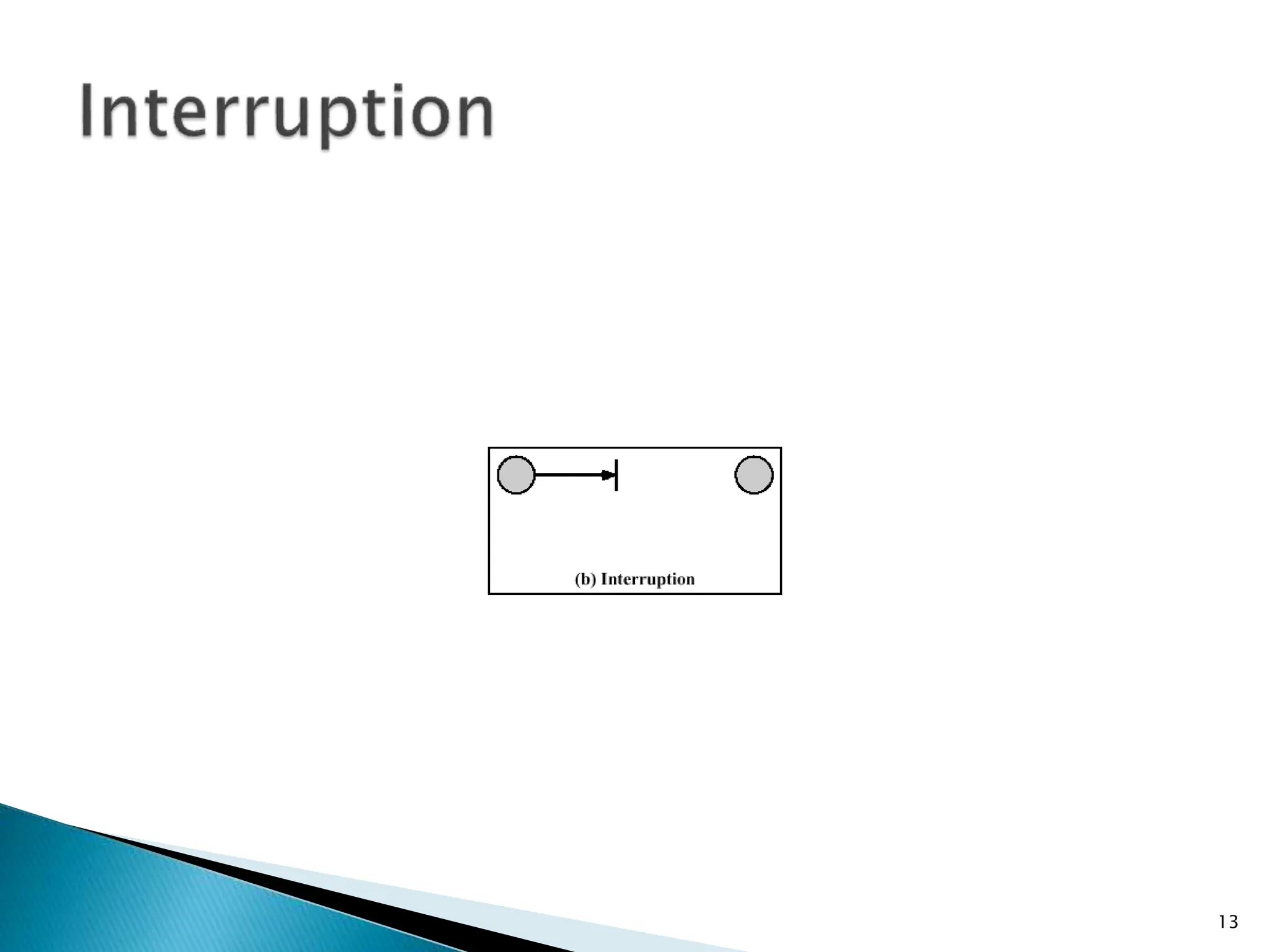
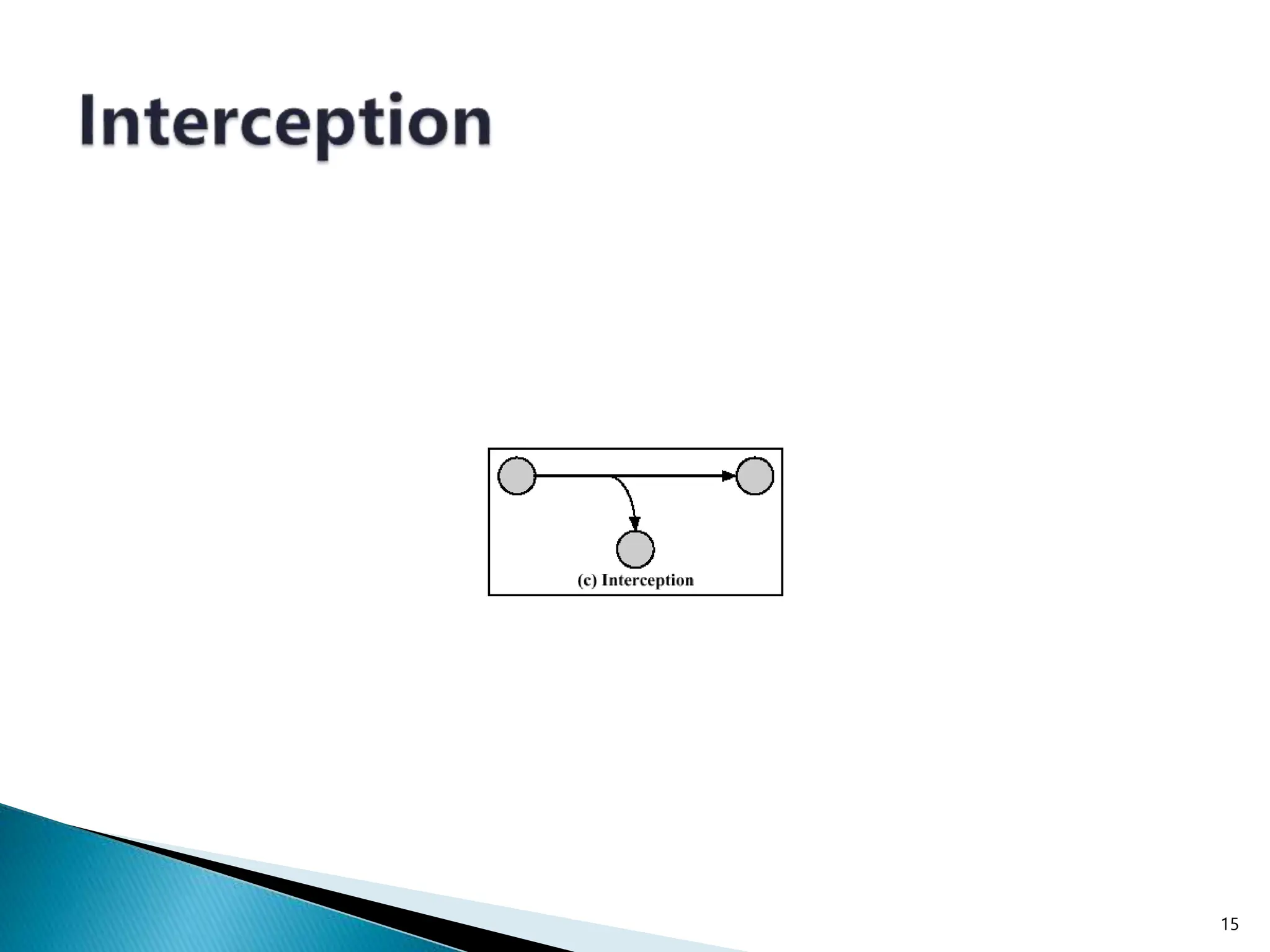
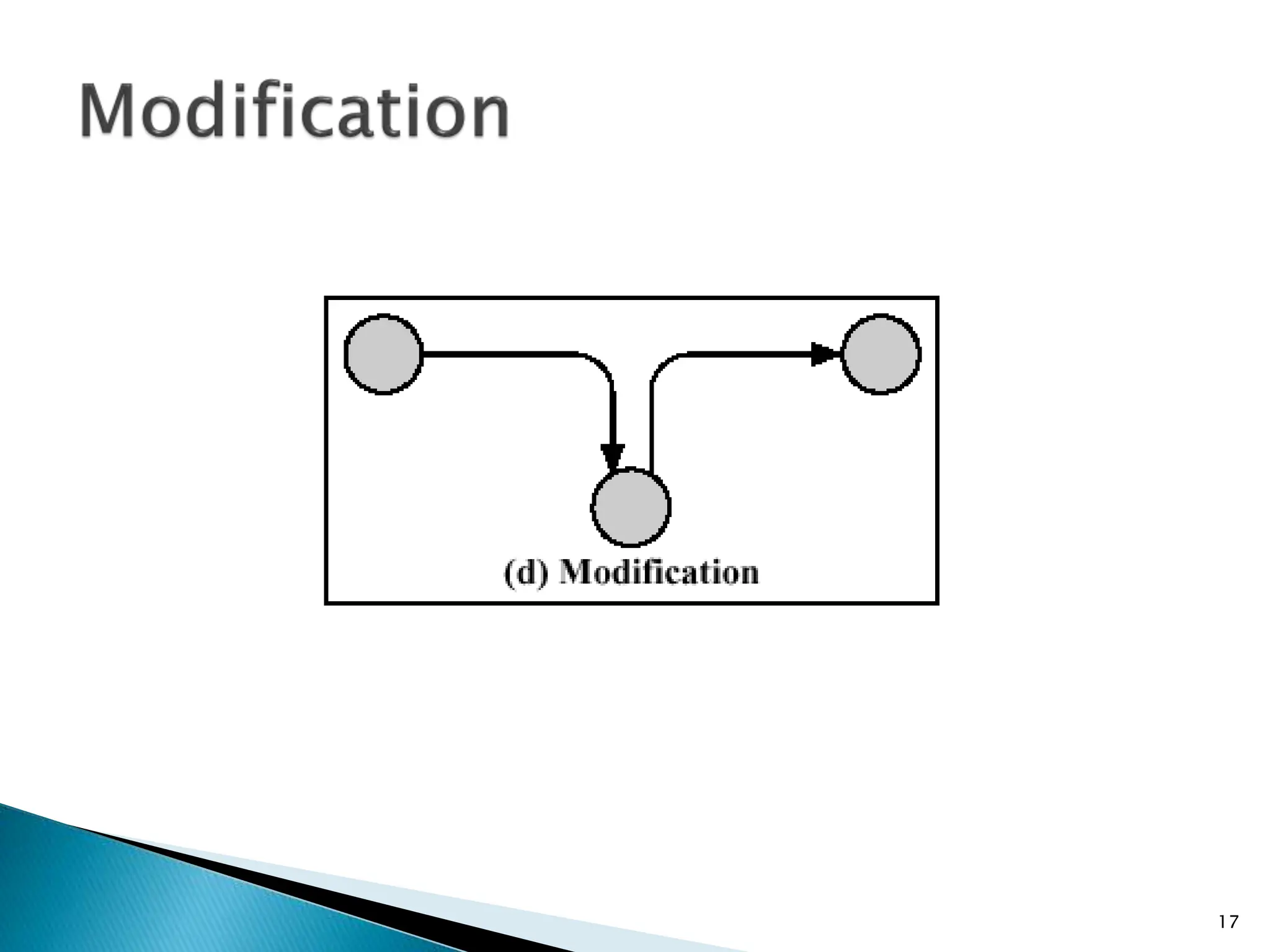
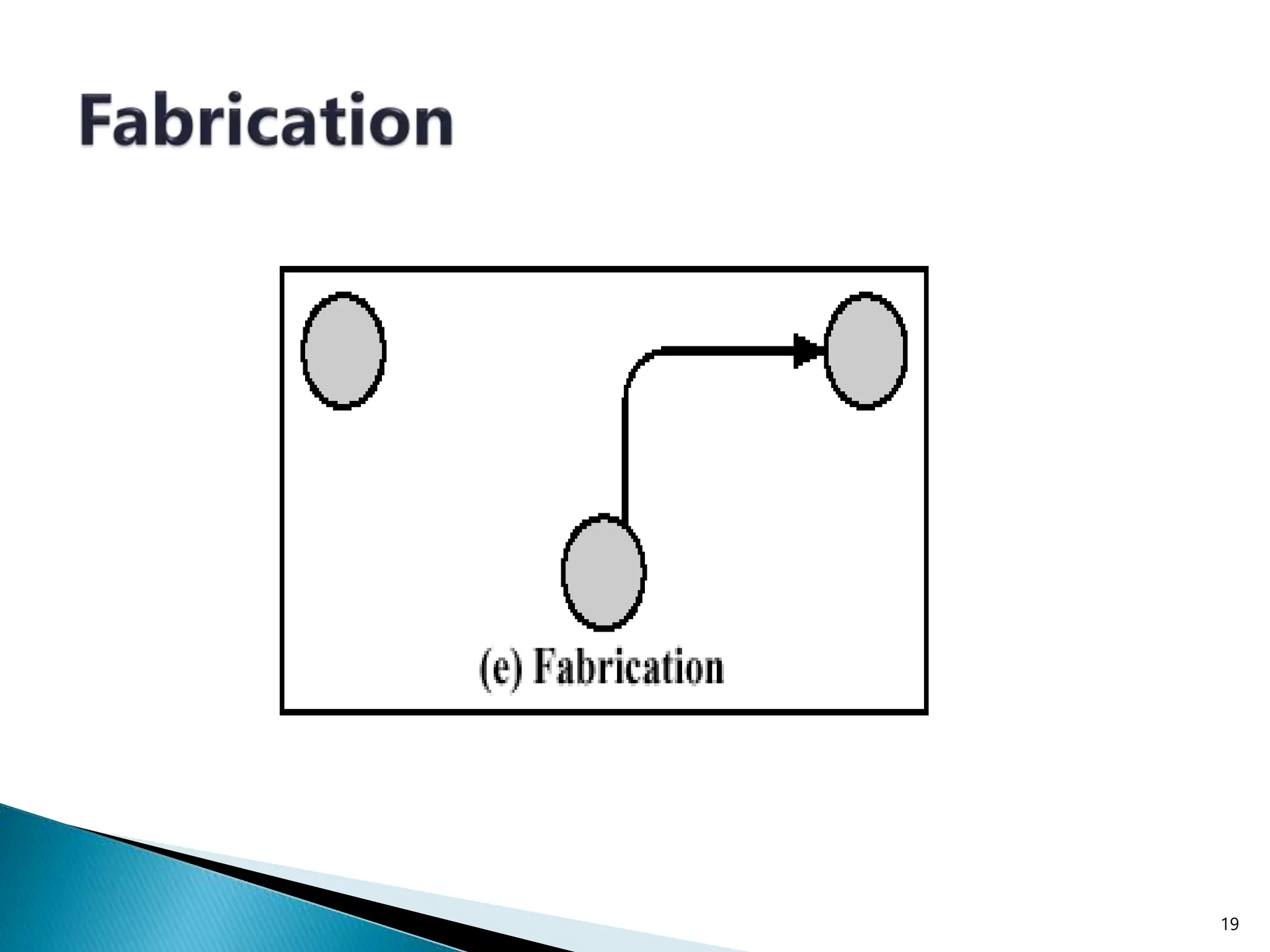
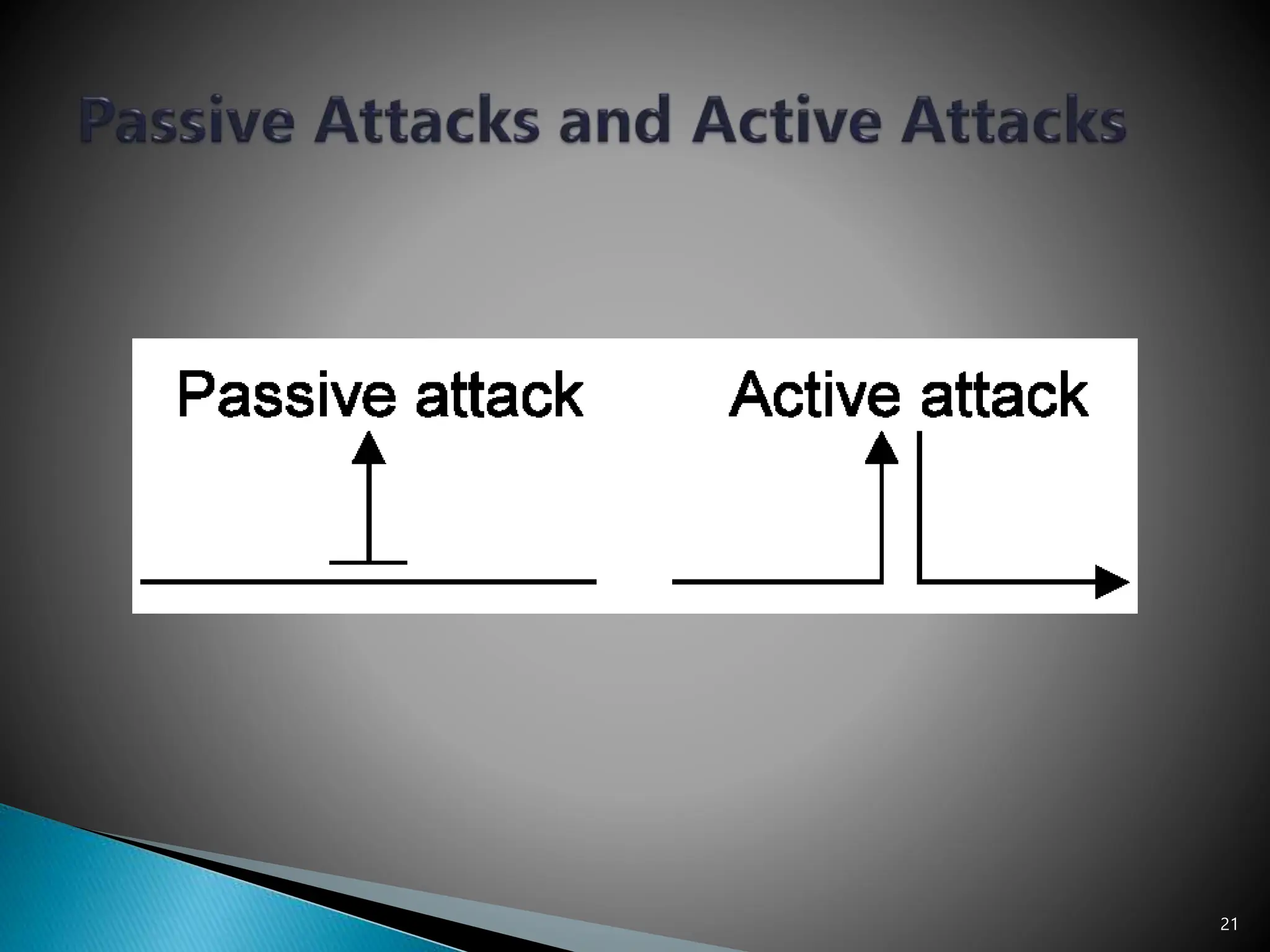
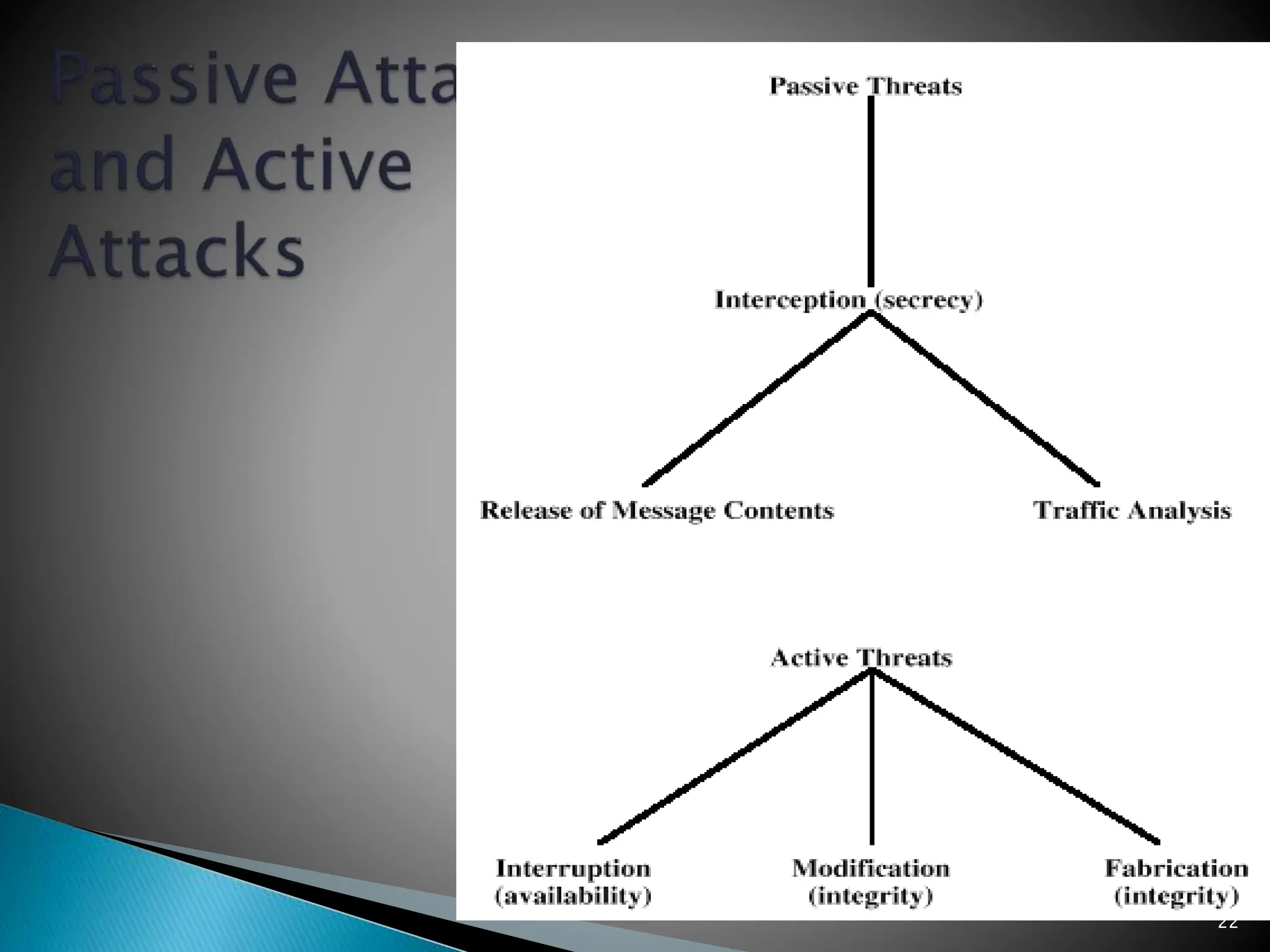
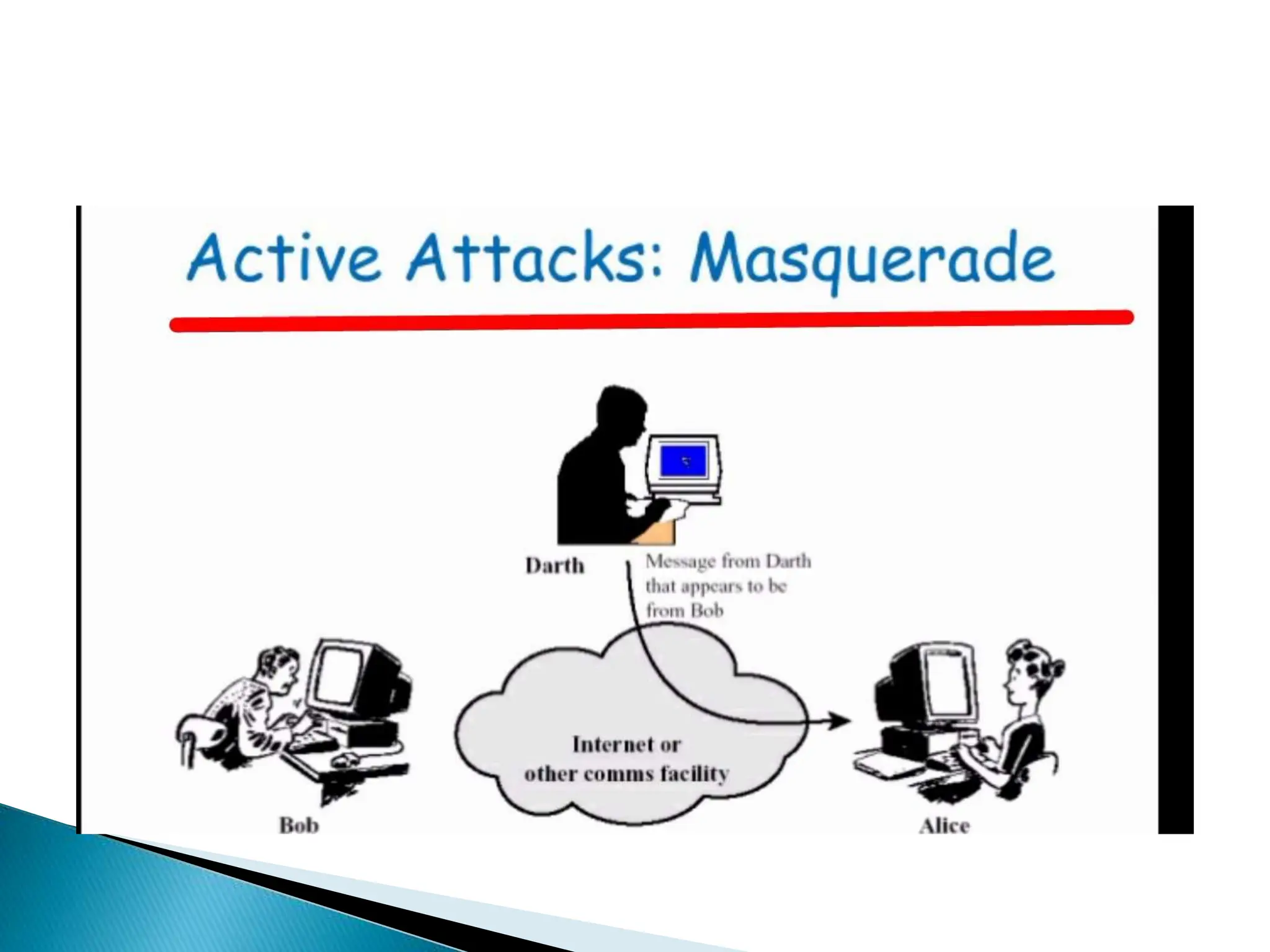
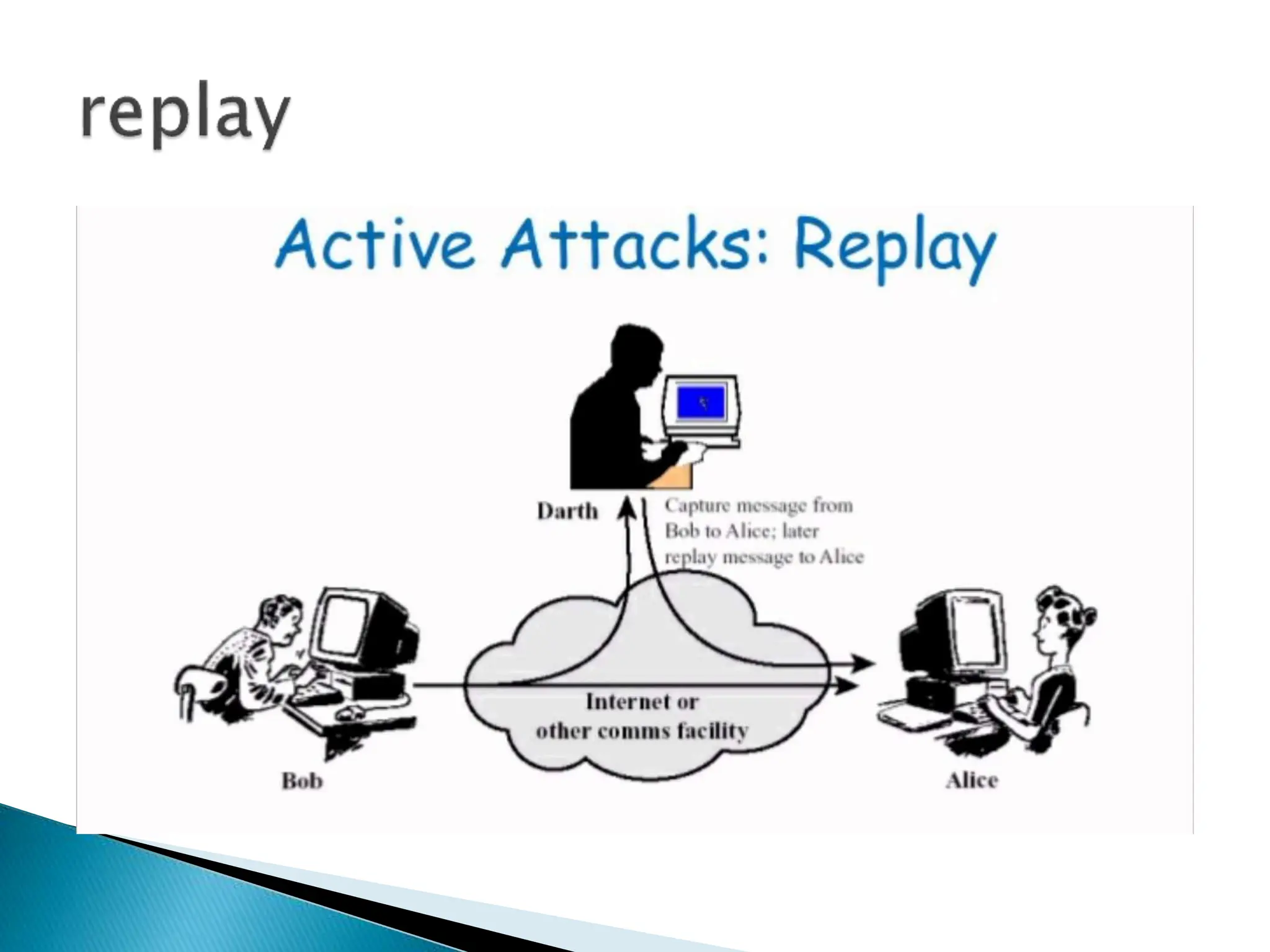
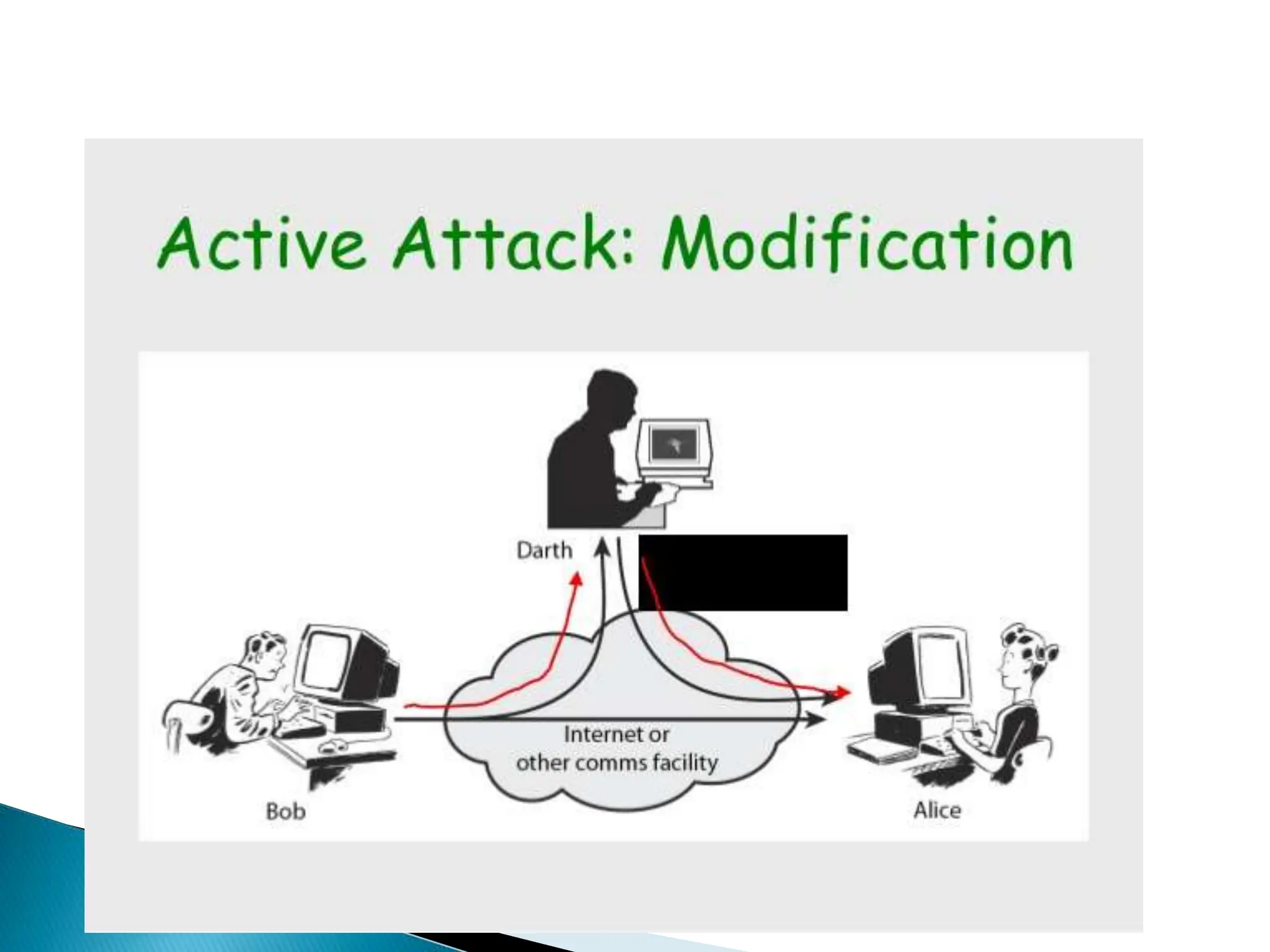
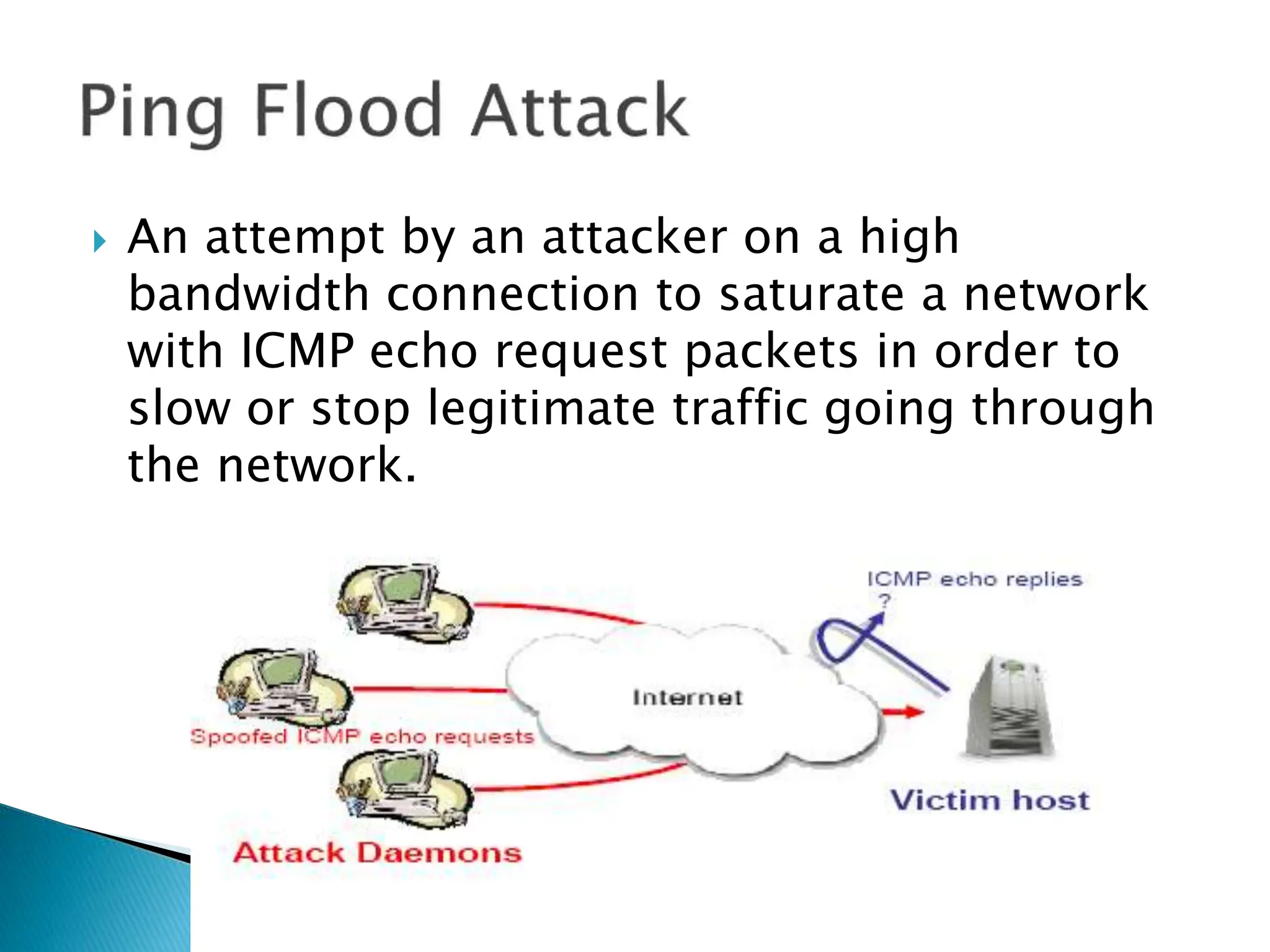
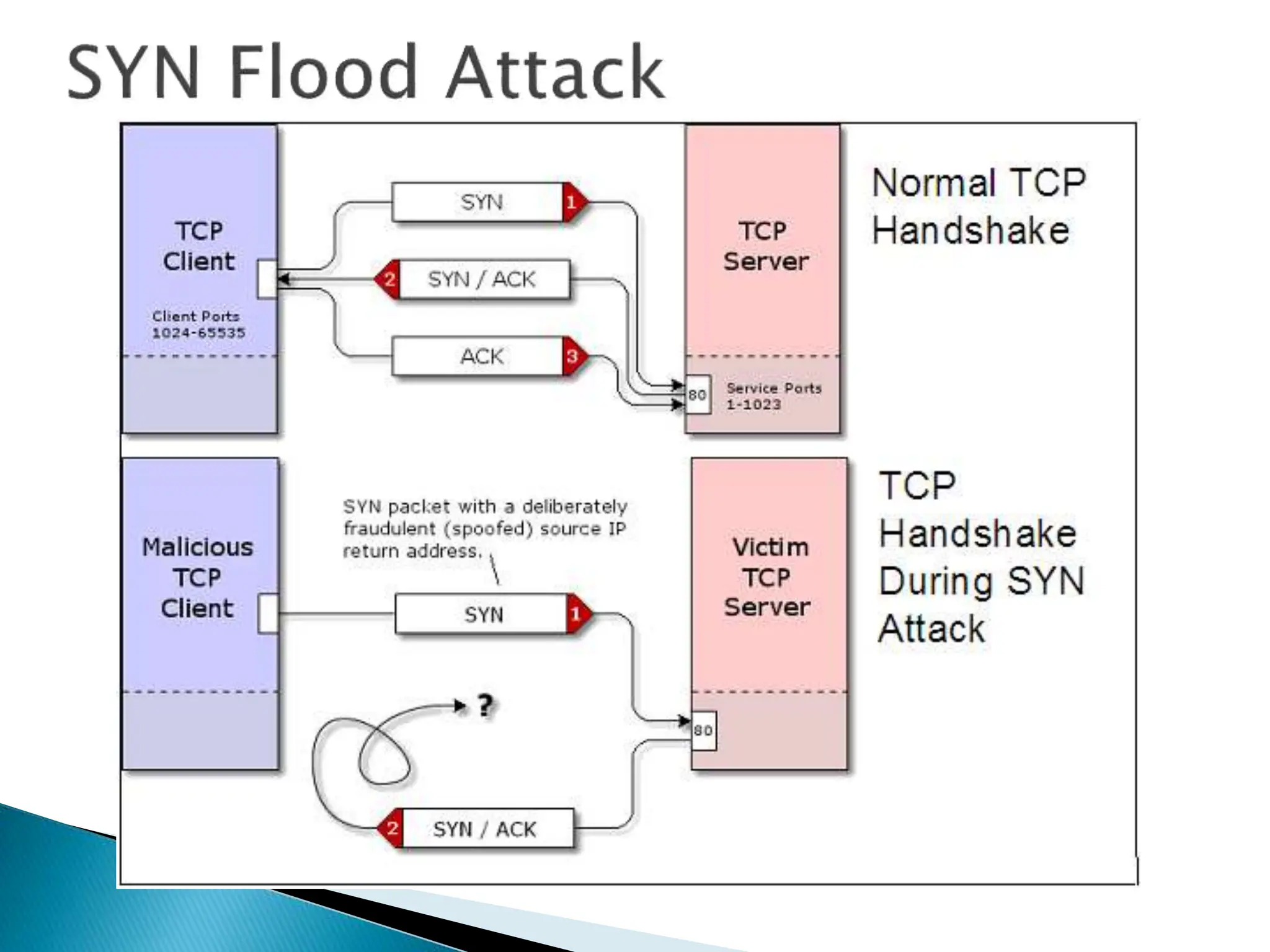
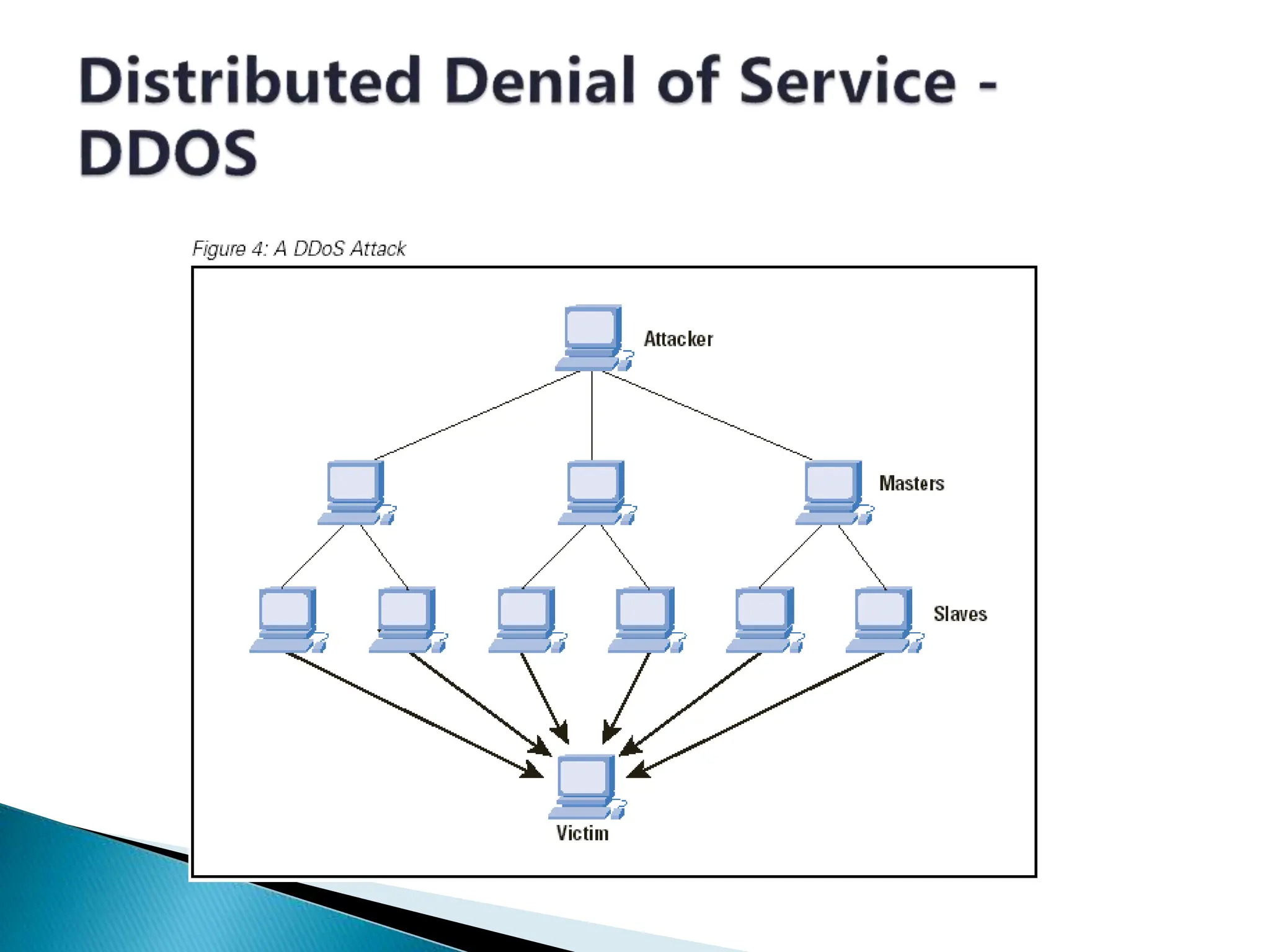
The document provides an overview of key concepts in computer security. It discusses the CIA triad of confidentiality, integrity, and availability as fundamental security principles. It also defines common security threats like eavesdropping, masquerading, replay attacks, and denial-of-service attacks. Authentication, authorization, access control, accountability, and non-repudiation are presented as important security mechanisms. Denial-of-service attacks aim to disrupt systems by overloading them with requests to deny access to legitimate users.