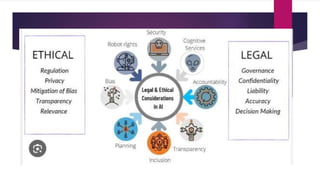
This document discusses laws and ethics related to information security. It begins by defining laws and ethics, noting that laws carry sanctions while ethics do not. It discusses how ethics are based on cultural norms and provides examples of universally accepted ethics. It then discusses organizational liability if an organization does not encourage or model strong ethical behavior. It notes that liability extends beyond criminal law and includes obligations to compensate for wrongs. It emphasizes the need for due care, due diligence, and counsel. The document also discusses policy versus law, types of law, general computer crime laws, privacy laws, identity theft laws, export/espionage laws, copyright law, codes of ethics, and why ethics are significant for information security. It poses ethical questions