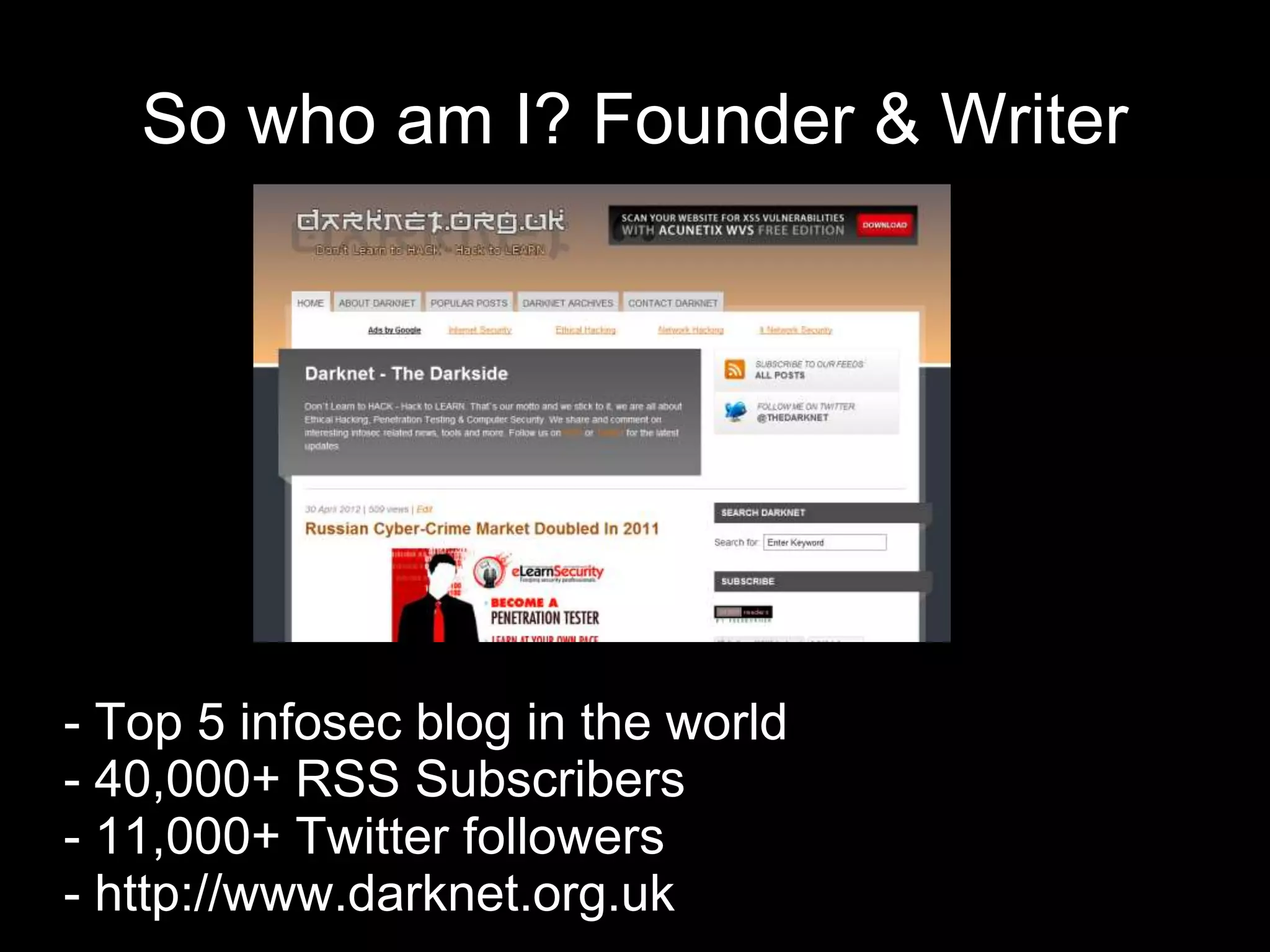
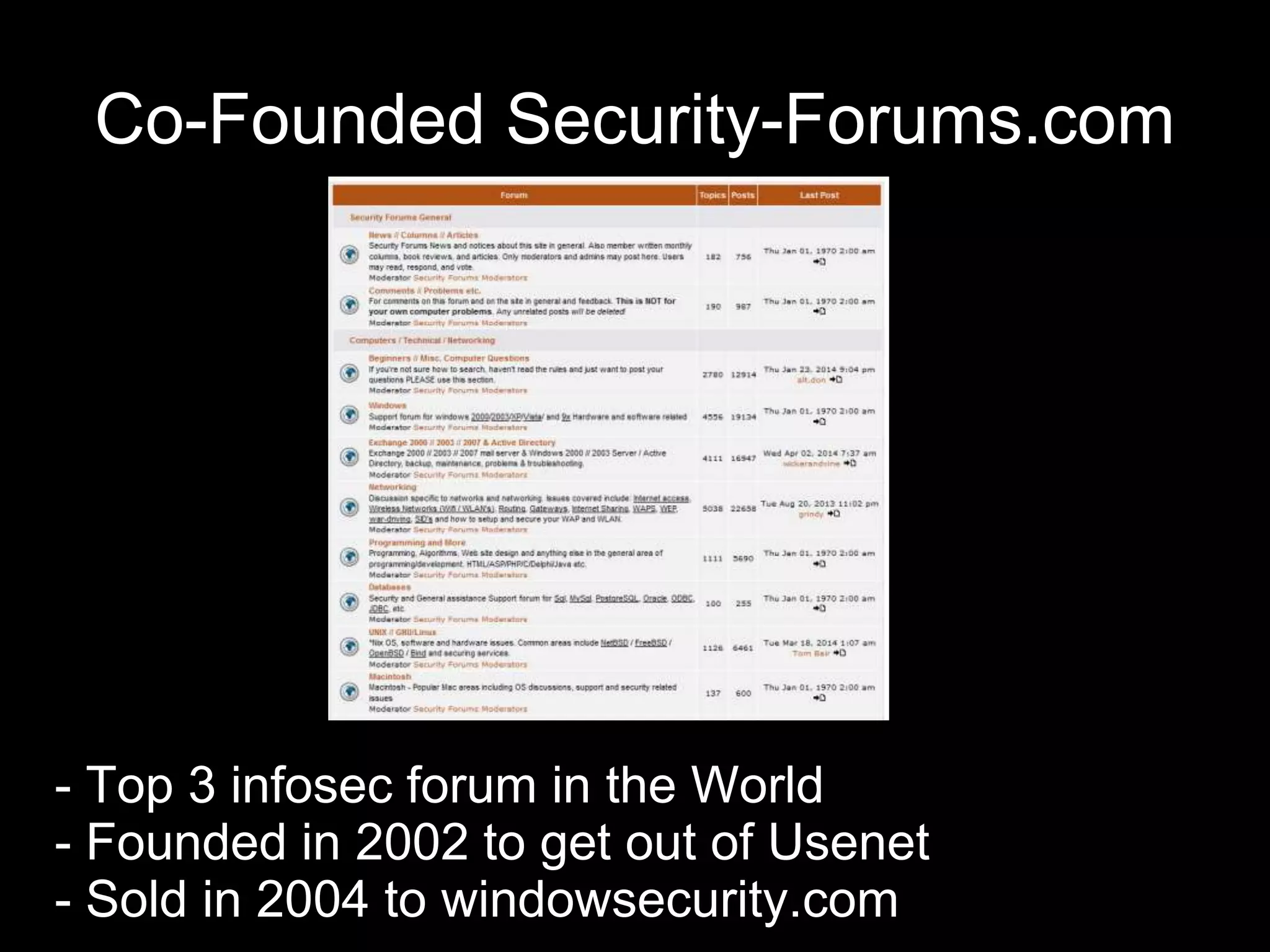
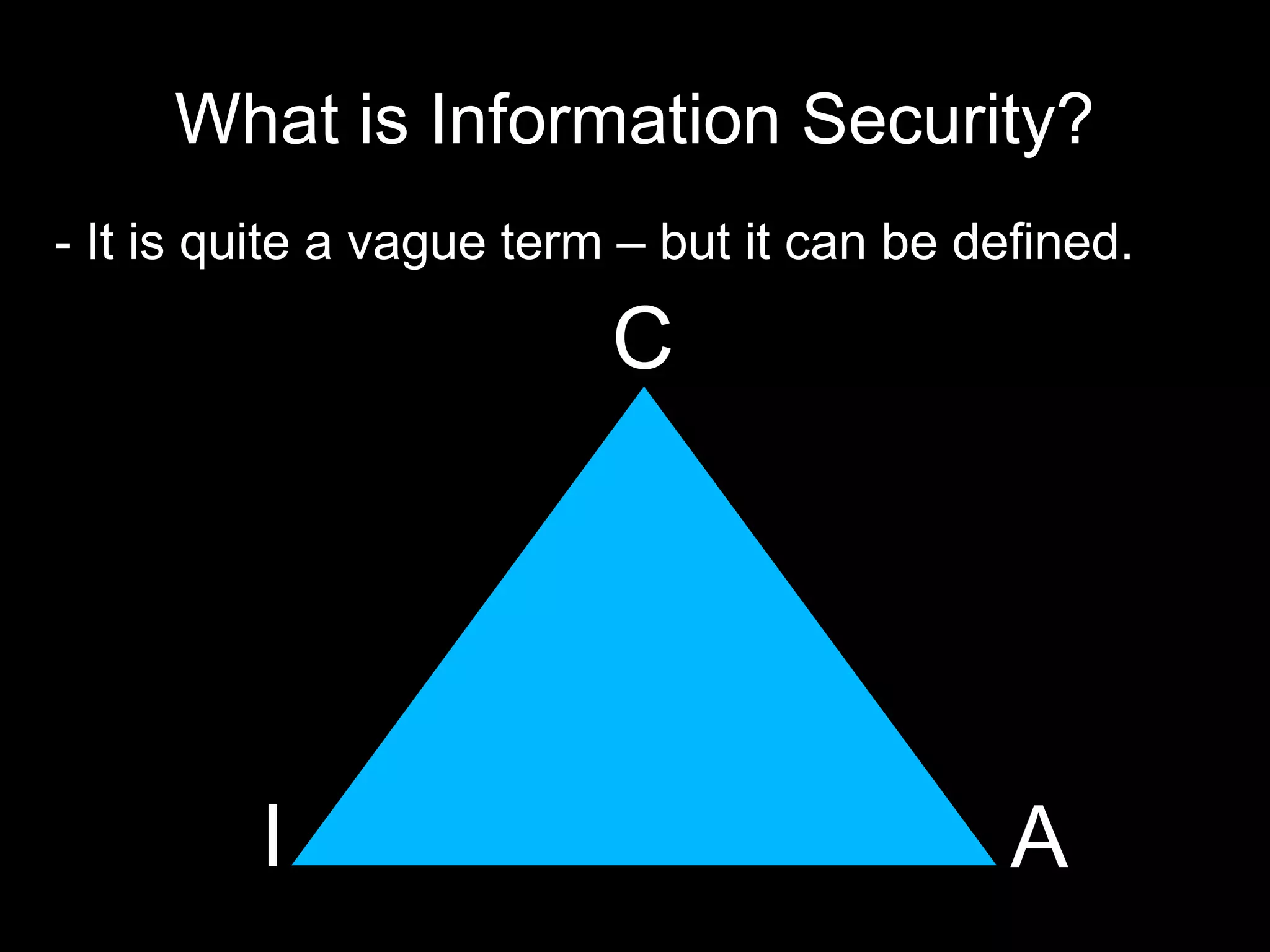
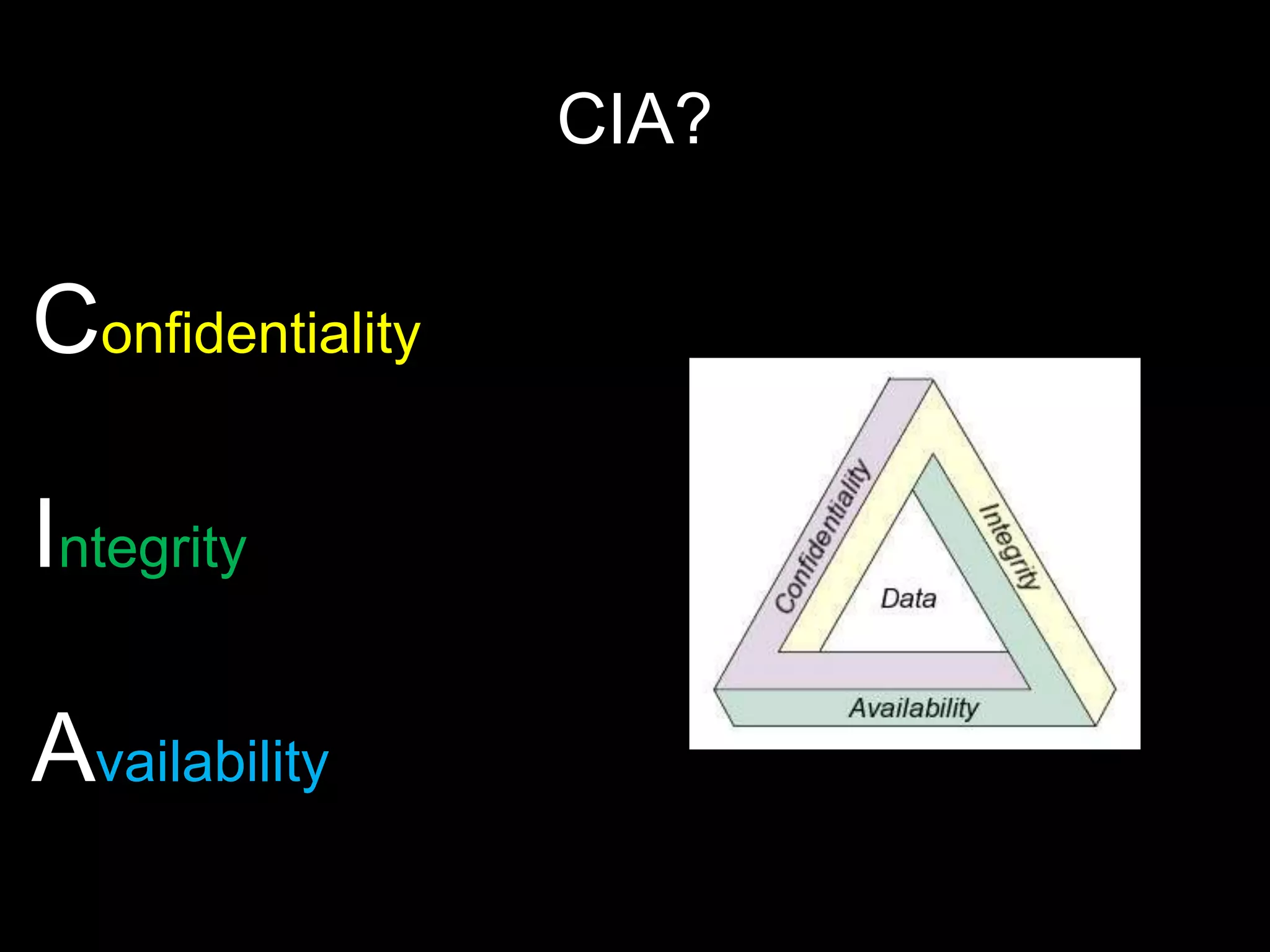
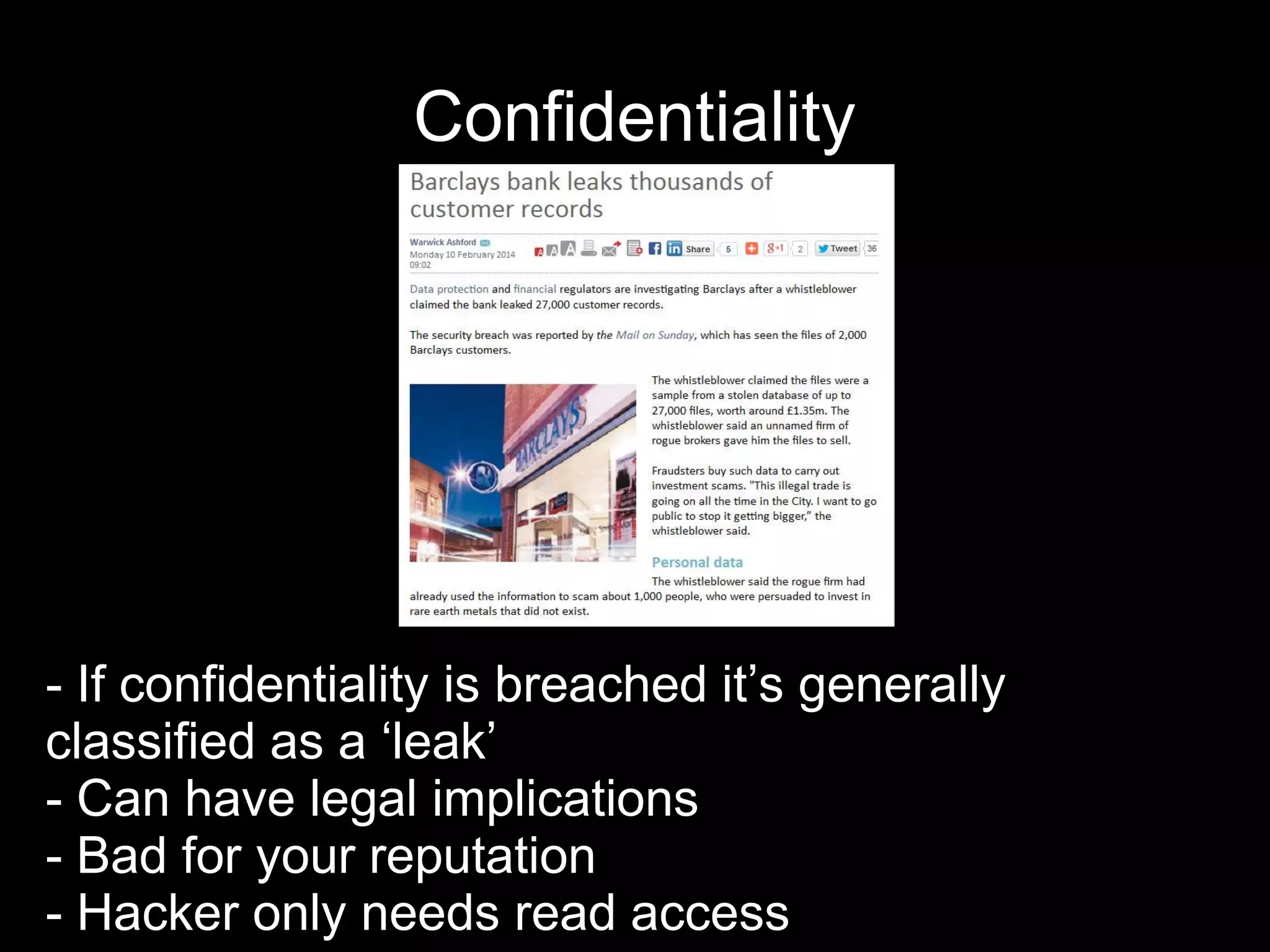
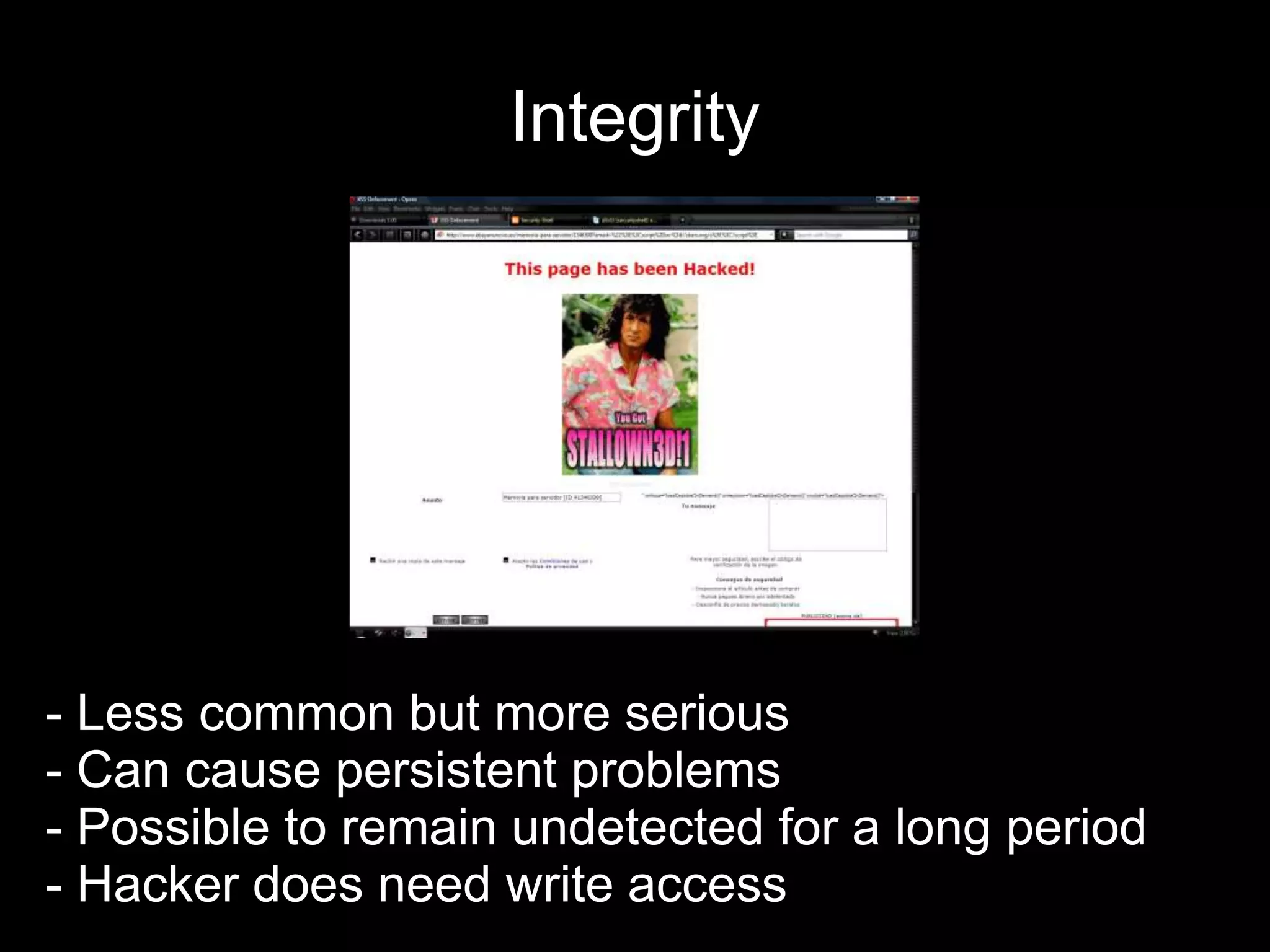
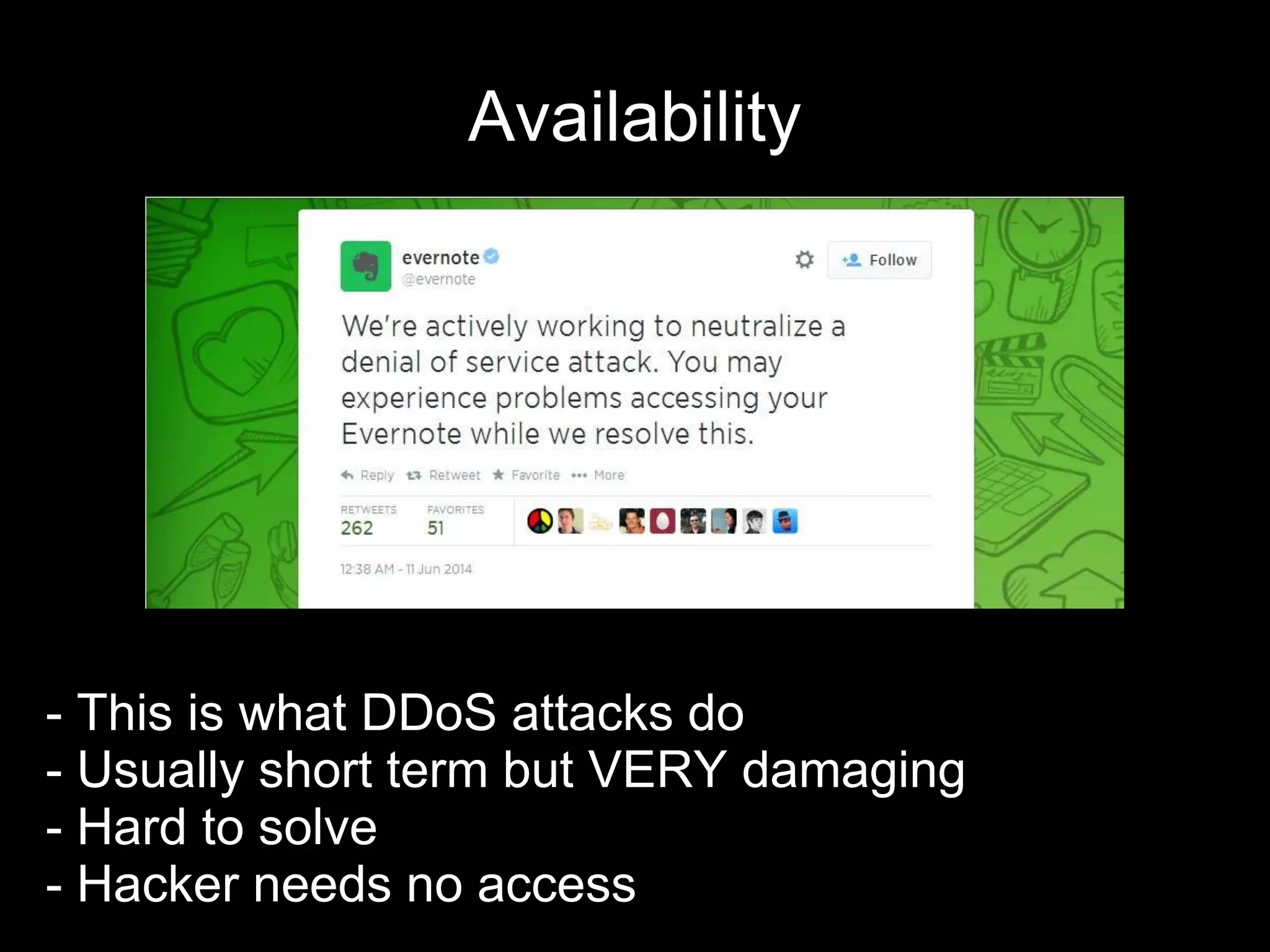
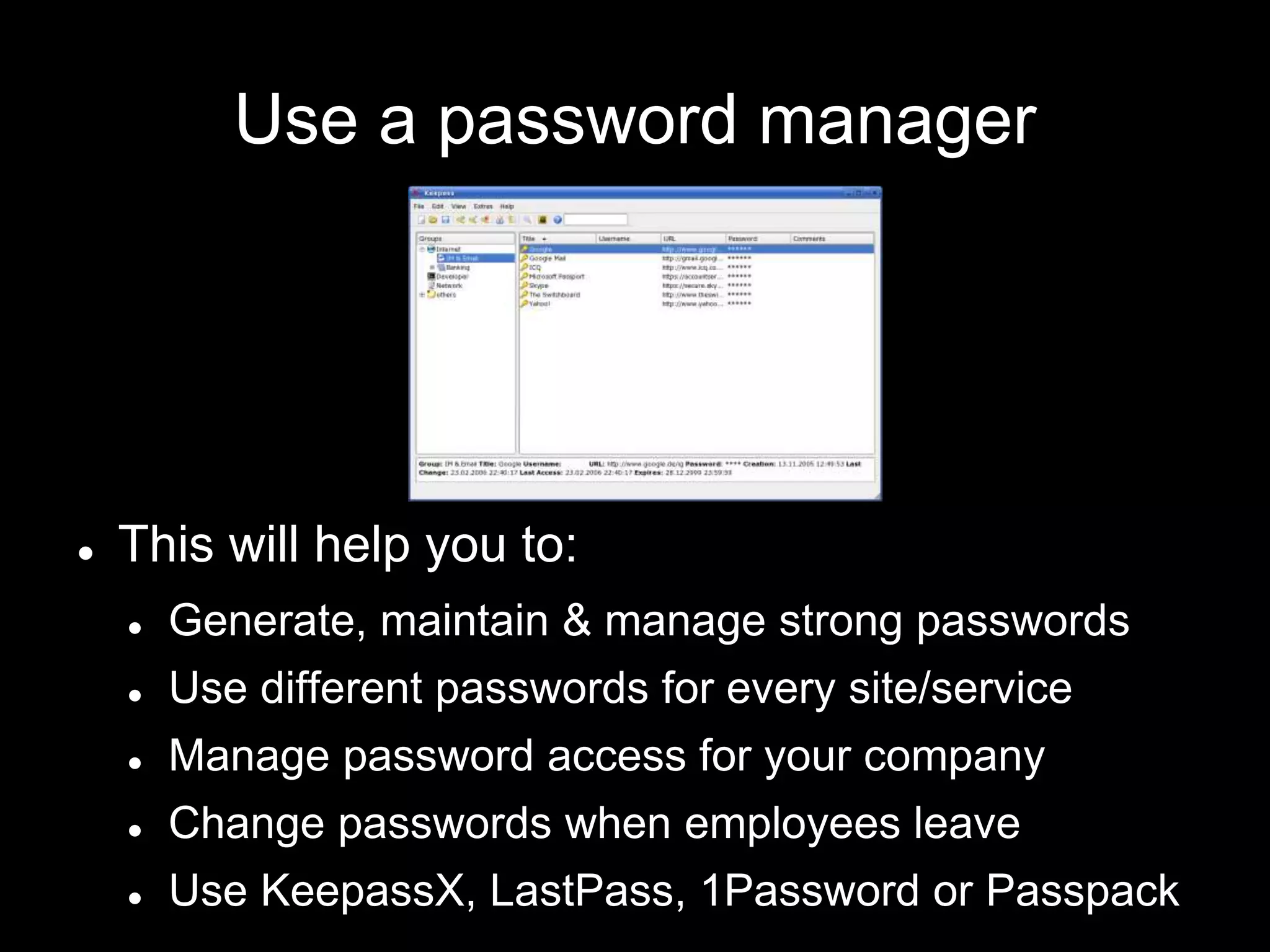
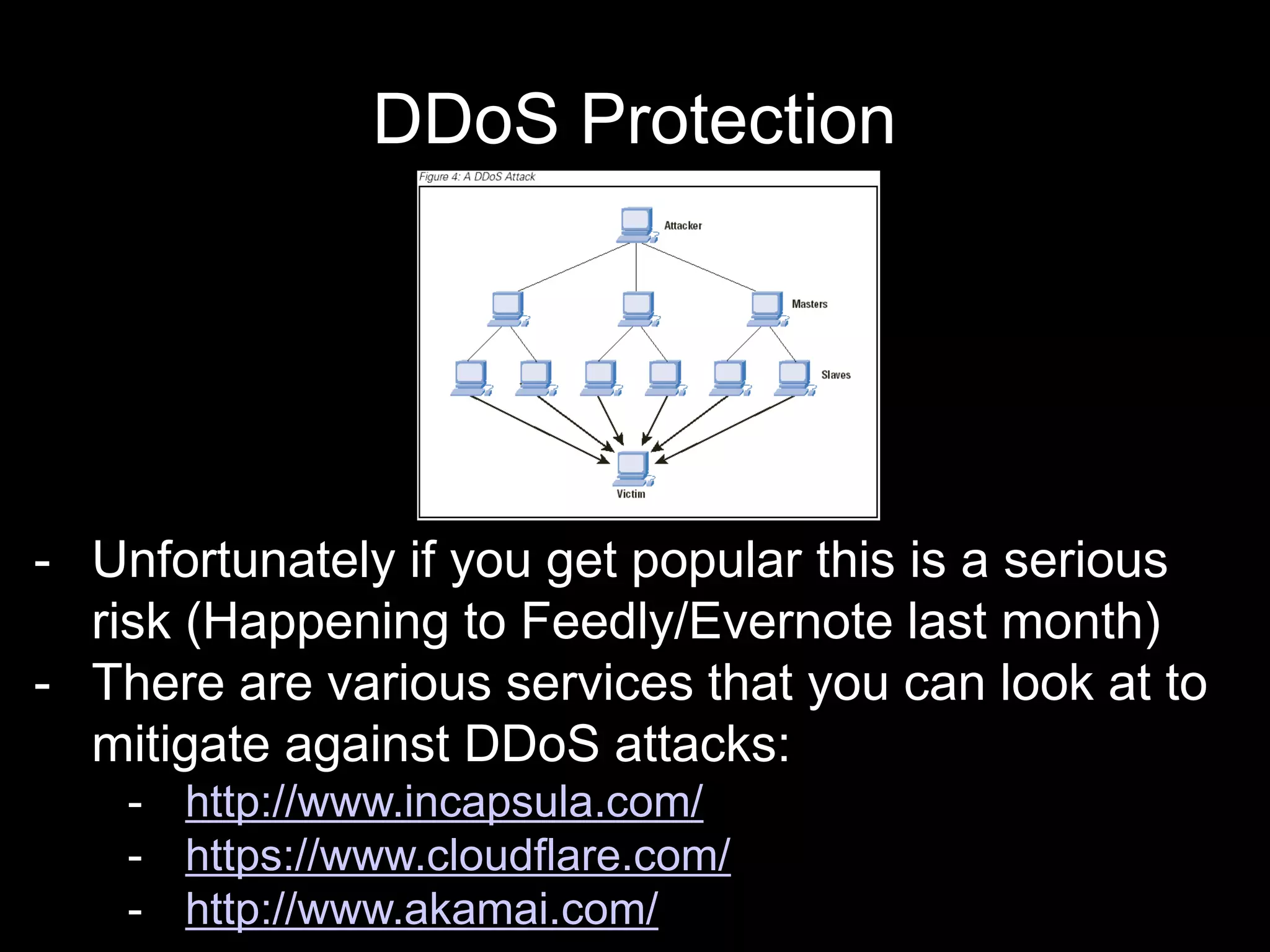
The document provides an introduction to information security, defining key concepts such as confidentiality, integrity, and availability. It emphasizes the importance of strong password management, resource management, and employee education to safeguard against security breaches. The document also highlights the risks of DDoS attacks and recommends using protective services and best practices for platform security.