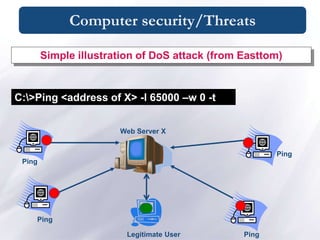
The document discusses various topics relating to computer security and privacy including definitions, types of attacks and threats, vulnerabilities, countermeasures, physical security, and the human factor. It provides an overview of security concepts, outlines common computer security attacks and their categories, and discusses prevention and recovery strategies. The document also covers specific threats like viruses, worms, trojans, and describes anti-virus functions.



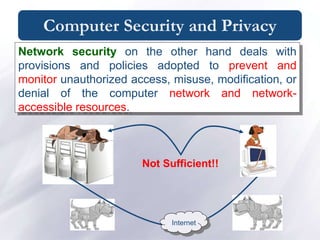
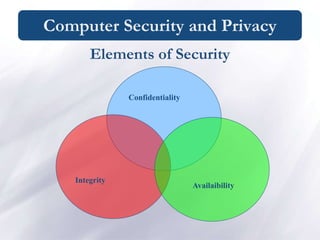







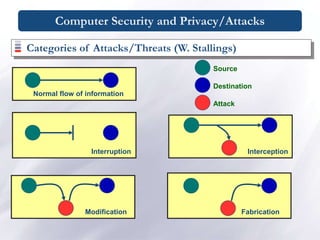




![Computer Security and Privacy/ Physical Security
“The most robustly secured
computer that is left sitting
unattended in an unlocked room
is not at all secure !!”
[Chuck Easttom]](https://image.slidesharecdn.com/chapter1security-240103152348-3d46ed35/85/chapter-1-security-ppt-18-320.jpg)
![Computer Security and Privacy/ Physical Security
Physical security protects your physical computer
facility (your building, your computer room, your
computer, your disks and other media) [Chuck
Easttom].
Physical security is the use of physical controls to
protect premises, site, facility, building or other
physical asset of an organization [Lawrence Fennelly]](https://image.slidesharecdn.com/chapter1security-240103152348-3d46ed35/85/chapter-1-security-ppt-19-320.jpg)