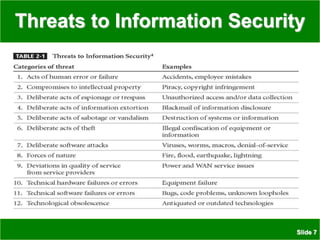
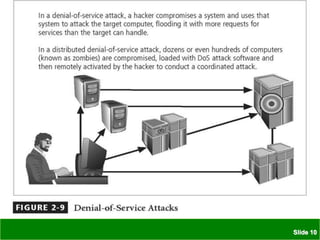
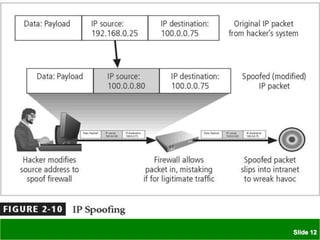
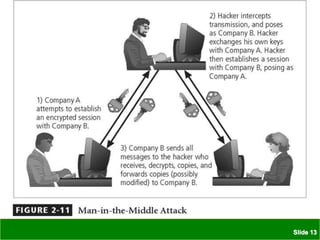
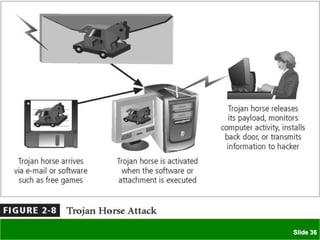
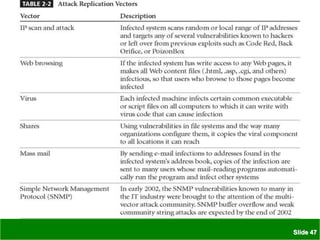
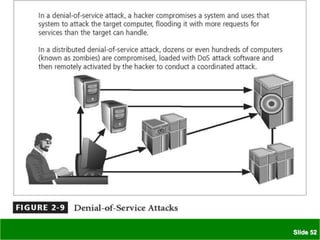
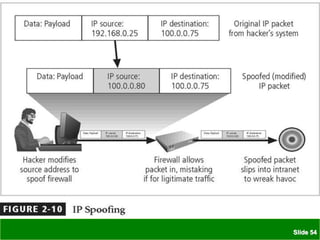
The document discusses various threats to information security assets like data, hardware, and users. It covers common types of hacking threats like malware, social engineering, and denial of service attacks. It also explains vulnerabilities in hardware, software, networks, personnel, physical sites, and organizational processes. The document provides details on protective measures organizations can take, including strong access control, keeping all software updated, network protection, employee training, and backups. Acts of human error, intellectual property compromises, espionage, information extortion, sabotage, theft, internet service issues, and loss of other utility services are also summarized as threats to information security.