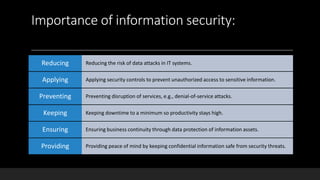
The document discusses information security and provides an agenda covering topics such as defining information security, principles of information security, examples of sensitive data, importance of information security, famous security threats and attacks, and how to protect systems. Information security refers to processes and methods used to protect sensitive information from unauthorized access or disruption, and the principles of information security are confidentiality, integrity, and availability. Examples of sensitive data include personal information like health records, financial information, and company or customer data.