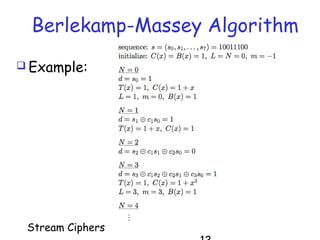
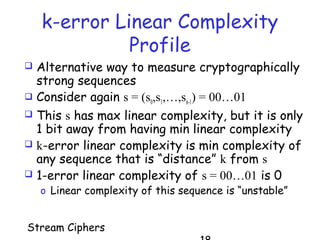
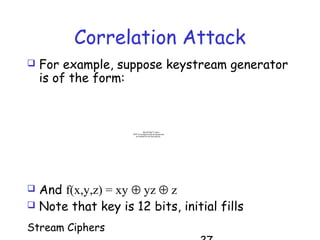
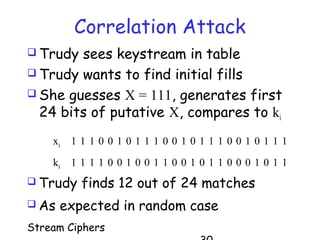
Stream ciphers work by generating a keystream that is XOR'd with the plaintext to produce the ciphertext. They generalize the one-time pad by using a short key to generate a pseudorandom keystream. Stream ciphers are commonly built using linear feedback shift registers (LFSRs) that generate bits over time. The keystream must have high linear complexity and be unpredictable to resist attacks like the Berlekamp-Massey algorithm. Multiple LFSRs combined with a nonlinear function can produce a cryptographically strong keystream, but must be designed carefully to prevent correlation attacks.