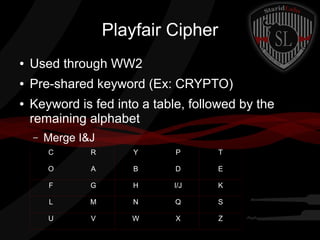
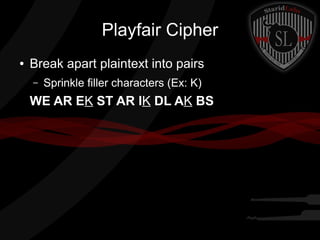
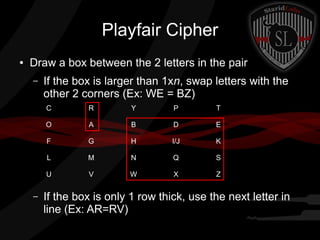
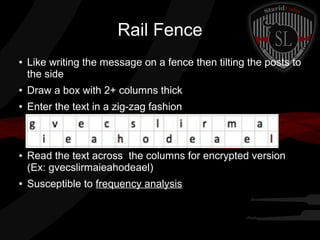
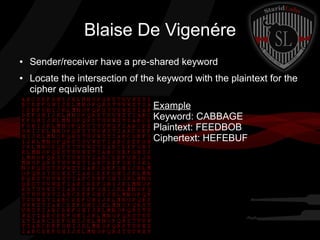
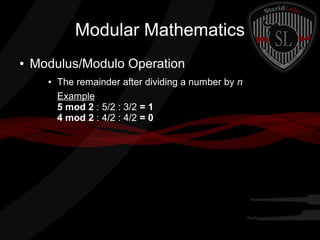
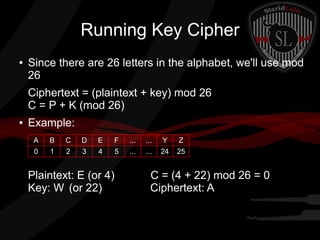
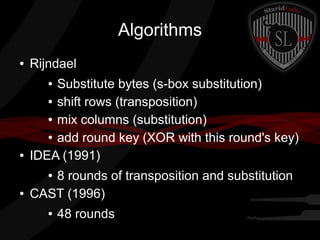
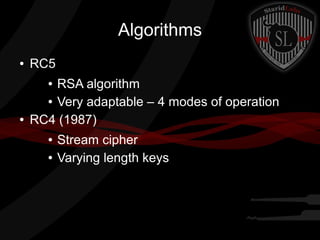
This document provides a summary of symmetric cryptography concepts and algorithms. It begins with a brief history of early ciphers like the Caesar cipher and Enigma machines. It then covers various types of symmetric ciphers including substitution, transposition, polyalphabetic, and one-time pads. Block cipher modes like ECB, CBC, CFB and OFB are also summarized. Popular symmetric algorithms like DES, AES, RC4, RC5 and Blowfish are mentioned along with their characteristics. The document concludes with pros and cons of symmetric cryptography, noting that while it is fast and secure, key management can be difficult without non-repudiation.