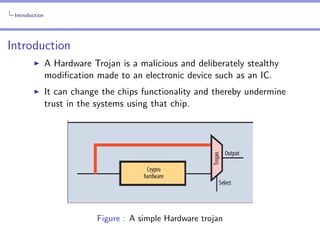
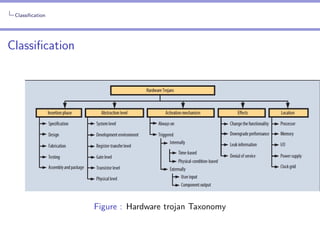
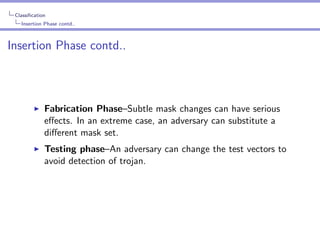
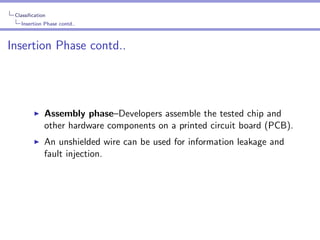
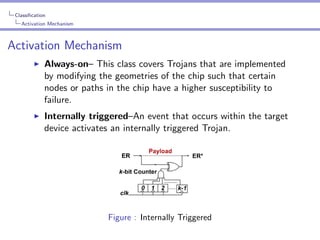
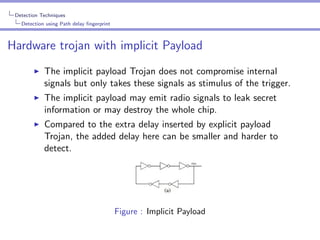
The document provides an in-depth analysis of hardware trojans, including their classification, insertion techniques, and detection methods. It discusses various phases where trojans can be inserted, such as specification, design, and fabrication, and highlights the challenges in detecting them with techniques like power analysis and delay fingerprinting. The paper concludes that hardware trojan insertion can occur at any stage of the IC design cycle and calls attention to the ineffectiveness of certain detection methods for implicit payload trojans.














![Hardware Trojan Insertion
Bypassing Delay fingerprint technique
The following trojans were inserted in [ZTT11]
Trojan
T1
T2
T3
T4
T5
T6
Class
DRULP
DRULP
DRULP
DRUPP
DRUPP
DRTPP
Trigger
din(1 downto 0)
din=4’hf
din=4’h8
Reset=1’b0
din( 1 downto 0)=2’b01
timing sequence
Payload
SP leaked by 7 segement display
Secret key leaked by 7 segement display
Secret leaked by LD7 in serial
1-stage ring oscillator
3-stage ring osillator
clock buffer chain
Out of the six trojans, T1,T2,T3 are explicit payload trojans.](https://image.slidesharecdn.com/seminarhardwaretrojan-131118032506-phpapp02/85/Hardware-Trojans-27-320.jpg)



![Hardware Trojan Insertion
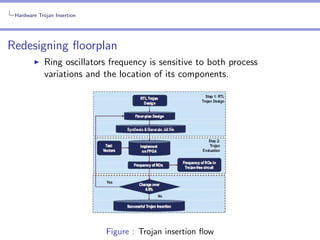
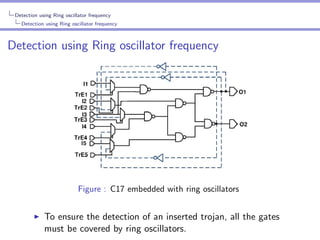
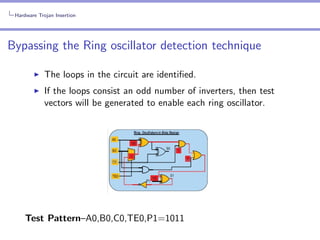
Bypassing the Ring oscillator detection technique
After generating the test patterns, two methods were
employed in [ZTT11] to evade the detection:Modelling the Ring oscillator frequency(Hard code attack).
Redesigning the floorplan.](https://image.slidesharecdn.com/seminarhardwaretrojan-131118032506-phpapp02/85/Hardware-Trojans-32-320.jpg)