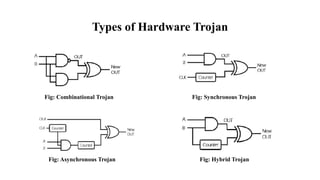
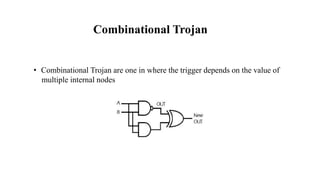
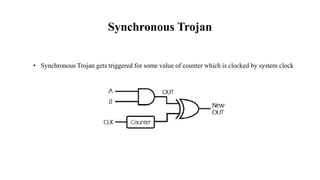
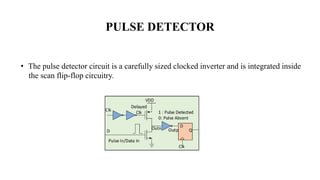
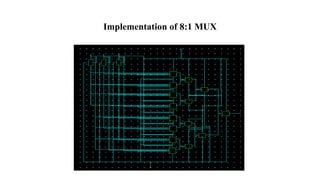
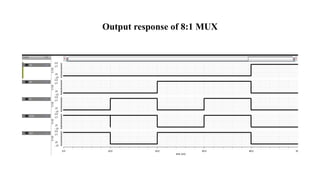
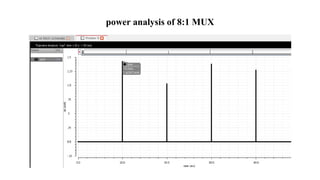
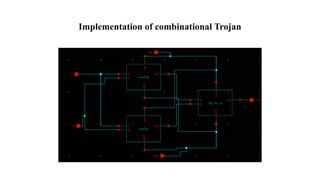
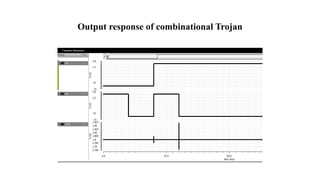
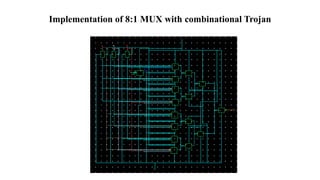
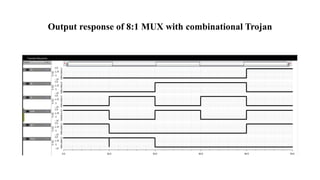
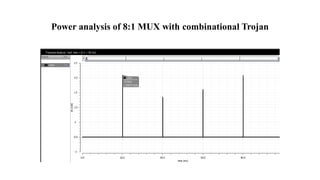
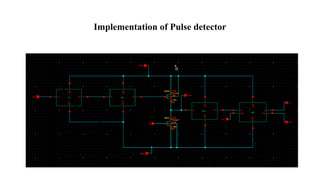
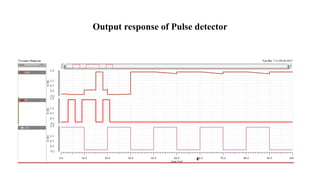
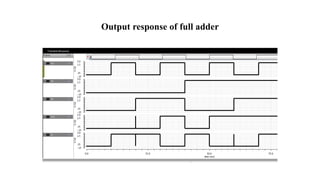
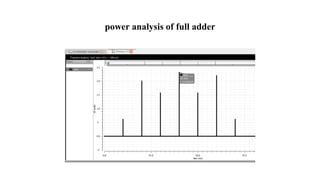
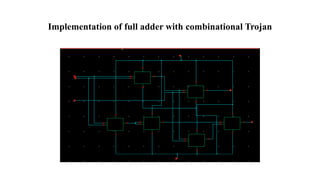
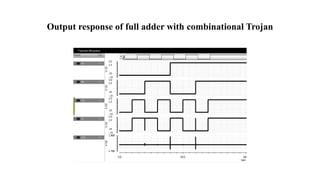
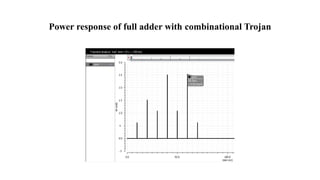
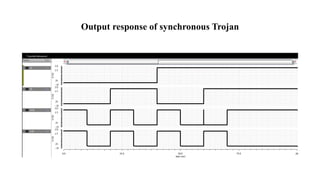
The document discusses hardware Trojan detection techniques. It describes the objective of detecting Trojans in circuits by analyzing power and delay. It then discusses different Trojan detection techniques like power measurement, path delay measurement, and physical design based testing. It also describes different types of hardware Trojans and provides implementation results of detecting Trojans in circuits like an 8:1 MUX and full adder using LBIST. LBIST was also implemented in an AES core to detect Trojans, achieving high test coverage while detecting minimal changes in area and power between Trojan-free and Trojan-inserted circuits.


















![References
[1] Mitra, S., McCluskey, E J., Makar, S. (2002). Design for testability and testing of IEEE 1149.1
TAP controller. Proceedings 20th IEEE VLSI Test Symposium (VTS’02), pages 247-252.
2] Janusz Rajski, Katarzyna Radecka, Jerzy Tyszer. (1997). Arithmetic Built-In Self-Test for DSP
Cores. IEEE Transactions On Computer-Aided Design Of Integrated Circuits AndSystems.16(11):1-
7.
[3] Tobias Strauch. (2012). Single Cycle Access Structure for Logic Test. IEEE Transactions On Very
Large Scale Integration Systems. 20(5):878 – 891.
[4] Kedarnath J. Balakrishnan, and Nur A. Touba. (2006). Improving Linear Test Data Compression.
IEEE Transactions On Very Large Scale Integration Systems. 14(11):1227-1237.
[5] J. Rajski, J. Tyszer, M. Kassab, and N. Mukherjee, “Embedded deterministic test,” IEEE
Transactions on Computer-Aided Design of Integrated Circuits and Systems, vol. 23, pp. 776 – 792,
May 2004.](https://image.slidesharecdn.com/15mv32-170512005904/85/trojan-detection-54-320.jpg)
![Cont.
[6] G. Hetherington, T. Fryars, N. Tamarapalli, M. Kassab, A. Hassan, and J. Rajski, “Logic BIST for
large industrial designs: real issues and case studies,” in Proceedings of International Test Conference
(ITC’1999), pp. 358 – 367, 1999.
[7] Alex Baumgarten, Michael Steffen, Matthew Clausman, Joseph Zambreno, "A case study in
hardware Trojan design and implementation," International Journal of Information Security, Volume
10, Issue 1, pp. 1‐14, 2011.
[8] Y.Jin and Y.Markis “Hardware trojan detection using path delay fingerprint”, IEEE intl. workshop
on Hardware oriented security and trust, pp.51-57,2008.
[9] Kurt Rosenfeld and Ramesh Karri. (2011). Security-Aware SoC Test Access Mechanism. IEEE
29th VLSI Test Symposium (VTS), pages 100-104.
[10] Luke pierce and Spyros Tragoudas. (2011) Multilevel Secure JTAG Architecture. IEEE 17th
International On-Line Symposium, pages 208-209.
[11] Nan Li, Gunnar Carlsson, Elena Dubrova, Kim Peters´en “Logic BIST: State-of-the-Art and Open
Problems” arXiv:1503.04628v1 [cs.AR] 16 Mar 2015](https://image.slidesharecdn.com/15mv32-170512005904/85/trojan-detection-55-320.jpg)
![Cont.
[12] S. Deyati, B. J. Muldrey, A. Singh, and A. Chatterjee, "High Resolution Pulse Propagation Driven Trojan
Detection in Digital Logic: Optimization Algorithms and Infrastructure," in Test Symposium (ATS), 2014 IEEE
23rd Asian, 2014, pp. 200-205.
[13] M. Banga and M. S. Hsiao, "A Novel Sustained Vector Technique for the Detection of Hardware Trojans,"
in VLSI Design, 2009 22nd International Conference on, 2009, pp. 327-332.
[14] B. Cha and S. K. Gupta, "Trojan detection via delay measurements: A new approach to select paths and
vectors to maximize effectiveness and minimize cost," in Design, Automation & Test in Europe Conference &
Exhibition (DATE), 2013, 2013, pp. 1265-1270.
[15] F. Wolff, C. Papachristou, S. Bhunia, and R. S. Chakraborty, "Towards Trojan-Free Trusted ICs: Problem
Analysis and Detection Scheme," in Design, Automation and Test in Europe, 2008. DATE '08, 2008, pp. 1362-
1365.
[16] J. Yier and Y. Makris, "Hardware Trojan detection using path delay fingerprint," in HOST 2008., pp. 51-57.
[17] R. S. Chakraborty, S. Narasimhan, and S. Bhunia, "Hardware Trojan: Threats and emerging solutions," in
High Level Design Validation and Test Workshop, 2009. HLDVT 2009. IEEE International, 2009, pp. 166-171.
[18] https://en.wikipedia.org/w/index.php?title=Hardware_Trojan& oldid=740716473](https://image.slidesharecdn.com/15mv32-170512005904/85/trojan-detection-56-320.jpg)