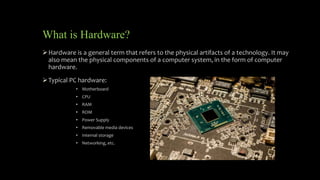
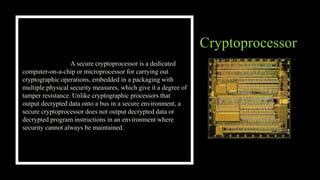
The document explains hardware security, including its distinction from software security and its importance in protecting data and computing systems. It highlights various types of hardware security devices, such as cryptoprocessors and hardware security modules, which help implement encryption, prevent data exposure, and enhance overall security. Additionally, it outlines the necessity of maintaining power protection and heat management to ensure the integrity and longevity of computer hardware.