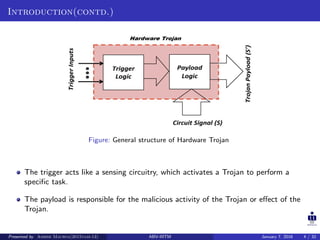
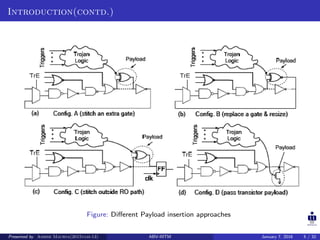
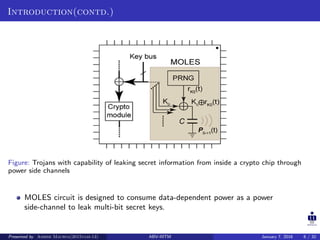
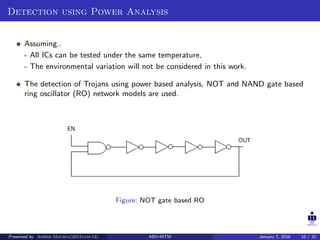
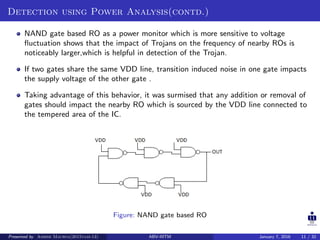
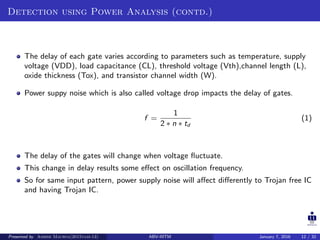
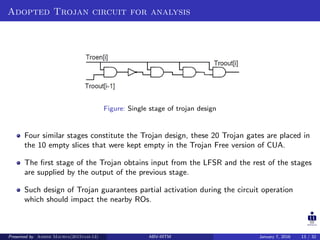
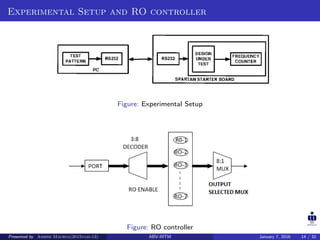
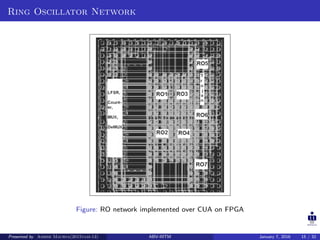
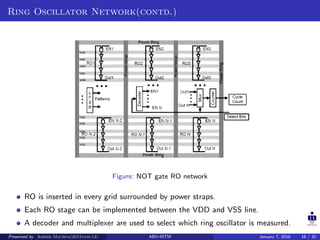
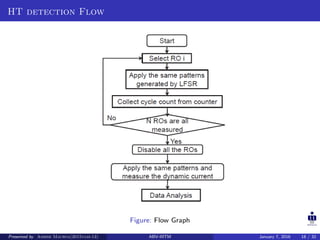
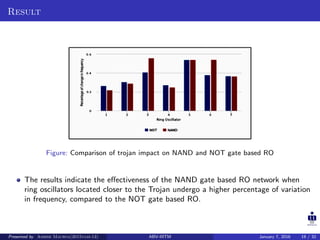
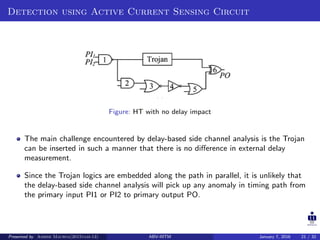
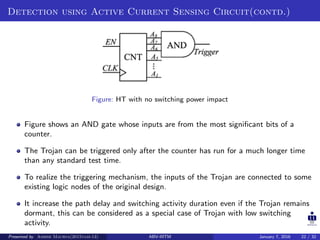
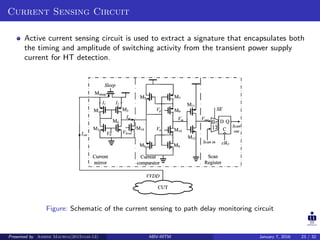
The document presents two techniques for detecting hardware Trojans: detection using power analysis and detection using active current sensing circuits. For power analysis, a ring oscillator network is used to detect Trojans by measuring changes in oscillation frequency from power supply noise. NAND gate-based ring oscillators are more sensitive than NOT gate-based ones. For current sensing, circuits measure switching activity and path delays to detect Trojans even if they do not impact delays or power. Both techniques aim to detect rarely activated Trojans through side-channel analysis of power signatures.